User identity mapping for improved anomaly detection

In any organization, a user may access numerous devices and applications, but not always with the same username or credentials. Devices and applications use platform-specific user registries that are distinct from each other. As a result, organizations may end up monitoring five user identities from five devices separately, while they actually belong to a single user.
The table below shows one user, Michael Bay, using different user identities to log on and access various devices and applications.
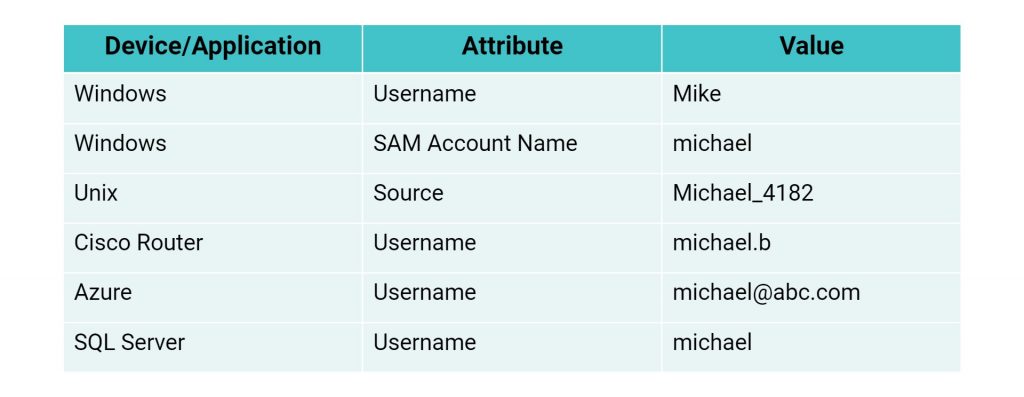
For enterprises, this is a huge administrative problem that can easily translate into a security problem. This is because during anomaly detection, your security solution may find it hard to attribute individual actions across applications as one particular user's activity.
The user identity mapping (UIM) feature in Log360 UEBA links all such distinct user registries with a base registry like Active Directory. This will help Log360 UEBA to determine the activity of a single user across multiple domains and correlate these activities to identify anomalies. Subsequent user risk scoring becomes more accurate as all of the user's identities in the network are synced together.
How are user identities mapped?
Users are mapped across the network using their AD account as the basis, or Source Account. Admins can create mapping rules by specifying which of the user account's Source Attributes and Target Attributes should match. Source Attribute is a value from the user's AD data (e.g., SAMAccount_Name). Target Attribute could be any field value in the target account (e.g., the SQL server's User Name field).

Figure 1: Creating new mapping to link user accounts
Log360 UEBA will then look for SQL user accounts that meet this criteria and map them to the user's AD account. Similarly, a mapping can be created with Windows as the target account and specifying the Target Attribute that will be same as the Source Attribute (SAM Account Name of AD account). Admins can review these mappings identified by Log360 UEBA and verify them. The individual user accounts (Windows and SQL) are thus mapped with AD, and all anomalies associated with the user across sources can be viewed in the dashboard.
User identity mapping in action
Michael will have just one representation on the User Risk Score dashboard once all of his accounts—including those of Windows, SQL Server, and other platforms—are mapped to his AD account. The dashboard collects all anomalies across platforms and generates an appropriate risk score for him.
Figure 2 illustrates the User Risk Score dashboard along with the contributing anomalies from Windows and SQL server activity.

Figure 2: User risk dashboard in Log360 UEBA