Application whitelisting using Software Restriction Policies
Software Restriction Policies (SRPs) is a Group Policy-based feature in Active Directory (AD) that identifies and controls the execution of various programs on the computers in an AD domain. With the help of SRPs, administrators can establish trust policies to restrict certain scripts and applications that aren't fully trusted from running. Using SRP as an application whitelisting technique allows administrators to enhance their domain's security posture by preventing malicious programs from executing.Configuring SRPs for application whitelistingConsider a scenario where a user installs a program without notifying the administrator. Such a program could remain unpatched after a critical vulnerability is publicly disclosed, which opens it up to be exploited by malware. Obviously, unpatched applications shouldn't be allowed to run until they're secured. With application whitelisting, administrators can ensure that only approved programs are allowed to run and any other program will be blocked by default.
To configure an SRP to operate in a path-based whitelisting mode with the most secure settings, follow these steps: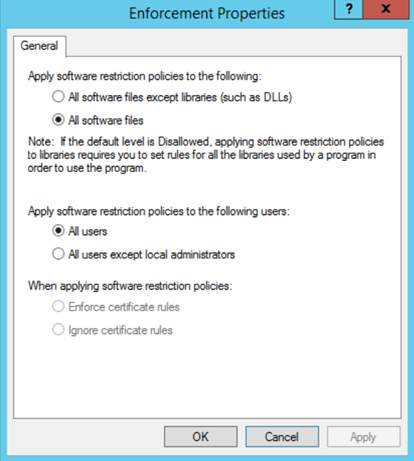 Figure 1. Configuring the Enforcement settings.
Figure 1. Configuring the Enforcement settings.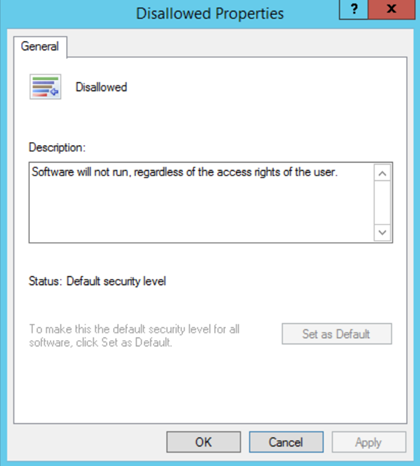 Figure 2. Configuring the Disallowed security level.
Figure 2. Configuring the Disallowed security level.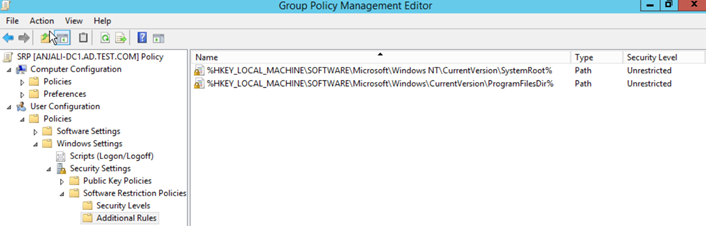 Figure 3. Default path rules for whitelisting.
Figure 3. Default path rules for whitelisting.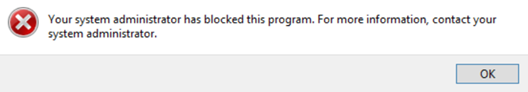 Figure 4. Error message for a program loading libraries from a disallowed path.SummaryApplication whitelisting using an SRP defines which applications are allowed and prevents unauthorized programs from running, which in turn protects your Windows environment. Whitelisting keeps your enterprise protected from emerging threats while still allowing users to run the applications they need to perform their duties. Application whitelisting will save you time and money by preventing costly downtime, recovery, and remediation efforts.
Figure 4. Error message for a program loading libraries from a disallowed path.SummaryApplication whitelisting using an SRP defines which applications are allowed and prevents unauthorized programs from running, which in turn protects your Windows environment. Whitelisting keeps your enterprise protected from emerging threats while still allowing users to run the applications they need to perform their duties. Application whitelisting will save you time and money by preventing costly downtime, recovery, and remediation efforts.
- Open Group Policy Management.
- Right-click the domain or the required subfolder to create a new GPO, or select an already existing one. Right-click and select Edit to open the Group Policy Management Editor.
- Go to User Configuration > Policies > Windows Settings > Security Settings > Software Restriction Policies.
- Right-click the Software Restriction Policies folder and select New Software Restriction Policies.
- Double-click the Enforcement Select All software files and All users options. Click OK, as shown in Figure 1.
 Figure 1. Configuring the Enforcement settings.
Figure 1. Configuring the Enforcement settings.- Double-click Security Levels>Disallowed. Click the Set as default button and click Yes on the dialog box that pops up, as shown in Figure 2. Click OK.
 Figure 2. Configuring the Disallowed security level.
Figure 2. Configuring the Disallowed security level.- Click Additional Rules to view the default file paths configured to allow programs running under paths specified by the SystemRoot and ProgramFiles environment variables. See Figure 3 for an example.
 Figure 3. Default path rules for whitelisting.
Figure 3. Default path rules for whitelisting.- To add a new path rule, right-click the Additional Rules folder and select New Path Rule.
- In the New Path Rule dialog box, specify a path or click Browse to select a path. From the Security level drop-down menu, select Unrestricted. Enter a suitable description.
- Click OK.
 Figure 4. Error message for a program loading libraries from a disallowed path.SummaryApplication whitelisting using an SRP defines which applications are allowed and prevents unauthorized programs from running, which in turn protects your Windows environment. Whitelisting keeps your enterprise protected from emerging threats while still allowing users to run the applications they need to perform their duties. Application whitelisting will save you time and money by preventing costly downtime, recovery, and remediation efforts.
Figure 4. Error message for a program loading libraries from a disallowed path.SummaryApplication whitelisting using an SRP defines which applications are allowed and prevents unauthorized programs from running, which in turn protects your Windows environment. Whitelisting keeps your enterprise protected from emerging threats while still allowing users to run the applications they need to perform their duties. Application whitelisting will save you time and money by preventing costly downtime, recovery, and remediation efforts.
How should I block these error massage also.(These application has blocked by your system administrator)
So I was scared to death of implementing this at work. The consequences are dire if I blow up our corporate network. So I tentatively stuck my toe in the water with blacklisting. I kept thinking "every little bit helps". But it was difficult and definitely less than effective. I should have just gone with a "deny all" and used whitelisting. That was so much easier. And hardly a problem at all. The only issue I had was our net logon batch wouldn't run so some network shares were not connecting. I found the location of the net logon batches, whitelisted them. And we were good to go. I am a little concerned about some programs using App Data for storing program update applications. We'll cross that bridge as they come up.
what's difference between basic user and unrestricted Software restriction policies and example plz thank you
Application whitelisting using software restriction policies is to prevent users of an Active Directory Domain Services from using specific applications. It is much easier to restrict software than websites.
Application whitelisting using software restriction policies helps restrict users from installing applications/.exe files. Do keep in mind that the application or .exe gets restricted only if it is added in the policy (e.g., a list of trusted executables/applications can only be installed), else any application can be installed by a domain user.
When a user tries to execute a restricted application, they will get this message: "This program is blocked by group policy. For more information, contact your system administrator."
Hi I got a big problem, i assign only two application in software restriction policy. and now i can't access that policy , and also command prompt as an administrator. All I can use is only that two applications. I can't access other things. Thank you.
Thank you for reaching out. Have you done this via GPO? Also, are you using ManageEngine ADManager Plus? If so, you can view this in our GPO/GPO management reports. We would need more details to help you further. Please drop an email to support@admanagerplus.com and we can help you figure this out.