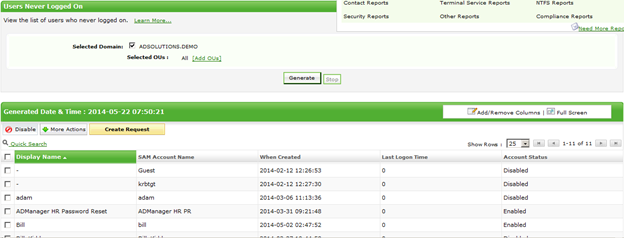
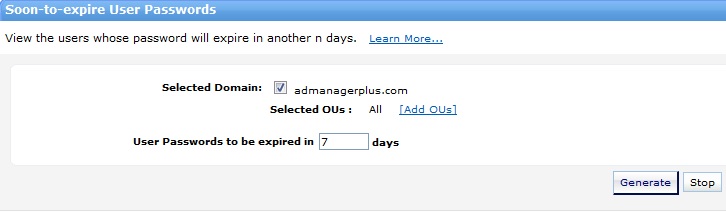
Every Active Directory installation has one common issue. Every installation has one or more users that were created for a project, new employee, returning employee,...
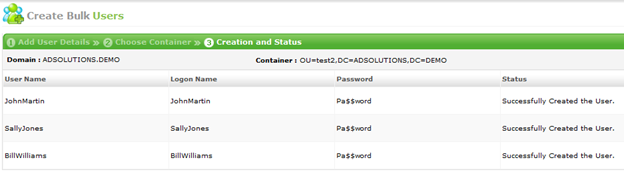
ADManager Plus: Creating Users in Bulk by Importing a CSV File
It is extremely common for a company to hire employees in mass. It might be a school with a new school year, a corporation hiring...
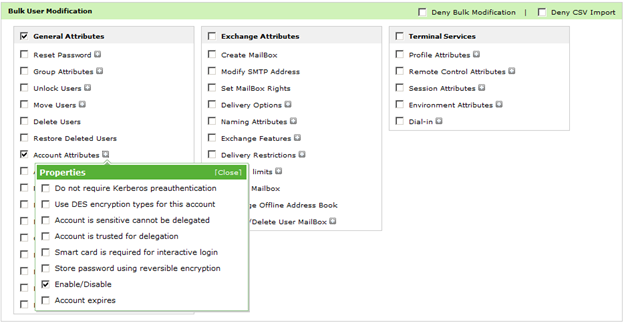
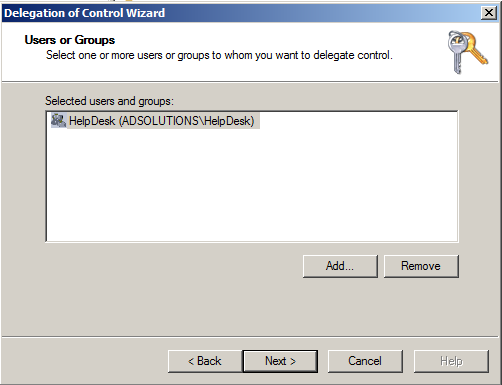
Delegating “Disabling of Active Directory Users” to a Department Manager
We all know it happens the exact same way each time. There is a user in a department, or maybe a department of users, that are going to be terminated. The...
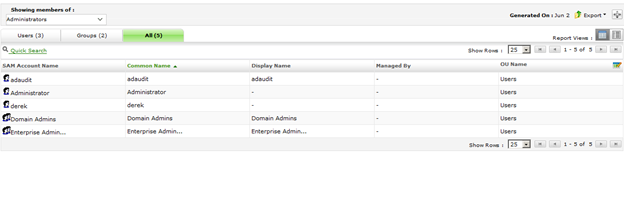
Going Deep With Nested Group Audits
It is one of the top three most complex areas of auditing: nested groups! You know, you find a group listed on an access control...
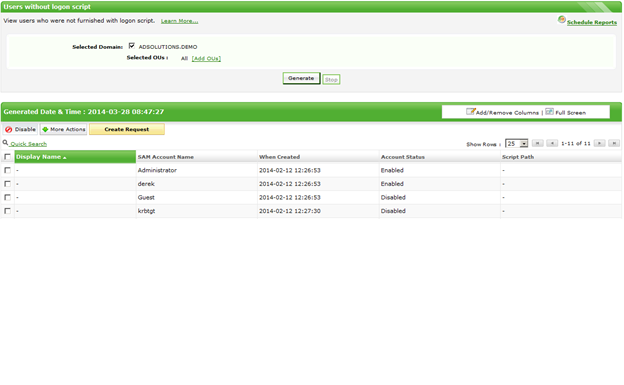
Tracking Down Users with no Logon Script Configuration
When users are created in Active Directory, the logon script configuration often fails to get configured. This can be due to a lack of process, a lack of restraint (i.e.,...
Happy Turkey Day!
A successful business, like ours, can never be a one-person show, but a star-studded, mega budget gamble! So, this Thanksgiving, we decided to thank the...