Google recently accused Symantec, one of the most prominent Certificate Authorities (CAs), of violating the trust internet users place in encrypted web communication. In his post in Google Groups on March 23, 2017, Google engineer Ryan Sleevi alleged that Symantec mis-issued roughly 30,000 SSL certificates over a period of several years. In an effort to strengthen website security, Google has considerably reduced the trust they place on Symantec certificates. In the midst of the certificate war between Google and Symantec, organizations cannot afford to ignore browser security warnings, as a website labelled potentially insecure by Google Chrome is going to drastically reduce customers’ trust.
Conflict over trust.
SSL certificates form the backbone of internet security, and the CAs that issue them represent the degree of trust users place in website communication. Google claims they have been investigating a series of improperly validated certificates from Symantec since January, initially discovering a set of 127 mis-issued certificates. But over the course of their investigation, the number of mis-issuances grew to nearly 30,000, spanning several years. It’s a serious allegation that completely undermines the trust users can place on encrypted web browsing.
Google has proposed to remedy the situation by distrusting Extended Validation (EV) certificates issued by Symantec for at least a year. They also stated that the accepted validity period for all Symantec certificates will be gradually reduced to nine months.
What does this mean for your organization?
Regardless of the industry you are in, your website is an interface that represents your organization to customers. Ensuring users perceive your website as secure is important for instilling trust in your customers. Considering Google’s severe restrictions against Symantec certificates, organizations must take proper steps to replace their vulnerable Symantec certificates with new certificates to avoid browser security warnings on their websites.
Are you resilient to CA issues?
Symantec has acknowledged that some certificates were mis-issued and has proposed a series of remedial measures after seeking feedback from its customers on the compatibility and interoperability issues that could arise from the implementation of Google’s proposal. As part of these remedial measures, Symantec will conduct periodic audits of its issued certificates, allow third parties to audit its certificates, and shorten its certificate validity period to three months.
All these measures call for certificate life cycle automation. Although SSL certificates form the bedrock of website security, most organizations lack the agility to respond to CA issues of this scale.
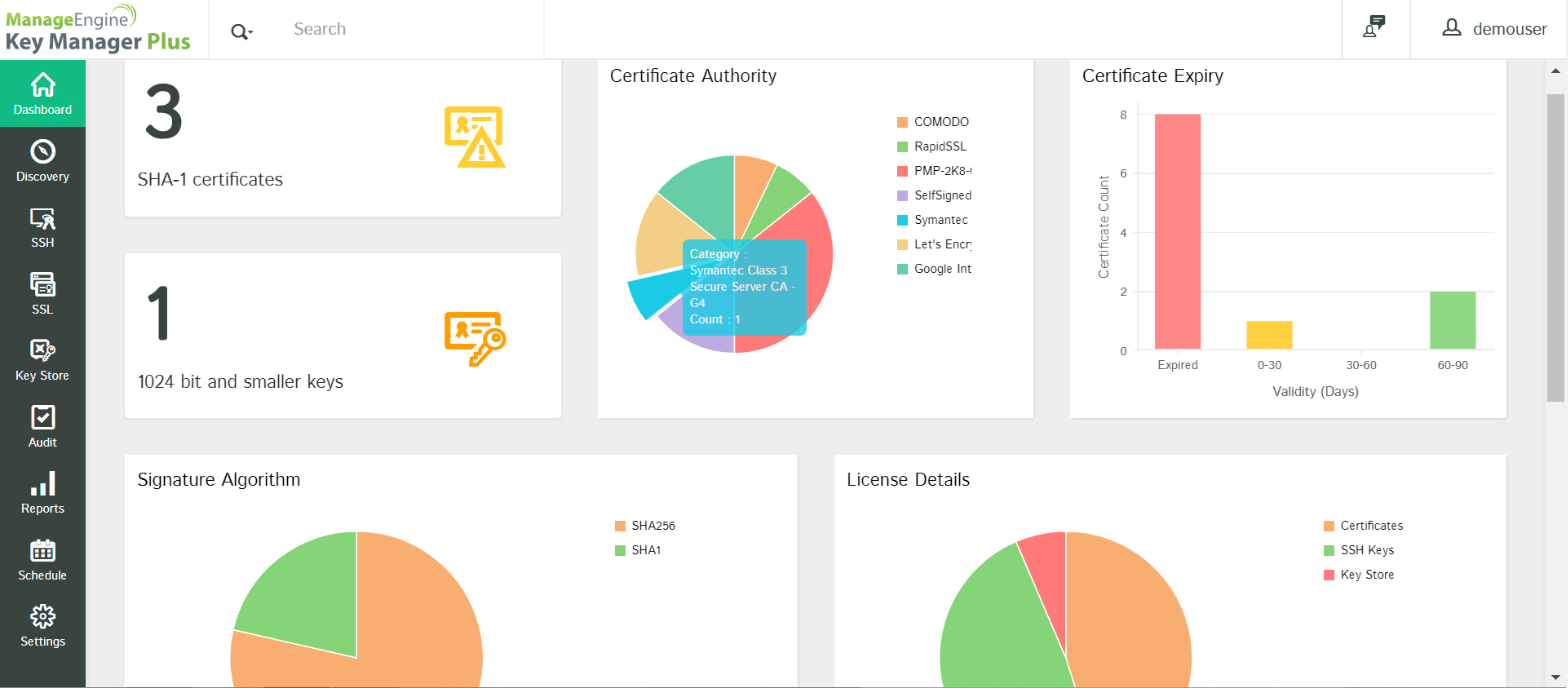
Key Manager Plus helps you react to such CA issues with ease by giving you complete visibility into your SSL environment. Follow these three simple steps to protect your organization from the Symantec certificate fallout:
Filter out all Symantec certificates:
First, you have to scan your network and isolate all the Symantec certificates. Key Manager Plus’ discovery tool helps you find all the Symantec certificates in your environment, displaying them all in a single window.
Replace old certificates:
Once you have all the Symantec certificates in one place, you can opt to swap old Symantec certificates with new ones. You can also request new certificates from other CAs by using the certificate request tool in Key Manager Plus.
Deploy new certificates:
Once you’ve obtained certificates from various CAs, consolidate and deploy them on your respective domain servers directly from the Key Manager Plus certificate repository.