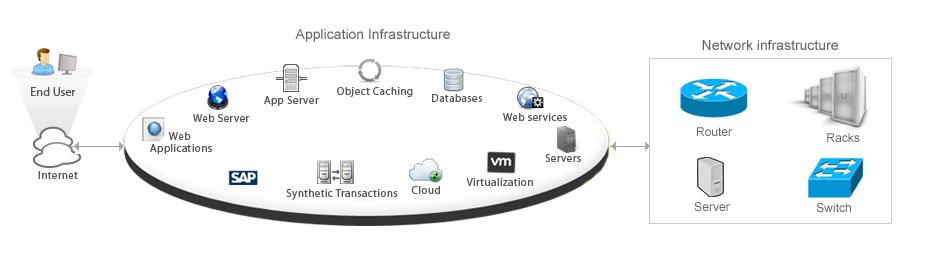
In today’s complex business environment, the first question thoughtful IT leaders ask when considering any new IT investment or change is, ‘How will it impact the business?’ That the business depends on well-managed IT is well understood. What is less well understood is how an IT organization can manage an infrastructure that is growing ever more complex. It’s not just the network infrastructure that IT teams need to consider; it’s not even the increasingly complex application infrastructure that stands between the physical network infrastructure and the users. The challenge today involves the effective management of both these infrastructures as well the interplay between them — and it’s the interplay between them that poses the greatest challenge. Application-aware network performance management (AA-NPM) tools can help you overcome that challenge. What is AA-NPM? These days, before an application appears in front of an end user, it may pass through numerous infrastructure components, as shown in the diagram below: Traditional or stand-alone application performance management (APM) tools provide visibility only into the middle component group, the application infrastructure. They typically support auto-discovery of all the applications in the networks, transaction analysis, application usage analysis, end-user experience analysis, and more. They also provide the basic functions to monitor the health and performance of all configured application infrastructure assets. But APM tools do not provide insight into the network infrastructure itself. Typically, network infrastructure managers rely on separate network performance management (NPM) tools for fault management, device monitoring, capacity planning, interface traffic analysis, configuration management and those sorts of tasks. The problem with a management approach that relies on two separate tools is that neither of these tools is designed to facilitate the management of the interplay between these environments...
Why should you care about streamlining the management of network device configs and passwords?
Enterprises depend on network availability for business continuity and network configuration data lies at the core of enterprise network administration. Network device configurations contain access...
Who moved my data?
Remember Hansel and Gretel? They could trace their way back home because of the pebbles they dropped as a trail. It was a great story...
It is hard to hit a changing target!
We have seen, heard and experienced various kinds of mobile devices; mobile phones, tablets, the old palmtops and any others you can think of. It’s...
Triple Recognition for Password Manager Pro this year! World’s Mightiest Enterprises Repose Trust!
The IT divisions of three of world’s largest organizations – software maker, retail chain and virtualization platform provider have deployed Password Manager Pro to manage...
Password Reuse, Insider Threats – The Most Dangerous IT Security Issues in 2012!
Deploying a password management solution would indeed be the best start towards information security this festive season! 2012 is fast drawing to a close. While...
Password Reuse, Insider Threats – The Most Dangerous IT Security Issues in 2012!
Deploying a password management solution would indeed be the best start towards information security this festive season! 2012 is fast drawing to a close. While...
Can your organization be Hack Immune?
This past few months witnessed a record breaking global level of malware threats and APTs (Advanced Persistent Threat) that put the mightiest of Enterprises’ security...
Cyber Monday Lessons: Apple Can Get Away with Outdated Mobile Sites…But You Can’t
Yesterday, I connected to Apple’s website on my iPhone, only to discover that the undisputed leader of all things mobile didn’t have a mobile-friendly website. Well to be...