A firewall rule audit is an essential process for ensuring that your firewall rules are effective and aligned with your security policies. As network environments grow more complex, managing and optimizing firewall rule bases becomes increasingly challenging. Over time, firewall rules can accumulate, leading to bloated, inefficient rule sets that hamper performance, increase security risks, and complicate compliance efforts. Regularly auditing and cleaning up these rules is essential for maintaining a secure and efficient network.
In this blog, we’ll provide a step-by-step approach to conducting an effective firewall rule audit and also explain how ManageEngine’s Firewall Analyzer can assist in cleaning up and optimizing your firewall rule base.
The importance of firewall rule audits
A well-optimized firewall rule base is crucial for several reasons:
-
Improved performance: A streamlined rule base enhances firewall efficiency, allowing for faster processing and reduced system load.
-
Enhanced security: Removing outdated, redundant, and permissive rules minimizes potential vulnerabilities and strengthens your network’s defense.
-
Simplified compliance: A clean rule base makes it easier to meet regulatory requirements, such as those outlined by PCI DSS, and reduces the burden of audits.
How to audit firewall rules
Effective firewall rule audits are essential for maintaining network security. By following these six key practices, you can ensure a successful firewall rule audit, keeping your defenses sharp and responsive.
1. Start with documentation
Proper documentation is essential for understanding the current firewall setup and for identifying which rules might need review or adjustment. This first step will help understand how the firewall is performing, forming the base of the audit. Begin by listing all existing firewall rules. This can include rules governing inbound and outbound traffic and rules for managing access between different network segments.
2. Identify redundancies and unused rules
Redundant rules can create confusion and slow down the firewall’s performance. Unused rules can create unnecessary clutter. Removing or consolidating redundant and obsolete rules helps improve both performance and security, making the firewall more efficient. So, review the list to find any duplicate or unused rules.
3. Review rule order
Firewalls process rules in a top-to-bottom order. Make sure that more specific rules are placed before general ones to prevent conflicts and ensure proper filtering of traffic. Correctly ordered rules prevent unintended access or blockage of legitimate traffic, thus avoiding potential security issues and operational disruptions.
4. Verify compliance with policies
Compliance with security policies and regulations is crucial for maintaining a strong security posture and avoiding legal or regulatory issues. Ensure that the firewall rules comply with organizational security policies and industry regulations. This involves verifying that rules enforce appropriate access controls, data protection measures and conducting regular security audits.
5. Log analysis
Log analysis helps you understand how well the rules are performing and identify any adjustments needed to better protect against emerging threats. Analyzing these logs can reveal patterns or anomalies that might indicate potential security threats. Review firewall logs to detect any unusual or suspicious activities.
6. Revisions and summary
Based on the analysis, adjust firewall rules. This might involve adding new rules, modifying existing ones, or removing outdated rules. Regular adjustments ensure that the firewall configuration remains effective in both security and performance, addressing any identified issues and adapting to new threats. Summarize the audit process, key findings, actions taken, and recommendations in a detailed report. It also supports future audits and improvements.
How Firewall Analyzer simplifies Firewall rule audits
ManageEngine’s Firewall Analyzer is a powerful tool designed to automate the process of firewall rule audits, making it easier to identify and address inefficiencies, security risks, and compliance issues. Here’s how this solution assists:
1. Automated rule management: Firewall Analyzer effortlessly adds, modifies, and deletes firewall rules across multiple devices. This proactive automated rule management feature reduces manual errors and ensures that rule changes are seamlessly integrated, helping maintain a clean and efficient rule base.
2. Comprehensive rule visibility: With this solution, you gain a complete overview of your firewall rules, including identifying those that are inactive, redundant, or outdated. This visibility enables you to declutter your rule base by removing rules that no longer serve a purpose, improving overall firewall performance.
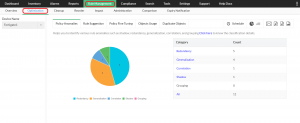
3. Optimization recommendations: Firewall Analyzer examines rule interactions and provides recommendations for reordering rules to enhance performance. By optimizing rule positions based on usage patterns and complexity, you can ensure your firewall operates at peak efficiency.
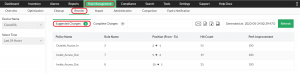
4. Impact analysis: Before implementing new rules, Firewall Analyzer conducts an in-depth impact evaluation to determine how the changes will affect the existing rule set. This helps prevent the introduction of security vulnerabilities or conflicts, ensuring that new rules enhance rather than compromise your firewall’s security.
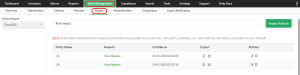
5. Rule cleanup: The comprehensive tool identifies and suggests the removal of unused rules, objects, and interfaces. Regular cleanup keeps your firewall rule base lean, reducing unnecessary processing and potential security risks.
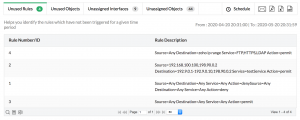
6. Compliance assurance: Firewall Analyzer helps you stay compliant with industry regulations by ensuring that your firewall configurations are regularly reviewed and optimized. The tool provides detailed reports and documentation, making it easier to meet audit and compliance requirements.
Create an efficient, secure, and compliant firewall environment
Optimizing the firewall rule base by conducting a firewall rule audit is not just about improving performance—it’s about ensuring the security and compliance of your network. By documenting rules, identifying redundancies, reviewing the rule order, ensuring compliance, analyzing logs, and making necessary adjustments, you can significantly enhance the effectiveness of your firewall. ManageEngine’s Firewall Analyzer provides the features necessary to automate and streamline this process. This solution makes it easier to create and maintain an efficient, secure, and compliant firewall environment.
Start your free, 30-day trial today to explore how Firewall Analyzer automates your firewall rule audit process and efficiently identifies and addresses your security risks and compliance issues.
