Mitigating rogue devices with OpUtils: What you need to know

Over the past few years, IT companies adopted IoT, wireless and hybrid networks to stay competitive and to meet the demands of their clients. Among these networks, wireless networks are the most common and the most vulnerable to cyberattacks as hackers constantly try to penetrate them.
A cyberattack is initiated by planting a rogue device in your organization's network. A rogue device is an unauthorized device that can steal your company's valuable information, induce malware, and mess up any solutions that protects your network. It is crucial to detect rogue devices and mitigate them before they can cause damage to your organization's reputation.
Rogue device detection and prevention is a challenge for enterprises with expanding IT footprints. It is essential to deploy a tool that detects and keep rogue devices in your network under control.
Introducing ManageEngine OpUtils, a powerful rogue device detection solution that integrates with IP Address Manager, Switch Port Mapper, and other networking tools to provide you with complete control over your network.
In this blog, we'll see how you can use OpUtils to secure your network from rogue devices and cyberattacks.
Detecting rogue devices made easy with OpUtils

The first step to detecting rogue devices is to identify and track the devices in your network. This process starts with discovering all your devices, subnets, DHCP servers, and switch ports in the OpUtils console. After discovery, OpUtils automatically detects rogue devices, marks them as rogue, and prevents them accessing your network.There are three major steps required to ensure your dynamic network is rogue-free. They are:
- Scanning your network periodically.
- Closing all the TCP connections, when not in use.
- Immediate alerting.
Scanning your network periodically: With OpUtils' rogue device module, you can schedule scans to run periodically. This helps you prevent rogue devices from having unrestricted access to your organization's network.
Closing all the TCP connections, when not in use: Closing TCP connections helps you filter the traffic that's harmful to your devices. OpUtils tracks devices, and the services running on them. This data helps you close unwanted connections and keep your network rogue-free.
Immediate alerting: If a new device is discovered in your organization's network, immediately alerting IT administrators is imperative. With OpUtils, you can configure alerts to advise you when a device or port is discovered into your network via email or syslog.
Simplify rogue device prevention with OpUtils
With your network catering to the multitudes of devices and ports, it's advisable to take a holistic approach to prevent and mitigate rogue devices. You can prevent rogue devices from your network by following these three simple steps:
- Identifying and marking authorized and unauthorized devices
- Establishing access controls for your network
- Continuously monitoring devices connected to your network
Identifying and marking authorized and unauthorized devices: OpUtils' rogue device module automatically identifies and marks the potential rogue devices in your network. It's a best practice to track the authorized and unauthorized devices, and block the unauthorized from having access to your organization's network.
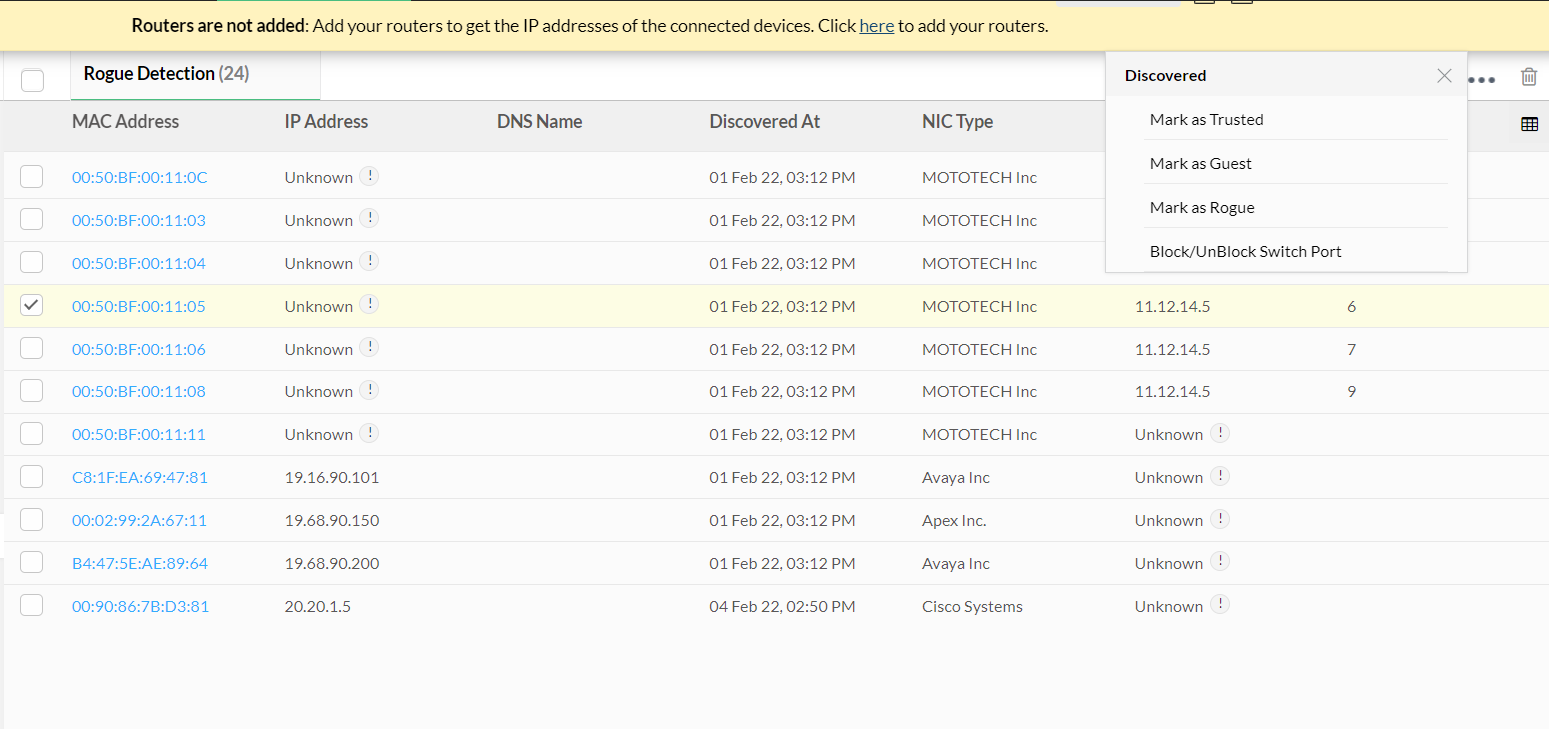
Establishing access controls for your network: Identifying devices that have administrator, user or moderate access is crucial to keeping your good devices from going rogue. OpUtils offers role based user access control (RBAC) which enables you to provide more streamlined network access for the devices connected to your corporate network.

Continuously monitoring devices connected to your network: As network compliances keep changing, and new devices are discovered from periodic network scans, continuously monitoring devices helps you track known devices, and spot any unknown rogue devices. OpUtils persistently monitors all your devices which are discovered into its console.
Choosing a rogue device detection tool you can trust
There are plenty of rogue device detection tools on the market, but most of these tools do not have the ability to scale with your dynamic, and growing network. They often provide limited visibility (performance, and capacity) for the devices connected to your network. Also, it might not provide you with proper network access controls which often leads to misuse of the enterprise networks using vulnerable devices.
ManageEngine OpUtils, a trusted rogue device detection tool, is an ideal choice for enterprise networks.
OpUtils' Rogue Device Detection module: What does it provide?
OpUtils' rogue device detection tool features a wide range of capabilities that provide holistic visibility into your organization's network. Here's how:
- Unlike other rogue device detection tools, OpUtils' rogue device module is integrated with IP Address Management (IPAM) and Switch Port Mapper, which enables maximum control and visibility over your network.
- OpUtils restricts access to your guest devices after a scheduled period.
- With OpUtils, you can monitor and manage devices, and the services running on it in real time.
- This solution provides the ability to mark rogue, trusted and guest devices at your convenience, this allows your network administrators to have more control.
- OpUtils provides Block and UnBlock switch ports at your convenience.
Interested in OpUtils Rogue Detection module? Schedule a live demo today with our product experts to get your hands on the best Rogue Detection tool. Or, download a 30-day free trial of OpUtils, and get started now.
Want to know more about how you can detect and prevent rogue devices from your network? Read our e-book, Rogues on the rise - Is your network secure enough?