Chances are you’ve heard of traditional credential-based attacks on Active Directory (AD) and cloud applications—brute force attacks, dictionary attacks, and keylogging, to name a few. There’s now another...
Five worthy reads: Augmented analytics paves the way
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we look at the...
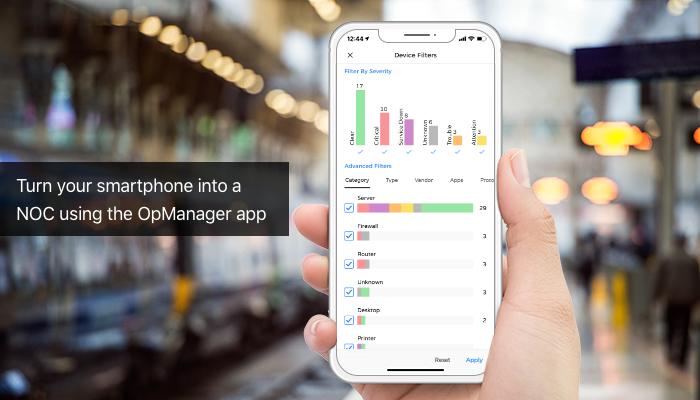
Become an eagle-eyed network admin using OpManager’s push notifications
The secret to exceptional network management is periodically identifying and diagnosing network problems. Putting your experts at the network operations center (NOC) all day watching for a device to go down isn’t the best use...
ManageEngine recognized in Gartner Magic Quadrant for Security Information and Event Management three years in a row
We’re happy to announce that ManageEngine has been positioned in Gartner’s Magic Quadrant for Security Information and Event Management[i] (SIEM) and its Critical Capabilities for Security Information...

Six reasons why data backups are crucial for your business
The increase in ransomware attacks and high-profile data breaches over the last few years has reinforced the importance of data security. It should be noted that WannaCry infected more than...

Five worthy reads: The role of workforce preparedness in digital transformation
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we highlight the significance...

[Office 365 webinar] Score a higher Secure Score
As you may know, the Office 365 Secure Score is an indication of how secure your current Office 365 environment is compared to the possible level of security that...

2018: A look back at what we’ve done in ITOM
2018 was a busy year for the ManageEngine IT operations management team. We tackled everything from major concerns like poor network performance, security, cost, enterprise...
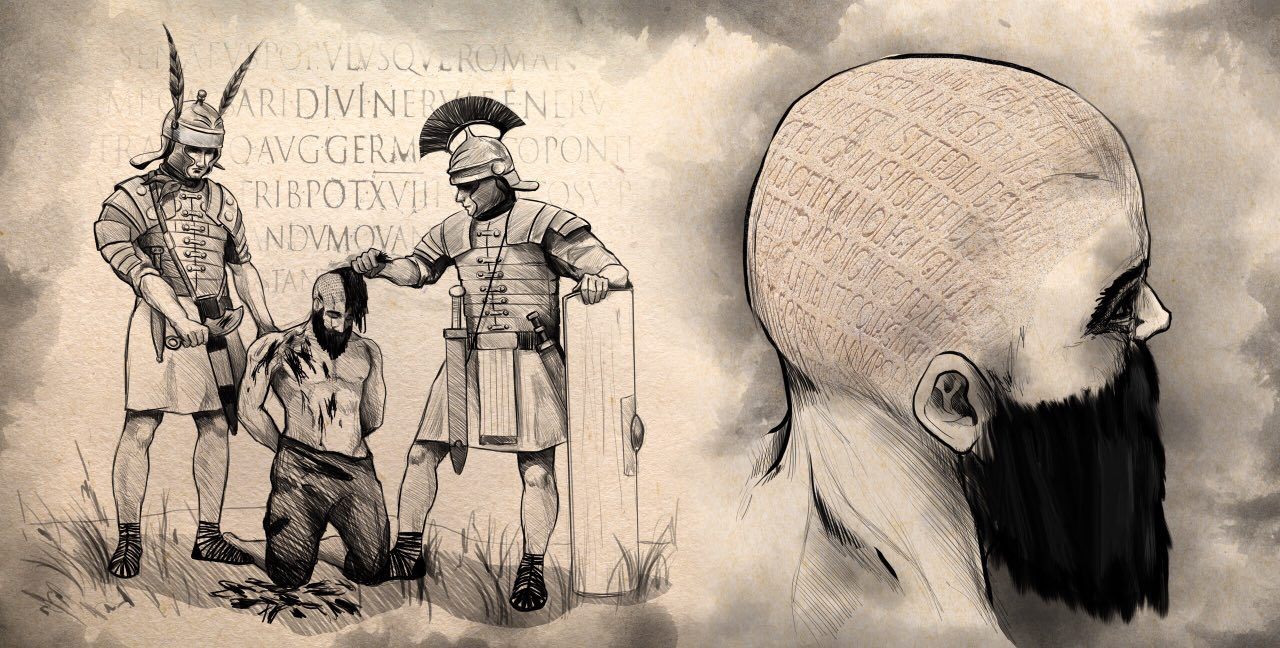
The relationship between steganography and cyberattacks
There’s no denying the importance of communication. Businesses cannot function without the proper means of communication, such as phone calls, faxes, emails, text messages, and more. However, not all forms of communication are secure, meaning the...