IAM is IT-centric. Identity and access management (IAM) may appear easy to some, but in reality, it is very tricky. Proper IAM is the key to...
Single sign-on (SSO) for the cloud
Nearly every organization has some cloud-based application. Of course the common cloud apps include Microsoft Azure, Office 365, G Suite, those from Zoho and Salesforce,...
5 things to keep in mind before backing up your VMware virtual machines
The architecture of a virtual machine differs vastly from traditional on-premises environments, and requires different data backup techniques and pre-backup operations. This post will explain some of the...
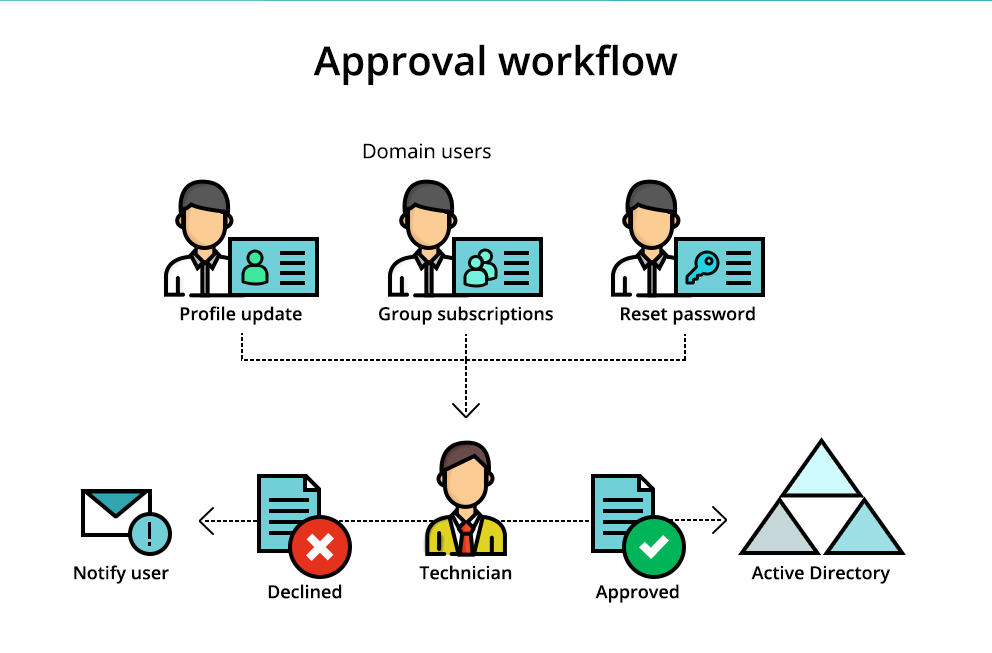
Approval workflow: Supervise self-service in Active Directory
Are you comfortable giving end users the power to update their own information in Active Directory? Definitely not! Are you willing to take on the responsibility of updating user information and managing users’ passwords? Not only is this a daunting task,...
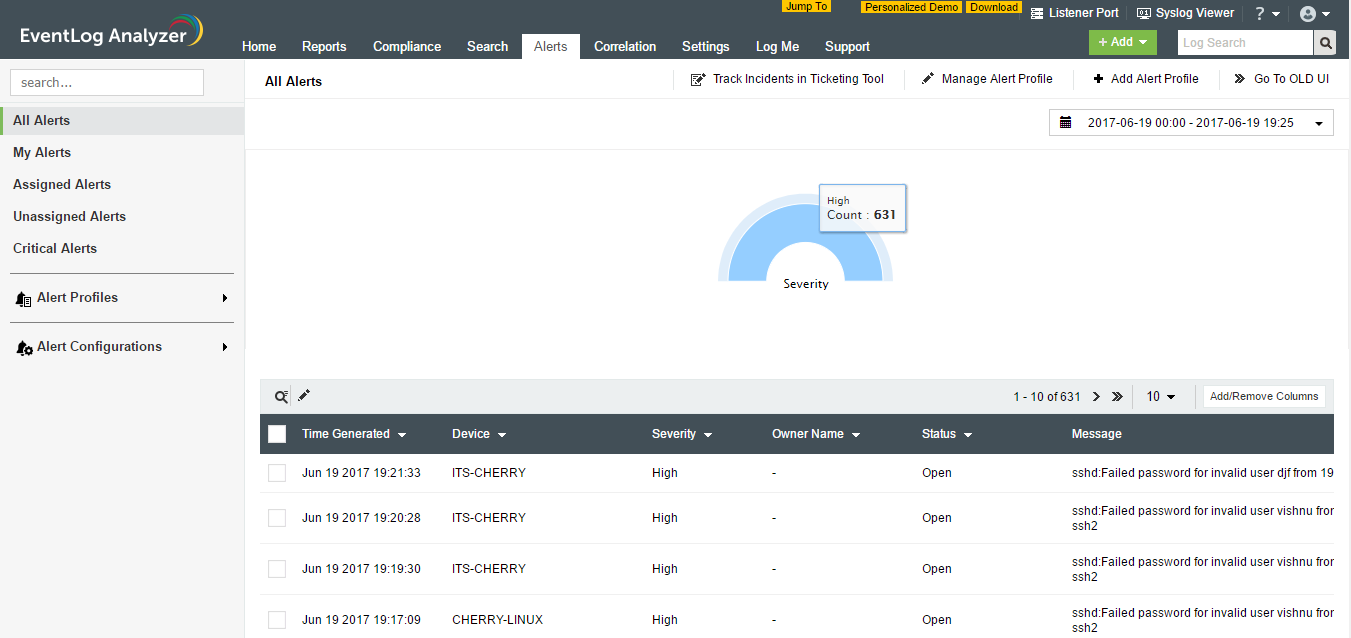
The case for incident management in a SIEM system
Log360‘s latest incident management system is the perfect bridge between your incident detection and response processes. The feature comes in handy for security administrators and the various agents who...
[Free Webinars] Active Directory security and control
There are many moving parts of Active Directory, many of which are difficult, if not impossible, to manage and monitor. In our upcoming series of...
[Free Webinar] Awesome Active Directory password controls
Active Directory passwords are easy to crack. Since the password controls have not changed in over 15 years, attackers have been given ample opportunity to...