Follina—while we’re sure this commune in Italy is lovely, the same can’t be said about this new vulnerability by the same name for InfoSec folks. Thanks to a zero-day bug in the Microsoft Support Diagnostic Tool, Follina is now making the headlines but for all the wrong reasons.
This blog talks in detail about the zero-day vulnerability in Microsoft Support Diagnostic Tool (MSDT), popularly known as Follina.
If you’re wondering why Follina of all names, researcher Kevin Beaumont says, “I’m calling it Follina because the spotted sample on the file references 0438, which is the area code of Follina in Italy.”
About the zero-day vulnerability
Tracked as CVE-2022-30190, this zero-day bug in MSDT can enable remote code execution when MSDT is called using the URL protocol from a calling application such as Microsoft Word.
The vulnerability affects all Windows versions that still receive security updates, i.e. Windows 7+ and Windows Server 2008+.
It has been reported that the threat actors can execute arbitrary code in the affected systems using a specially crafted Microsoft Word document. As soon as the user opens the malicious file, the infected document paves the way for attackers to execute PowerShell commands using MSDT.
Once successfully executed, attackers can then perform a wide array of activities such as installing applications, viewing/modifying/deleting data, or creating new accounts in user-specific scenarios.
The bug was disclosed by nao_sec, a Tokyo-based cybersecurity research group on Twitter.
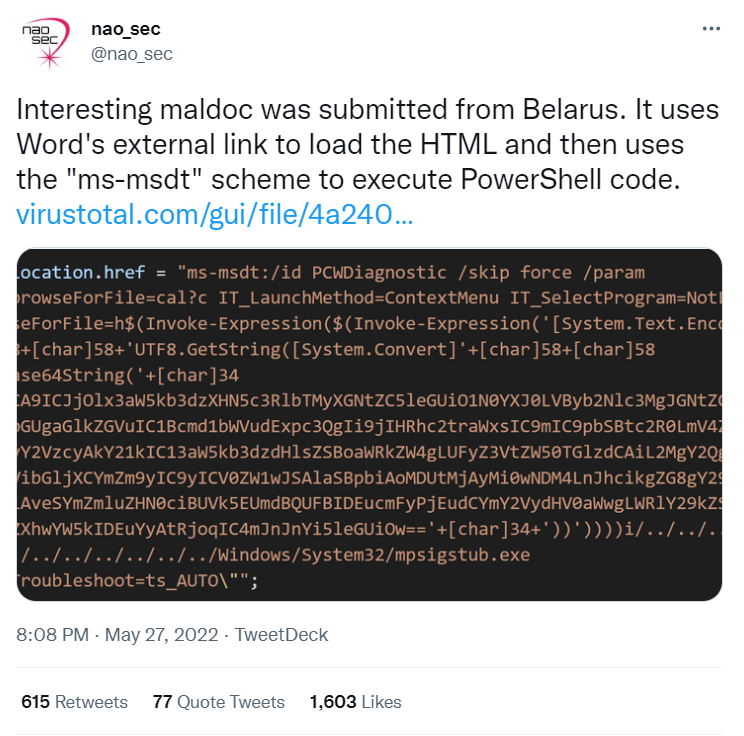
Kevin examined nao_sec’s research and stated in his blog:
“There’s a lot going on here, but the first problem is Microsoft Word is executing the code via msdt (a support tool) even if macros are disabled. Protected View does kick in, although if you change the document to RTF form, it runs without even opening the document (via the preview tab in Explorer) let alone Protected View.”
Microsoft has acknowledged this vulnerability in its Microsoft Security Response Center (MSRC) blog. As per its official statement:
“A remote code execution vulnerability exists when MSDT is called using the URL protocol from a calling application such as Word. An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application. The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights.”
The impact
Some major impacts have been observed:
-
By leveraging the vulnerability, attackers can execute arbitrary code in the affected systems using a specially crafted Microsoft Word document and can elevate privileges, potentially gaining GodMode access.
-
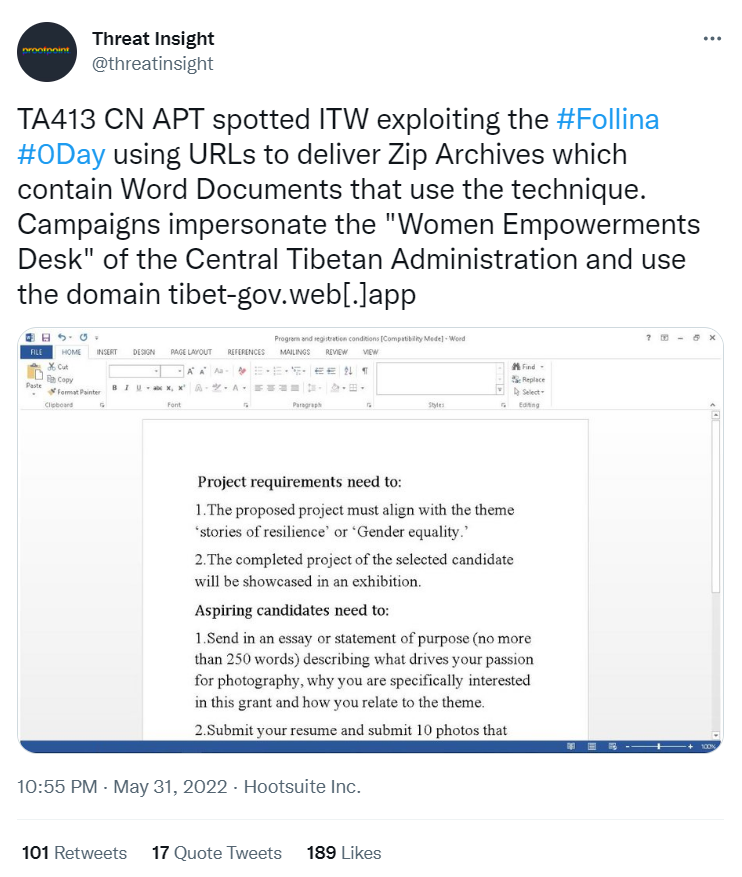
TA413 CN APT (an advanced persistent threat actor linked with China) has been spotted in the wild exploiting the zero-day vulnerability.
ManageEngine to the rescue: Detection and mitigation
As of now, Microsoft has not released any official patch to mitigate the vulnerability, instead offering manual workarounds.
However, if you’re using ManageEngine Endpoint Central with either the Vulnerability Manager Plus add-on or the Endpoint Security add-on, or if you’re using ManageEngine Vulnerability Manager Plus, we have good news! You can seamlessly execute Microsoft’s suggested workarounds using our pre-built scripts right from the product console.
To detect and mitigate the vulnerabilities using:
-
Endpoint Central with the Vulnerability Manager Plus add-on or the Endpoint Security add-on, find the mitigation steps here.
-
Vulnerability Manager Plus, these mitigation steps can help.
Suggested workarounds from Microsoft
While Microsoft is yet to release a patch to mitigate the vulnerabilities, it has suggested manual workarounds to prevent exploitation. As per the MSRC blog, users should:
-
Disable the MSDT URL protocol
or
-
Turn on cloud-delivered protection and automatic sample submission in Windows Defender
Read more on the suggested workarounds from Microsoft.
The situation now
As of now, Microsoft has released no official patches. There is a high probability that the vulnerability is being exploited in the wild. You can seamlessly execute Microsoft’s suggested workarounds using ManageEngine Endpoint Central with the Vulnerability Manager Plus add-on or the Endpoint Security add-on (by following these steps). You can also do this if you’re using Vulnerability Manager Plus (find steps to implement these here).
ManageEngine is keeping an eye on the latest news related to CVE-2022-30190. We’ll support the patches for deployment via our patch management solutions (viz. Endpoint Central, Patch Manager Plus, and Vulnerability Manager Plus) once the vendor releases them.
This blog post will be updated periodically to include important details as and when we get them.