The Black Hat USA 2013 conference, which kicks off tomorrow in Las Vegas, brings together the brightest minds in IT security each year — those who are...

IT outsourcing: When outsiders become insiders, how do you ensure information security?
Organizations outsource a part or whole of their IT services to third-party service providers for various reasons, such as cost savings, leveraging outside expertise, need...
Security Gaffes You Might Have Missed So Far This Year
If you can believe it, 2013 is already halfway over. With summer here, businesses everywhere are feeling the heat in their IT organizations – as they...
If Big Data’s too scary, try Little Data (it’s free)
Here are some stats that will blow your mind: Every minute of every day, 48 hours of video content is uploaded to YouTube, Google receives...

$45 million ATM heist turns focus again on insider threats, controlling privileged access!
New wave of cyber-attacks on banks lend credence to the belief that insider threat is getting complex and cyber-criminals are increasingly targeting to siphon-off the...
Could Your Jewelry Stop Hackers?
Google has been talking about an innovative idea to replace passwords with jewelry — that’s right, jewelry. Actually, the enabling technology could be hidden in jewelry,...
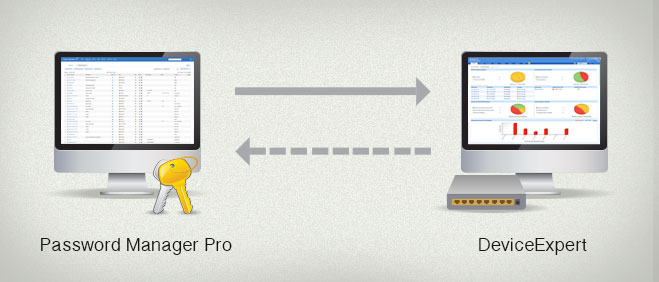
Why should you care about streamlining the management of network device configs and passwords?
Enterprises depend on network availability for business continuity and network configuration data lies at the core of enterprise network administration. Network device configurations contain access...
Password Manager Pro Consolidates Leadership in Privileged Identity Management
First some statistics: Global customer base grew by 45% during 2012; Grew 61 percent in Germany; Netherlands 52 percent; Australia 50 percent; Canada, UK and...

