How does Amazon VPC work?
Amazon Virtual Private Cloud (VPC) is a commercial cloud computing service that enables users to create a logically isolated section within the AWS Cloud. Users can deploy AWS resources in a self-defined virtual network within this isolated section. In essence, it enables customers to build resources within a private, separated area of the AWS cloud, such as databases, Elastic Compute Cloud (EC2) instances, and other AWS services.
AWS offers VPC to enterprises as a way to improve cloud security. By using this technology, businesses can add additional security layers to their cloud resources by launching them into a private virtual cloud environment.
Each Amazon account created after 2013 comes with a preconfigured default VPC. This means users can launch instances straight away without having to configure anything. The default VPC is preconfigured with:
A size /16 IPv4 CIDR block that provides up to 65,536 IPv4 addresses.
A size /20 subnet in each availability zone that offers 4,096 addresses per subnet.
An internet gateway connected to the VPC.
A default security group and a default network access control list (NACL).
Architecture and working of VPCs
The VPC architecture consists of:
Foundation and framework: The AWS cloud's core infrastructure serves as the basis for Amazon VPC. An organization's cloud resources require network isolation and segmentation, which the VPC provides as the framework.
Subnets: You can segregate your resources logically in Amazon VPC by creating subnets. Each subnet has a distinct function. For example, you might have a subnet for web servers, another for application servers, and a third for databases.
Access control: Security groups and NACLs are used in Amazon VPC to manage access control. These act as virtual gates, controlling traffic flow in and out of subnets and instances based on defined rules.
Utilities and services: Internet gateways for internet connectivity, network address translation (NAT) gateways for outbound internet access, VPN connections for secure communication, and direct connect for dedicated network connections to your on-premises infrastructure are just a few of the services and tools that AWS offers with Amazon VPC to support your virtual infrastructure. For example, you can use an internet gateway to set up internet access with a VPC, allowing resources inside your VPC to connect to the internet privately or exchange data.
Security and monitoring: Network firewalls, encryption, monitoring tools, and logging capabilities are some of the security features in Amazon VPC that guard your virtual environment from unauthorized access and malicious activities.
Extension and renovation: You can scale and modify the network infrastructure with Amazon VPC as needed to adapt security policies, integrate new AWS services, and add or delete subnets with ease to meet evolving business needs.
Before we delve deeper into the way it works, let's understand the key concepts that are necessary for Amazon VPC to operate correctly.
Default VPC
Every region has a default VPC set up when you register an AWS account. With this ready-to-use environment, you can begin deploying instances immediately. Amazon EC2 is the service used to create and run virtual machines in the cloud. Each EC2 instance you deploy in the default VPC has a private and public IP address, facilitating communication between the instances and the internet with the help of AWS's infrastructure.
Generating extra VPCs
You can divide your network into different segments by creating more VPCs. For example, you can keep distinct VPCs for development and production environments. The isolation and security of your different environments are guaranteed by the complete independence of these extra VPCs from any other VPC in your network.
A new VPC is launched with an IP address range, router, NACL, default security groups, and route table of its own. Moreover, you can increase the number of subnets, security groups, network ACLs, etc. based on the needs of your project.
While the default VPC is great for launching new instances, IAM policies do not apply to it. Creating a VPC allows users to define and customize their virtual network so it abides by the organization's IAM policies, thereby making it more secure and reliable.
Configuring the subnet
Subnets are a range of IP addresses in the VPC. You can establish one or more subnets inside your VPC. Subnets are not allowed to navigate availability zones; they must all reside fully within one availability zone. Subnets can be defined for various uses. For example, private subnets for resources that shouldn't be directly available from the internet and public-facing subnets for resources that are accessible from the internet.
Defining route tables
Route tables are the backbone of network traffic flow. They are a collection of rules, or routes, that specify the direction in which network traffic is to be sent. A route table, which manages the subnet's routing, needs to be connected to each subnet in your VPC. Although you can link more than one subnet to a single route table, each subnet can only have one connected route table at a time.
Internet gateway
An essential element that gives network traffic a route between your Amazon VPC and the internet is an internet gateway. It's an AWS-managed component designed to be highly available and scalable, ensuring reliability and performance.
The internet gateway plays two critical roles. First, it serves as a route through which your VPC can communicate with the internet. Second, it performs NAT for instances that have been assigned public IPv4 addresses.
The internet gateway is essential in two ways:
It acts as a conduit for communication between your VPC and the internet.
It handles NAT for instances that have public IPv4 addresses assigned to them.
An internet gateway must be attached to your VPC to enable internet access within it. Also, you must make sure that instances have publicly routed IP addresses (public or elastic IPs) and change your subnet's route table to direct traffic to the internet gateway.
VPN connection
Secure internet communication between your on-premises network and your virtual private network (VPN) is made possible by a VPN connection. By securely extending your current network infrastructure to the AWS cloud, you can seamlessly integrate AWS-hosted resources and applications with those in your on-premises data center or office.
VPC peering
VPC peering is a networking connection that allows you to privately route traffic between two VPCs, either inside the same region or across separate AWS regions. Peer VPC instances are able to communicate with one another much like they would if they were on the same network.
Transitive peering connections are not supported by VPC peering. Suppose there is a VPC peering connection between VPC A and VPC B as well as between VPC A and VPC C. You cannot route traffic from VPC B to VPC C through VPC A. You need to establish a VPC peering connection between VPC B and VPC C to transport traffic between them.
Refer to Fig. 1 below, which depicts the way the components mentioned above work together.
 Figure 1: Amazon VPC architecture and working.
Figure 1: Amazon VPC architecture and working.This VPC is fully self-contained and isolated. It is a logical constraint that establishes a shared networking and security boundary for your applications and services.
The instances will only be able to communicate with each other inside the VPC. You have complete control over how the instances access resources outside of the VPCs.
In this case, a public IP address is assigned to the instance and an internet gateway is attached to the VPC to provide internet connectivity.
The public subnet will always have a route to get out to the internet. Here, for example, you can put servers that would host public-facing webpages.
On the other side, the private subnet doesn't have the route. For example, you can put your critical databases here. This will provide an extra layer of security protection from the outside world.
You can also connect the VPC to your own corporate data center using a site-to-site VPN connection, making the AWS cloud an extension of your data center.
A VPC peering connection must be established to route traffic discreetly between two VPCs and enable instances in either VPC to communicate with one another as though they were on the same network.
Since each VPC spans a single area, we can be certain that all of the instances within it are physically located there and that there is no connection outside of the region between them.
However, do you ever wonder how the private subnet gets to the internet without the route?
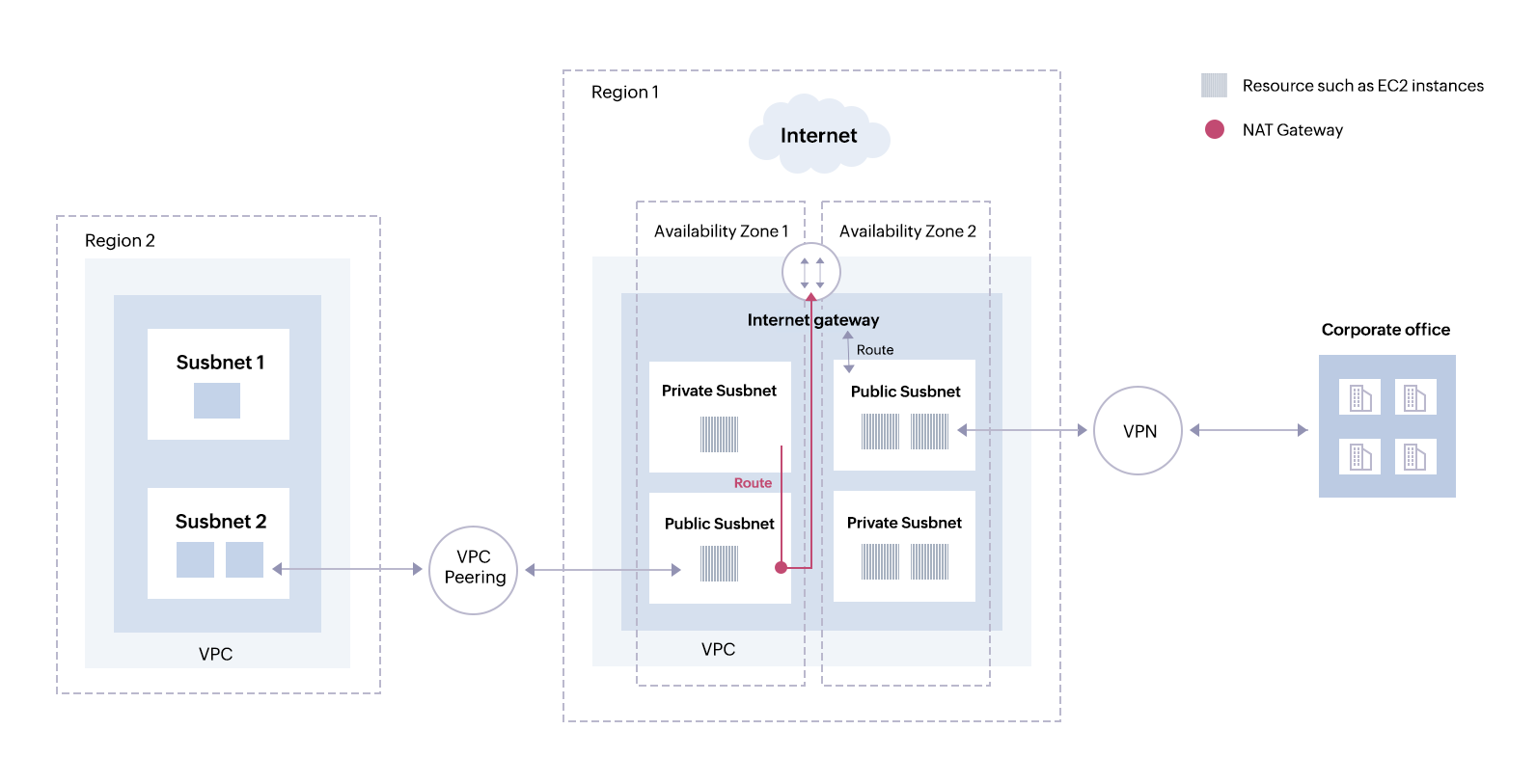 Figure 2: NAT gateways in Amzon VPCs.
Figure 2: NAT gateways in Amzon VPCs.In these situations, you add a route from your private instance to a NAT gateway that has been established in the public subnet. Next, add a NAT gateway to the internet gateway. Your resources in the private subnet are now able to access the internet (refer to Fig. 2).
The two ways that you can control the flow of traffic are as follows:
NACLs: Stateless firewalls that regulate traffic at the subnet level are called NACLs. They are optional, but NACLs are useful for creating rules that allow or deny communication to and from subnets inside your VPC. These rules can only be used with IP addresses to either allow or deny the IP address.
Security group: Security groups manage traffic for one or more instances by functioning as a virtual firewall. Rules that permit traffic (only allow) to and from instances can be defined depending on parameters like the protocol, port, and source and destination IP addresses.
Importance of securing and monitoring Amazon VPC
The primary reason for using Amazon VPC is security. You may securely deploy AWS resources with a VPC, a separate section of the AWS public cloud. Amazon VPC assists you in lowering the expenses related to a private cloud, much like many other AWS features do. One of the things you should become familiar with right away if you want to use AWS for your organization is Amazon VPC. Despite the fact that Amazon VPC offers more protection than conventional networks, it still requires monitoring and security measures. Amazon VPC is a target for many cybercriminals.
An unprotected VPC may be vulnerable to online attacks. By keeping an eye on Amazon VPC, you can proactively find and fix problems, maximize resource utilization, and ensure compliance with security and regulatory standards. Here are some other reasons why maintaining VPC security is critical for strengthening your network infrastructure:
Enhancing performance: Monitoring the essential components of your Amazon VPC allows you to obtain insights into the performance of your network infrastructure, identify and address any issues early on, and optimize the utilization of resources for improved performance. The components that need to be monitored include network traffic, load balancers, NAT gateways, VPN flow logs, VPN connection performance, and subnet performance.
Resource utilization: Tracking the resource usage within your VPC, including EC2 instances, databases, and other services, aids in resource allocation optimization and the identification of cost-saving opportunities.
Security and compliance: Identifying potential security breaches, unauthorized access attempts, or unusual activities by monitoring network traffic and access patterns are necessary to maintain the security and compliance of your infrastructure.
Troubleshooting: Monitoring network throughput, latency, and error rates will help you quickly troubleshoot and resolve issues before they impact the performance or availability of your applications.
Cost management: Identifying unused resources by gaining visibility into resource usage will help you optimize the infrastructure to cut down on unwanted expenses spent within your VPC.
To learn more about the need for monitoring and securing Amazon VPC, check this page.
If you want to know more about Amazon VPC, refer to the pages below: