Securing zone levels in Internet Explorer
Managing and configuring Internet Explorer can be complicated. This is especially true when users meddle with the numerous settings it houses. Users may even unknowingly enable the execution of malicious codes. This highlights the importance of securing Internet Explorer.
In this blog, we'll talk about restricting users from changing security settings, setting trusted sites, preventing them from changing security zone policies, adding or deleting sites from security zones, and removing the Security tab altogether to ensure that users have a secure environment when using their browser.Restricting users from changing security settings A security zone is a list of websites at the same security level. These zones can be thought of as invisible boundaries that prevent certain web-based applications from performing unauthorized actions. These zones easily provide the appropriate level of security for the various types of web content that users are likely to encounter. Usually, sites are added or removed from a zone depending on the functionality available to users on that particular site.To set trusted sites via GPO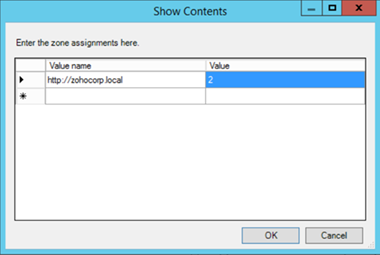 Figure 1. Assigning sites to the Trusted Sites zone.
Figure 1. Assigning sites to the Trusted Sites zone.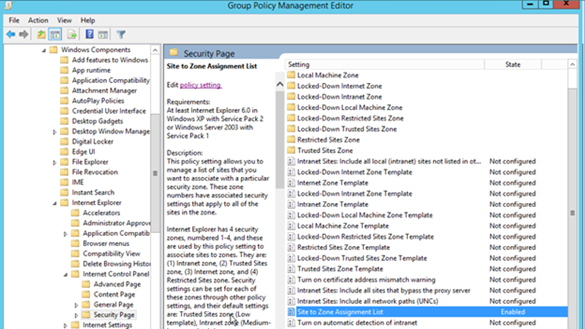 Figure 2. Enabling the Site to Zone Assignment List policy.
By enabling this policy setting, you can manage a list of sites that you want to associate with a particular security zone. See Figure 2.Restricting users from changing security zone policies
Figure 2. Enabling the Site to Zone Assignment List policy.
By enabling this policy setting, you can manage a list of sites that you want to associate with a particular security zone. See Figure 2.Restricting users from changing security zone policies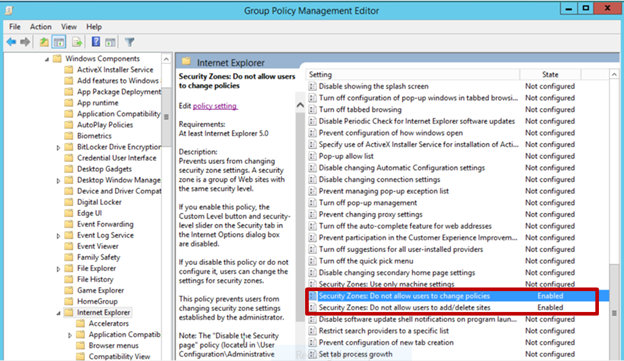 Figure 3. Enabling Security Zones: Do not allow users to change policies and Security Zones: Do not allow users to add/delete sites.Removing the Security tabThe Security tab in Internet Explorer's options controls access to websites by applying security settings to various download and browsing options, including defining security levels for respective security zones. By removing this tab, users will no longer be able to see or change the settings established by the administrator.
Figure 3. Enabling Security Zones: Do not allow users to change policies and Security Zones: Do not allow users to add/delete sites.Removing the Security tabThe Security tab in Internet Explorer's options controls access to websites by applying security settings to various download and browsing options, including defining security levels for respective security zones. By removing this tab, users will no longer be able to see or change the settings established by the administrator.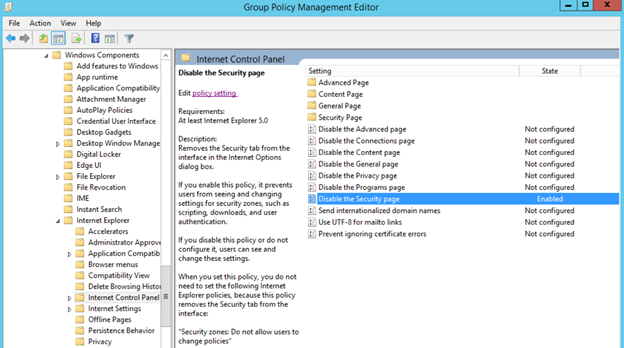 Figure 4. Enabling the Disable the Security page policy.
Enabling this policy prevents users from seeing and changing settings for security zones such as scripting, downloads, and user authentication. See Figure 4.
There's no denying the importance of securing Internet Explorer for any enterprise. By setting security levels, restricting users from changing security zone policies, preventing them from adding or deleting sites from security zones, and removing the Security tab, users will not be able to change any security settings in Microsoft Internet Explorer that have been established by the administrator. This helps you gain more control over Internet Explorer's settings in your environment.
Figure 4. Enabling the Disable the Security page policy.
Enabling this policy prevents users from seeing and changing settings for security zones such as scripting, downloads, and user authentication. See Figure 4.
There's no denying the importance of securing Internet Explorer for any enterprise. By setting security levels, restricting users from changing security zone policies, preventing them from adding or deleting sites from security zones, and removing the Security tab, users will not be able to change any security settings in Microsoft Internet Explorer that have been established by the administrator. This helps you gain more control over Internet Explorer's settings in your environment.
- Open the Group Policy Management Editor.
- Go to User Configuration> Policies > Administrative Templates > Windows Components >Internet Explorer > Internet Control Panel > Security Page.
- Select the Site to Zone Assignment List.
- Select Enabled and click Show to edit the list. Refer to Figure 1 below. The zone values are as follows: 1 — intranet, 2 — trusted sites, 3 — internet zone, 4 — restricted sites.
- Click OK.
- Click Apply and OK.
 Figure 1. Assigning sites to the Trusted Sites zone.
Figure 1. Assigning sites to the Trusted Sites zone. Figure 2. Enabling the Site to Zone Assignment List policy.
By enabling this policy setting, you can manage a list of sites that you want to associate with a particular security zone. See Figure 2.Restricting users from changing security zone policies
Figure 2. Enabling the Site to Zone Assignment List policy.
By enabling this policy setting, you can manage a list of sites that you want to associate with a particular security zone. See Figure 2.Restricting users from changing security zone policies- Open the Group Policy Management Editor.
- Go to Computer Configuration> Administrative Templates > Windows Components >Internet Explorer.
- Double-click Security Zones: Do not allow users to change policies.
- Select Enabled.
- Click
- Click Apply and OK.
- Open the Group Policy Management Editor.
- Go to Computer Configuration> Administrative Templates > Windows Components > Internet Explorer.
- Double-click Security Zones: Do not allow users to add/delete sites.
- Select Enabled.
- Click
- Click Apply and OK.
 Figure 3. Enabling Security Zones: Do not allow users to change policies and Security Zones: Do not allow users to add/delete sites.Removing the Security tabThe Security tab in Internet Explorer's options controls access to websites by applying security settings to various download and browsing options, including defining security levels for respective security zones. By removing this tab, users will no longer be able to see or change the settings established by the administrator.
Figure 3. Enabling Security Zones: Do not allow users to change policies and Security Zones: Do not allow users to add/delete sites.Removing the Security tabThe Security tab in Internet Explorer's options controls access to websites by applying security settings to various download and browsing options, including defining security levels for respective security zones. By removing this tab, users will no longer be able to see or change the settings established by the administrator.- Open the Group Policy Management Editor.
- Go to User Configuration > Policies > Administrative Templates >Windows Components>Internet Explorer > Internet Control Panel.
- Double-click Disable the Security page.
- Select Enabled.
- Click Apply and OK.
- Click
 Figure 4. Enabling the Disable the Security page policy.
Enabling this policy prevents users from seeing and changing settings for security zones such as scripting, downloads, and user authentication. See Figure 4.
There's no denying the importance of securing Internet Explorer for any enterprise. By setting security levels, restricting users from changing security zone policies, preventing them from adding or deleting sites from security zones, and removing the Security tab, users will not be able to change any security settings in Microsoft Internet Explorer that have been established by the administrator. This helps you gain more control over Internet Explorer's settings in your environment.
Figure 4. Enabling the Disable the Security page policy.
Enabling this policy prevents users from seeing and changing settings for security zones such as scripting, downloads, and user authentication. See Figure 4.
There's no denying the importance of securing Internet Explorer for any enterprise. By setting security levels, restricting users from changing security zone policies, preventing them from adding or deleting sites from security zones, and removing the Security tab, users will not be able to change any security settings in Microsoft Internet Explorer that have been established by the administrator. This helps you gain more control over Internet Explorer's settings in your environment.
Is there a way to enable Site to Zone assignment list and still let the user enter their own sites to the trusted list?
Hi Joe. You need to disable the below setting to achieve the requirement. Note: Even if the policy is not configured, users can add their own sites. Only when the policy is enabled, users can't add their own sites to trusted sites.
Thanks a lot.