Ever since Microsoft released Active Directory in 2000, there has been an option referred to as “delegation.” The term is pretty familiar now, but then it was a bit confusing. For Active Directory admins and designers, it was one of the major reasons to move to Active Directory from nearly any other directory operating system. Fast forward nearly 15 years and delegation – the term and technology – is the same. Nothing has changed with delegation, which in this case is not a good thing.
Delegation is the ability for the domain administrator to grant a non-domain administrator the ability to control a portion of the Active Directory environment. This control could be as large as creating user accounts in a specified organizational unit (OU) to as small as modifying the phone number for a single user. Common delegations that are widely used include:
- Resetting passwords for users located in one or more OUs.
- Modifying the group membership for all the groups located in a specified OU.
The configuration of delegation is quite simple, as the delegation wizard walks you through the key configurations. The delegation wizard has you perform the following steps:
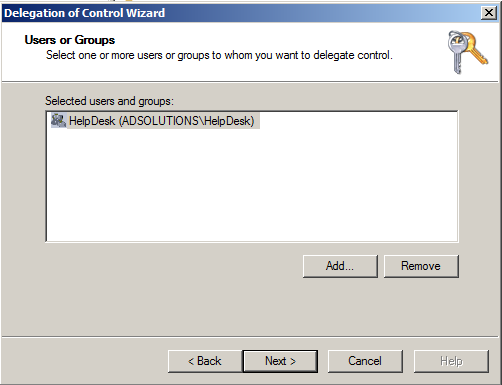
- Select which user(s) or group(s) you want to give control to. Figure 1 shows you what this looks like.
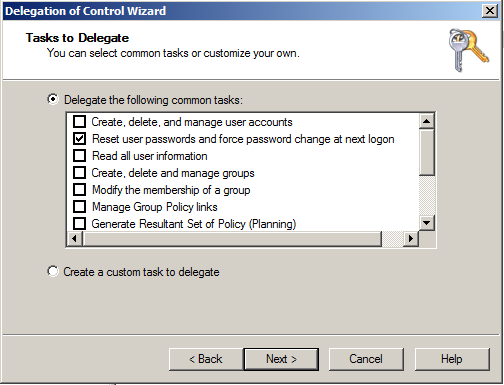
- Select which controls you want to give to the specified user(s) or group(s). Figure 2 shows you what this looks like.
- Finish the wizard.
Figure 1. User(s) or group(s) that you are giving control to.
Figure 2. Task(s) to be delegated.
These settings are extremely hard to track down once they are established. Actually, the wizard does not even indicate to you what settings are changing to accommodate the delegations.
Sure, you could go to the OU where the delegation was placed and try to discover the settings that were set. The delegation wizard is really a modification of the security permissions on the OU and subsequent objects contained within the OU. By looking at the security tab of the properties page of the OU, you can see what has changed. Figure 3 illustrates what is added to the OU security permissions when delegation is granted over resetting the password for users in the OU.
Figure 3. Security permissions after delegation is completed.
Drilling down into these two permissions will show that only three check boxes out of potentially thousands of options. Trying to review this manually for all of your OUs would take many, many hours.
Rather than take this painstaking approach to viewing the security set by the delegation wizard, you can instead run dsacls, the built-in tool to all domain controllers. This command line tool is very easy to use and very easy to review the results. The syntax you need to use is LDAP syntax for the OU that you are looking at. For example:
Dsacls ou=finance,dc=adsolutions,dc=demo
Dsacls ou=hr,ou=employees,dc=adsolutions,dc=demo
(Note: The domain name for the AD domain is adsolutions.demo)
The output from this would be similar to what you see in Figure 4.
Figure 4. Output from dsacls for the finance OU permissions.
You can see from the output that the HelpDesk group is listed on the ACL. Also, you can clearly see what permissions are granted to this group.
So the delegation wizard that Microsoft provides is a very powerful tool…for delegating control over AD. However, the delegation wizard can’t remove delegations, report on what delegations are granted, nor provide insight into what delegations relate to which permissions. By using the dsacls command line tool, you can easily and clearly see what permissions are currently on each OU and even at the domain level in AD.