
In March this year, organizations employing Microsoft Exchange were in for a shock when Microsoft announced that a hacker group was gaining access to organizations’ email accounts through vulnerabilities in its Exchange Server email software. The group tried to gain information from defense contractors, schools, and other establishments in the U.S.
Organizations across the globe employ Exchange as their email solution, and Outlook on the web—or Outlook Web Access (OWA)—allows enterprise users to access their organizational email, calendars, tasks and contacts from Exchange Server right from their web browsers. With OWA providing straightforward access to such sensitive, and sometimes confidential, information like details on an upcoming project or correspondence consisting of client information, it’s imperative that access through OWA is secured.
OWA logins are authenticated by entering a username and password, which doesn’t effectively deter the advanced credential-based attacks making the rounds these days. In fact, Microsoft’s corporate vice president attributed exposed credentials as a cause for the Exchange cyberattack, stating that the hacker group would:
“…gain access to an Exchange Server either with stolen passwords or by using the previously undiscovered vulnerabilities to disguise itself as someone who should have access.”
How can organizations secure OWA and prevent unauthorized login attempts?
ManageEngine ADSelfService Plus now supports multi-factor authentication for OWA. Using ADSelfService Plus, organizations can implement additional authentication factors apart from the existing credential-based authentication method and fortify logins to both OWA and the Exchange admin center (EAC).
ADSelfService Plus supports more than 15 authentication methods including biometrics, Microsoft Authenticator, Zoho OneAuth one-time passcode, and QR-code-based authentication. Up to three authentication factors can be implemented during an OWA login creating a solid guard against hacks.
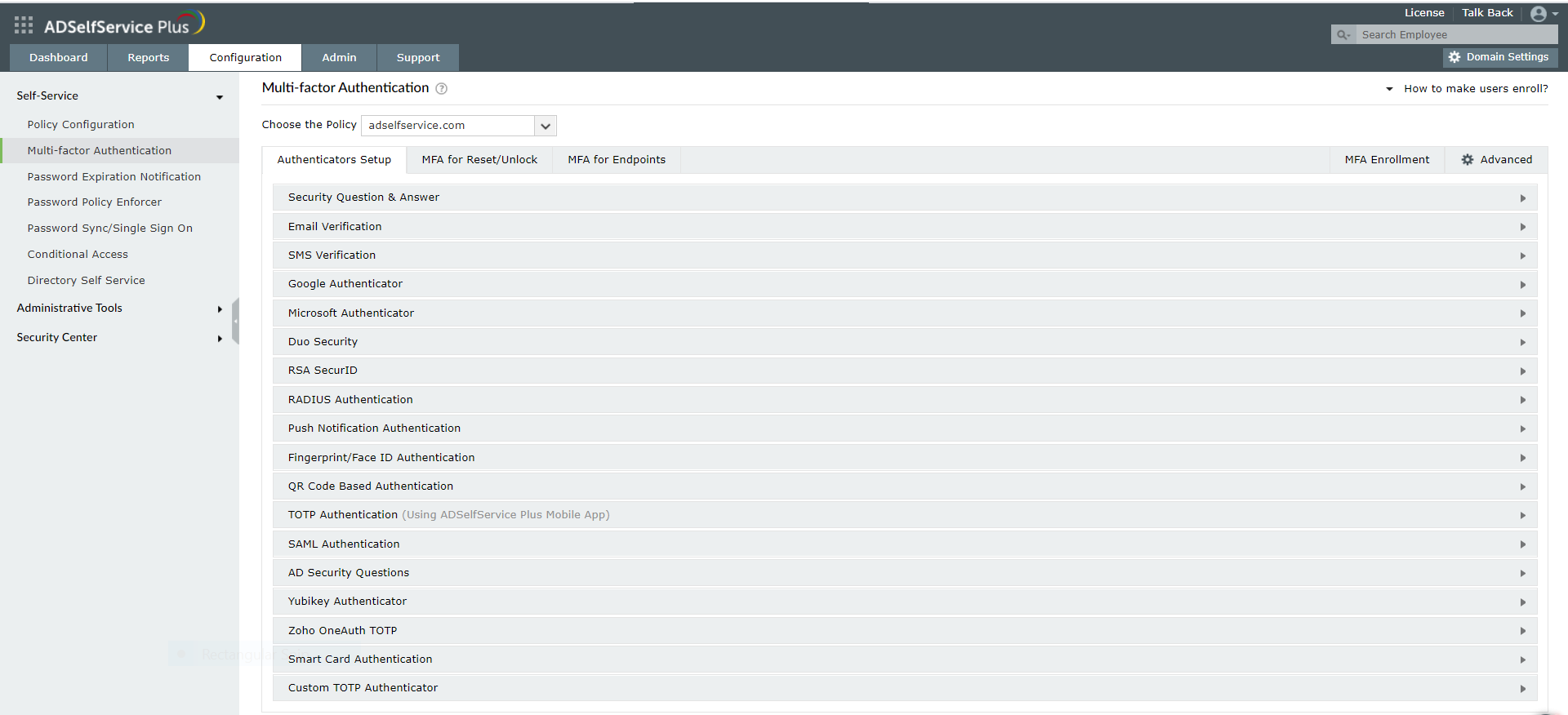
How does MFA for OWA and EAC logins work?
Once MFA is configured for OWA logins, here’s how the login process goes:
-
User opens the OWA or EAC login page and enters their Active Directory domain username and password.
-
Once the credentials are authenticated, the MFA methods configured in ADSelfService Plus are loaded.
-
The user has to successfully prove their identity using these methods and, if successful, they are allowed access to OWA and EAC.
Why ADSelfService Plus is a step above other MFA providers
-
Flexible configuration: Enable specific authentication methods for users belonging to specific domains, groups, and organizational units.
-
Risk-based access control: Automate access control decisions based on factors like IP address, time of access, geolocation, and device used.
-
Secure multiple gateways: Use MFA to secure not just OWA access, but also local and remote logins into Windows, macOS, and Linux machines, and VPN logins for all-around endpoint security.
Download a free, 30-day trial of ADSelfService Plus to try MFA for OWA along with a wide range of other features ADSelfService Plus has to offer.