
From exposing your network vulnerabilities to becoming a passageway for intruders, open ports can pose several risk vectors that threaten your network's confidentiality, integrity, and availability. This is why it's a best practice to close your open ports. To tackle the risks introduced by open ports, network admins rely on port scanning tools to identify, inspect, analyze, and close open ports in their networks.
Let's take a closer look at how open ports expose your network to security attacks and how port scanning tools help you reduce your network's attack surface.
A quick look into the port states
Port scanning tools use three common terms to determine the state of the scanned ports – closed, filtered, and open.
Closed ports: These network ports completely reject all the packets directed towards them and do not facilitate any incoming or outgoing traffic.
Filtered ports: The in and out traffic of these ports is regulated by network agents such as firewalls. Any traffic or packet that is not authorized by the firewall is ignored or dropped.
Open ports: A port's status is considered open when there is an application or service listening on that port and it is reachable from outside your network.
The farrago of open ports: Are all open ports dangerous?
Let's say there are 150 ports that are currently open in your network. An attacker can find them all by carrying out a port scan on your network. But does this mean that all 150 open ports are dangerous by default?
Before answering this question, we first need to determine what makes a port dangerous.Technically, a port simply being open isn't enough for a communication channel to be established. For any entity outside your network to communicate with your network ports, there needs to be an application or service listening on the port. If there is none listening, then all the packets directed to that port are automatically dropped.
Not all open ports with services listening on them expose your network to risk vectors. In fact, your network devices might have some ports such as port 21 (FTP), and port 23 (Telnet) open by default. An open port becomes a valid target for attackers if there's a network vulnerability that allows them to intrude on your system and extract critical information.
Not all services listening on a port make the port dangerous, however, any open ports that are left unmonitored might be running services that are unauthorized, misconfigured, or are easily exploitable by attackers. Attackers can run a port scan to easily identify the vulnerable points in your network, which can help them carry out a full-fledged attack on your network.
So no, open ports by themselves are not dangerous. The risk lies with the ports that have been left unmonitored and the services running on them.
The risk vectors of unmonitored open ports

Between the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), there are 65,535 ports constantly being used by services and applications to receive inbound packets and messages from outside and transmit responses, if any. When these ports are left unmonitored, the open ports and the services listening on them increase the chances of network attacks, including:
1. Malware, Trojans, and unauthorized accessWith open ports, network entities can easily communicate with the services running in your network through data packets. Malware and Trojans exploit open ports to intrude on your network by running unauthorized services on network ports. These services can only be identified by detailed scanning and continual monitoring of services running in your network ports.
2. Exposing vulnerabilities risking network confidentialityAttackers can use port scanning tools to scan and identify open ports in your network. Once the list is obtained, they can communicate with the listening services on these ports to uncover crucial network aspects such as the deployed use of the service, the software version, the underlying architecture, communication models, and so on. This exposes your network's weak spots and exploitable areas to the attacker.
3. DoS attacks hindering your network availabilityPorts are the gateway to your network. They facilitate message transfer for any entity willing to communicate with your network, and when one service is running on a port, no other service can utilize it. These factors make it important to ensure that there are enough ports available for authorized applications to communicate with your network.
If these open ports are left unmonitored, attackers can easily scan and establish communication with all the services listening on the open ports in your network. On exhausting all the available ports in your network, they can carry out attacks such as denial-of-service (DoS) attacks that interrupt your network availability and make your network unreachable.
How do port scanning tools help?
Port scanning tools are useful both to an attacker trying to breach a network and an IT admin trying to secure it. Since ports play an important role in determining when, how, and by whom your network can be accessed, it's crucial that you continually monitor them to avoid security mishaps. Port scanning tools help you with this by:
1. Automating the cumbersome process of manual port scanningManual port scanning methods such as those offered in native command line interface (CLI) tools can display an overview of the ports in your device. However, these commands are inefficient and time-consuming, making manual port scanning in enterprise-level networks impractical.
On the other hand, port scanning tools help you run organization-wide port scans within minutes. By automating the periodic scan process and eliminating the need for manually entering commands to initiate scans, port scanning tools enable network admins to easily access port availability and usability metrics.
2. Offering visibility into different aspects of the scanned network portsPort scanning tools provide you a view of what port is being used in your network, when, and how in real time. It displays to you various details about your ports such as the number of open ports, the services that are currently running, the OS type, and so on.
Advanced port scanning tools help you better analyze your network security by
quickly finding open ports in your network, the services running on them, and their response times by pulling real-time port scan statuses. It also generates a list of closed, open, or listening ports by conducting an end-to-end port scan on a range of IPs and their TCP and UDP ports. This helps you to monitor your ports in real time as well as analyze your port usage pattern to enhance your network security measures.
3. Enhancing network security with proactive scanningUsing a port scanning tool to scan your network gives you in-depth visibility of how your network devices are connected and the services running in your network. With the ability to scan and display the status of your network ports in real time, port scanning tools help you stay ahead of attackers by instantly detecting and closing open ports in your network.
Port scanning tools keep you informed about various aspects of your network ports such as which ports are open and which are closed. Since it continually scans and alerts you about the network port status, you can use these details to get an outsider's view of your network. This helps you identify and secure spots that are vulnerable to security breaches.
Getting started with port scanning: OpUtils – An advanced port scanner
If you are on the hunt for a port scanning tool that can scan, monitor, and manage your enterprise-level ports and network resources, try ManageEngine OpUtils! OpUtils is an IP address management and switch port mapping tool that enables you to conduct advanced port scans spanning across your organization-wide network.
What makes OpUtils stand out as a port scanning tool?
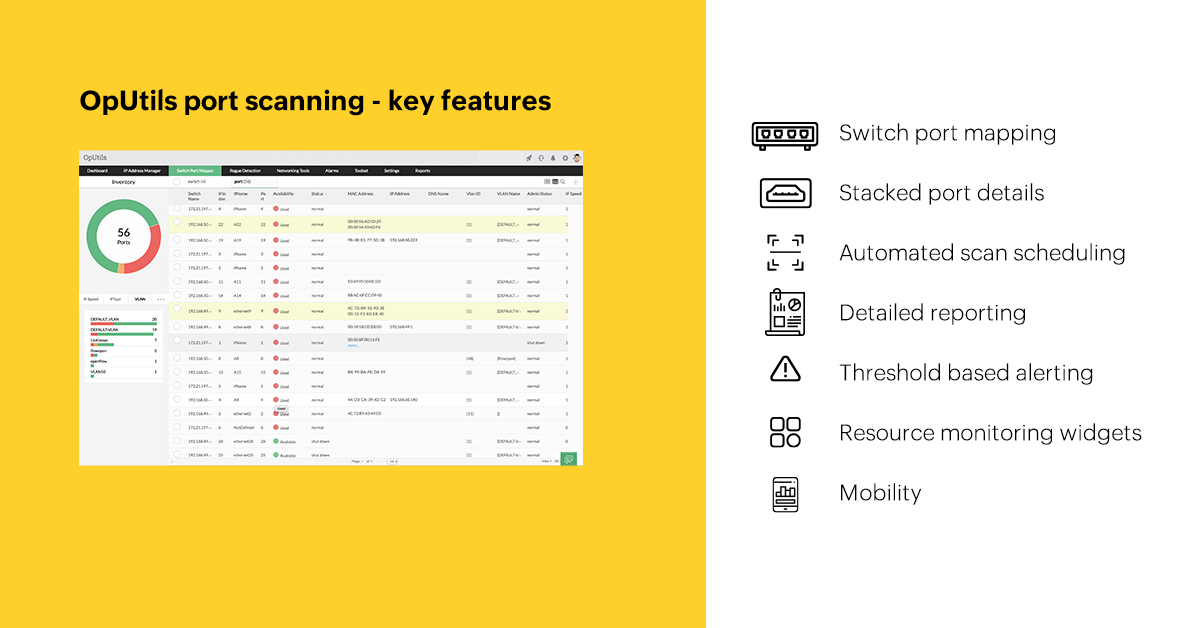
- Switch port mapping: OpUtils discovers the devices plugged into each port of a specified switch. This is useful for you to gain visibility into the IP, MAC, status, and availability of ports.
- Stacked port details: View stacked port details as well as the MAC-specific details of all connected devices.
- Automated scan scheduling: Once scheduled, OpUtils periodically scans the switches to discover new ports and report port state changes.
- Detailed reports: OpUtils automatically generates granular reports on the monitored switch ports in your network, which includes reports on port availability, usage, speed, and type.
- Threshold-based alerting: OpUtils helps you proactively monitor network ports by raising alarms if there are any changes in behavior of the network ports.
- Resource monitoring widgets: OpUtils' real-time advance port scanner has a collection of widgets that provide crucial information about the status and usability metrics of the ports at a glance.
- Restricted tool access: OpUtils provides administrator and operator roles for users.
- Mobility: OpUtils' iOS and Android mobile apps let you monitor network resources on the go!
OpUtils offers various other features such as
IP address management, which includes
advanced IP scanning,
DHCP server monitoring, rogue detection, and more than 30 networking tools including a
Wake-on-LAN tool that help network admins efficiently scan and track network resources and troubleshoot issues.
Try ManageEngine OpUtils hands on and learn how it can manage your network resources with a free, 30-day trial.
Download it now!
 From exposing your network vulnerabilities to becoming a passageway for intruders, open ports can pose several risk vectors that threaten your network's confidentiality, integrity, and availability. This is why it's a best practice to close your open ports. To tackle the risks introduced by open ports, network admins rely on port scanning tools to identify, inspect, analyze, and close open ports in their networks.
Let's take a closer look at how open ports expose your network to security attacks and how port scanning tools help you reduce your network's attack surface.
From exposing your network vulnerabilities to becoming a passageway for intruders, open ports can pose several risk vectors that threaten your network's confidentiality, integrity, and availability. This is why it's a best practice to close your open ports. To tackle the risks introduced by open ports, network admins rely on port scanning tools to identify, inspect, analyze, and close open ports in their networks.
Let's take a closer look at how open ports expose your network to security attacks and how port scanning tools help you reduce your network's attack surface. Between the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), there are 65,535 ports constantly being used by services and applications to receive inbound packets and messages from outside and transmit responses, if any. When these ports are left unmonitored, the open ports and the services listening on them increase the chances of network attacks, including:1. Malware, Trojans, and unauthorized accessWith open ports, network entities can easily communicate with the services running in your network through data packets. Malware and Trojans exploit open ports to intrude on your network by running unauthorized services on network ports. These services can only be identified by detailed scanning and continual monitoring of services running in your network ports.2. Exposing vulnerabilities risking network confidentialityAttackers can use port scanning tools to scan and identify open ports in your network. Once the list is obtained, they can communicate with the listening services on these ports to uncover crucial network aspects such as the deployed use of the service, the software version, the underlying architecture, communication models, and so on. This exposes your network's weak spots and exploitable areas to the attacker.3. DoS attacks hindering your network availabilityPorts are the gateway to your network. They facilitate message transfer for any entity willing to communicate with your network, and when one service is running on a port, no other service can utilize it. These factors make it important to ensure that there are enough ports available for authorized applications to communicate with your network.
If these open ports are left unmonitored, attackers can easily scan and establish communication with all the services listening on the open ports in your network. On exhausting all the available ports in your network, they can carry out attacks such as denial-of-service (DoS) attacks that interrupt your network availability and make your network unreachable.
Between the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), there are 65,535 ports constantly being used by services and applications to receive inbound packets and messages from outside and transmit responses, if any. When these ports are left unmonitored, the open ports and the services listening on them increase the chances of network attacks, including:1. Malware, Trojans, and unauthorized accessWith open ports, network entities can easily communicate with the services running in your network through data packets. Malware and Trojans exploit open ports to intrude on your network by running unauthorized services on network ports. These services can only be identified by detailed scanning and continual monitoring of services running in your network ports.2. Exposing vulnerabilities risking network confidentialityAttackers can use port scanning tools to scan and identify open ports in your network. Once the list is obtained, they can communicate with the listening services on these ports to uncover crucial network aspects such as the deployed use of the service, the software version, the underlying architecture, communication models, and so on. This exposes your network's weak spots and exploitable areas to the attacker.3. DoS attacks hindering your network availabilityPorts are the gateway to your network. They facilitate message transfer for any entity willing to communicate with your network, and when one service is running on a port, no other service can utilize it. These factors make it important to ensure that there are enough ports available for authorized applications to communicate with your network.
If these open ports are left unmonitored, attackers can easily scan and establish communication with all the services listening on the open ports in your network. On exhausting all the available ports in your network, they can carry out attacks such as denial-of-service (DoS) attacks that interrupt your network availability and make your network unreachable.