Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we highlight the rising...
Secure access to multiple enterprise applications! ADSelfService Plus makes it twice as safe.
Enterprise applications have become an integral part of a tech user’s life. Although the utility and user experience of these applications have been getting better, the risk...
Simplifying security auditing, Part 4: Securing web servers
Web servers are front-end facing applications that are vital for the daily operations of businesses. They are subject to attacks such as SQL injection, malicious URL...
Five worthy reads: Rise of the no-collar culture
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we look into the...

Ghostscript vulnerability leaves enterprises waiting for a security patch
It often feels like there’s no end to software vulnerabilities and exploits. With every step towards technological advancements, another threat turns up. This is especially frustrating for enterprises,...
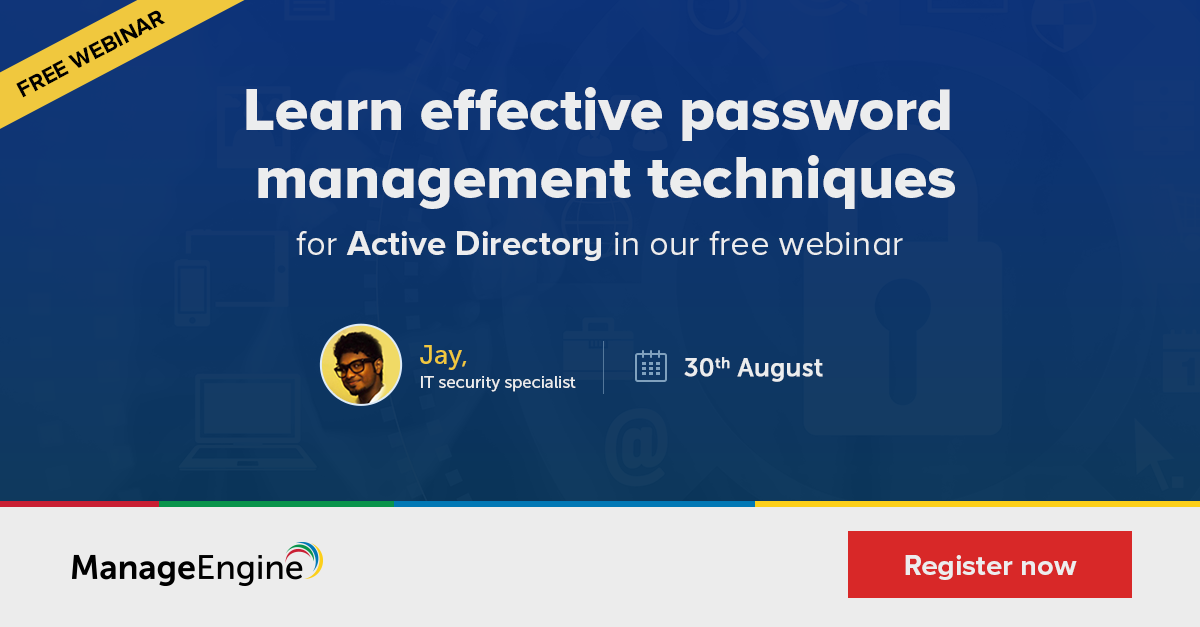
Effective password management techniques for Active Directory [free webinar]
Passwords have formed an integral part of Microsoft Active Directory since its inception. From then on, most organizations have relied on Active Directory to manage their IT...
Simplifying security auditing, Part 2: Auditing systems that store sensitive data
In part 1, we looked at an overview of auditing servers. In this blog, we’ll discuss which events you need to audit in your databases and file servers where...
Five worthy reads: The “edge” is near!
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we explore how edge computing...

Lessons from one of the first major data breaches in a post-GDPR Europe
As the buzz around the GDPR and its implementation begins to settle down, we’re starting to see how this regulation is changing the way business respond to breaches. One of the first victims of...
