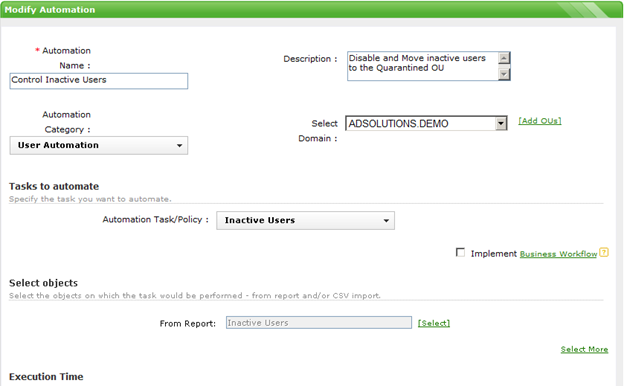
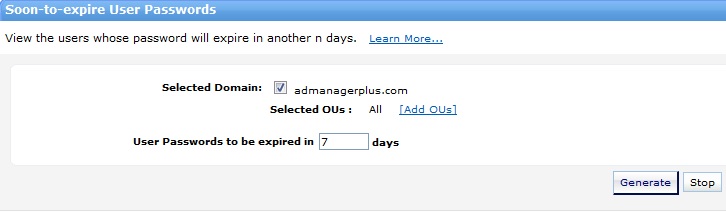
With so many compliance regulations requiring controls over inactive users, it is important to ensure that these user accounts in Active Directory are correctly managed....
Search results for: applications manager

Safeguard Your Computers Easily with Desktop Central’s Exclusive Patch Edition
Is your organization focusing on securing its network against operating system and application vulnerabilities to alleviate costs due to potential threats? Then you are perhaps...
Maximize Your Application Performance to Ensure Successful Business Outcomes – September 9, Forrester Webinar
Join Forrester and ManageEngine on a free, one-hour webinar that will help you discover ways to unlock the true prowess of application monitoring. Learn how to fully leverage the capabilities your...
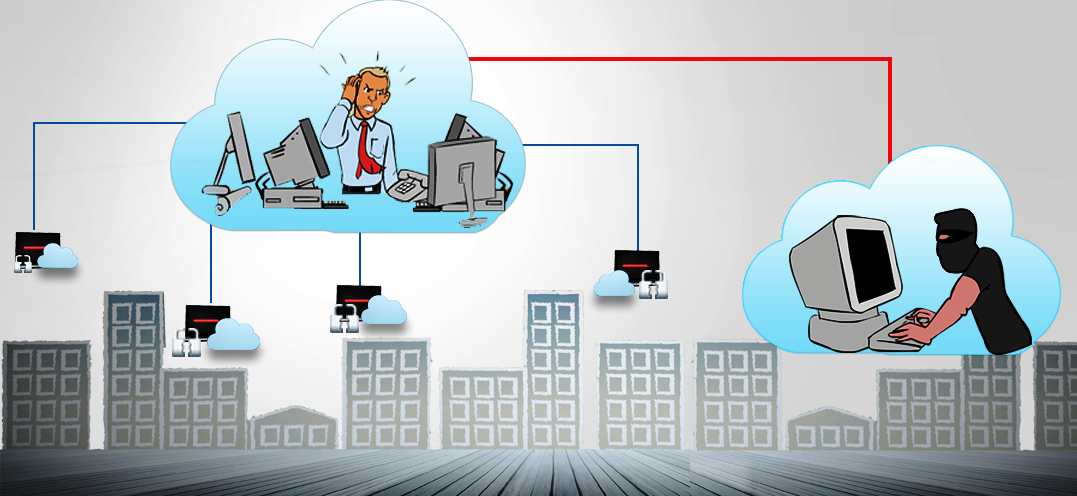
Code Spaces AWS Security Breach: A Sad Reminder of the Importance of Cloud Environment Password Management
In the recently concluded Black Hat USA, 2014, one of the topics that drew much attention was the session on the pitfalls in cloud environment...

Combat Advanced Cyber Attacks With Shared Security Intelligence
(Originally published in Cyber Defense Magazine, Black Hat special edition) In this information age, even the mightiest of enterprises and governments across the globe are worried...

Passwords, King of Authentication: Long Live the King!
This post is a reproduction of an article I wrote that was originally published in Business Computing World. “When you play the Game of Thrones, you...

Tips to consolidate your data center, IT Management for SMBs, the impact of the Internet of Things, and more
Is the password on its way out? V. Balasubramanian, marketing manager at ManageEngine weighs in on the death of the password in his Business Computing World article. Read about the benefits...

Why MSPs Should Take Extra Care in Managing Client Passwords
Passwords on spreadsheets put client networks at risk, along with Managed IT service providers’ credibility and trustworthiness. Managed IT Service Providers (MSPs) deliver a variety of...