At over $60 billion per year, Medicare fraud has become one of the most profitable crimes in America, say analysts. In South Florida, health information...
Cyber-attack on Zappos: Information Security Lessons for Enterprises [Part-5]
In the previous four posts, we analyzed the causes for security incidents. We discussed how lack of internal controls, access restrictions, centralized management, accountability, strong...
Cyber-attack on Zappos: Information Security Lessons for Enterprises [Part-4]
In the previous three posts in the backdrop of the cyber-attack on Zappos.com, we analyzed the challenges associated with achieving the highest level of information...
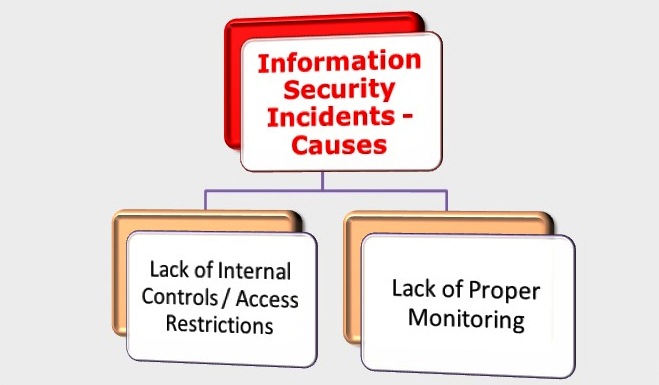
Cyber-attack on Zappos: Information Security Lessons for Enterprises [Part-3]
In the previous two posts in the backdrop of the cyber-attack on Zappos.com, we analyzed the challenges associated with achieving the highest level of information...
Cyber-attack on Zappos: Information Security Lessons for Enterprises [Part-2]
In the previous post, in the backdrop of the cyber-attack on Zappos.com, we analyzed the main challenges associated with achieving the highest level of information...

Cyber-attack on Zappos: Information Security Lessons for Enterprises [Part-1]
For information security, the year 2012 has indeed started off with a shocking note. Zappos.com, one of the largest online retailers dealing with shoes and...

Password Manager Pro is worth every penny, say our customers!
There can’t be a better finish to an eventful year. As 2011 is drawing to a close, we are hearing feedback from scores of highly...
Password Manager Pro emerges the top choice of IT Managers across the globe in 2011
2011 is fast drawing to a close. While looking ahead for a great holiday season and a wonderful New Year 2012, we just looked back...
How do you control concurrent privileged access to sensitive IT resources?
In enterprises, quite often, many administrators might be accessing a system in production environment concurrently. They might be attempting to carry out conflicting operations, unconnected...
