Photo credit: Hindu Business Line Across the world people love various sports, be it basketball, football, tennis or cricket. There are humongous number of diehard...
Search results for: applications manager
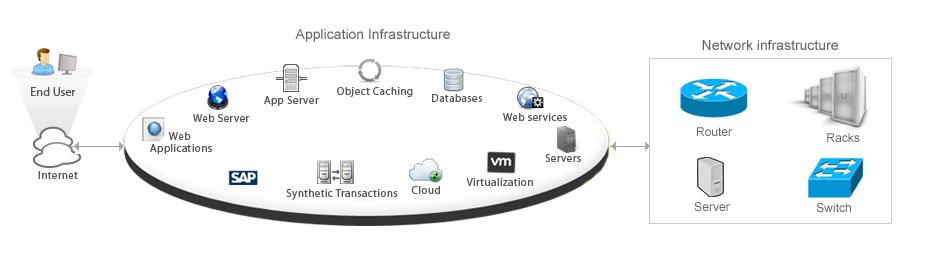
5 Reasons You Should Consider Application-Aware Network Performance Management
In today’s complex business environment, the first question thoughtful IT leaders ask when considering any new IT investment or change is, ‘How will it impact the business?’ That the business depends on well-managed IT is well understood. What is less well understood is how an IT organization can manage an infrastructure that is growing ever more complex. It’s not just the network infrastructure that IT teams need to consider; it’s not even the increasingly complex application infrastructure that stands between the physical network infrastructure and the users. The challenge today involves the effective management of both these infrastructures as well the interplay between them — and it’s the interplay between them that poses the greatest challenge. Application-aware network performance management (AA-NPM) tools can help you overcome that challenge. What is AA-NPM? These days, before an application appears in front of an end user, it may pass through numerous infrastructure components, as shown in the diagram below: Traditional or stand-alone application performance management (APM) tools provide visibility only into the middle component group, the application infrastructure. They typically support auto-discovery of all the applications in the networks, transaction analysis, application usage analysis, end-user experience analysis, and more. They also provide the basic functions to monitor the health and performance of all configured application infrastructure assets. But APM tools do not provide insight into the network infrastructure itself. Typically, network infrastructure managers rely on separate network performance management (NPM) tools for fault management, device monitoring, capacity planning, interface traffic analysis, configuration management and those sorts of tasks. The problem with a management approach that relies on two separate tools is that neither of these tools is designed to facilitate the management of the interplay between these environments...
Could Your Jewelry Stop Hackers?
Google has been talking about an innovative idea to replace passwords with jewelry — that’s right, jewelry. Actually, the enabling technology could be hidden in jewelry,...
Superbowl vs Soup bowl!
The Superbowl fever is still on. It has the potential of putting the IT Administrator at the brink of a soup bowl. Statistics show that...
Password Reuse, Insider Threats – The Most Dangerous IT Security Issues in 2012!
Deploying a password management solution would indeed be the best start towards information security this festive season! 2012 is fast drawing to a close. While...
Password Reuse, Insider Threats – The Most Dangerous IT Security Issues in 2012!
Deploying a password management solution would indeed be the best start towards information security this festive season! 2012 is fast drawing to a close. While...
High Profile Cyber-Security Breaches in Australia – You Might Be The Next Victim!
(Originally published in CSO, Australia) Australian media is agog about the stories of hacking by the hacktivist group ‘Anonymous’, the group that defaced several Australian...
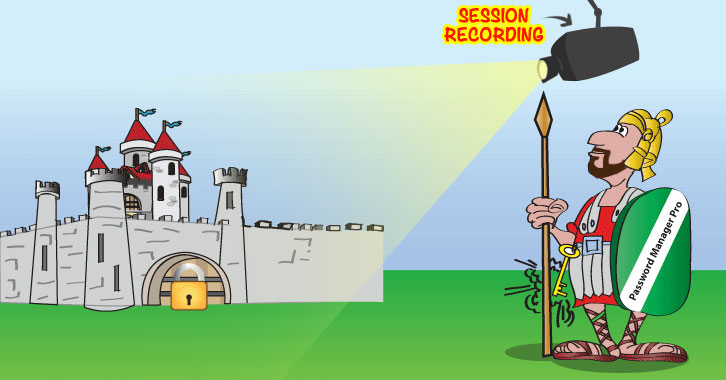
Monitoring Privileged Activities, a Crucial Aspect of Data Center Infrastructure Management
Data centers represent the nerve center of IT enterprises. With the presence of a complex mix of databases, network devices, applications and physical and virtual systems,...

Change Control Automation & Better Management of Network Assets
In IT infrastructure management, integration of tools/software with one another has always been a crucial requirement. In Network Change and Configuration Management (NCCM), which predominantly...
