CVE-2025-59287 (RCE) turns WSUS into an attack vector: Track suspicious process behavior using ADAudit Plus
CVE-2025-59287 in a nutshell
|
Let’s take a closer look at how this WSUS flaw works, how to check for WSUS compromise in a few clicks without native tools, and how to detect CVE-2025-59287 (RCE) in real time with ManageEngine ADAudit Plus.
What's the fuss about?
On October 23rd, 2025, Microsoft rolled out an unexpected out-of-band update to fix a critical WSUS flaw, tracked as CVE-2025-59287. This remote code execution (RCE) bug, already being exploited in active attacks, allowed threat actors to take full control of unpatched WSUS servers.
What is WSUS?
Windows Server Update Services (WSUS) is a Microsoft tool that helps organizations centrally download, manage, and deploy updates to Windows devices within their network.
| Did you know? 100,000 client systems can be managed by a single WSUS server, making it a high-value target in enterprise security environments. (Source) |
Since WSUS operates with high-level permissions and controls software updates for many systems, a compromised WSUS server can give attackers a powerful entry point to move across the network or gain higher privileges.
How serious is CVE-2025-59287?
CVE-2025-59287 is a critical flaw in Windows Server Update Services (WSUS) that enables attackers to remotely run commands on the server without having to log in.
The issue stems from how WSUS processes certain update requests so that an attacker can exploit this weakness by tricking the server into executing their own code with full system privileges. Once that happens, the attacker can execute arbitrary code as SYSTEM, giving them full control of the WSUS server and enabling data theft, persistence, and lateral movement across the network.
Timeline of the CVE-2025-59287 exploitation
October 14, 2025: Microsoft initially disclosed CVE-2025-59287 and released a patch as part of October Patch Tuesday; however, this patch was incomplete.
↓October 23, 2025: Microsoft issued an out-of-band patch for CVE-2025-59287, a WSUS remote code execution flaw, requiring a reboot after installation.
↓October 23, 2025: Huntress, a global cybersecurity company, observed early exploitation targeting WSUS servers exposed on ports 8530 and 8531.
↓October 24, 2025: The Dutch National Cyber Security Centre confirmed active exploitation; Eye Security reported a .NET payload executing system commands.
↓October 24, 2025: Public proof-of-concept code and analyses were released, fueling rapid weaponization.
↓October 27, 2025: Security firms noted widespread attacks; CISA added the flaw to its KEV catalog with a November 14 remediation deadline.
Detecting WSUS compromise using native methods
Look for these key indicators of compromise in the SoftwareDistribution.log file on your WSUS server:
This error often appears in the log right after the server has been attacked.
SoapUtilities.CreateException ThrowException: actor = https://<host>:8531/ClientWebService/client.asmx A unique text pattern seen in the malicious request that triggered the attack.
AAEAAAD/////AQAAAAAAAAAEAQAAAH9 The attacker’s IP address. Check if your WSUS server received any traffic from this address.
207.180.254[.]242 The file hash of the malicious program used in the attack. If this hash shows up on your server, it likely means the system was compromised.
ac7351b617f85863905ba8a30e46a112a9083f4d388fd708ccfe6ed33b5cf91d - Review process logs for suspicious activity like w3wp.exe or wsusservice.exe launching cmd.exe or powershell.exe, as this might indicate that the exploit was successful
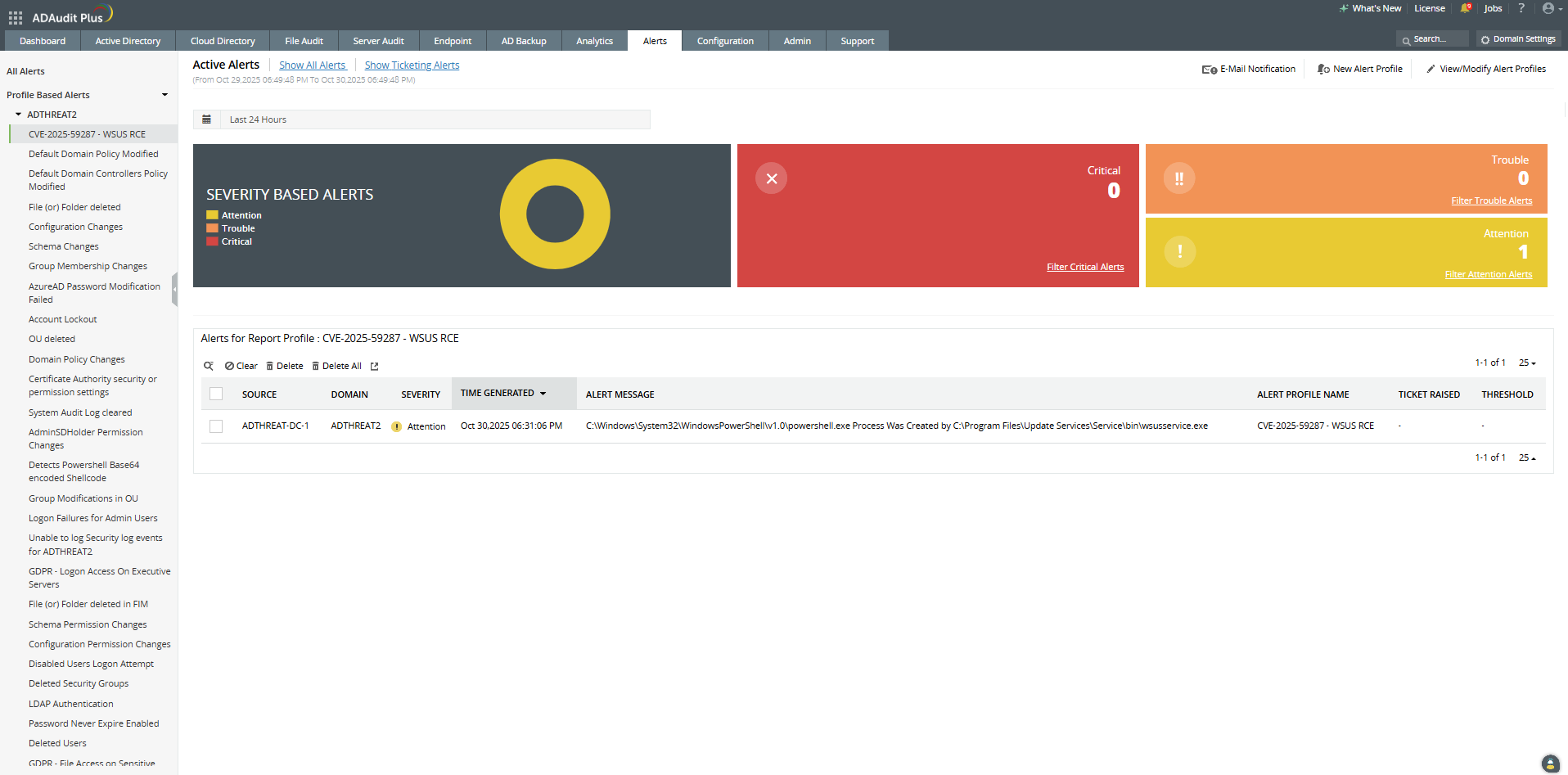
Identify WSUS compromise in just a few clicks with ADAudit Plus
Quickly verify if your WSUS server has been compromised, no native tools or manual log searches needed.
- Open the ADAudit Plus console.
- Go to the Server Audit tab.
- Under Process Tracking, select the New Process Created report.
- Click Advanced Search and set the following filters:
- Creator Process Name → Ends With → wsusservice.exe, OR
- Creator Process Name → Ends With → w3wp.exe
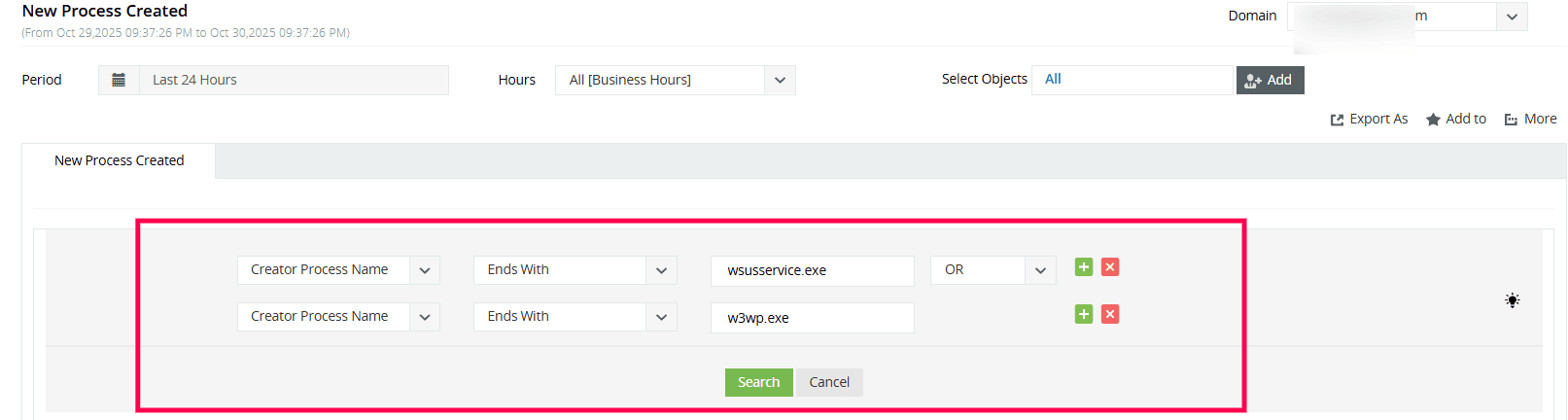
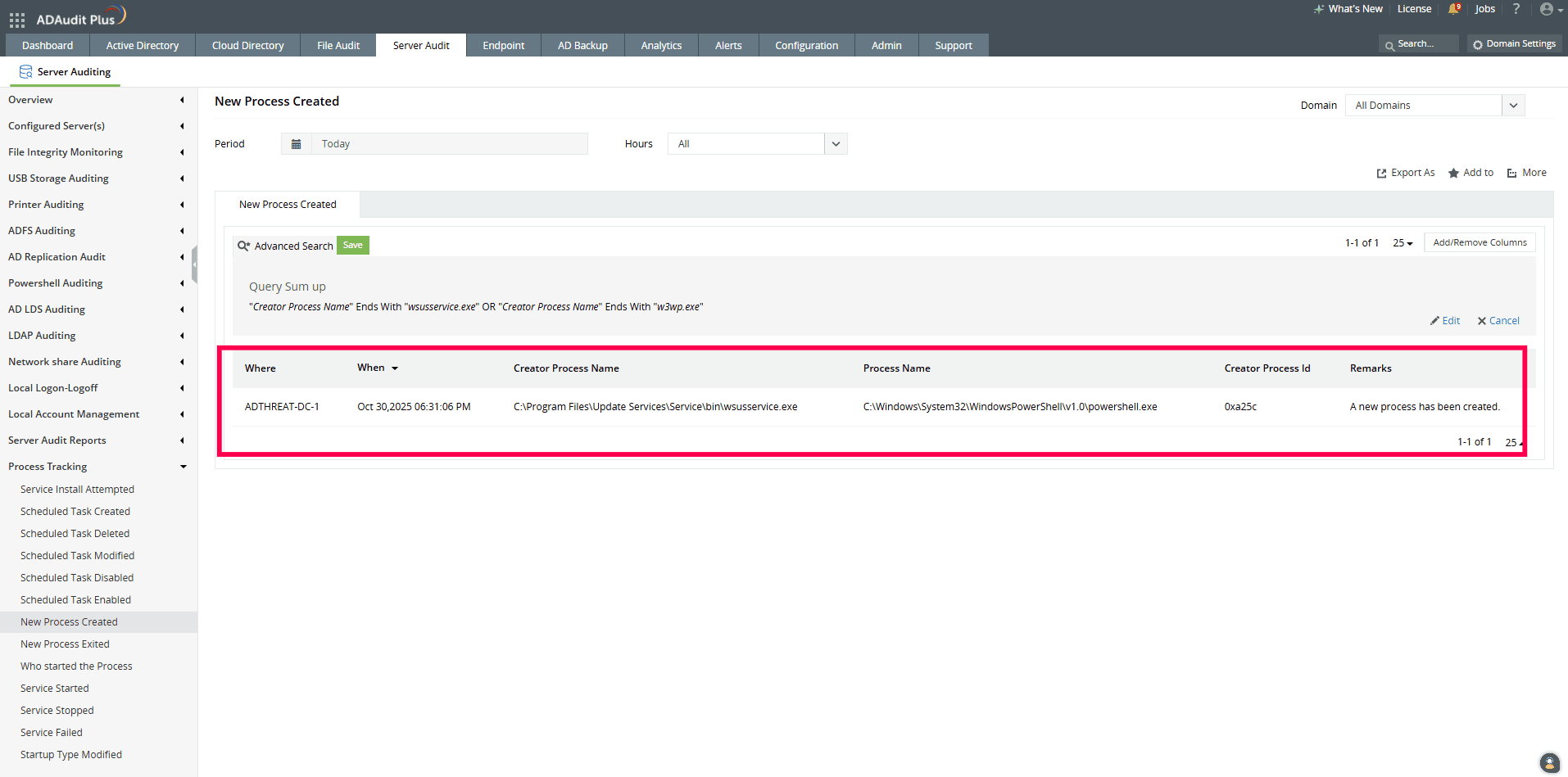
Click Search.
If you see suspicious child processes (like powershell.exe or cmd.exe) spawned by either wsusservice.exe or w3wp.exe, it’s a strong indicator of potential exploitation of CVE-2025-59287.
Defend your WSUS environment from CVE-2025-59287
To stay protected from CVE-2025-59287 and other similar vulnerabilities, take the following steps:
Install Microsoft’s security update immediately.
Microsoft has released a dedicated out-of-band patch that closes the vulnerability. Apply the update on all servers running the WSUS role and reboot to complete the installation. For more details, click here.
Limit access to your WSUS server.
Only allow trusted management hosts or internal update clients to connect. If possible, place the WSUS server behind a firewall or restrict inbound connections using network segmentation.
Close or monitor WSUS ports (8530 and 8531).
If WSUS must remain reachable, restrict or closely monitor traffic on these ports for signs of scanning or exploitation attempts.
Review WSUS permissions.
Ensure that only administrators have access to WSUS management consoles and update approval settings to prevent misuse.
Use indicators of compromise to strengthen your SIEM and EDR detections.
Integrate these IoCs into SIEM and EDR platforms for continuous monitoring and alerting.
CVE-2025-59287 under watch: Set up a custom alert to catch WSUS exploitation attempts with ADAudit Plus
We’ll show you how to create a custom alert in ADAudit Plus to monitor unusual process creation activity on WSUS servers.
Go to the Configuration tab and click New Alert Profile to start.
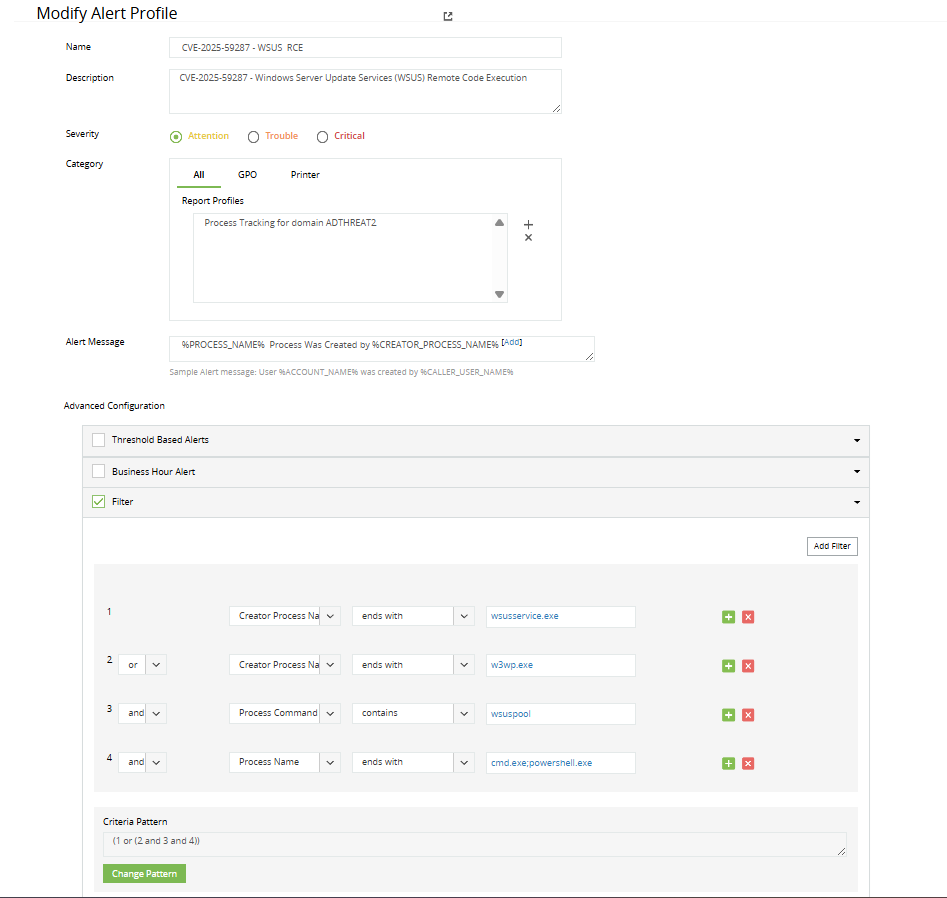
Name the alert appropriately and add a description if needed.
Set the desired severity level based on your organization’s risk standards.
Under Category, select All, then choose the report profile titled Sysmon Auditing.
In Advanced Configurations, enable the Filter checkbox and click Add Filter.
Set the filter conditions as follows:
Parent image → ends with → wsusservice.exe, or
Parent image → ends with → w3wp.exe, and
ParentCommandLine → contains → wsuspool, and
Process Name → ends with → cmd.exe;powershell.exe
Click Change Pattern and set the criteria pattern to: (1 or (2 and 3 and 4)).
Once the alert is configured, any process matching the defined filter conditions will trigger an alert, which can be viewed under the Alerts tab.
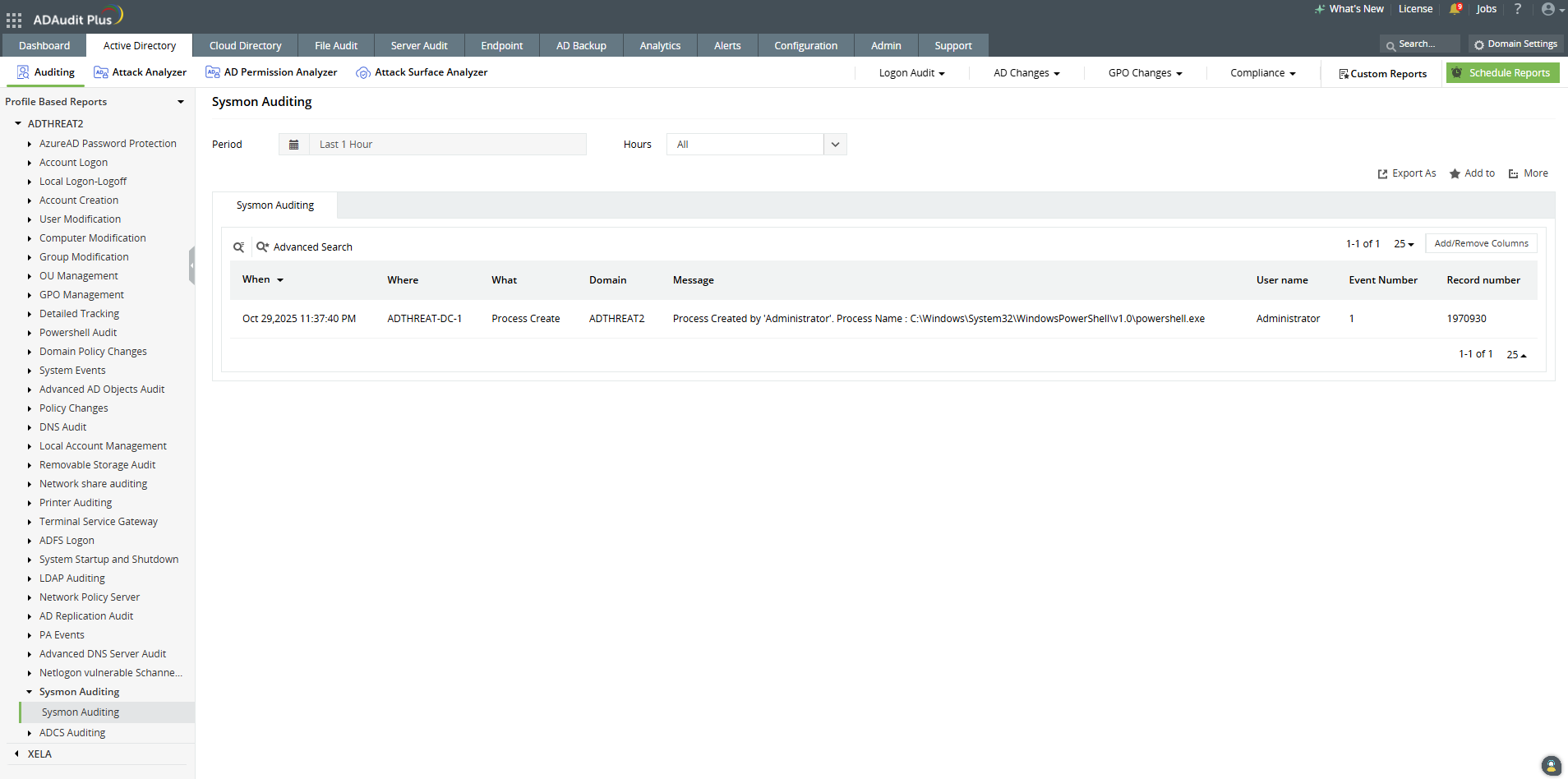
For detailed insights, including who made the change, when it occurred, and from where, go to the Active Directory tab > Sysmon Auditing.
This helps verify whether the activity originated from a legitimate source and aligns with your organization’s security policies.
About ManageEngine ADAudit Plus
ADAudit Plus is a UBA-driven change auditing solution that helps ensure accountability, security, and compliance across your AD, file servers, Windows servers, and workstations.