There is nothing scarier to an Active Directory administrator than the thought of someone attacking the domain controllers. The majority of attacks come from within the internal network and come from existing domain users. If the attacker does not have elevated credentials, the goal for the attacker is to try to obtain these credentials. The typical method for this is to guess passwords of existing users.
When an attacker tries to guess the password of another user, there will inevitably be failures – at least, we hope so! A high, repetitive number of failed logons for a single account can indicate a potential attack. The key is finding these failed logons before the attacker is successful, so you can negate the attack before it is accomplished.
The built-in tools that Microsoft provides have nothing that gives insight into this behavior. Even if you enable auditing of failed logons, you would need to scour the logs to analyze these failed logons – and that’s only as long as the log does not overwrite your events. The Microsoft logs will not only contain the failed logons, but will contain other security-related events that are occurring on the domain controller. You also need to consider that there are many domain controllers that must be analyzed, as the logs are not centralized by Microsoft.
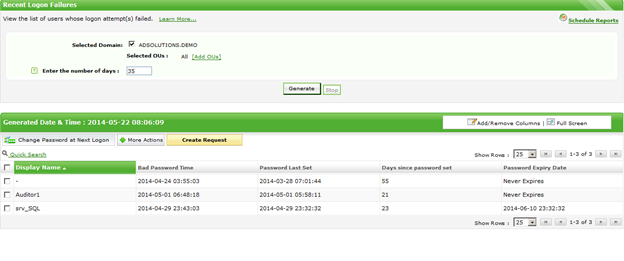
So instead of trying to analyze logs and centralize the logs, just use a tool that does this for you. ManageEngine’s ADManager Plus will allow you to see these failed logons with just a single click. Figure 1 illustrates the result of the failed logons report.
Figure 1. ADManager Plus failed logon attempts report.
With just a single click, you can view the failed logons over any period of time you want. This will clearly show if one or more user accounts is being attacked by attempting to guess or obtain the password.
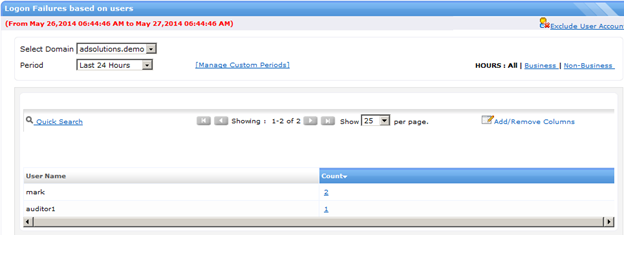
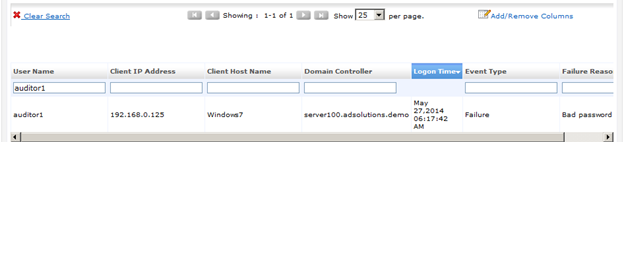
If you want to see more details, you can take advantage of the granular details provided in ADAudit Plus. For example, you might want to also know how many failed logons are recorded in the time period you are searching, as well as which computers were used to attempt the logons. Figure 2 shows you the number of failed logons and Figure 3 shows you which computer the attempts were made from.
Figure 2. ADAudit Plus shows you how many failed logons by a single user.
Figure 3. ADAudit Plus can show you which computer the failed logon originated from.
This level of detail for failed logons can really help prevent attacks from continuing and possibly negate future attacks.
For a video of how to view failed logons for both ADManager Plus and ADAudit Plus, see https://www.youtube.com/watch?v=xOERi99YUS4