Staying ahead of LockBit ransomware attacks

LockBit is a Ransomware as a Service (RaaS) provider accountable for most LockBit ransomware attacks in 2023. The LockBit RaaS group came into existence in 2019 and has posed great challenges to security experts ever since. A recent report states that LockBit accounted for over one-third of all ransomware attacks in the latter half of 2022 and the initial quarter of 2023. With LockBit ransomware threat actors working around the clock to upgrade and intensify their attacks, it has now evolved to be one of the most notorious ransomware variants.
Timeline of LockBit evolution
Launch year | Variant name | Description |
September 2019 | ABCD ransomware |
|
January 2020 | LockBit |
|
June 2021 | LockBit Red |
|
October 2021 | LockBit Linux-ESXi Locker version 1.0 |
|
March 2022 | LockBit Black |
|
January 2023 | LockBit Green |
|
April 2023 | LockBit on macOS |
|
The future
Ransomware attacks are never ending, with RaaS providers constantly upgrading their strains to meet technological advancements. As security experts, it's imperative that you stay ahead of attackers and prevent such attacks.
One of the solutions is to integrate the MITRE ATT&CK framework with your organization's network security framework to map attacks like LockBit. MITRE ATT&CK is a knowledge base that helps you foresee an attack from an attacker's point of view. By understanding the perceptions of an attacker, you can predict and prevent potential attacks and their consequences. You can find more information about MITRE ATT&CK in our e-book.
Mapping the LockBit attack scenario with MITRE ATT&CK
The LockBit ransomware gains initial access to the network via phishing emails, brute-force attacks on RDP accounts, or by exploiting vulnerable applications.
It then infiltrates deeper into the victim's network and prepares the environment to stage the attack using post-exploitation tools that use Windows PowerShell or the SMB protocol for execution.
It deploys the ransomware payload and infects the first host. This single infected host automatically spreads the infection to multiple devices by sharing an infected script to all compromised devices using the SMB protocol.
All the files on the infected devices get encrypted, and a ransom note appears on the victims' compromised devices.
The files can be decrypted only with the help of LockBit's proprietary decryption tool.
By studying the line of action of LockBit ransomware, a joint advisory by the CISA concluded the following tactics and techniques to be the most predominant in a LockBit attack. The tactics and techniques are as shown in Table 1.
Tactic | Techniques |
Initial access |
|
Execution |
|
Exfiltration |
|
Impact |
|
Table 1: Tactics and techniques used in a LockBit attack
Now the question is: How can you implement the MITRE ATT&CK framework in your organization?
The answer lies in a SIEM solution like ManageEngine Log360 that provides predefined detection rules, alerts, and reports pertaining to the MITRE ATT&CK framework.
Predefined MITRE ATT&CK reports: An effective SIEM solution like Log360 consists of exclusive reports for each tactic of the ATT&CK framework. The reports are further categorized based on the different techniques and sub-techniques under each tactic. Figure 1 shows a preview of the MITRE ATT&CK reports page.

Figure 1: MITRE ATT&CK reports in Log360
- Predefined MITRE ATT&CK alert profiles: Log360 comprises built-in alert profiles for each tactic of the MITRE ATT&CK framework. These alerts are further classified based on the techniques under each tactic. Figure 2 represents the predefined alert profiles for MIRE ATT&CK.
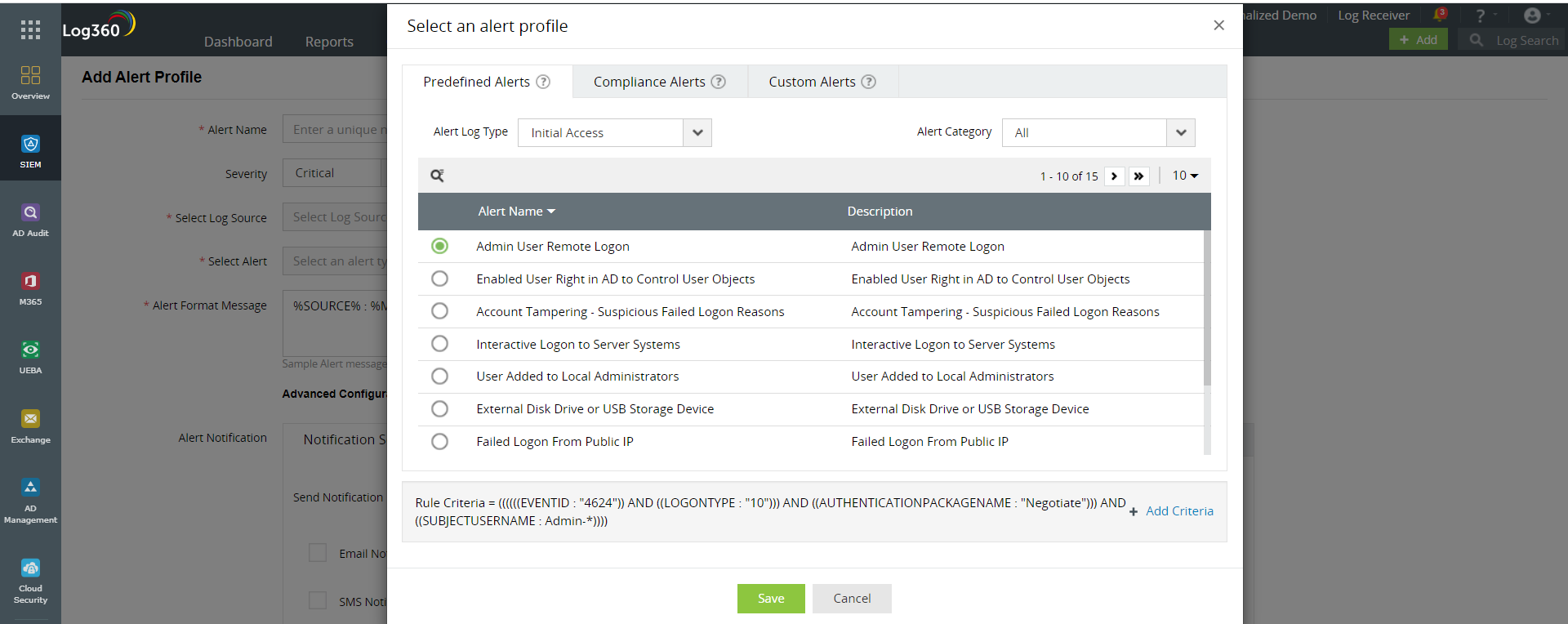
Figure 2: Predefined MITRE ATT&CK alert profiles in Log360
- Predefined correlation rules: This feature allows you to keep track of all incidents relevant to MITRE ATT&CK'S tactics, techniques, and procedures by correlating a sequence of malicious events and incidents. Figure 3 depicts a correlation rule.

Figure 3: MITRE ATT&CK correlation rule in Log360
It is imperative for you to stay proactive in your defense against cyberattacks with extended attack surfaces and sophisticated attack techniques. So why wait? Sign up for a personalized demo of Log360 to learn more.