IT security under attack: Why are group memberships so crucial?
The anatomy of groups and memberships
Group memberships, both in Active Directory and Azure AD are extremely underrated when it comes to security. Memberships are often modified by administrators, help desks, and department managers.
Here are the various ways by which group memberships can be misconfigured in AD or Azure.
- Nested and indirect group memberships
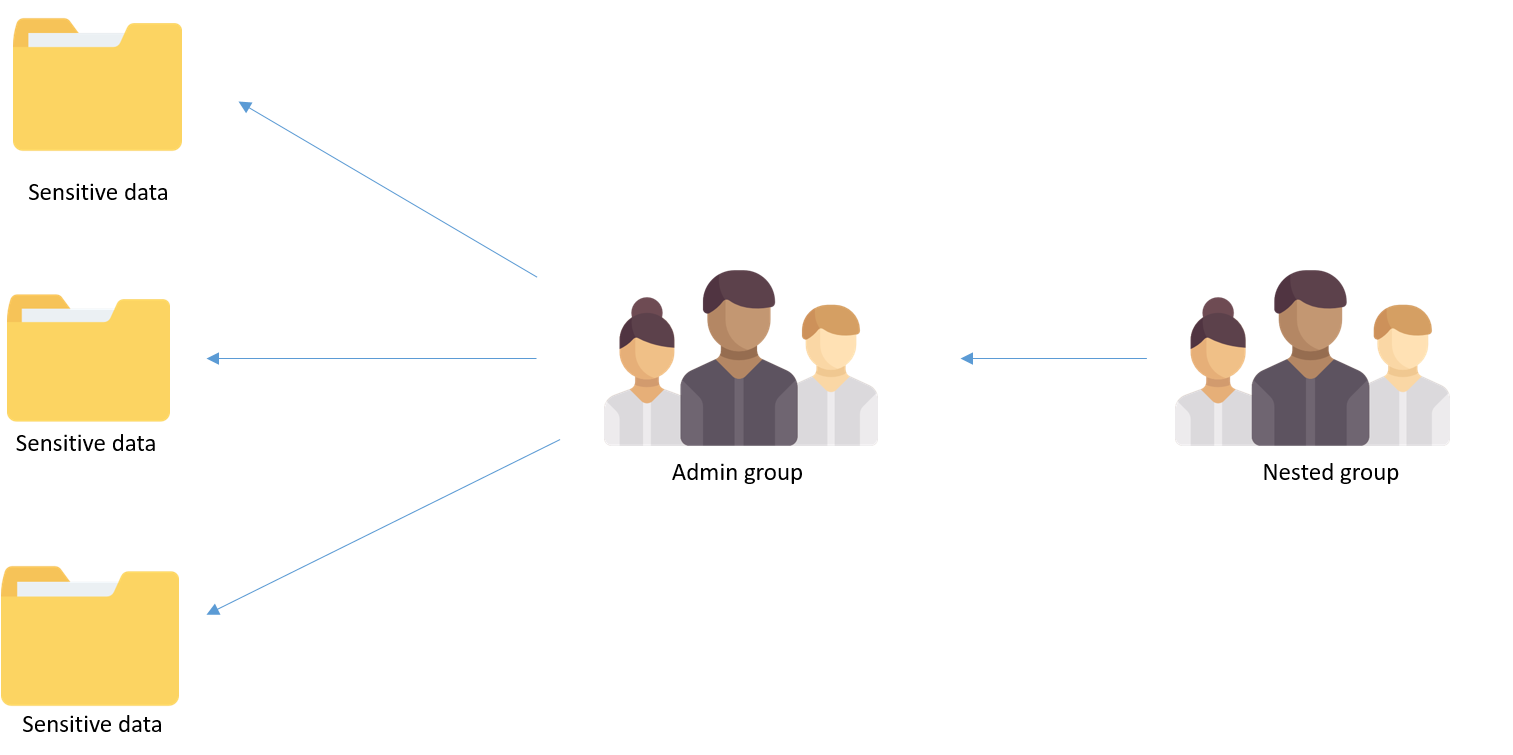
Adding a group as a member of another group is called nesting. For instance, there can be one or more security groups added to the Admin Group. Though the changes to this Admin Group are continuously monitored, it can still cause a security loophole when changes to the Nested Group are not watched.
Malicious insiders or external attackers can easily add members to the nested or indirect group and gain access to sensitive data, as the Nested Group is a part of the Admin Group. To overcome this challenge, enterprises should adopt a Zero Trust policy to grant only the required level of access to users.
Before we look into the various other ways groups can be misconfigured, let's take a look at how group membership changes can be audited in AD.

After you enable the required audit policies in AD to audit group memberships, any membership change on any type of group in your AD domain will be audited and recorded in the security tab of the Windows Event Viewer on your Domain controllers (DCs).
However, monitoring changes to groups is not that simple, because every other security change on the AD domain like changes to permissions, files, and folders along with logon and logoff activities are dumped into the same location (i.e., the security tab of Event Viewer). We have to look through all these security events using the respective Event IDs that denote changes to group modification.

Different events and IDs are recorded based on the scope of groups and operations performed, group creation, permission changes, and membership changes, which makes sorting through group changes extremely tedious and time-consuming.
2. Groups are more than just security groupsSecurity groups are the only groups that can dictate access to resources, but there are also various other types of groups in AD and Azure that grant access to other network resources.
Security groups across DCs and universal groups: If you own a multi-DC environment, then you may already be aware of these groups. There are default admin groups like DNSadmins, domain admins, and enterprise admins, which allow users to manage various components of your AD domain. Universal groups enable you to define roles or manage resources that span more than one domain.
Other platform groups: Any group created by a third-party service can dictate access to that service. For example:
On-premises AD groups are used to access Azure resources.
Exchange Server group: By default, this group has the right to clear the security log of the domain. Any malicious user who is a member of this group can easily erase the security log of the domain thus eliminating all traces of malicious activities.
Exchange Windows Permissions group: Has write DACL control over the domain DNS node. Any user with permissions over the domain DNS node can modify and take control of every object in the domain.
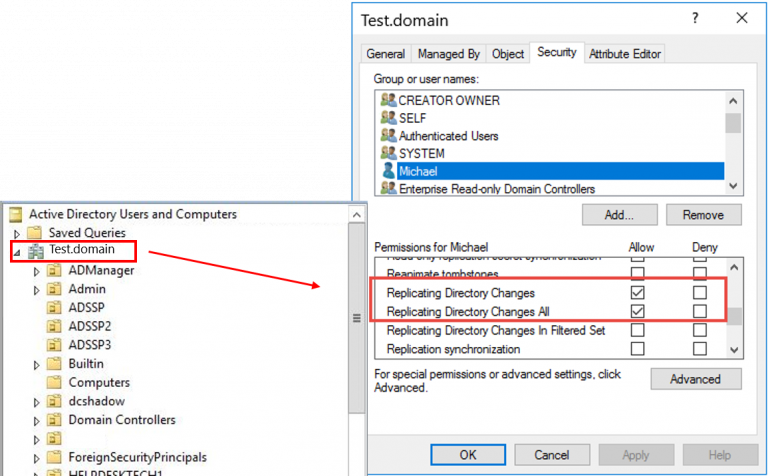
Read more about how permissions on your domain DNS in AD can be exploited here.
Azure AD security groups and Microsoft 365 groups: Azure AD and Microsoft 365 groups are pivotal to managing resources in Azure AD.
Security groups are used to manage members' and computers' access to shared resources for a group of users in Azure.
Microsoft 365 groups provide collaboration by giving members access to a shared mailbox, calendar, files, SharePoint sites, and more.
Let's take a look at group membership auditing in Azure AD.
Azure AD Audit logs

Just like Windows Event Viewer in on-premises Active Directory, Azure AD also has a central location where audit logs are stored. These audit logs record directory-based changes such as changes to users, groups, and applications.
Fortunately, Azure AD offers more sorting and filtering options compared to on-premises AD. For instance, you can filter security events based on time, operation, and more.
However, the audit logs don't offer a bird's-eye view of security changes. For example, let's assume you want to find out a list of security groups that were modified in your Azure AD. You will have to open and check every single log to determine which group was modified, which is neither quick nor easy. Let's take a look other possible ways to audit security events in Azure AD.
Microsoft 365 Unified Audit Logs
Microsoft has provided a solution for the above stated issue via the unified audit log in its Security & Compliance Center. However, this solution isn't efficient.

As you can see from the image above, the Security & Compliance Center has an audit log search feature that allows you to search and filter audit logs. Sounds great, right? Not exactly! If you want to further analyze the event, the details will be in JSON format when you open it. The only way to analyze this data is to export the JSON log data, and filter it using Microsoft Excel.

As you can see, although the filtering options are significantly better, the auditing and analysis challenges you face in a typical on-premises AD infrastructure also exist in Azure! On top of that, both Azure AD and Microsoft 365 store logs only for a short time period of 30 and 90 days respectively, which makes it difficult to conduct forensic analysis.

Timely capture and analysis of security group membership changes is the need of the hour. Although the native options capture sensitive events on time, the limited sorting and searching capabilities make analyzing these events challenging. Sometimes, detecting a membership change is not enough. Your organization should have a real-time alert mechanism and a mitigation action in place to counter any unauthorized group membership changes.
Don't have a group membership monitoring strategy in place? Here's an example of what that could lead to.
youtu.be/dbNWyAJYW2wWant to improve your security plan? Visit our IT security under attack page, and watch live simulations of widely-used attack techniques on various IT on environments like Active Directory, Azure AD, Windows, and more. Looking for a comprehensive solution to sort out your group security woes? Check out ManageEngine Log360!