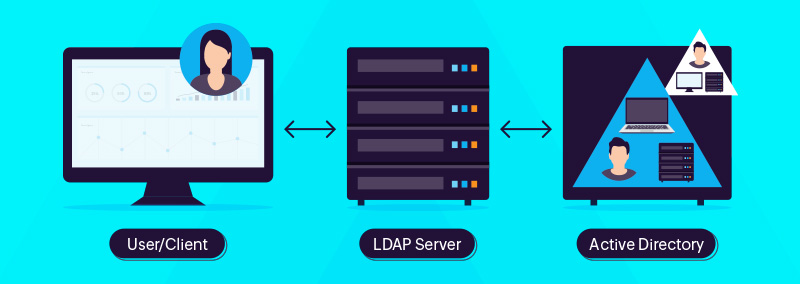
If you are a beginner on your Active Directory (AD) learning journey, then you must have stumbled upon the term LDAP. It’s quite possible that you feel a little lost trying to understand this concept. The objective of this blog is to get you comfortable with LDAP and more confident about your AD learning journey.
To begin with, let’s address the subject head-on! What is LDAP?
LDAP is a standard software protocol that allows users to find information about other users and their attributes, resources, applications, and other directory details. It is the main protocol that makes the functioning of AD possible.
The roles that LDAP plays are as follows:
-
It helps authenticate and authorize users so they can access and modify data and resources in the network.
-
It provides a communication language for clients to interact with servers and request required information from the directory service.
LDAP uses bind operations to authorize the clients to access the LDAP server once they have been successfully verified. The bind operation includes the bind request and the bind response.
The LDAP bind request consists of the following three parameters:
1) The LDAP version: This specifies the LDAP version the client wants to use. LDAP Version 3 is popular among clients, but some old clients may still request LDAP Version 2.
2) The distinguished name (DN): A DN uniquely identifies an object in the directory. This field can have a value of 0 in the case of anonymous authentication.
3) The authentication method: The client can use any of the following authentication methods: anonymous authentication, simple authentication, or Simple Authentication and Security Layer (SASL).
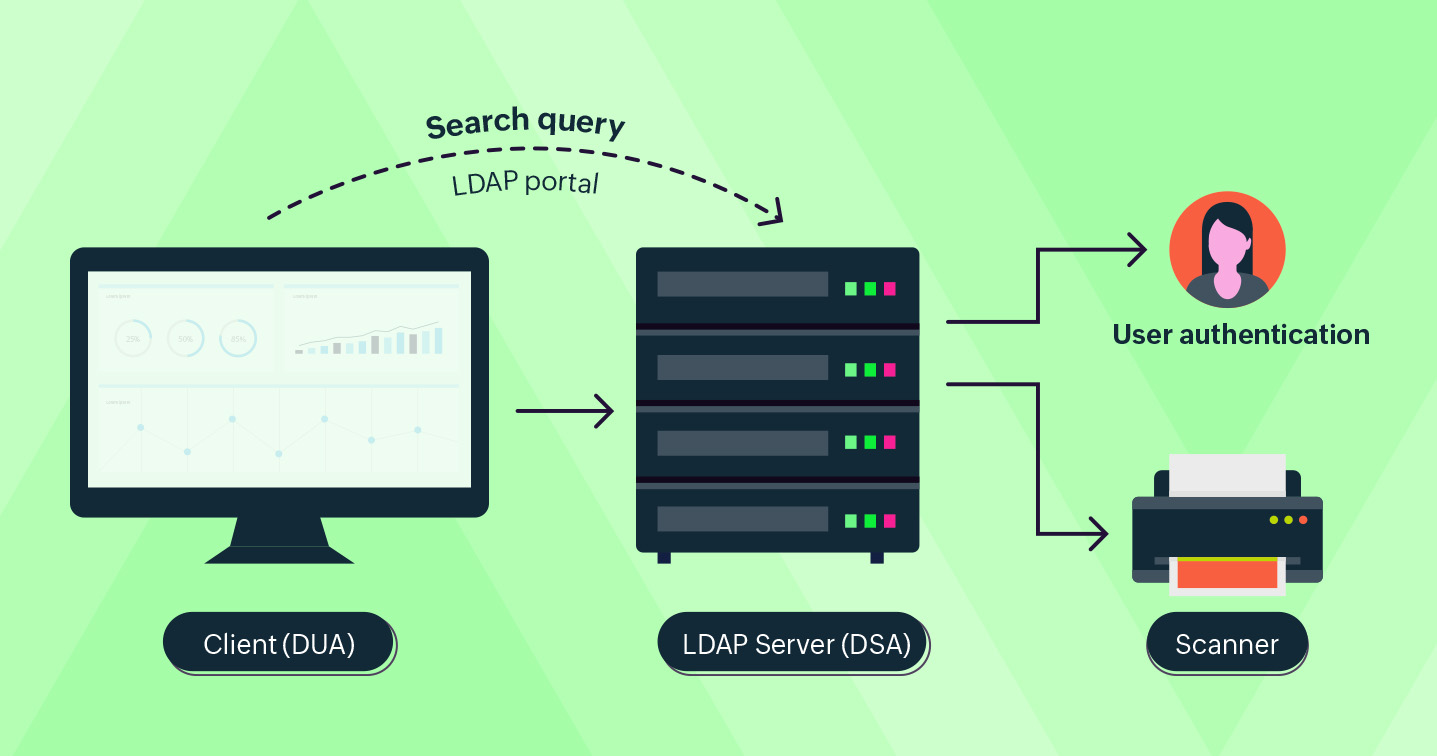
To understand this better, let’s consider an example. Jennifer wants to access a scanner on the fifth floor of her office for some official work. LDAP enables her to search and locate scanners on the fifth floor and it further authenticates and authorizes her to access the scanner and securely connect to it.
The following steps detail how LDAP performs this process of authentication and authorization:
-
Jennifer (the user, aka the client or directory user agent (DUA)) connects to the LDAP server (aka the directory system agent (DSA)).
-
Jennifer then uses LDAP to send a search request to the server, requesting the specific scanner on the fifth floor.
-
The LDAP database authenticates Jennifer.
-
LDAP searches the directory and returns the address of the requested scanner to Jennifer.
-
Jennifer receives the requested response and disconnects from the LDAP server.
In the process described above, the LDAP server can use any of three ways to authenticate Jennifer. These are:
- Anonymous authentication: In this method, the client connects to the server by sending a bind request where the username value is 0 and the password value has a length of 0. The extent of information available to the client is usually minimal with this method.
-
Simple authentication: In this method, the client enters their username and password to bind with the LDAP server. The server then verifies and authenticates the credentials against the master data stored in the LDAP database.
-
SASL authentication: In this method, the LDAP server uses an authentication mechanism like Kerberos in AD to carry out the authentication process.
LDAP is compatible with most directory services, such as OpenLDAP, and it is one of the key protocols employed in Microsoft AD.
Now let’s say Jennifer’s organization has more than 5,000 employees. Managing and storing information about all those users (along with their attributes) and the resources used by them requires an enormous amount of data. To extract the information from this mountain of data, we need LDAP.
Thus, LDAP acts a language for clients to communicate with AD in a secure fashion and extract the desired information from the AD database after authentication and authorization.
I hope this blog helped you get a better, clearer understanding of LDAP and its relationship to AD. To learn more about such concepts, stay tuned!

