The global corporate landscape is on the brink of a complete premises lockdown in light of the COVID-19 crisis. Service disruption is inevitable, and enterprises’...
Search results for: applications manager

The truth about server virtualization management: Tried and true techniques
Server virtualization management is a strategy of running multiple autonomous virtual operating systems on a single physical server. By maximizing the capacity of physical resources to optimize the...
March Patch Tuesday 2020 resolves 115 CVEs from Microsoft, and 12 CVEs from Firefox
It’s that time of the month when IT admins are glued to their systems again. Why? March Patch Tuesday is here. Microsoft has patched 115...
Microsoft’s February Patch Tuesday comes with fixes for 99 vulnerabilities
This Patch Tuesday, a total of 99 vulnerabilities have been addressed, making the February 2020 Patch Tuesday the biggest yet. As an early Valentine’s gift,...
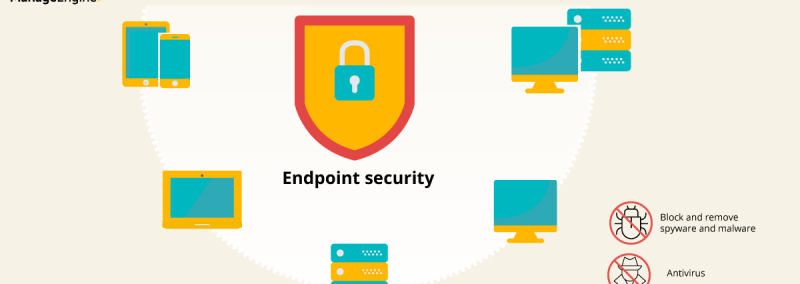
Endpoint security: The key to protecting your enterprise
To operate efficiently, businesses today use numerous devices such as laptops, desktop computers, and mobile devices. Securing all these devices—collectively called endpoints—significantly improves the overall security of...

9 essential UEM capabilities that empower your IT administration
Unified endpoint management (UEM) is an IT best practice and strategy for securing and controlling desktop computers, laptops, smartphones, and tablets in a connected, secure...
50 vulnerabilities patched in January 2020 Patch Tuesday
The first Patch Tuesday of the decade has arrived with a bang. There’s been a lot of buzz regarding essential updates that were set to...
2019 at a glance: Looking back on a journey of transformation
Mark Twain once said, “Twenty years from now you will be more disappointed by the things that you didn’t do than by the ones you did...
What is vulnerability management and why should enterprises adopt it?
In the current digital era, enterprises across the world heavily rely on information systems for day-to-day operations and for accessing business-related data. In essential institutions,...