As a security professional, which do you fear more: 1) explaining to your boss or CEO that your enterprise’s files are no longer accessible because...
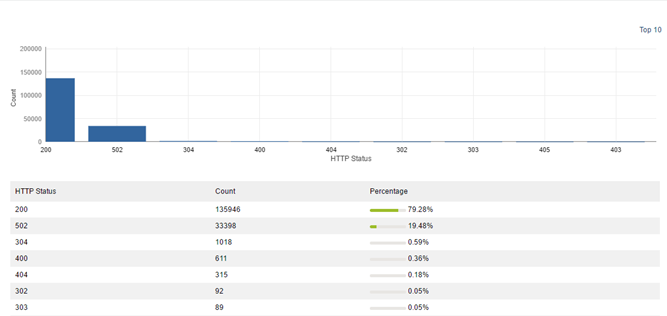
Log management and SIEM fundamentals: Comprehensive log collection and auditing
The first step in SIEM is collecting log data. Log data, as we saw in part 1, is what drives any SIEM solution. A SIEM...
Log management and SIEM fundamentals: Getting started
Cyber attacks and network breaches can bring even the largest organizations to their knees. Recently, of course, we had the WannaCry ransomware attack, which not...
Why privilege misuse is still a serious security risk for enterprises
The 10th installment of Verizon’s annual Data Breach Investigations Report (DBIR) came out in April 2017. The DBIR does a lot for the public by providing...

Will you survive the certificate war between Google and Symantec?
Google recently accused Symantec, one of the most prominent Certificate Authorities (CAs), of violating the trust internet users place in encrypted web communication. In his...
Kick-starting our free, online Log360 and ADAudit Plus workshop series
Security administrators are obviously concerned about external security threats, but did you know that internal threats can be just as dangerous? Sure you’ve got a...
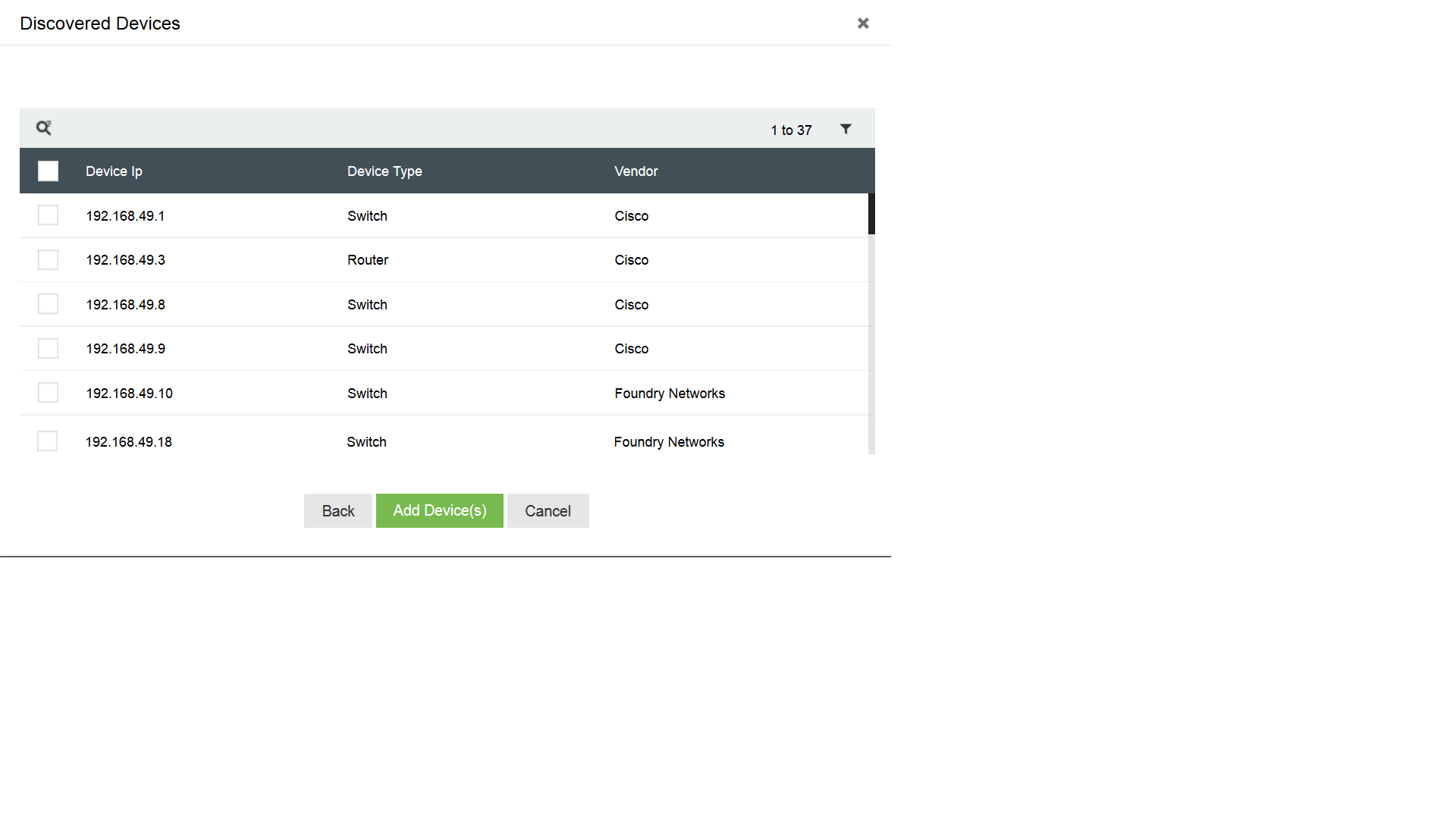
Could adding devices for log collection be any easier?
In December, we released EventLog Analyzer 11.3, which automatically discovers Windows devices from Active Directory and workgroups. This greatly simplifies the process of configuring Windows...

Breaking SIEM and network security stereotypes
Whenever we see the word SIEM, we can’t help but picture something really complex—a huge network, a big organization, advanced attacks, and a lot...


