DDI Central 5.5 is here—with DNS threat intelligence, OpManager Plus integration, and more!
We’re excited to announce the launch of DDI Central version 5.5, a release shaped by the most demanded features from our customers and the ever-growing need for stronger security at the core of enterprise networks. With this version, the spotlight is on security, resiliency, and device-diagnostics driven IP address management. It's packed with advanced features like DNS threat intelligence, DNS detection and response (DDR), and enhanced DNS protection, built on top of our already security-rich DDI stack.
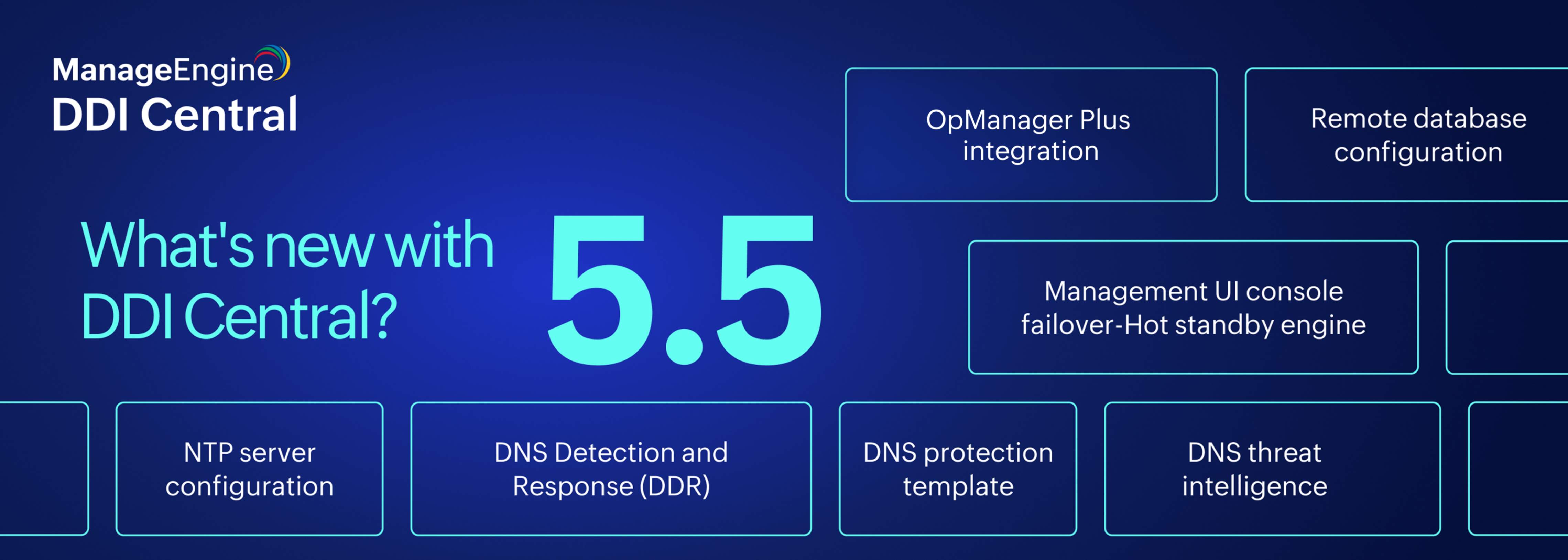
What's new in DDI Central version 5.5?
Let’s walk through the seven advanced features that make this version a game-changer.
Feature 1: DNS threat intelligence
DDI Central’s DNS threat intelligence equips admins with real-time visibility into malicious domains and IPs, powered by live, multi-vendor feeds like ManageEngine's own advanced CloudDNS threat intelligence engine, Kaspersky, and AlienVault. With automatic synchronization, every new IoC is instantly enforced at the resolver layer, eliminating manual updates and reducing exposure to zero-day threats.
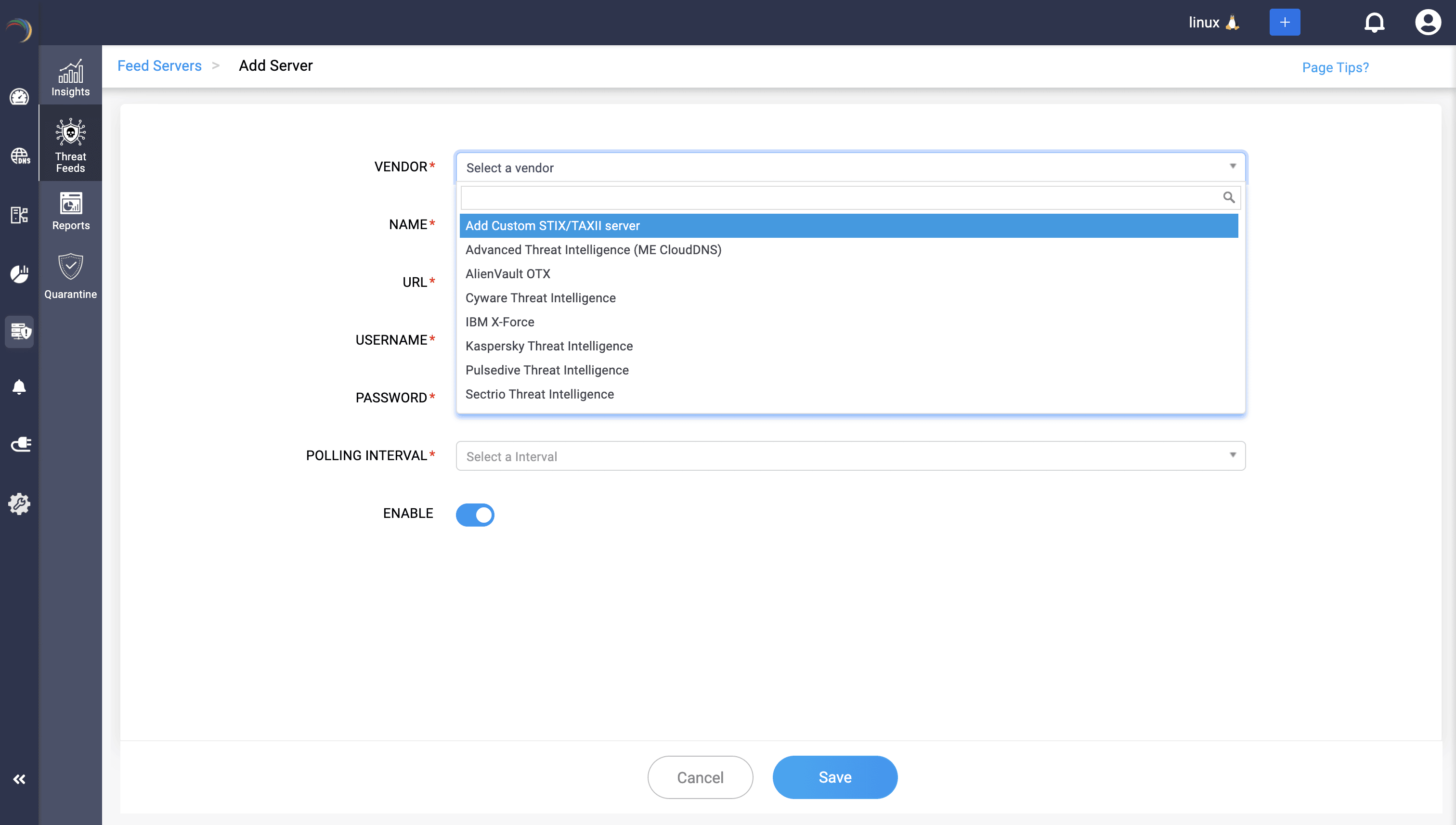
Admins get a watchtower view of threats, consolidating confidence scores, feed sources, categories, and record types, all visualized through rich charts and drill-downs. Each indicator can be traced back to its source, linked to affected hosts, and tracked over time, simplifying investigations and containment.
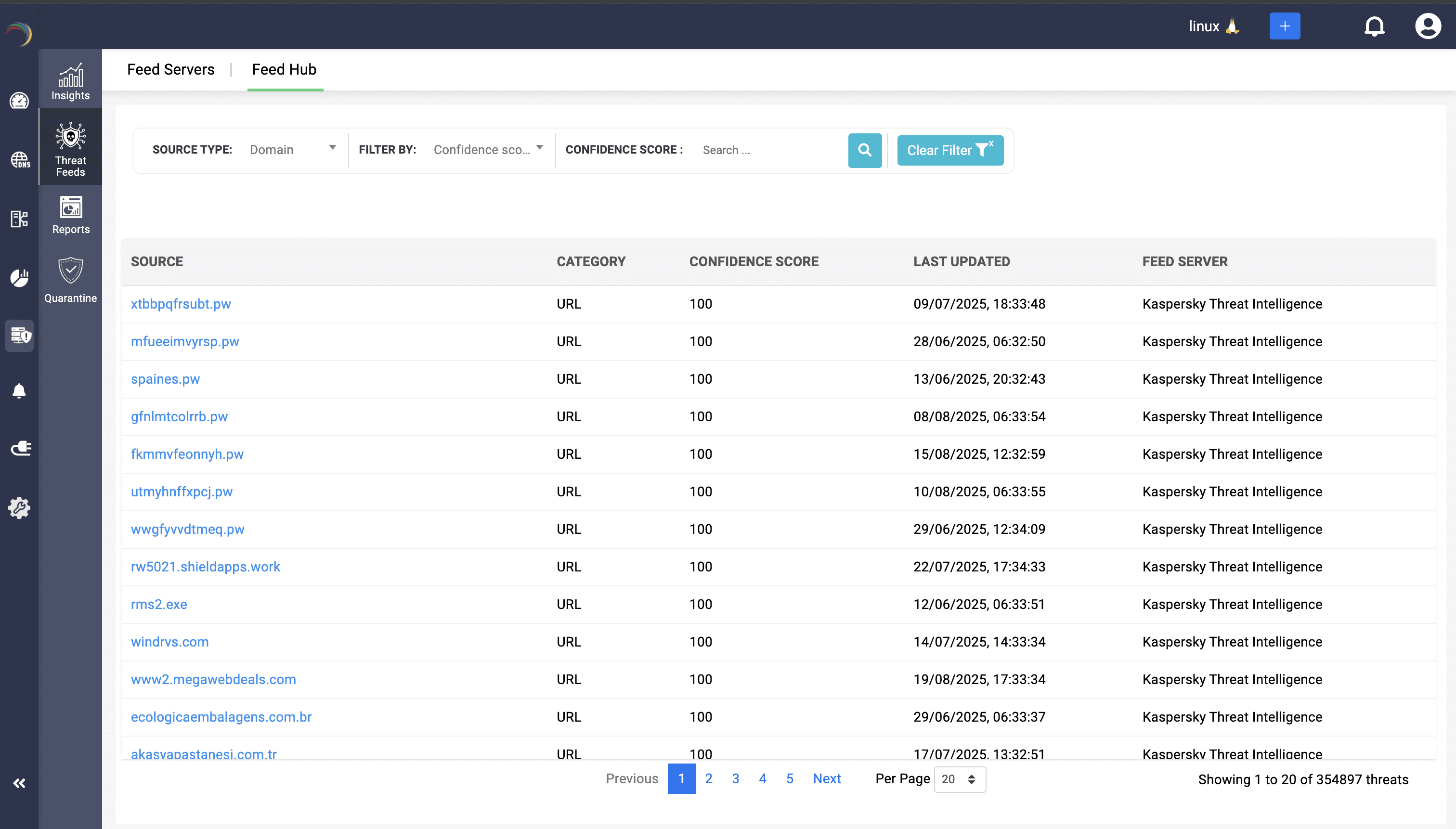
Beyond detection, DDI Central automates policy enforcement by converting feed data into DNS and DHCP rules, ensuring consistent protection across your infrastructure. Reports on each IoC, whether a malicious domain name, URL, or IP, can be exported to PDF format, supporting compliance audits and SOC handoffs with evidence-grade detail.
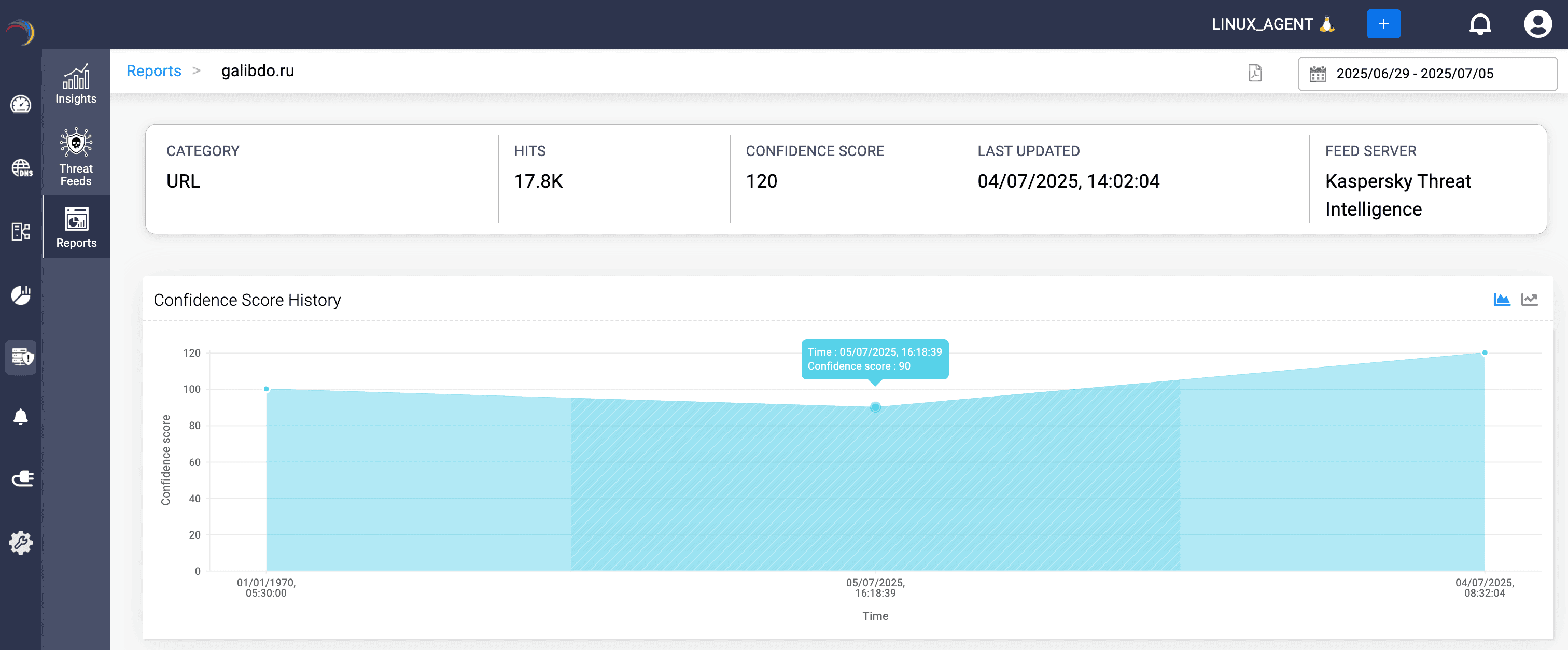
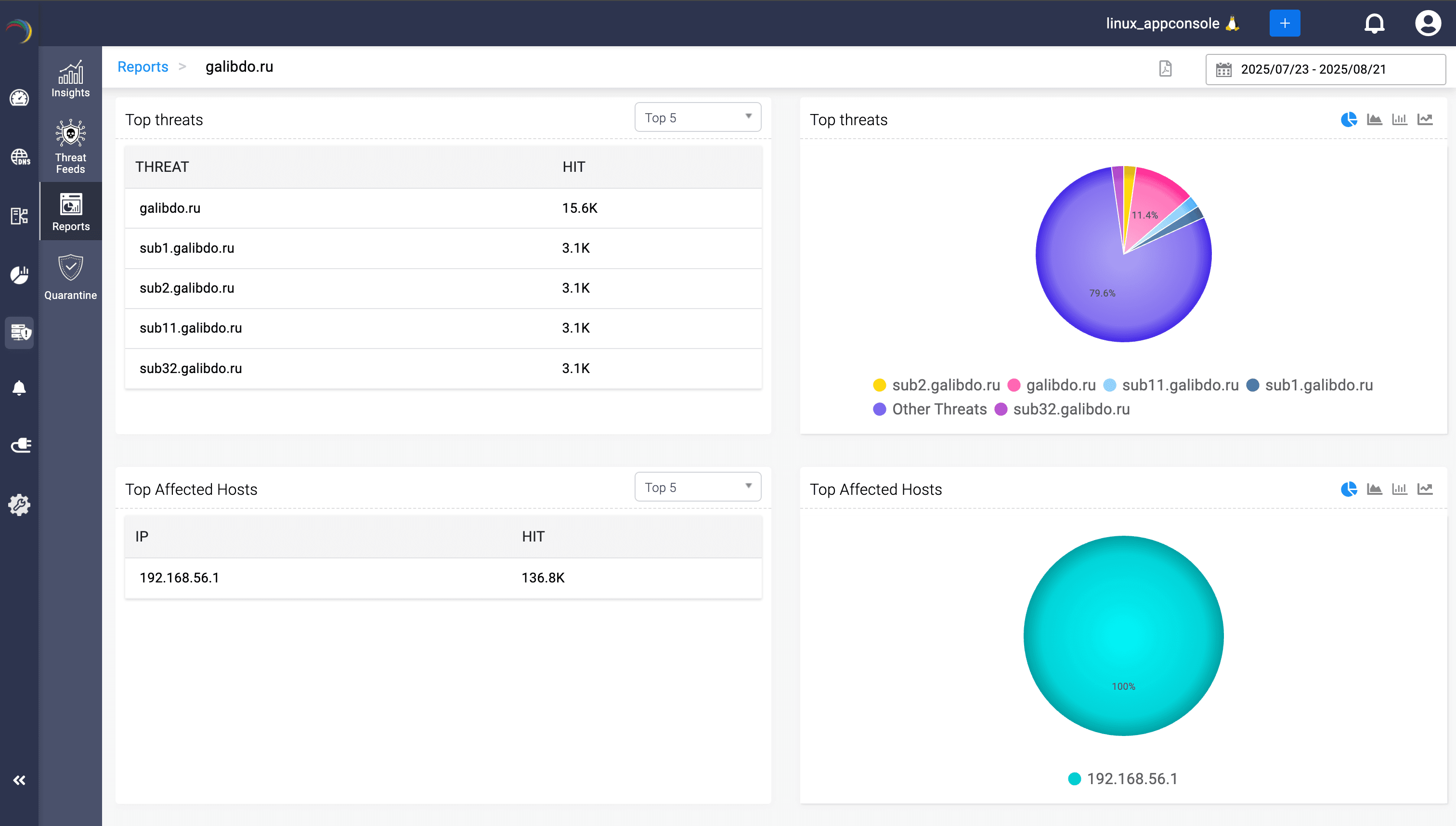
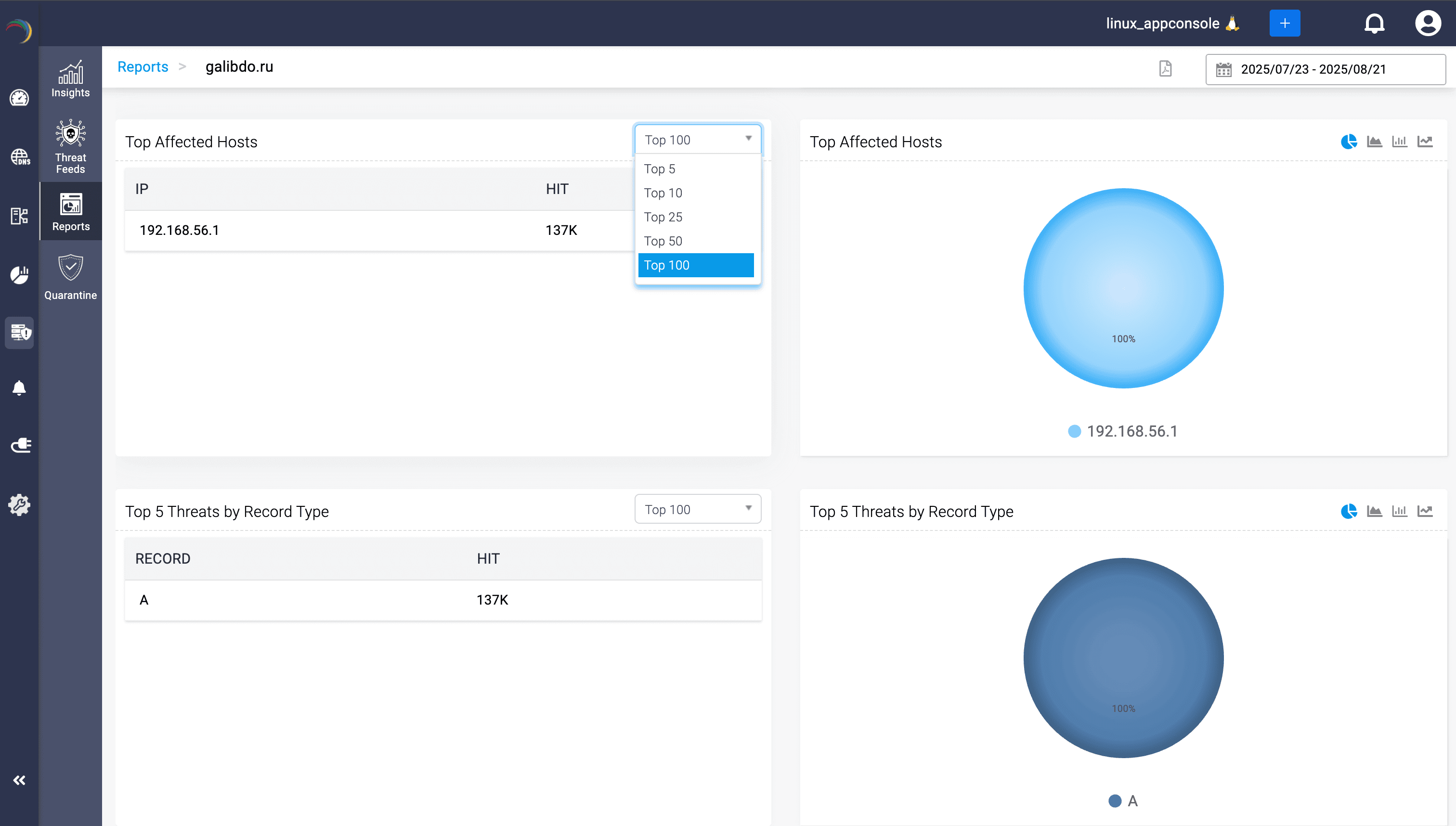
With DNS threat intelligence, raw DNS queries become actionable insights. Admins can see which devices are compromised, which domains are trending malicious, and where attacker tactics are shifting—giving them clarity, speed, and confidence in their next move.
Feature 2: DNS detection and response (DDR) — Containment on detection
Detecting a malicious domain is one thing. Stopping the device that reached out to it before it can spread malware across your network is another. That’s where DDR comes in.
With DDR, containment starts at the domain-resolution layer. On Linux, DNS ACLs immediately cut off compromised devices; on Windows, subnet-based isolation locks down devices the moment they try to query a flagged domain. No waiting, no manual intervention—threat lookups are shut down the instant they appear.
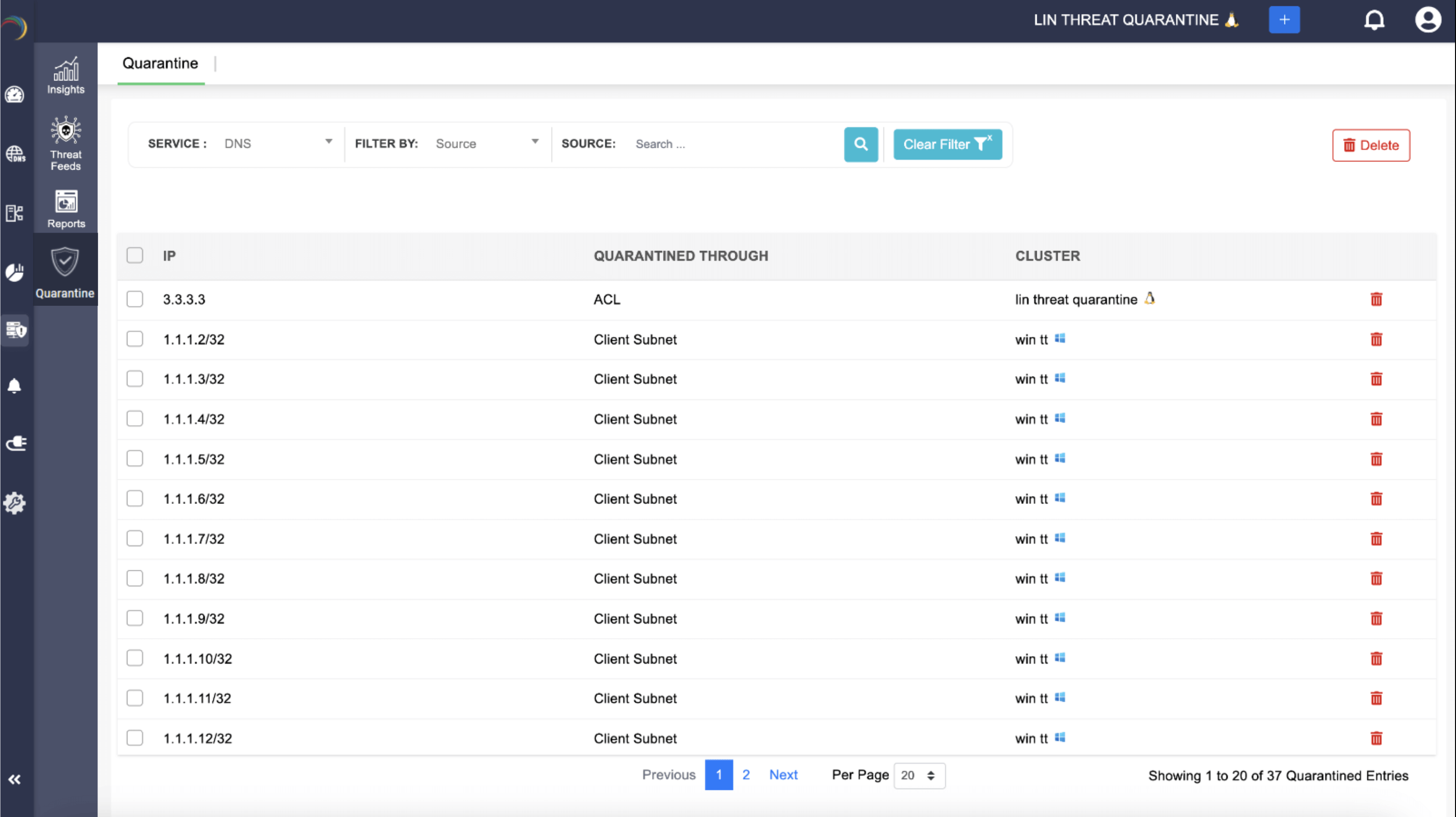
And it doesn’t stop at DNS. DDR offers DHCP quarantine, blocking rogue MAC addresses from ever getting a new lease and shrinking their dwell time in the network. In Linux clusters, they’re funneled into a restricted subnet built just for quarantine. In Windows, MAC filtering ensures misbehaving devices can’t sneak back onto the network. With no lease, no lurking, and no lateral movement, there's no data exfiltration.
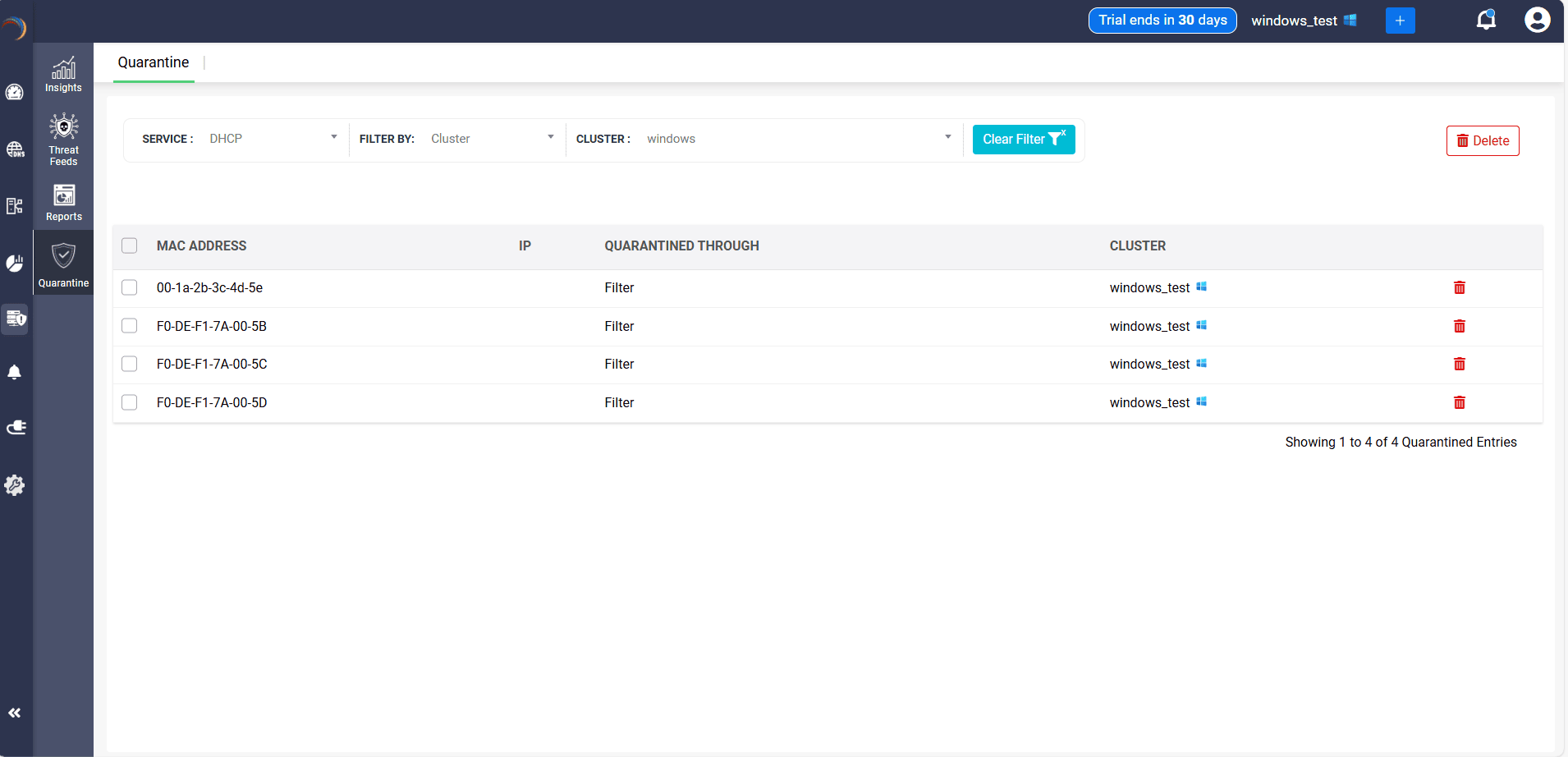
Admins still keep full visibility. The Quarantine dashboard shows exactly what was blocked, when, and why—complete with cluster, service, and timestamps. That means clean attribution, informed decision-making, and audit-ready records.
Together, these layers make DDR a catch-contain-cutoff engine. Threats are spotted at the DNS layer, devices are quarantined at the DHCP layer, and admins stay one step ahead of lateral movement—without lifting a finger.
Feature 3: DDI Central + OpManager Plus — Unlocking layer 2 traceability
Every IP lease is more than just an address—it’s a window into the health of the device behind it. With the new DDI Central + OpManager Plus integration, that window becomes a diagnostic cockpit at your fingertips.
From a single IP, admins can drill down into live device telemetry, including availability, packet loss, latency, CPU and memory usage, and even the exact switch port a device connects to. No more swivel-chair monitoring across tools; all relevant data lives in one console.
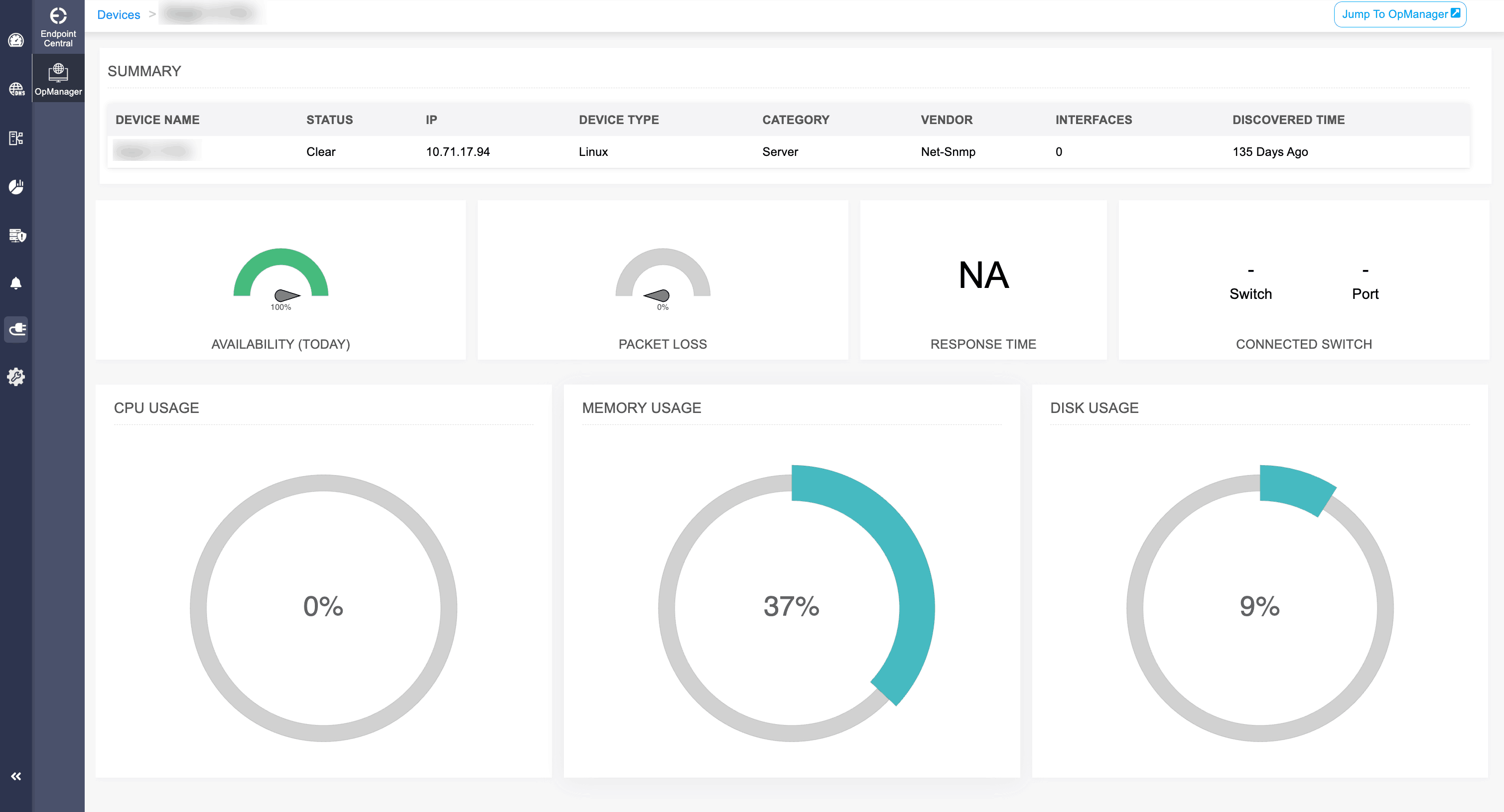
This integration also tracks uptime patterns across hours, days, and weeks, letting teams separate real outages from routine maintenance. Add in anomaly detection for rogue IPs or misprovisioned devices, and admins gain the ability to spot the irregular, investigate the root cause, and take decisive action faster.
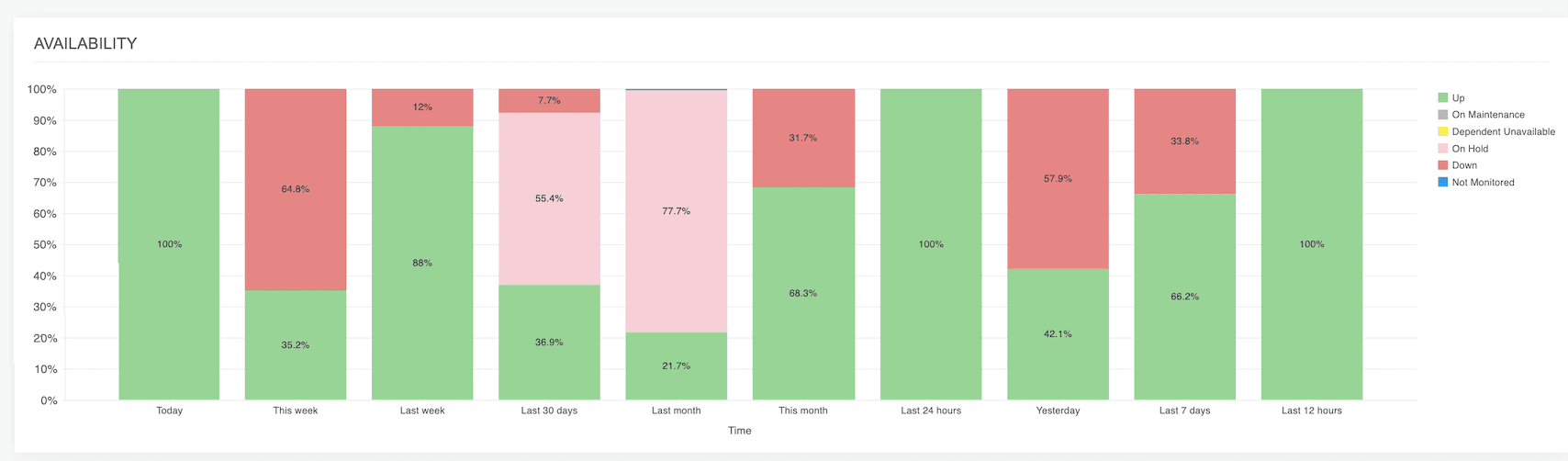
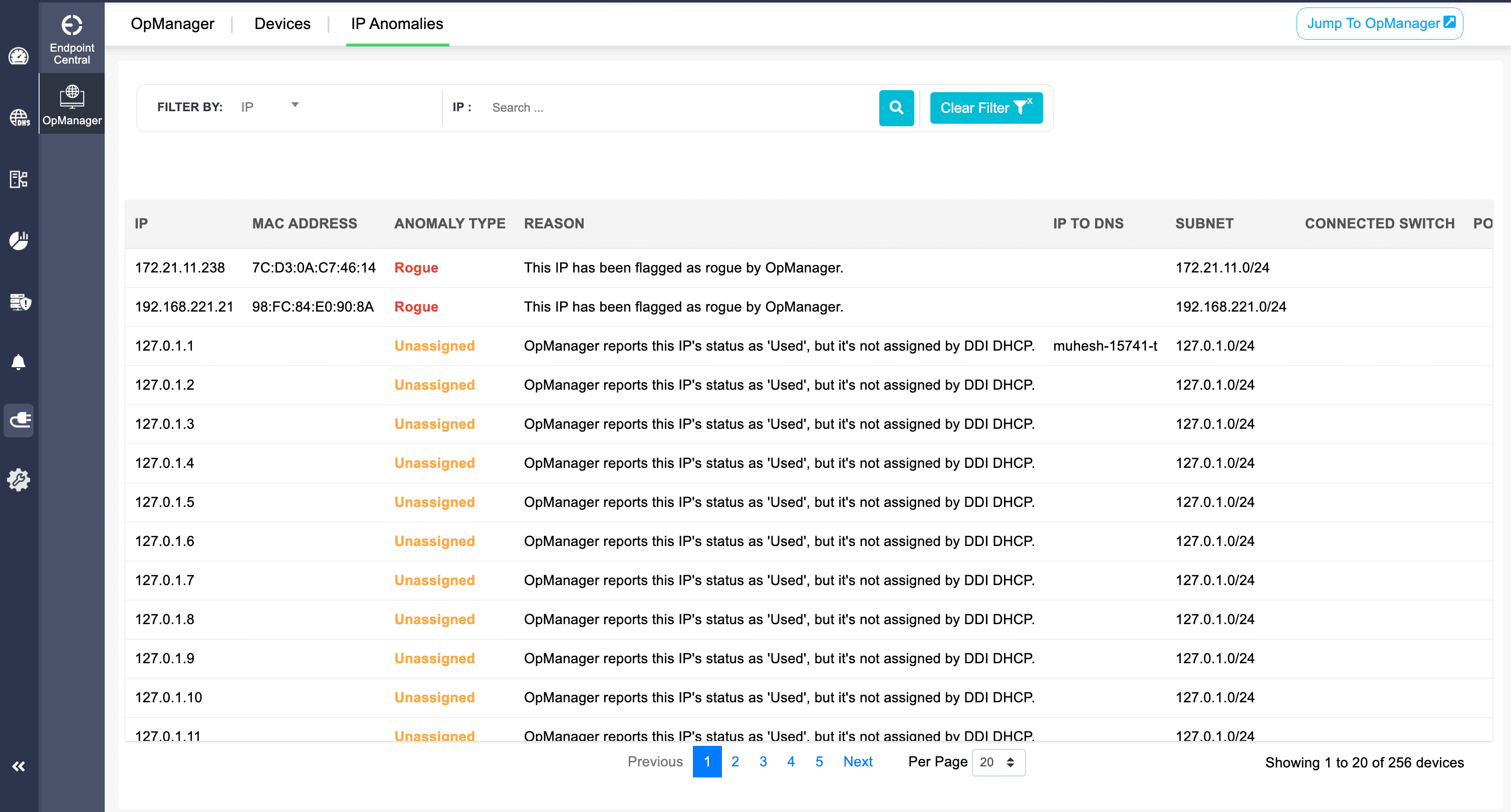
The value is simple: What starts as an IP lease in IPAM opens into a real-time cockpit of device health and diagnostics, giving admins the clarity they need to troubleshoot smarter and keep services resilient.
Feature 4: NTP server configuration — Centralized, secure, and precise
In every enterprise network, time is the invisible backbone. Network Time Protocol (NTP) servers keep clocks aligned across devices, ensuring that logs are correlated, certificates validated, and automated tasks executed with precision. Without synchronized time, investigations drift, compliance suffers, and even basic trust in system events breaks down.
Traditionally, managing NTP at scale has been messy—configured server by server, vulnerable to drift, and open to spoofing attacks if left unsecured. Peer servers exchange time data with each other to maintain accuracy and redundancy, but without central oversight, visibility and consistency are hard to guarantee.
DDI Central 5.5 changes that by introducing centralized NTP server configuration, turning time services into a securely managed part of your infrastructure.
With version 5.5, DDI Central introduces centralized NTP server configuration, giving admins a single console to define peers, enforce restrictions, and monitor performance across environments. Setup is no longer a manual, server-by-server process; we've streamlined onboarding with reusable profiles that guarantee consistency and eliminate drift.
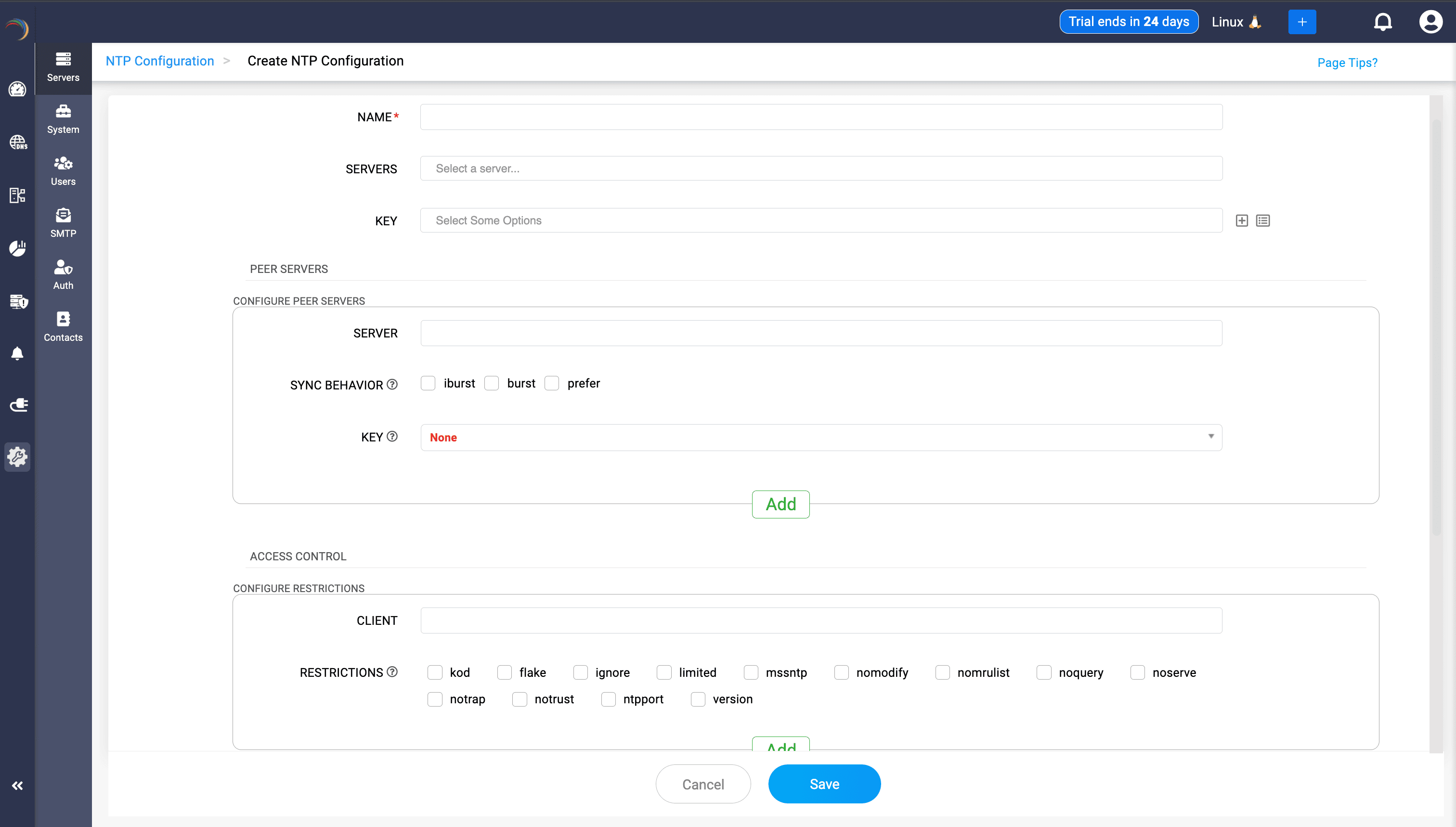
Admins can fine-tune synchronization logic with iburst, burst, and prefer flags.
Here’s what they do:
iburst: When a time server starts up, this flag tells its NTP clients to send a burst of packets (usually four to eight) in quick succession to speed up the initial sync. This is especially helpful when starting with an empty clock.
burst: Unlike iburst, which operates at startup, this flag sends multiple queries during each polling interval, improving accuracy on stable networks by reducing jitter.
prefer: This lets the admin mark a preferred peer among multiple upstream time sources. If all peers are valid, the preferred peer takes precedence during time selection.
These help in ensuring precise timing even in HA or latency-sensitive infrastructures. Built-in support for authenticated peering protects against rogue time injections or spoofed responses.
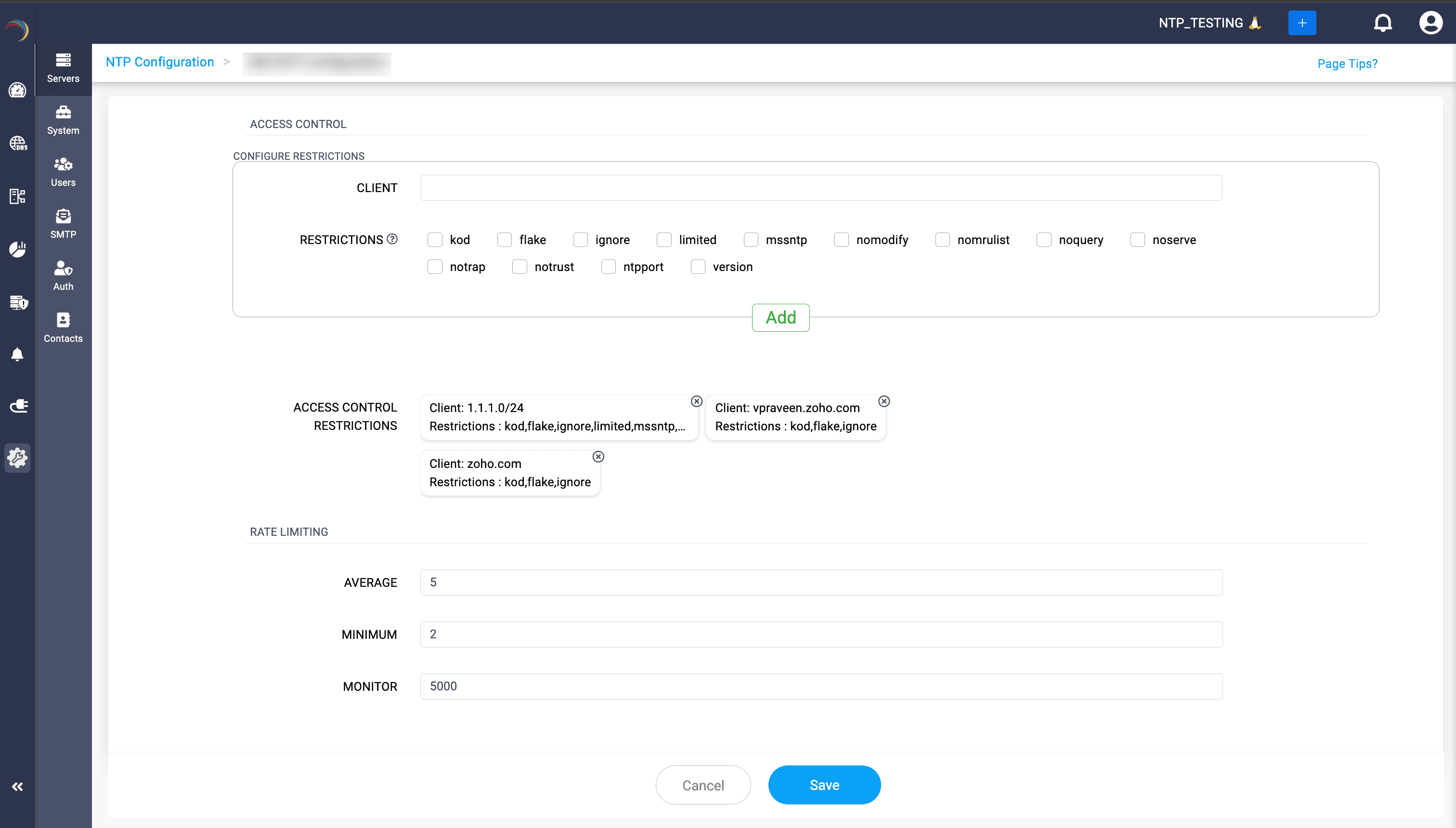
Control also extends to who can sync with your time servers. Admins can use granular restrictions to add trusted clients or subnets to allowlists, apply layered access boundaries, and even set rate limits to prevent overload in high-density environments. Every policy is reusable, ensuring repeatable best practices at enterprise scale.
The visibility doesn’t stop at configuration. A unified performance dashboard tracks jitter, offset, stability, and frequency in real time for each onboarded NTP server. Admins can establish baselines, flag anomalies, and support forensic investigations with precision—all from a single view.
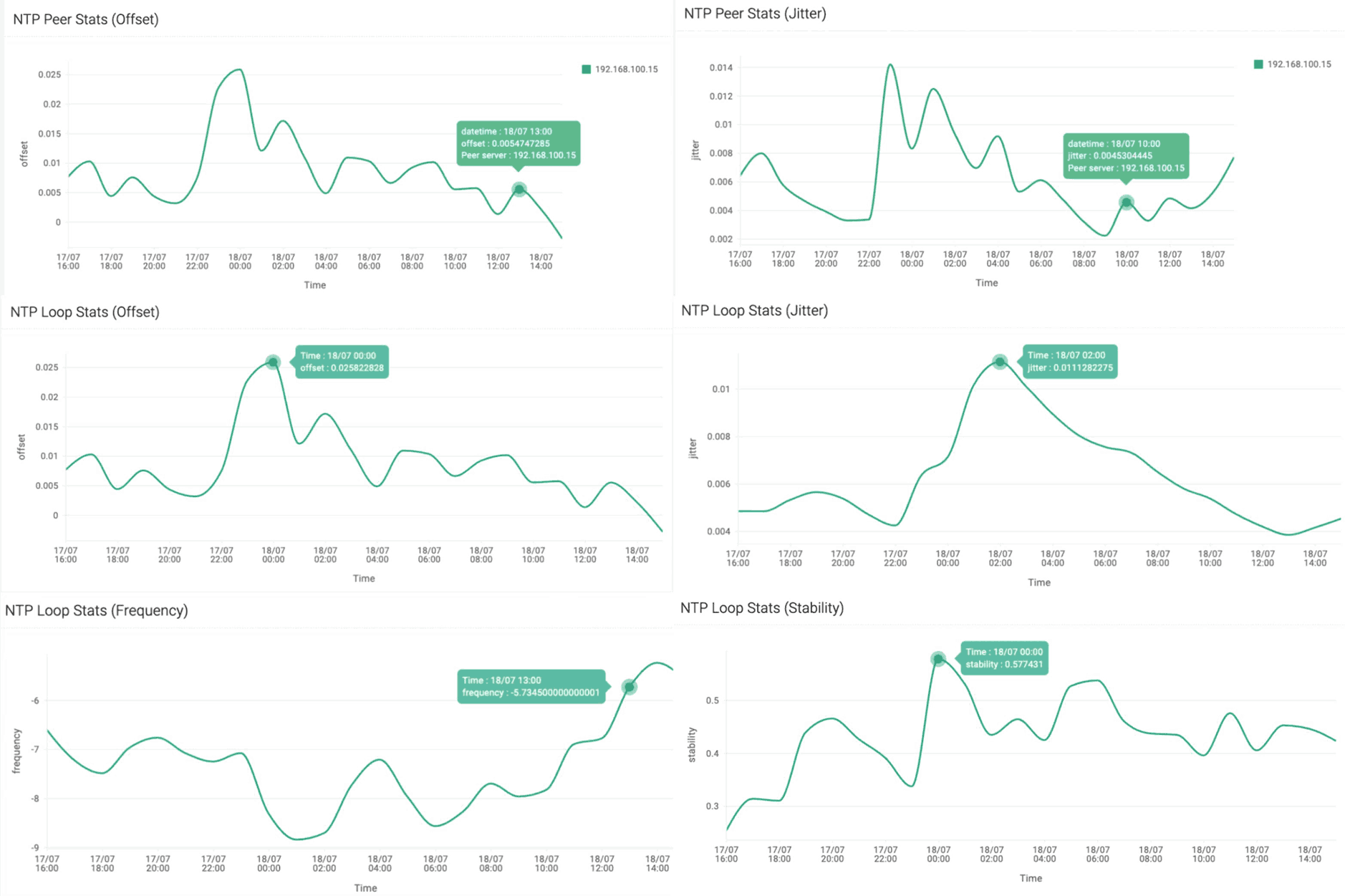
The result is a hardened time service that's easy to configure, secure against abuse, and transparent to monitor. With DDI Central 5.5, time synchronization is no longer a hidden dependency; it becomes an actively managed, reliable part of your network’s backbone.
Feature 5: DNS protection templates — Resilient defense that's ready to deploy
In any modern network, DNS is both the backbone of connectivity and a high-value target for abuse. A flood of queries—whether from misconfigured clients, malicious bots, or full-blown DDoS attacks—can cripple service availability in seconds. DNS servers must enforce guardrails that keep traffic fair, balanced, and secure.
That’s where DNS protection templates in DDI Central 5.5 come in.
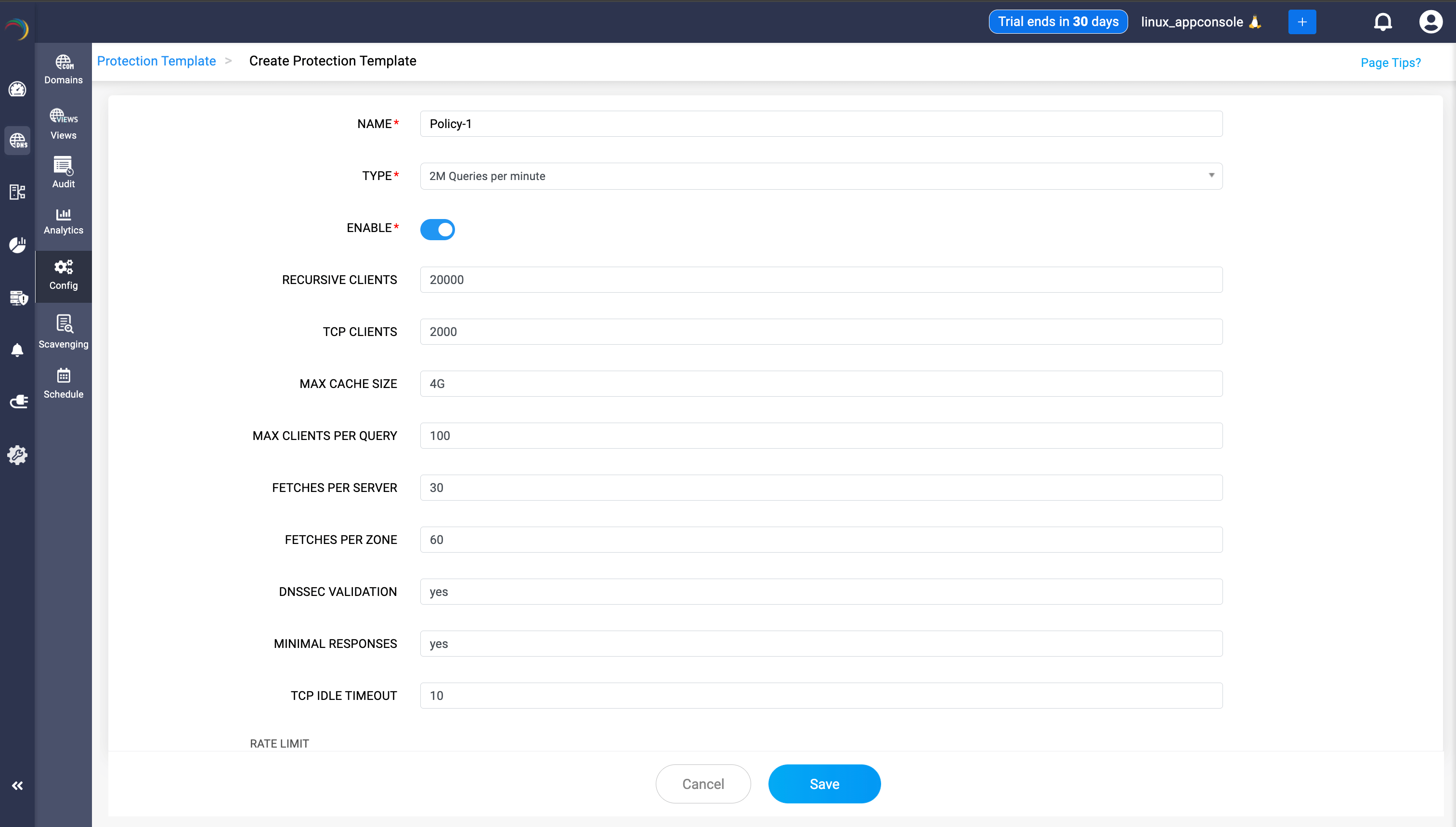
With templates, admins can codify rate-limiting into reusable, ready-to-deploy policies. Choose from industry-grade presets like “50K to 5M queries per minute,” or fine-tune custom thresholds to match evolving threats. Once defined, templates can be rolled out instantly across servers or domains, eliminating manual guesswork and ensuring consistent protection.
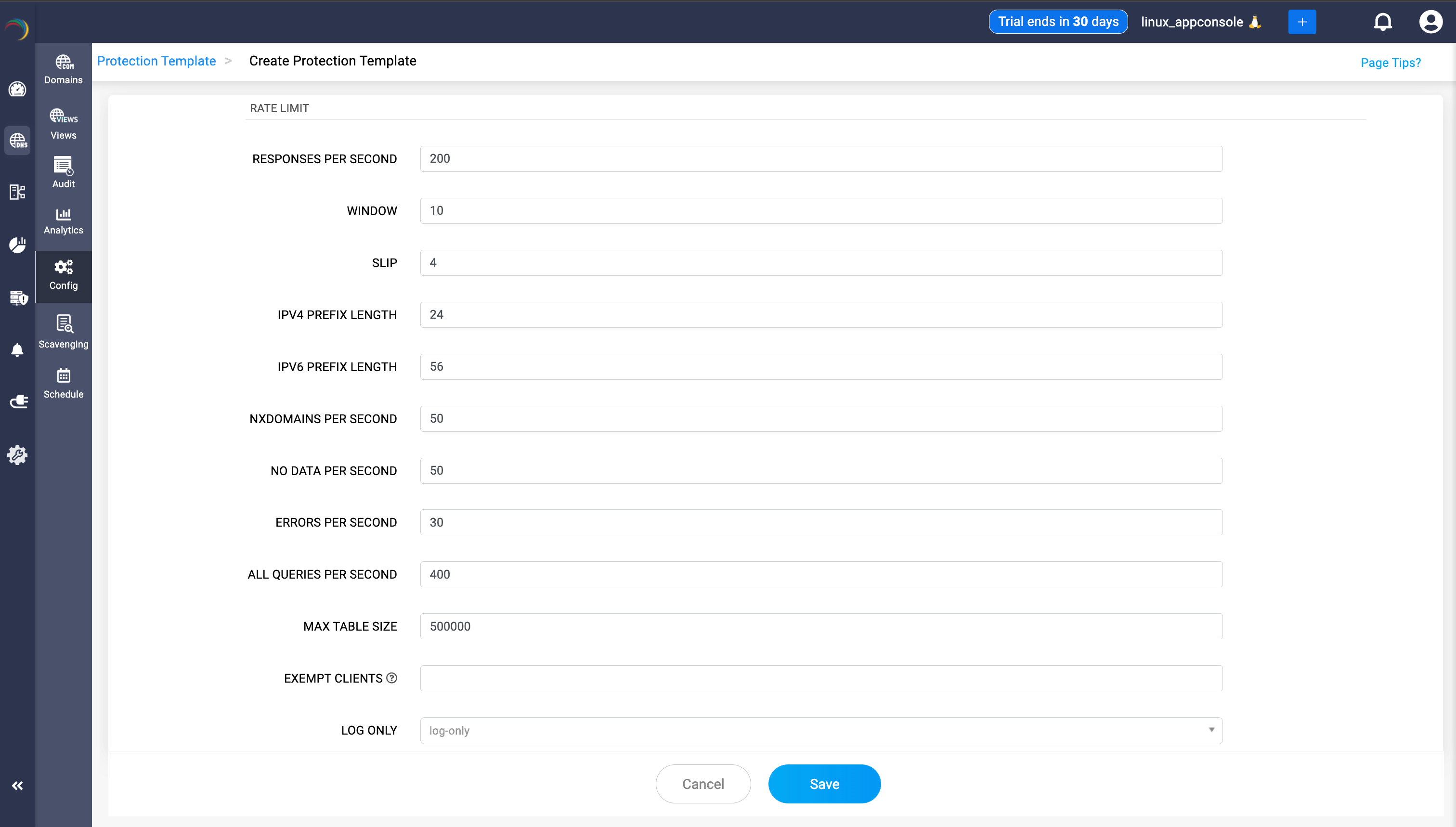
Unlike blunt blocking, these controls are context-aware. Templates let admins limit traffic by client, zone, or subnet—throttling abusive patterns without punishing legitimate queries. Nuanced controls like error thresholds, slip ratios, and NXDOMAIN caps keep performance steady, even during storm conditions.
Security doesn’t take a backseat either. DNSSEC-safe enforcement ensures that rate-limiting never interferes with query validation, preserving integrity and compliance while under load. And for admins who prefer to test before enforcing, templates support a log-only mode, letting teams tune behavior in the background before going live.
With protection templates, DNS defenses evolve from reactive firefighting into proactive, reusable safeguards. Whether you’re bracing for a flood, sandboxing a new policy, or fine-tuning thresholds, your DNS layer remains fast, resilient, and always prepared.
Feature 6: Management UI console failover — Hot-standby engine
Think of the management console as the command center of your network. It’s where admins log in every day to see what’s happening, push out changes, and keep operations steady. Now imagine that command center suddenly going dark. No dashboards, no updates, no visibility. That's not only stressful—it’s risky.
That’s why we built console failover with a hot-standby engine. If the primary console trips, the standby doesn’t ask questions—it simply takes over. No scrambling, no downtime. You keep working in the same familiar console, and the switchover happens automatically.
We’ve also made it crystal clear which console is at the controls. The UI shows whether you’re connected to the primary or the standby, along with IP, sync time, and HA status. There’s no second-guessing, and no hidden surprises.
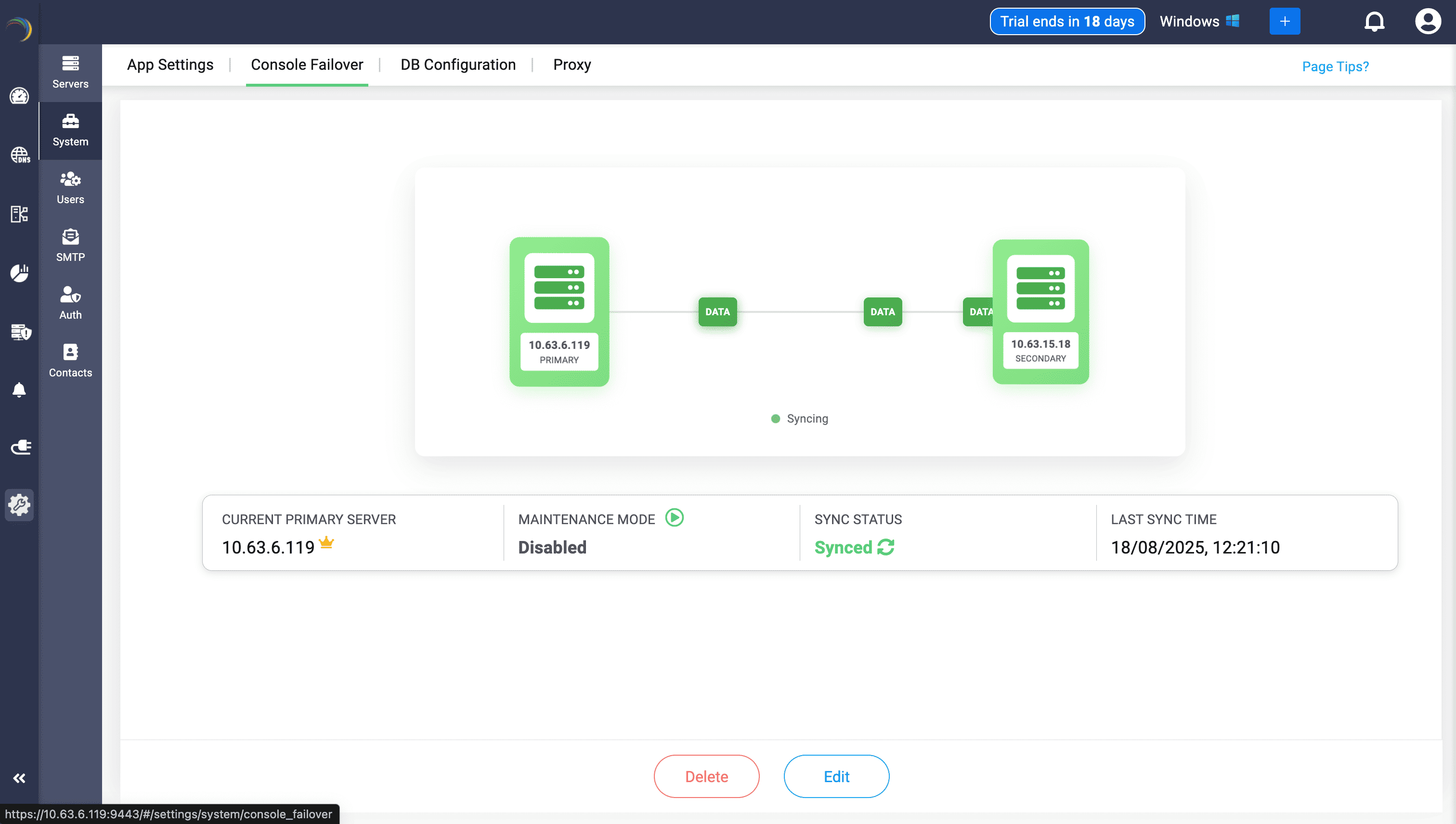
Admins will still stay in the driver’s seat. Want to test a cutover or perform an upgrade? Promote the standby manually. Need peace of mind during maintenance? Pause failovers until your updates are done. All the while, configurations and logs are mirrored in real time, so the standby is always ready to pick up where the primary left off.
Get confidence that your console is configured with a failover that won’t flinch, your operations won’t skip a beat, and your team can always keep their hands on the controls—even if one server falters.
Feature 7: Remote database configuration
As networks scale, databases need room to breathe. With version 5.5, DDI Central now supports remote database hosting, letting you offload the backend to a dedicated node, VM, or cloud instance.
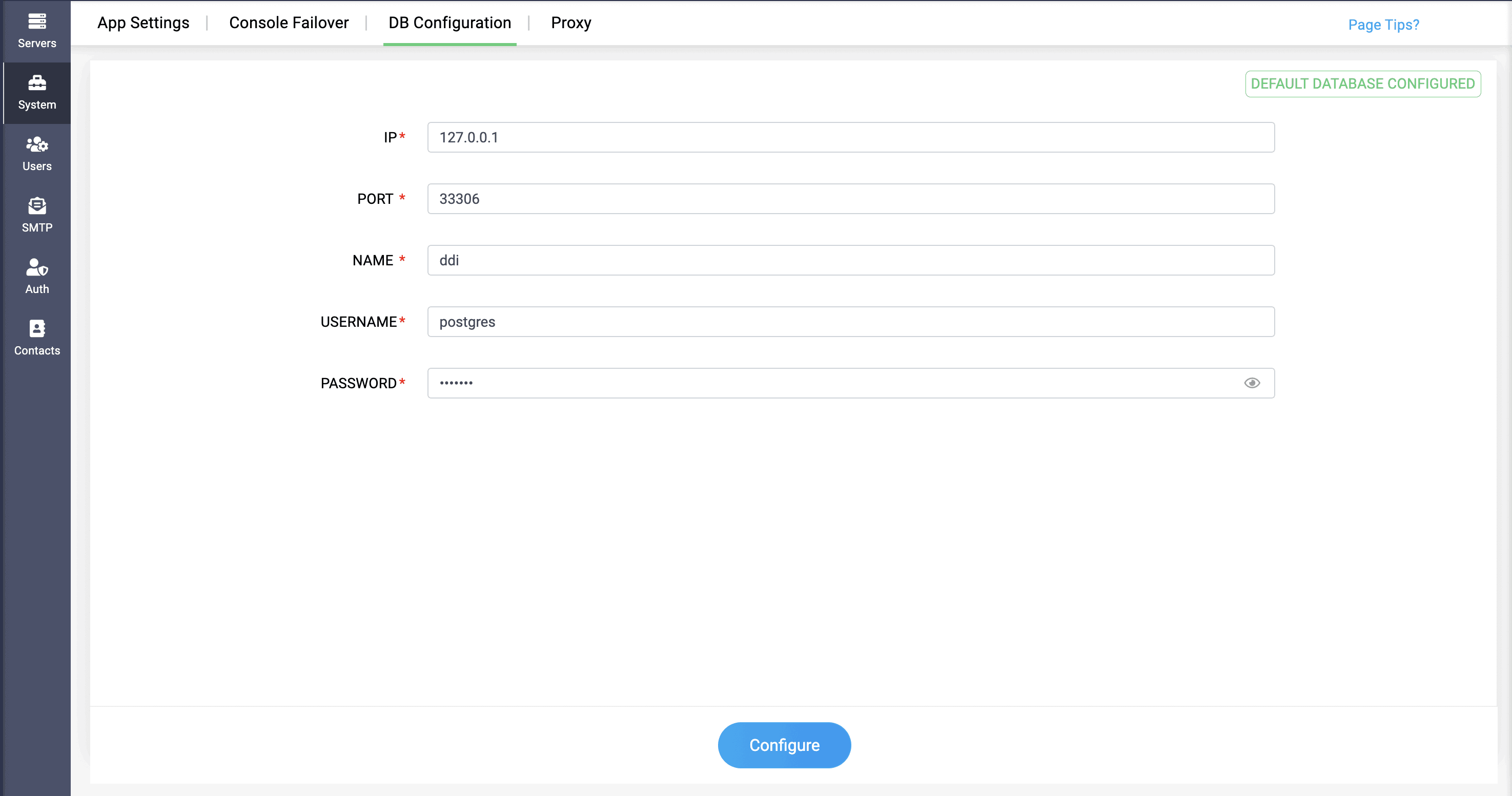
This separation boosts performance, reduces contention, and aligns with enterprise infrastructure strategies. Add role-based privileges for tighter access control and smooth migration routines, and your DDI Central database layer is now as flexible as the environments it serves.
Final thoughts
With DDI Central 5.5, we’ve pushed the boundaries of what a DDI platform can deliver—establishing a security-first foundation for modern network infrastructure. Every feature in version 5.5 reflects a deliberate focus on resilience, automation, and scale. Admins gain stronger visibility into malicious activity, faster containment at the device level, and a hardened management plane that can withstand failure without compromising control.
Whether you’re securing thousands of IPs or managing services across distributed sites, DDI Central 5.5 ensures that your DNS, DHCP, and IPAM foundation is both defensible and future-ready.
Next steps
New to DDI Central? Start your 30-day, free trial today and experience how unified DNS, DHCP, and IPAM with built-in security can harden your infrastructure.
Already a customer? Upgrade now to version 5.5to unlock these capabilities and extend your operational resilience.