Threat intelligence, DNS detection and response, and DNS firewall: The future-proof defense every network needs

When it comes to incident response, every network admin knows the drill—endpoints trip alarms, firewalls block traffic, SOC dashboards light up with alerts. But the real story almost always starts earlier—in DNS. Long before malware detonates or data leaves the building, an attack whispers its intent in a query. Newly registered domains, fast-flux campaigns, suspicious TXT lookups—in all of these actions, DNS is where adversaries test the waters.
That’s why DNS firewalls have become a staple in enterprise security. They filter queries against blocklists and keep users away from known bad destinations. But here’s the catch: static blocklists can’t keep pace with today’s threat landscape. Attackers spin up domains by the thousands, rotate infrastructure on the fly, and weaponize zero-day domains faster than signature updates can arrive.
So the question remains: Every DNS firewall filters. But when was the last time your DNS firewall hunted back?
To keep up with evolving threats, a DNS firewall needs more than lists. It needs live threat intelligence feeds, confidence scoring, contextual visibility, and automated quarantine. That’s where DDI Central’s DNS Threat Intelligence and DNS Detection and Response (DDR) turns resolution into resilience. It's a DNS layer that doesn’t just block. It catches, contains, and cuts off attacks in real time.
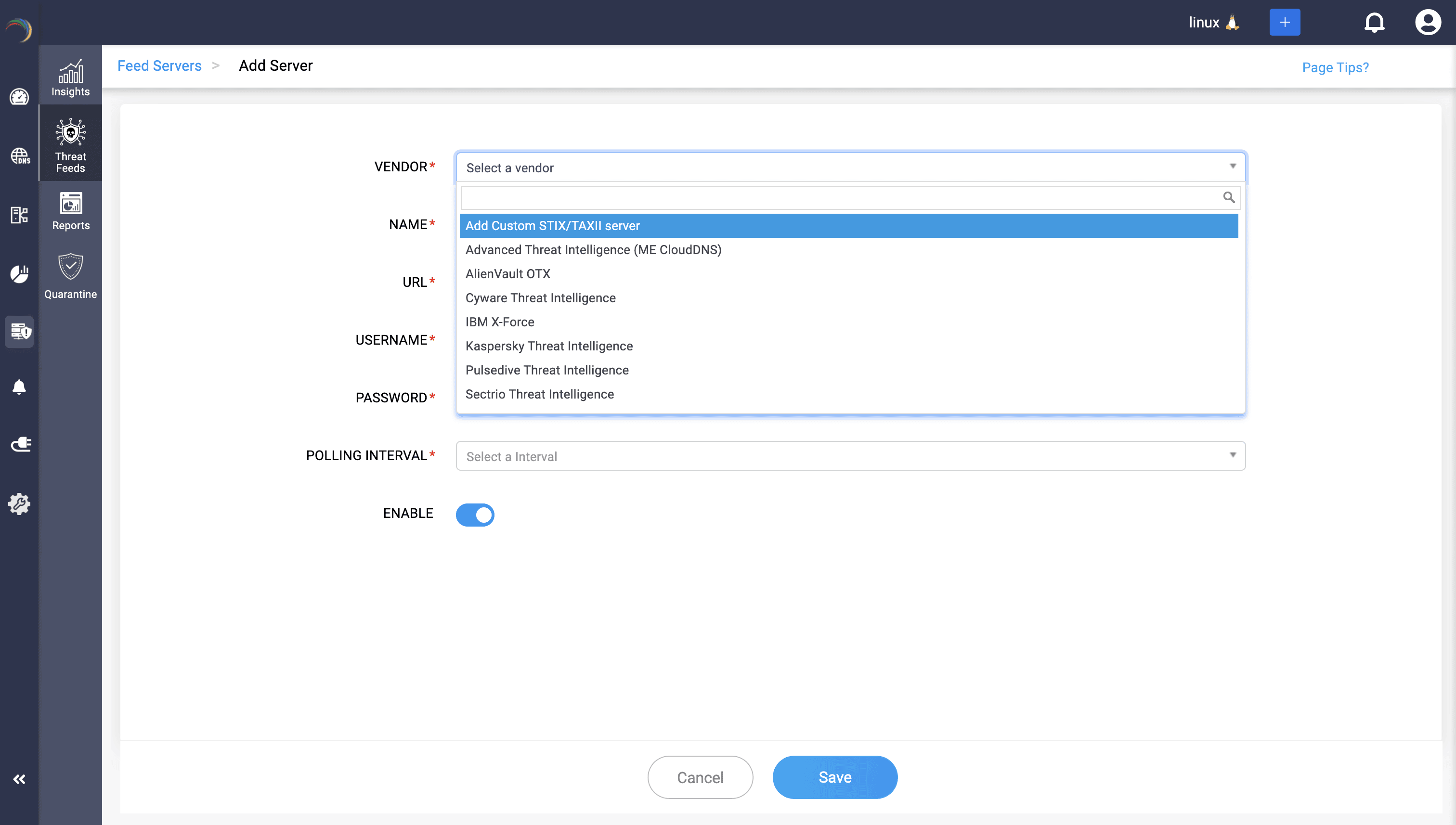
1. Onboarding the feed servers: All threat feeds, one hub
Threats don’t arrive in one format, from one vendor, or through one channel. That’s why DDI Central begins by unifying your threat feeds, including vendor feeds, curated indicators of compromise (IoCs), and even your own custom STIX/TAXII servers, into a single command center called the Threat Intelligence Feed Hub.
Your watchtower for IoCs
The Feed Hub is where every IoC flagged across sources is clustered, scored, and put under continuous watch. Instead of flipping between portals, admins get one pane of glass showing:
Multi-vendor intel: It onboards feeds like AlienVault, IBM X-Force, Cyware, or any standards-compliant STIX/TAXII feed—no custom parsers required.
Bring your own intelligence: It plugs in custom STIX/TAXII servers for industry-specific IoCs, ransomware campaigns, or partner-shared intel.
Frictionless, secure, and always-on
Here’s how DDI Central keeps your threat feeds synced and under control:
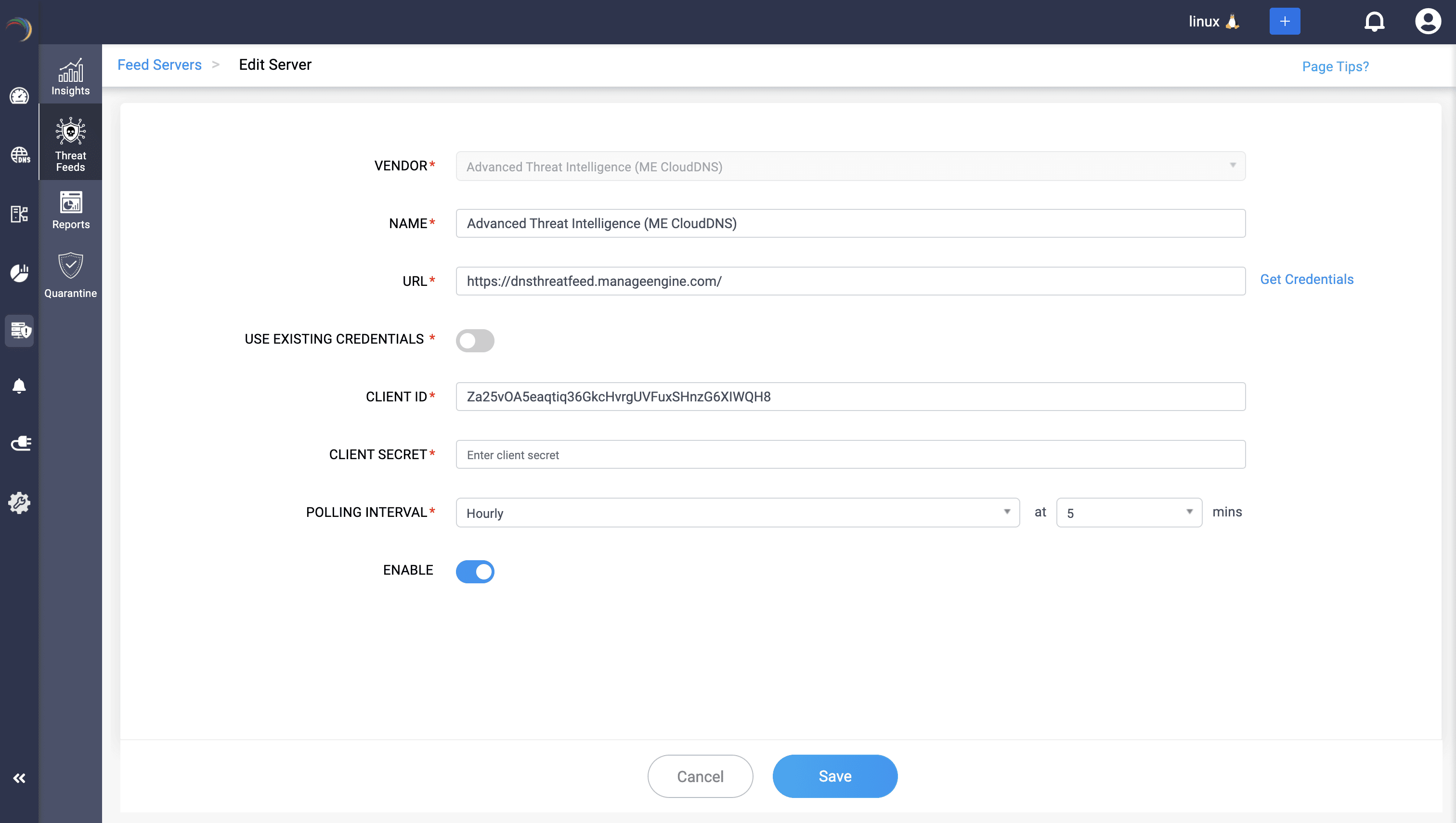
Credentialed onboarding: Secure OAuth-based access ensures feeds are pulled safely, with token rotation and vendor-compliant syncs.
Fine-grained control: You can toggle feeds on and off, set hourly or daily polling intervals, or trigger a manual sync when freshness matters most.
Unified visibility: At a glance, see which feeds are active, when they last synced, and what’s next—no log hunting.
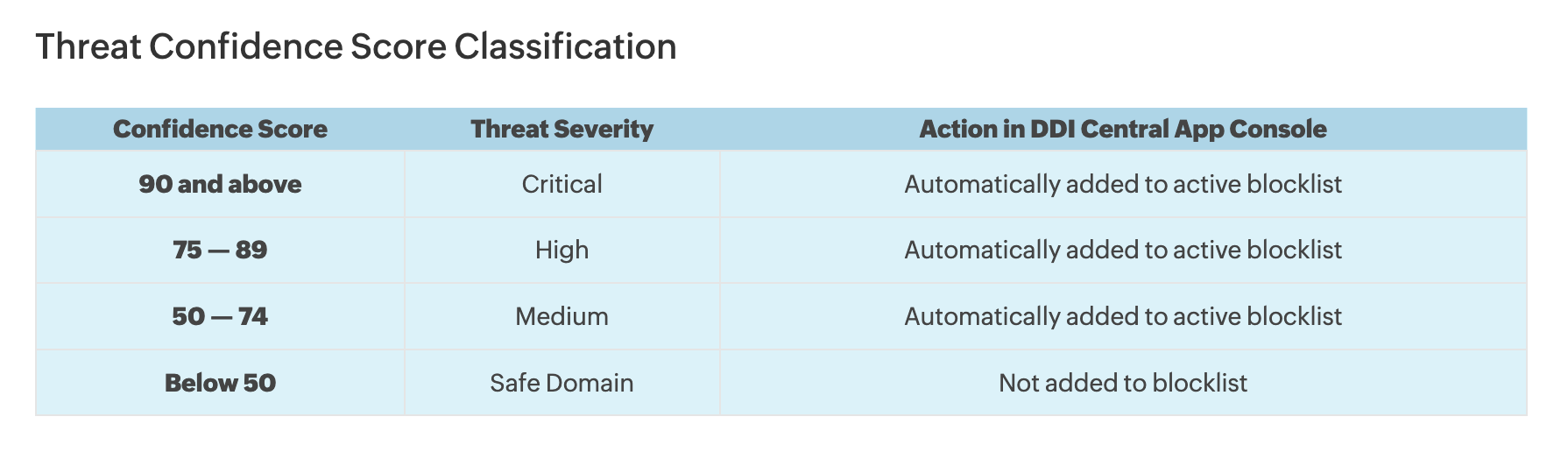
By consolidating all STIX/TAXII threat intelligence feeds in the Feed Hub, DDI Central turns scattered data into a continuously vetted, real-time blocklist. Each IoC carries a confidence score that updates as vendor intelligence shifts, ensuring only substantial threats with a score of more than 50 graduate into policy enforcement.
This is where the pipeline sets the stage. Feeds gather, the Feed Hub scores and clusters, and the moment a client query brushes against one of those IoCs, the strategy pivots to IoC spotlight.
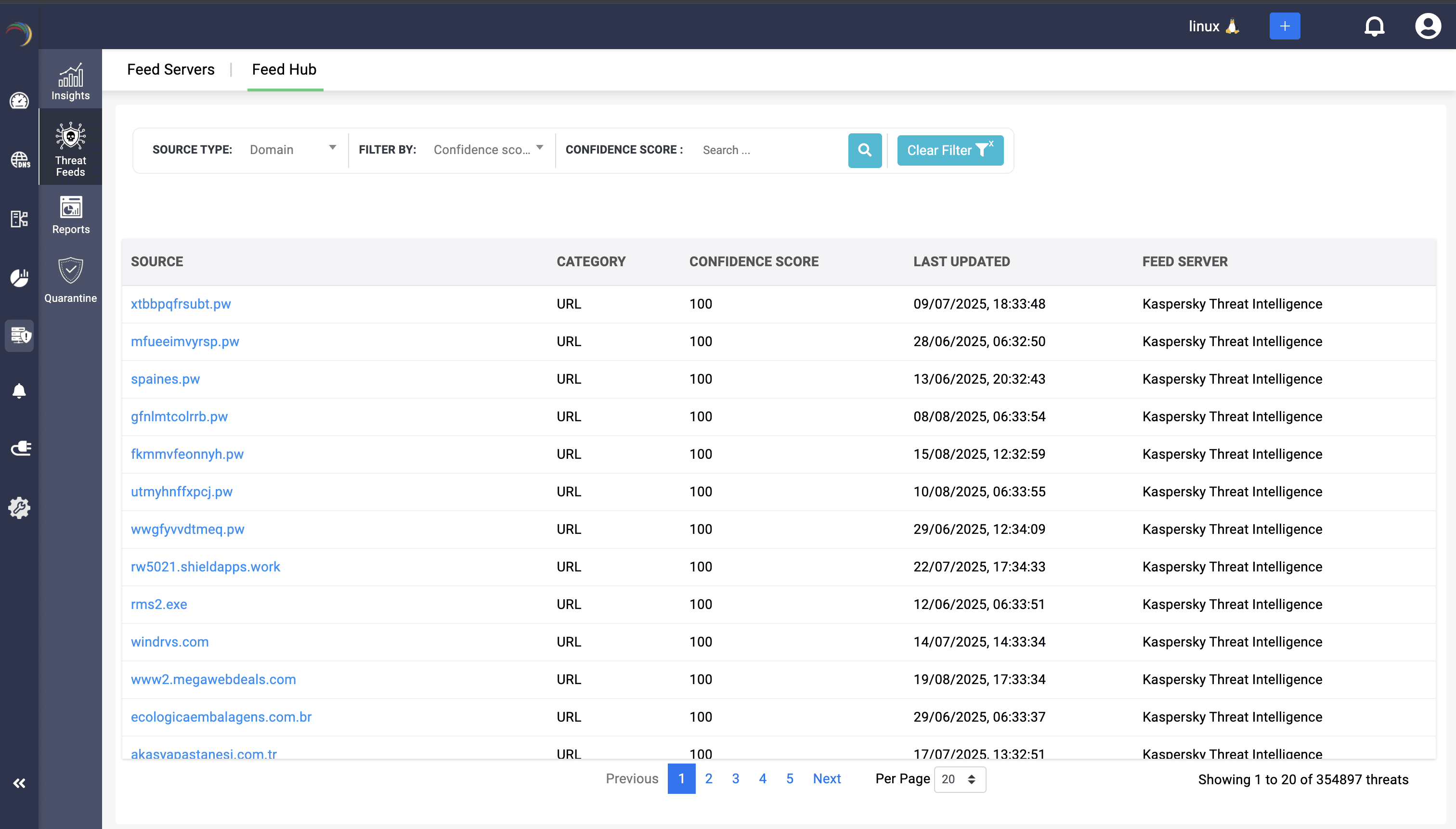
2. IoC spotlight: Threats under the microscope
Typically, an IoC in a feed is just a passive indicator of a potential threat, sitting dormant until a client in your network queries it. The moment traffic hits a flagged domain, DDI Central moves the IoC under active watch, building a live dossier that tracks its confidence, history, and hits.
Confidence, history, and hits—your full threat dossier in one view
Here’s what the IoC spotlight reveals when a domain moves from feed to active watch:
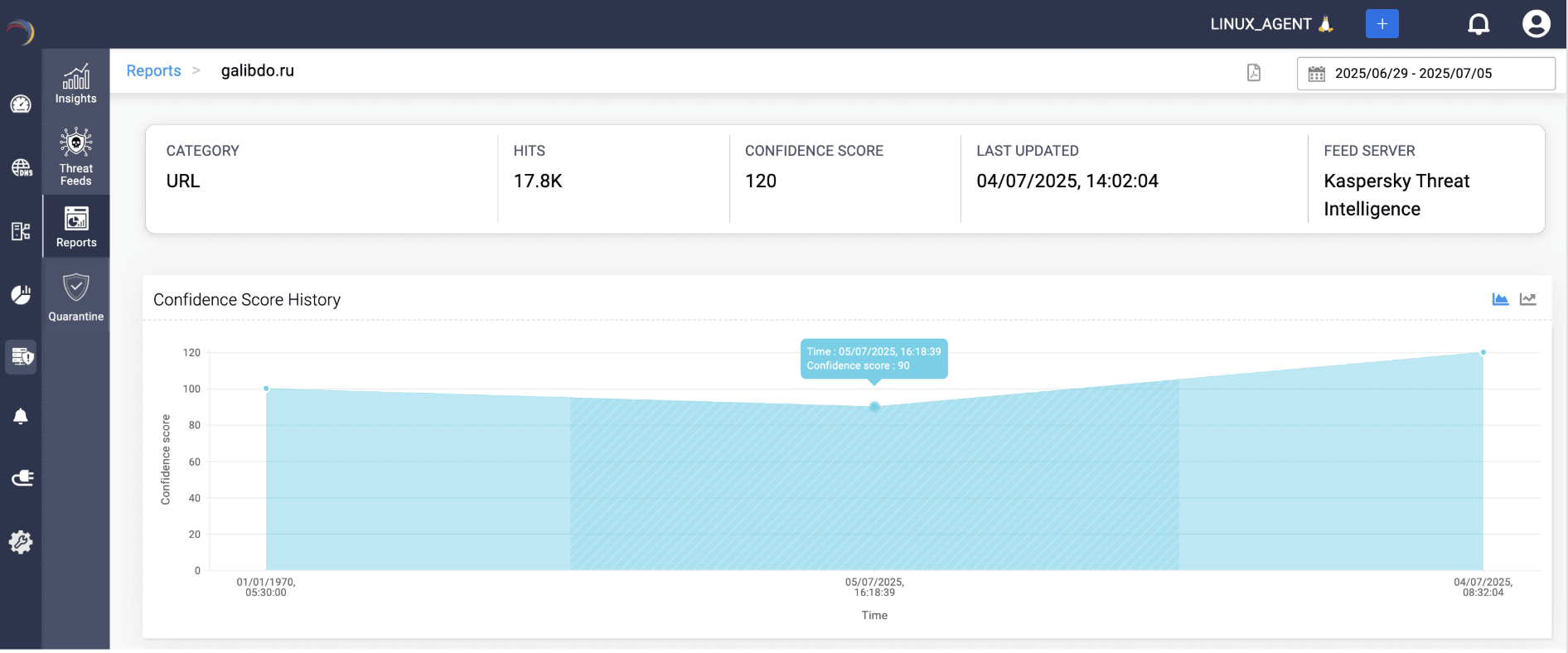
See risk unfold in real time: IoCs are continuously scored, updated, and enriched with traffic context.
Timeline clarity: Track when a domain turned hostile, which is critical for investigations and attack reconstruction.
Vendor-vetted feeds: Each IoC is tied back to its source and timestamp, so intelligence is always current and credible.
Scope of compromise: Map exactly which internal hosts queried the IoC and how often, exposing the blast radius.
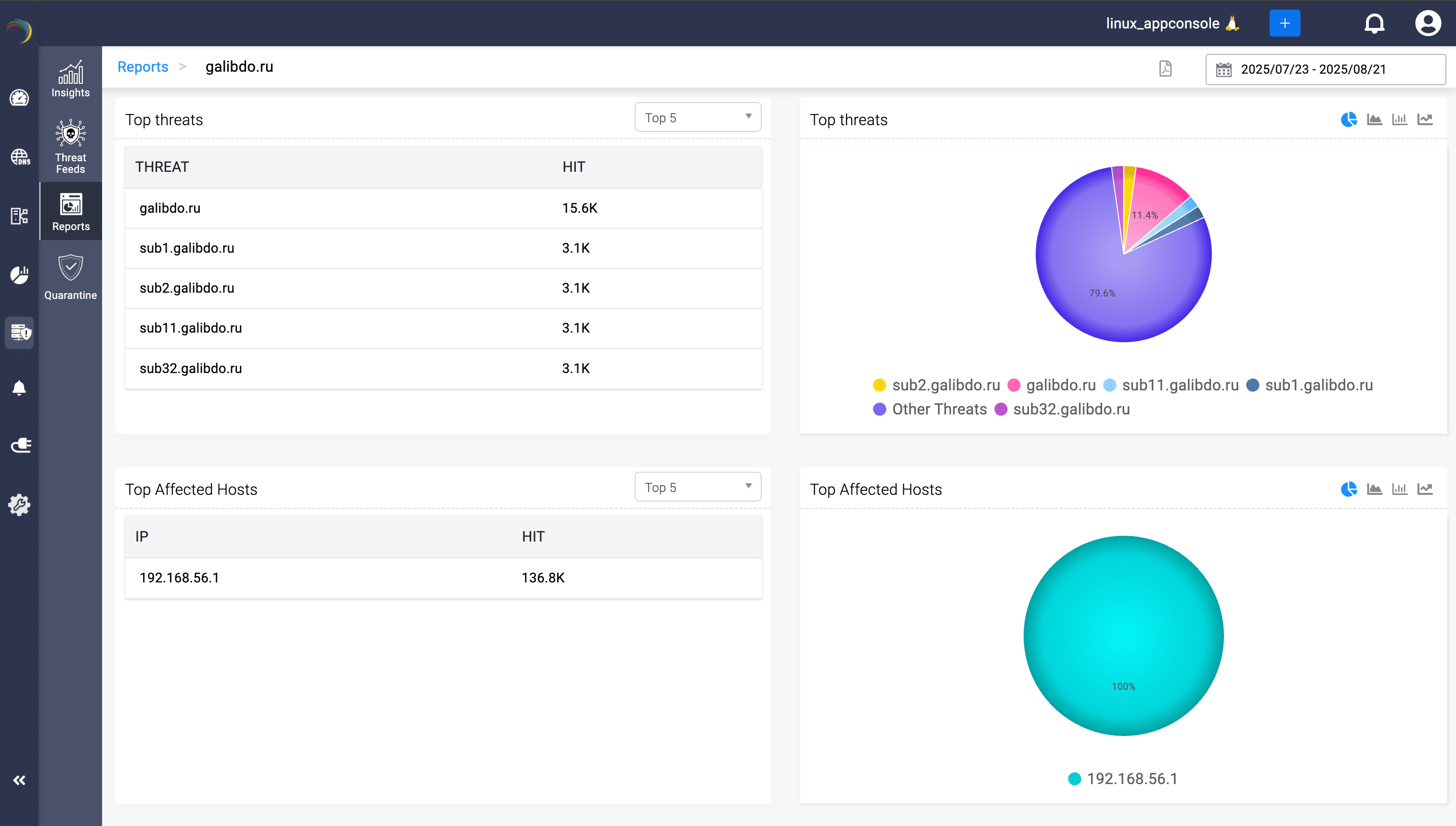
Forensics on demand: Export reports linking domains, subdomains, and DNS record types (e.g., A, TXT, MX) to attack campaigns for audit and SOC escalation.
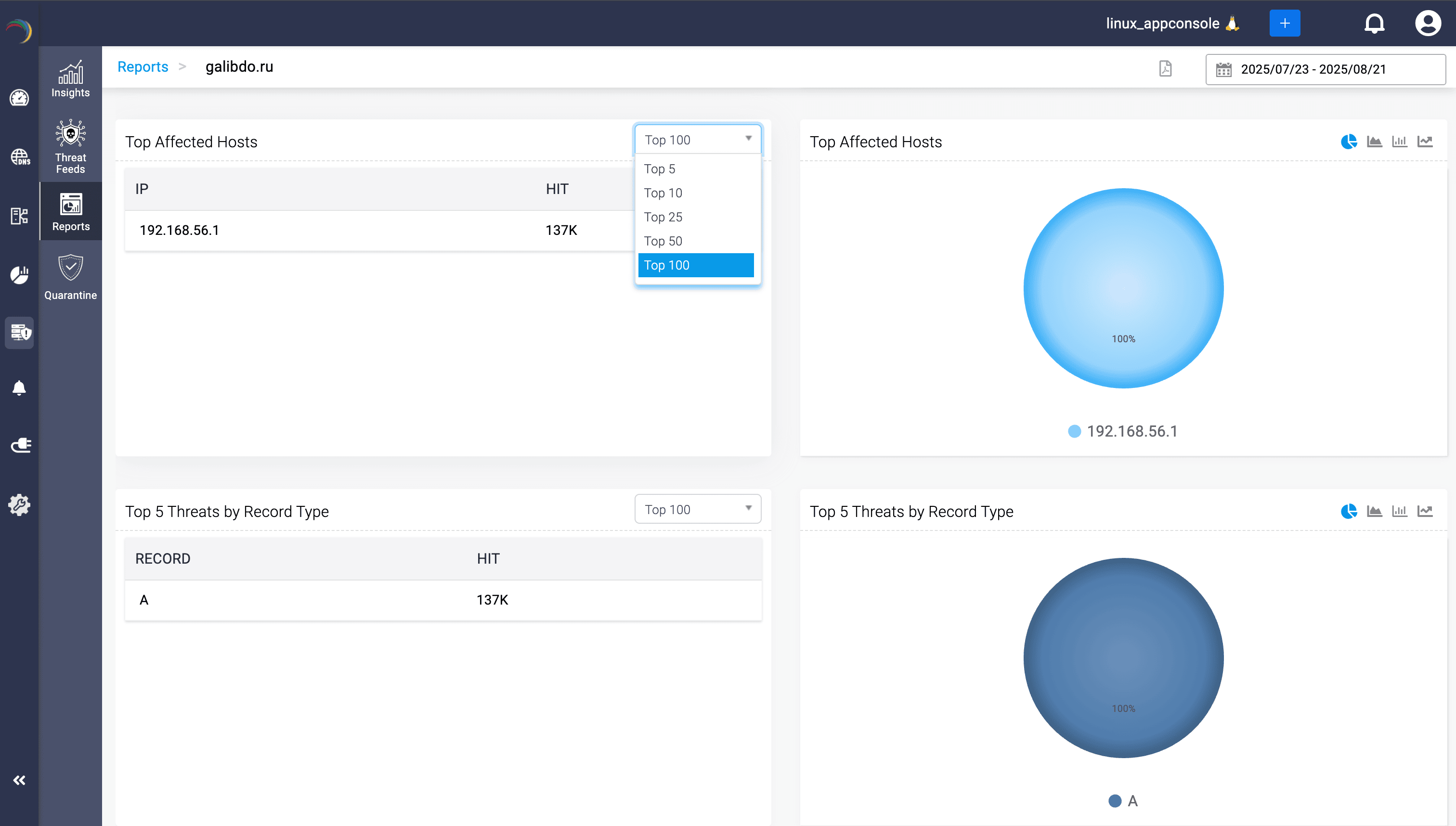
But here’s the shift: Once an IoC in your environment is confirmed by live queries, DDI Central doesn’t stop at spotlighting it. It seamlessly hands off automated containment to the DDR engine as the IoC moves from being watched to actively blocked.
That’s where DDR comes to the forefront. Flagged threats are quarantined at the DNS or DHCP layer in real time, without waiting for human intervention.
3. DNS DDR: From detection to containment
Every breach has a moment of truth: What happens the instant you spot malicious behavior but before it spreads? In that gap, most defenses lag while waiting for manual triage, alerts to be acknowledged, or for someone to hit the kill switch. DNS DDR closes that gap automatically.
Flag, isolate, and defend—on autopilot
The second DDI Central sees a compromised client reaching for a threat domain, the quarantine begins.
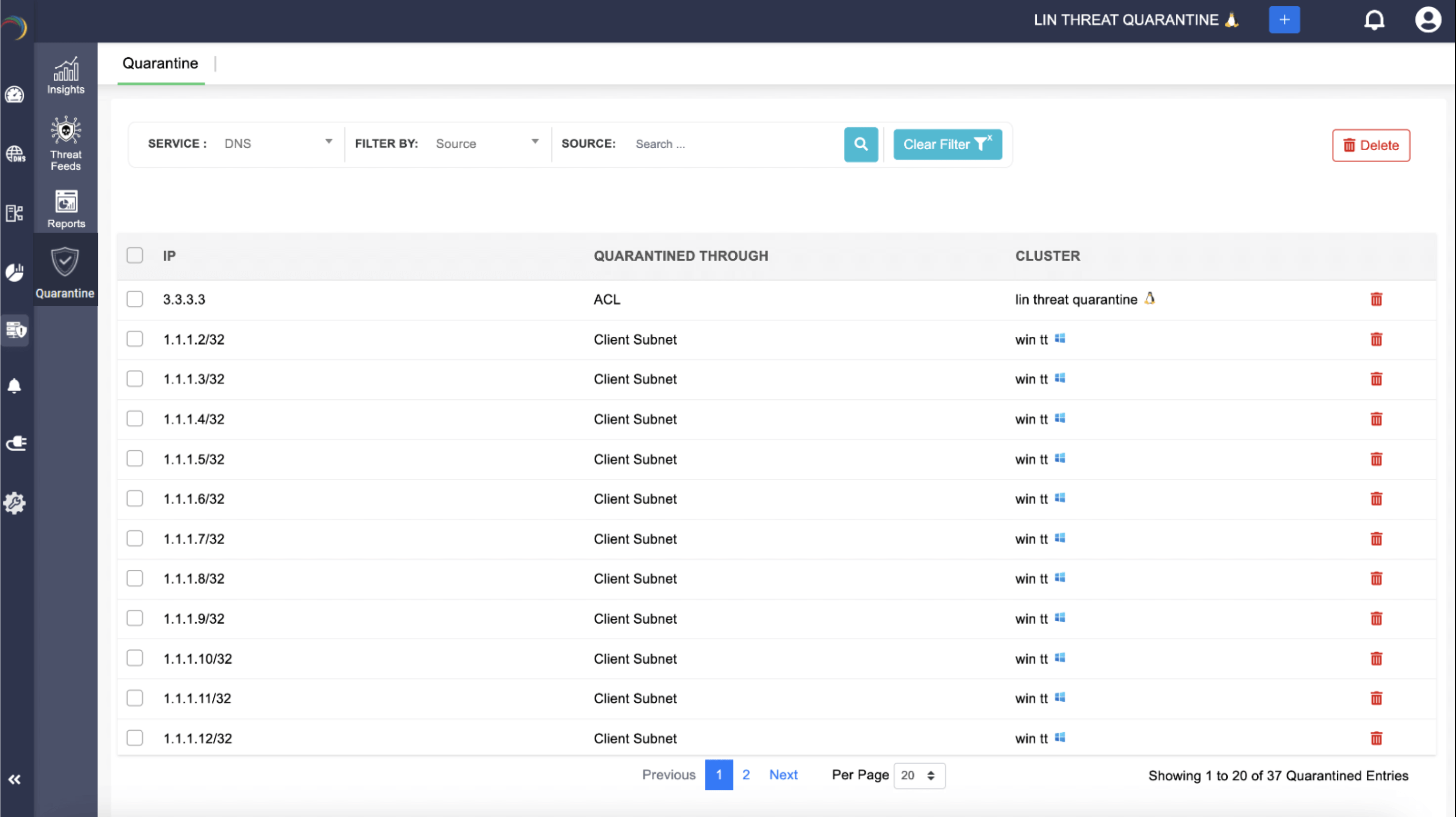
DNS doors slam shut: DNS ACLs on Linux and client-subnet isolation on Windows cut off devices at the first suspicious query. Malware can’t move further when its lookups are blocked at the root.
Containment without delay: No more waiting on admins to isolate endpoints. DDR enforces quarantine instantly, shrinking attacker dwell time from hours to moments.
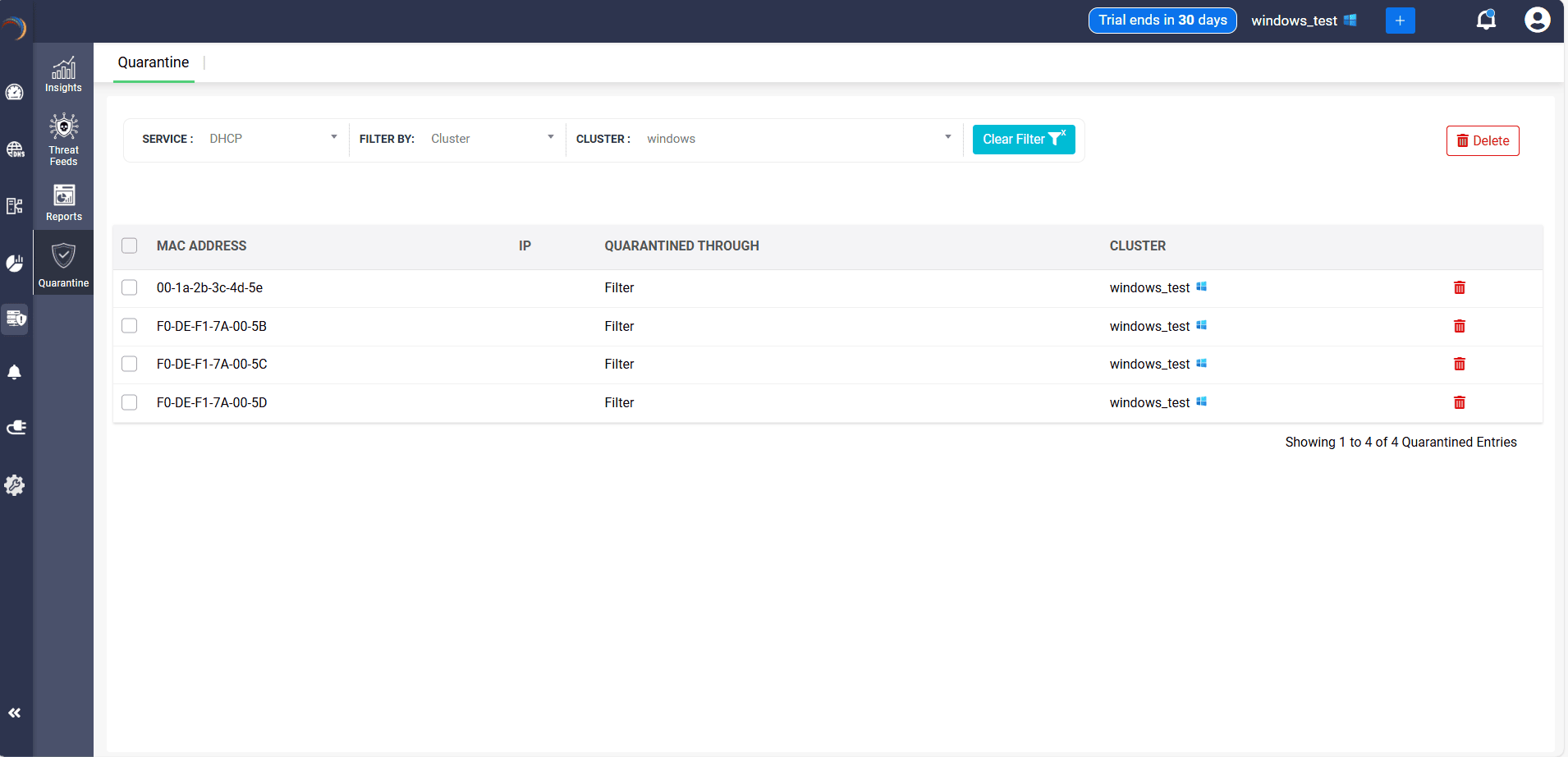
Visibility with precision: The Quarantine dashboard tells you what was blocked, when, how, and why, complete with service, method, cluster, and timestamp.
Your choice: DNS, DHCP, or both
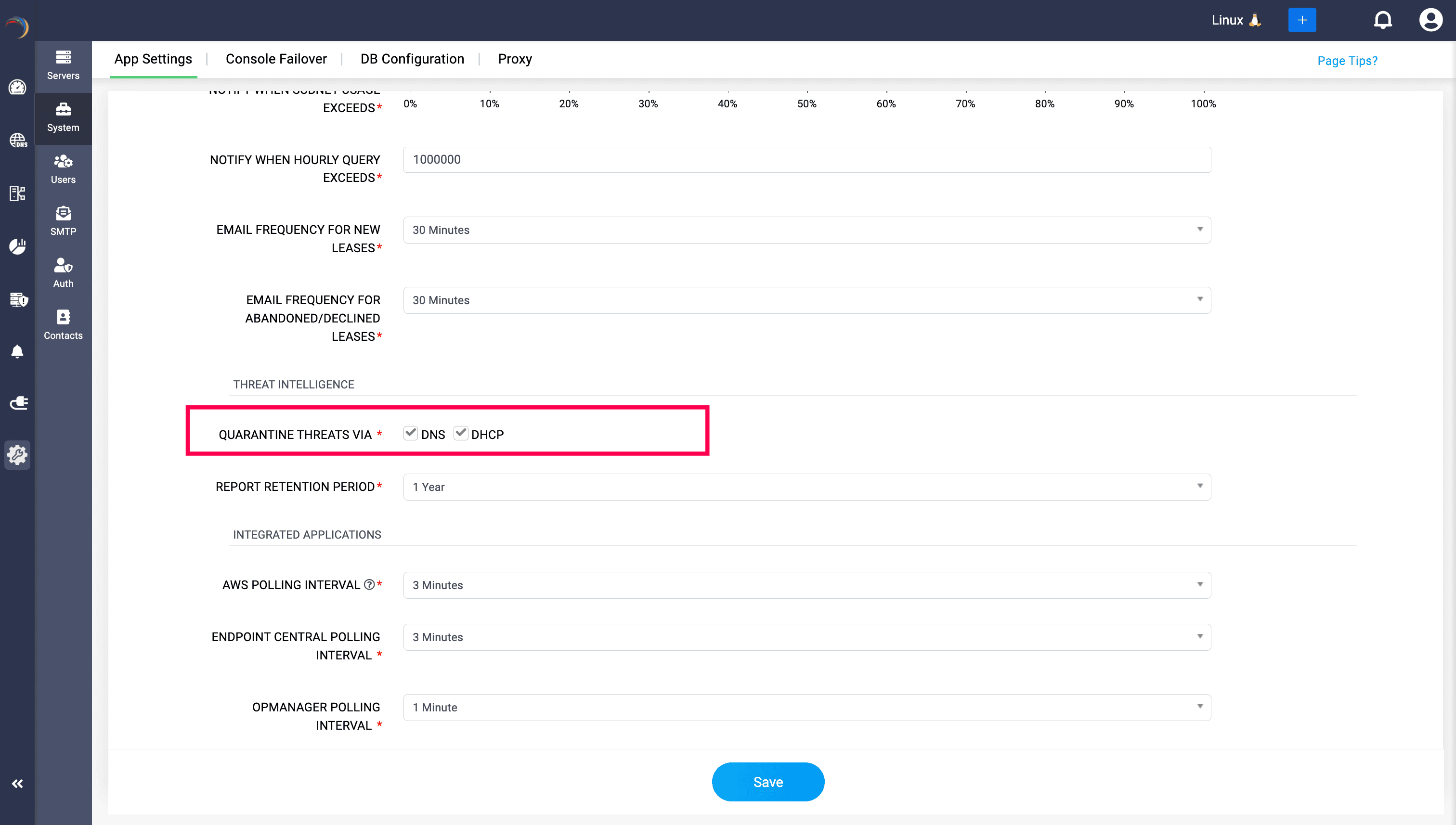
Not every environment is the same. That’s why DDR gives admins flexibility to enforce quarantine at the DNS layer, DHCP layer, or both, tailoring containment to how threats propagate inside your network.
From MAC address to MAC arrest
On the DHCP side, DDR ensures infected devices can’t sneak back in:
MAC filtering on Windows denies new IP leases permanently, blocking compromised endpoints from ever getting back on the grid.
Restricted pools on Linux funnel flagged MACs into isolated subnets built for quarantine, eliminating lateral movement.
No lease, no lurking. Whether by dynamic lease or even a manual IP setup, the DHCP server uses the MAC as the gatekeeper. Once flagged, that MAC is locked out forever.
Catch, contain, and cut off threats
By turning threat intelligence into live firewall rules and DHCP policies in real time, DDR enforces policy at network scale automatically. Compromised clients are quarantined the moment they act suspicious, attackers lose their foothold, and admins regain the upper hand.
4. Quarantine control: Manual release, informed choice
With DDI Central, containment happens instantly—the moment a client queries a flagged domain or a suspicious IP, the DDR engine slams the doors shut. The compromised host is cut off at the DNS or DHCP layer before it can spread the infection. But containment isn’t the end of the story.
Handing control back to the admin
Once devices are quarantined automatically, the final decision rests with the admin:
Immediate alerts: The admin receives an email notification the moment a client is quarantined, with details of the IoC, quarantine method, and timestamp.
Decision time: While the system isolates automatically, the choice to restore access is always made by a human. An admin can release the host from the DNS ACL, remove it from the restricted DHCP scope, or keep it contained until remediation is complete.
One console for cleanup: The Quarantine dashboard makes triage simple. You can filter by IP, MAC, or method, review the activity trail, and revive a device to rejoin the network by deleting its entry from the quarantine dashboard.
While automated detection and response shrink the dwell time, the final say rests with the admin. This balance of automation and oversight ensures that threats are contained without delay, yet legitimate business operations can be restored quickly and safely.
A dashboard bolstered with threat feeds and forensics
The journey starts with onboarding feeds, moves through IoC Spotlight, and flows into automated quarantine with DDR and admin-controlled lock and release. Each step builds the layers of a living defense system.
And it all converges here: the Threat Insights dashboard.
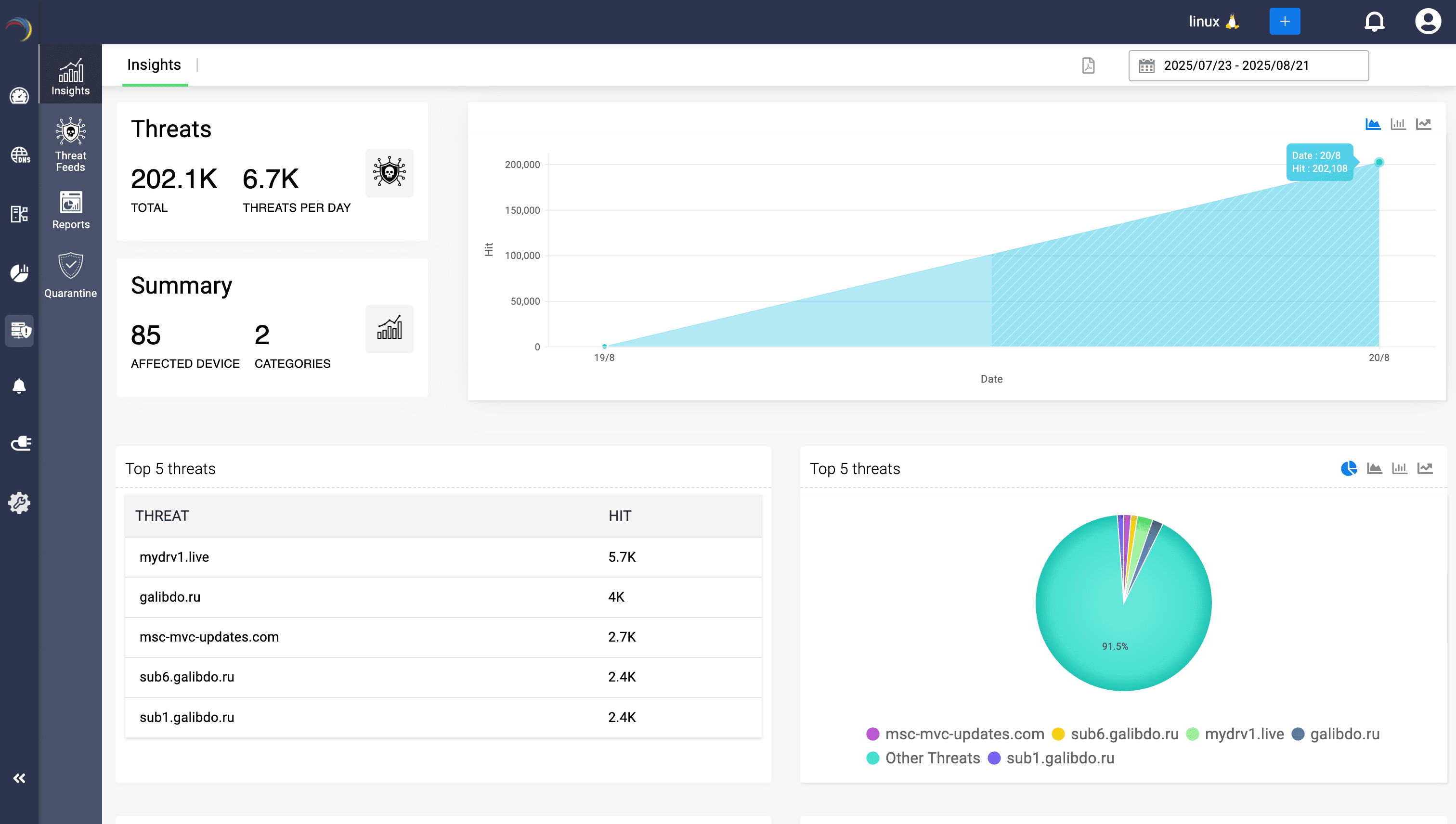
Think of this dashboard as your air-traffic control tower for DNS security. Feeds converge, IoCs are tracked, quarantines are logged, and threats are visualized in real time.
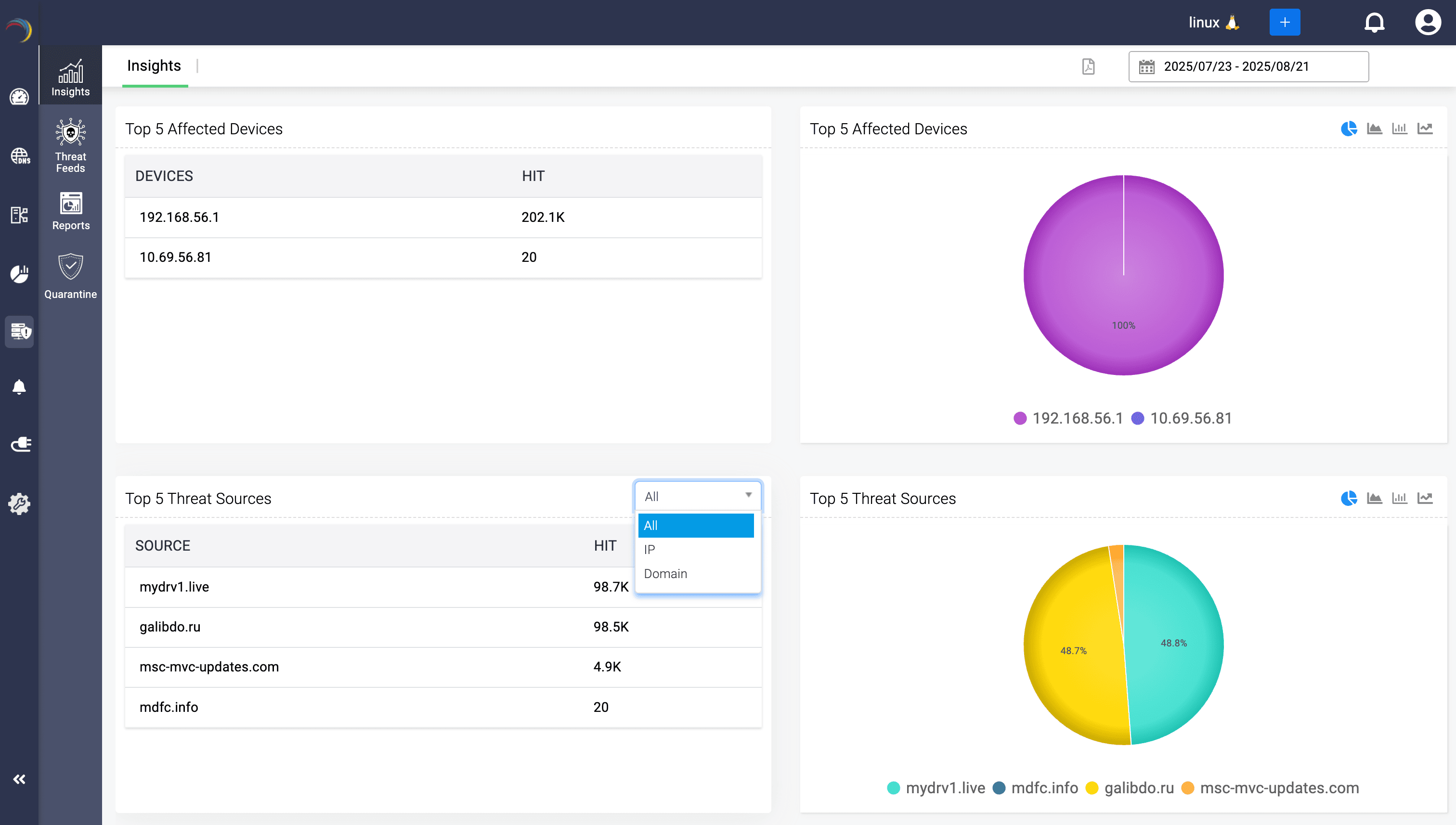
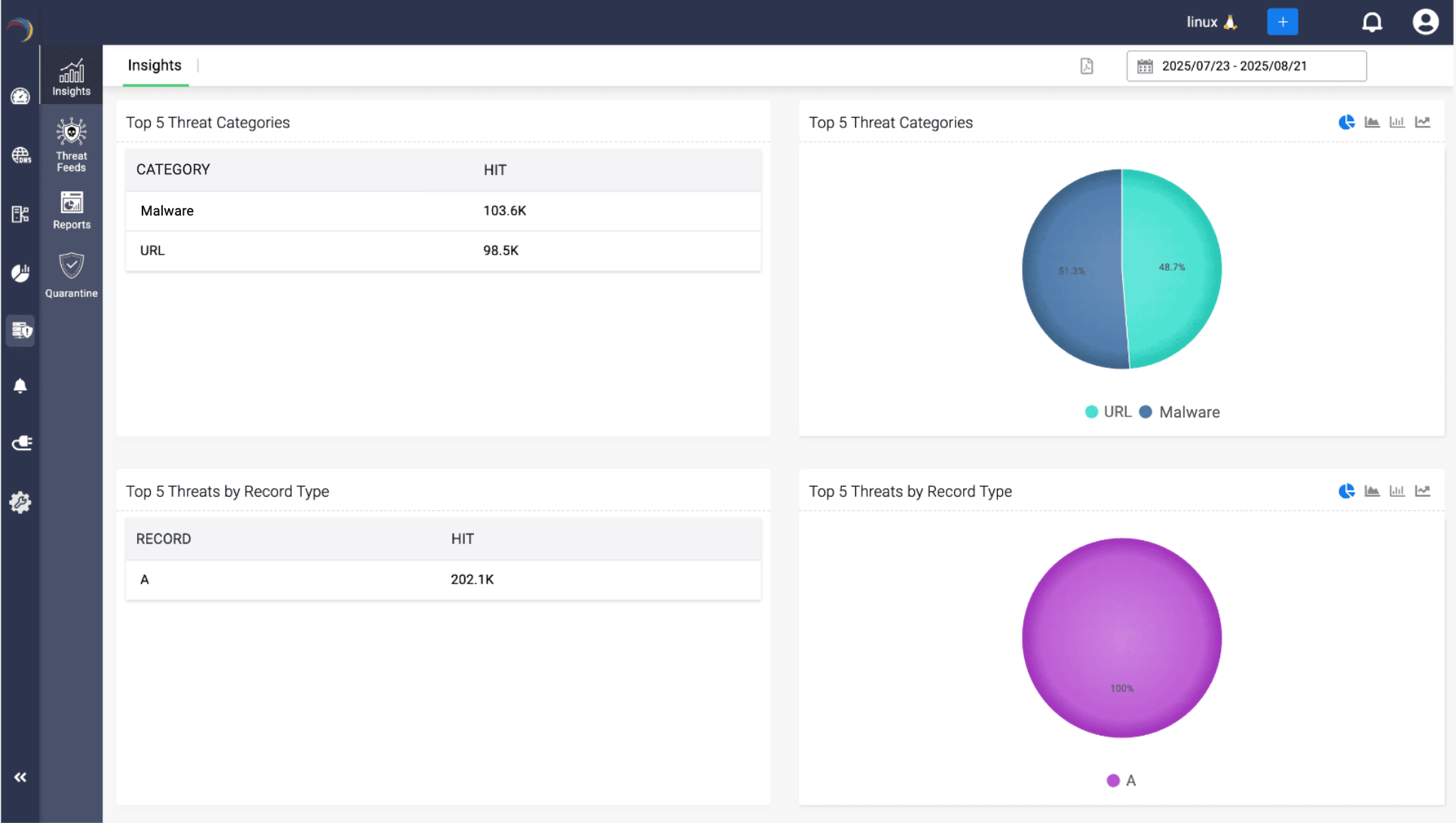
Admins get the bird’s-eye view they need, including which domains are under attack, which devices are compromised, what tactics adversaries are using, and where risk is concentrating.
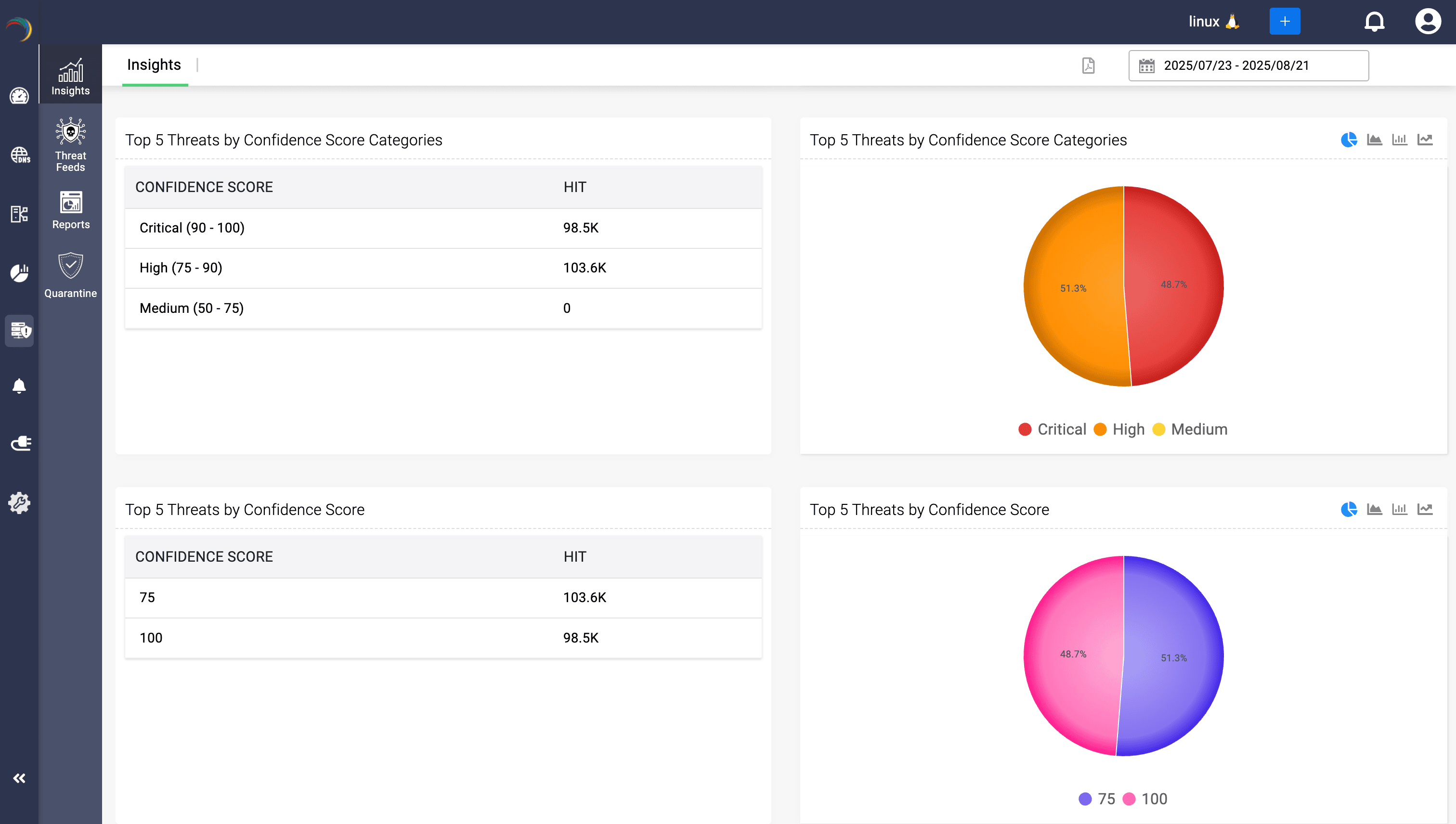
Admins get to track risk distribution over time using stratified counts to see whether high-confidence threats are rising or falling, helping gauge the shifting threat climate in your environment.
No more swivel-chair analysis, no log-diving, no guesswork. Just one console that transforms scattered threat signals into a coherent, actionable picture.
With the Threat Insights dashboard, DDI Central doesn’t just stop threats—it showcases their life cycle, from the first query to final containment, because visibility is victory.
Ready to fortify your first line of defense?
Your network doesn’t have to play catch-up. With DDI Central, DNS becomes more than resolution—it becomes resilience in action. Armed with live threat intelligence and automated detection and response, you gain a firewall that hunts back, protects proactively, and keeps your business moving without disruption.
The power to stay ahead of evolving threats is already at your fingertips.
Start your 30-day, free trialor request a personalized demoand experience DNS security that grows stronger with every query.