One of the most important and powerful reasons that organizations consider Active Directory is the fact that delegation is built into the product. Windows NT did not have delegation, unless you want to call membership in the Account Operators group delegation! Windows Active Directory provides a simple method, using the Delegate Control Wizard, to grant a group of users granular control over all or even just a subset of your Active Directory objects.
For example, if you have a help desk that should have the ability to reset passwords for all users except for those in IT, you can delegate this permission to the OU that contains the non-IT employees. Another good use of delegation is to grant managers in a department the ability to modify group members, so the managers can control who can access data and applications owned by that department.
When this delegation is completed, which literally can take just seconds, the next step is to give those employees with the delegation some form of interface, so they can accomplish these administrative tasks. The only tool that Microsoft has for such management of Active Directory is the Active Directory Users and Computers administrative tool. I will assume, since the tool has been out for 15 years, that everyone has heard of it. What I will mention is that if you are running Windows XP or earlier, you can install this tool using the adminpak.msi. If you are running Windows Vista or later, you will need to install the RSAT (Remote Server Administrative Tools).
The biggest issue with the Active Directory Users and Computers tool is that it does not have any intelligence regarding the delegations that have been made within the Active Directory structure. This is partly due to the fact that every user in Active Directory has “read” access to everything in Active Directory. Because of this level of access, the user with the delegations will need to maneuver around in the tool to find the correct area for which they have been granted the delegations. This will require quite a bit of trial and error to find the area as well as to find the menus and tasks for which they can perform.
As an alternate solution to using the full Active Directory Users and Computers tool, Microsoft provides Taskpad Views to narrow down the “view” of what the user with delegated permissions can see. I prefer not to get into the complete details of generating Taskpad Views, as it is painful and not all that pleasant, but I will describe how you can create them.
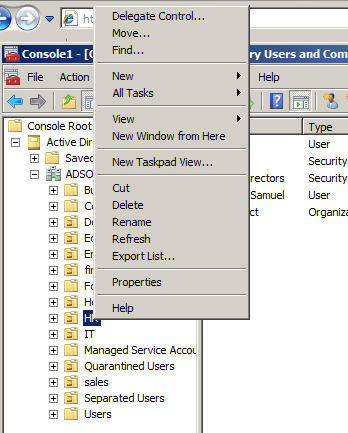
First, you can’t use the Active Directory Users and Computers tool that is located in the Administrative Tools folder or menu listing. Second, you must launch the Active Directory Users and Computers tool by using the MMC (Microsoft Management Console) administrative tool. Once inside the MMC, after you have added the Active Directory users and Computers snap-in, you will now be able to start the process to create a Taskpad View. To create a Taskpad View, you will first need to get to the node (domain level, OU, or even object) in the Active Directory Users and Computers interface. From there, right-click on the node and you will see an option for Taskpad View, which can also be seen in Figure 1.
Figure 1. Creating a Taskpad View.
The trick of the Taskpad View is that you will first need to decide on what the delegated user will see, then you need to configure what the delegated user’s interface can accomplish. I will tell you now this will require many trials and errors before you get it just right.
Yes, the Active Directory Users and Computers and the accompanying Taskpad View is free. However, you will find that the administration of these interfaces is manual, laborious, and requires constant maintenance as delegations change.
Instead of going through the efforts to use a tool that is not all that easy or useful, you could use a tool that is designed to make delegations easy, automatic, and maintenance free! The tool is ADManager Plus. I find authors and evangelists say that things are “easy” when in reality they are not. In this case, I can tell you it is easy to setup delegations and there is no work to be completed, so the delegated user has a simple, easy- to-use, customized interface.
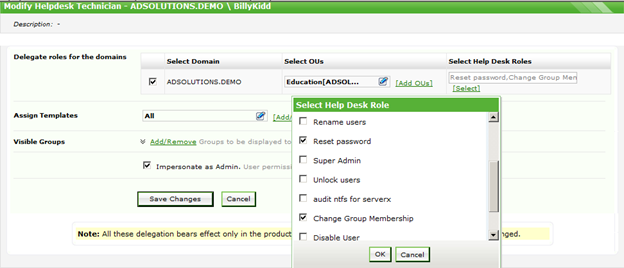
Figure 2 illustrates the interface that is used to perform the delegations in ADManager Plus.
Figure 2. Delegating to technicians is easy in ADManager Plus.
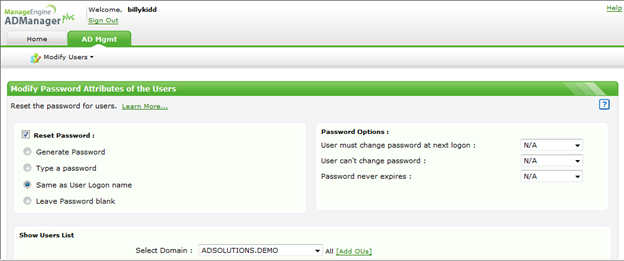
Figure 3 shows you what the resulting “Reset password” delegation would look like to the delegated technician. Notice that the user simply connects to an HTML page, and the resulting options are 100-percent driven by the delegations performed by the administrator.
Figure 3. Delegated technician view to reset passwords.
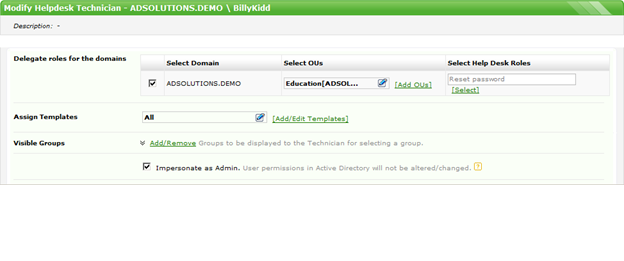
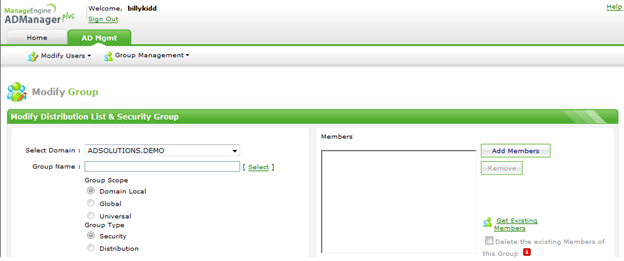
Now, let’s assume that you also want this technician to be able to change group membership. Figure 4 illustrates the delegation, and Figure 5 illustrates the new HTML page that would appear after quickly logging off and logging back into ADManager Plus.
Figure 4. Delegation to add modification to group membership.
Figure 5. New delegation interface in ADManager Plus for both resetting passwords and changing group membership.
Notice that not only does the technician have access to user properties, but now group properties.
Just comparing the GUI results from the Taskpad View (lots of effort) to ADManager Plus (nearly-zero effort), it’s a no-brainer which option is more powerful, useful, and efficient.