Wi-Fi security auditing: Vital checks for organizational security
Cyberattacks are now more sophisticated than ever. Attackers no longer even need extensive resources and infrastructure to cause major damage. A single bad Wi-Fi connection is all it takes to overthrow all the security measures your organization has in place.
In this blog, we'll look at how you can track and monitor your Wi-Fi connections to stay off an attacker's radar.
Why should you monitor Wi-Fi activities?
We all connect to Wi-Fi, be it in offices, homes, cafes, or on the go. While we connect to Wi-Fi, what information do we knowingly or unknowingly divulge?
Let's break the typical Wi-Fi networks down into two categories: organization networks and public and private unsecured networks.
Organization networks
You can connect a domain device to the organization's Wi-Fi by authenticating with the required credentials. If your organization allows the connecting of personal devices to the corporate Wi-Fi, you can do so as well using the same network credentials. Corporate networks are secure and encrypted. All transmitted data will remain safe.
Your organization might record the hostname, the IP address, and the time of network connection.
Public and private unsecured networks
More often than you think, you may connect to public and private Wi-Fi using your domain devices that store organizational data. The Wi-Fi may not be encrypted or secure, leaving the data at risk. You might unknowingly reveal sensitive information, such as your IP address, hostname, transactions, and other critical information, that could compromise the safety of the device.
Unsecure networks are notorious for hosting defense-evading malware and ransomware which can install and run on connected devices and subsequently infect your corporate network. These payloads can also steal and wipe data from the infected device.What can you do about unsecured Wi-Fi?
While it's almost impractical to restrict employees from connecting to private and public Wi-Fi outside of your organization, you must be able to track the Wi-Fi networks your devices connect to and record details such as the name of the Wi-Fi connection, connection status, and the device that initiated the connection.
Tracking Wi-Fi activities: Event IDs and their significance
Event ID | Description | Log information |
5632 | A request was made to authenticate to a wireless network | Event ID 5632 logs the following information:
|
8001 | Successful connection established to a Wi-Fi connection | Event ID 8001 logs the following information:
|
8003 | Successfully disconnected from a Wi-Fi network | Event ID 8003 logs the following information:
|
What if a device automatically disconnects from and reconnects to a Wi-Fi connection?
When a device connected to a Wi-Fi hibernates or switches off due to low power and wakes up within the same range of the Wi-Fi network, it will automatically connect to the Wi-Fi. However, event IDs 8001 and 8003 will not be recorded for such activities.
You can track the following event IDs to track such Wi-Fi events constantly:
Event ID | Description | Log information |
11004 | Wireless security stopped: WLAN AutoConfig service was disconnected automatically from a wireless network | Event ID 11004 logs the following information:
|
11005 | Wireless security succeeded: WLAN AutoConfig service started automatically for a wireless network | Event ID 11005 logs the following information:
|
Tracking the above events will ensure that you have complete visibility into who is connecting to which Wi-Fi and what activities they're carrying out.
You can also gain in-depth Wi-Fi analytics from a security solution that covers all the bases. Log360, a SIEM solution from ManageEngine, can help track all Wi-Fi activities closely.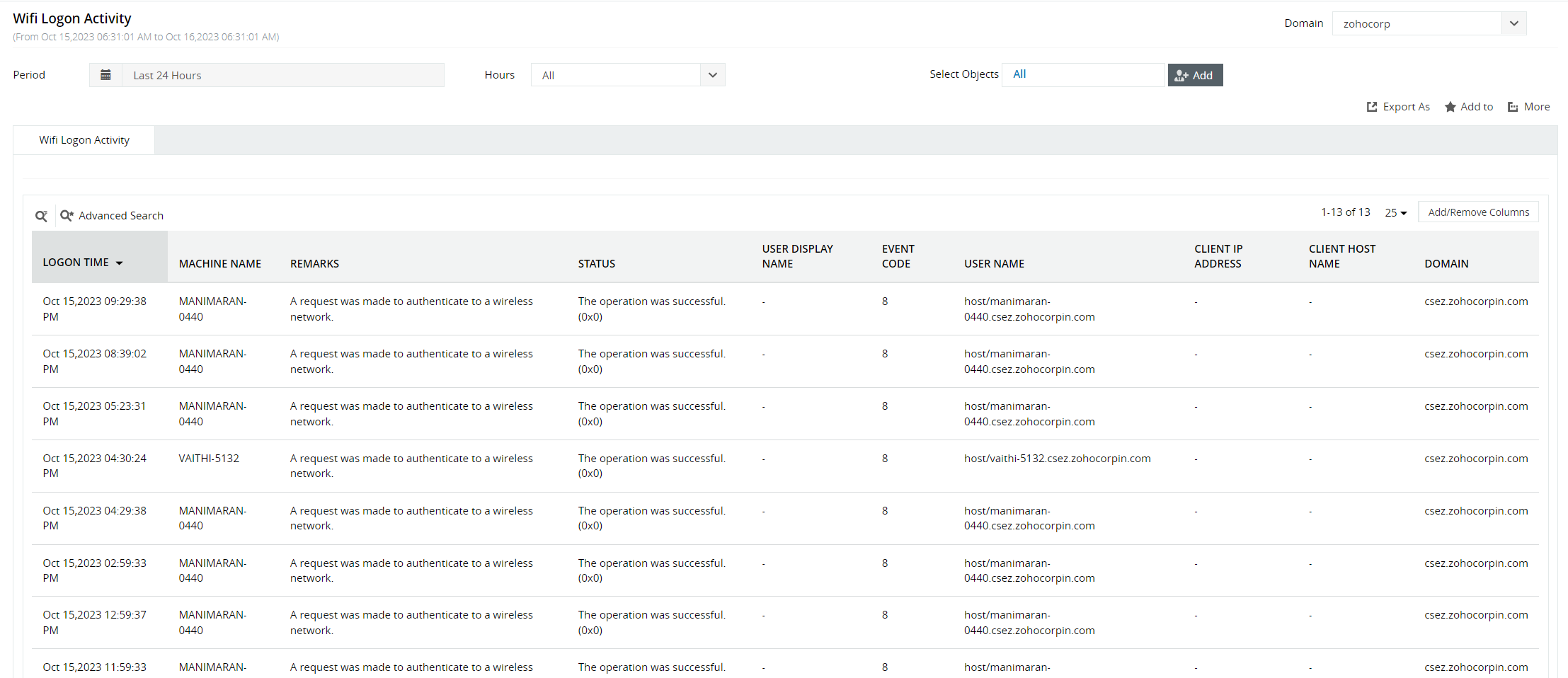
The solution will also send real-time notifications for sensitive devices connecting to and disconnecting from unsecured networks. You can view these Wi-Fi security analytics in your environment using the 30-day, free trial of Log360 today.
