The “right to be forgotten” is one of the new rights consumers will have under the CCPA. “I’d like to pay with my credit card.”...

Five reasons to choose Log360, part 5: Integrated compliance management
So far in this blog series, we’ve seen how Log360 is simple to get up and running, allows you to receive a central view of...
Five reasons to choose Log360, part 4: Advanced security features
Part two and part three of this blog series gave a detailed look at Log360’s in-depth auditing capabilities, while part one explained how easy the...

Five reasons to choose Log360, part 3: Comprehensive network auditing
In the previous post, we discussed the various environments that Log360 helps you audit and secure. Having established the ease of Log360’s use and the...

Five reasons to choose Log360, part 2: Multi-environment support
In the previous post of this series, we looked at how easy it is to get Log360 up and running due to its various deployment...

Five reasons to choose Log360, part 1: User-friendly deployment and UI
SIEM solutions are a must-have in any organization’s security toolkit. They allow you to analyze events from your network, gain actionable insights into network activity,...
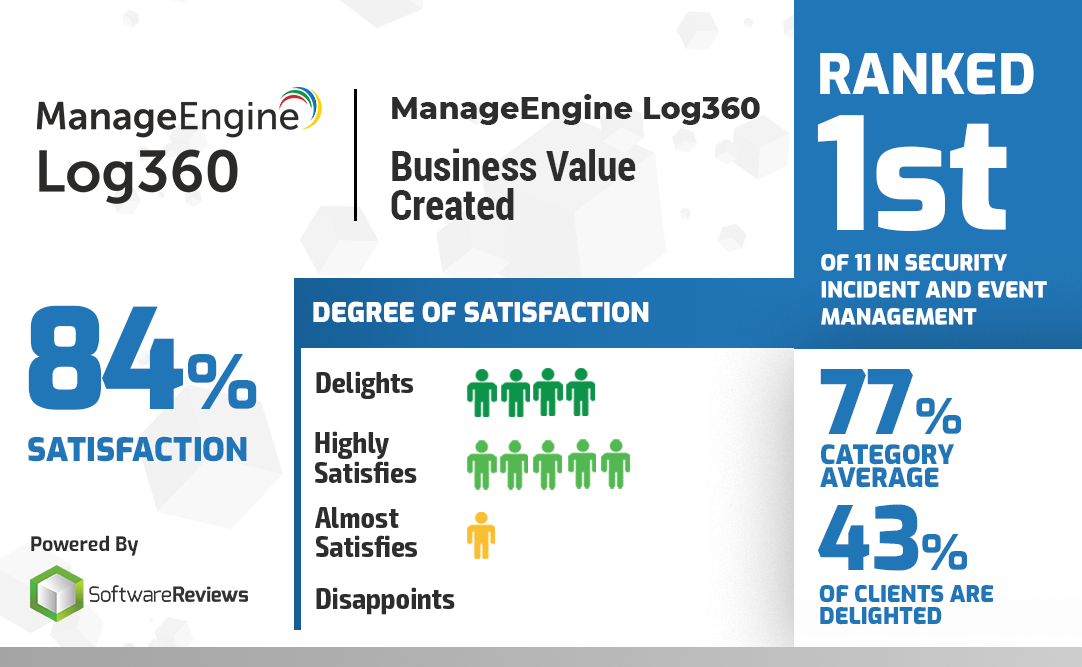
Log360 named a Champion in Software Reviews’ 2019 SIEM Customer Experience Report
Software Reviews, a division of Info-Tech Research Group, has named Log360 a Champion in its recent Customer Experience Report. Out of eleven software vendors evaluated...

Free webinar on accelerating threat detection and response with user and entity behavior analytics (UEBA)
Most security personnel take measures to combat threats from outside the network. However, what happens when the threat originates from the place you least expect–your...

Conquer it with correlation—Part 3: Cryptojacking
In the previous posts of this blog series, we discussed advanced persistent threats and data breaches, highlighting the importance of data security in today’s times. In the...

