IT security under attack: A typical day in the life of an IT admin or security analyst
The job of IT admins and IT security analysts are, without a doubt, some of the most important jobs in any company. When things are running smoothly, it is easy for everyone to forget they exist. However, the moment things go askew, everyone points fingers at them.
IT security professionals are expected to know everything. Most of them are self-taught and have learned on-the-job. Over time, experience has turned them into battle-hardened soldiers. The pressure is real, as they are responsible for the configuration, administration and, most importantly, the security of the entire infrastructure.

 When we asked what was checked first thing Monday morning, one IT admin offered, a bit sarcastically: "I discover any changes made on the domain while I was away over the weekend! I typically look for unusual logons on servers now that we're working remotely, and modifications done by our help desks or authorized department managers."
For example, the security changes that IT admins are looking for could be anything, such as:
When we asked what was checked first thing Monday morning, one IT admin offered, a bit sarcastically: "I discover any changes made on the domain while I was away over the weekend! I typically look for unusual logons on servers now that we're working remotely, and modifications done by our help desks or authorized department managers."
For example, the security changes that IT admins are looking for could be anything, such as:- A simple logon on a server, even a domain controller, or on a cloud directory (like Azure)
- A permission granted on a file and folder
- Attribute changes, such as memberships of security groups, or a manager changed for a security object, like users, groups or computers
 To discover all the security events that could have occurred from Friday evening and up until Monday morning, IT admins have to depend primarily on Windows event logs. Unfortunately, this log data is dumped into one location, and the sheer number of events makes it complicated to gain a bird's-eye view of all changes that occurred in the domain.Before lunch:
To discover all the security events that could have occurred from Friday evening and up until Monday morning, IT admins have to depend primarily on Windows event logs. Unfortunately, this log data is dumped into one location, and the sheer number of events makes it complicated to gain a bird's-eye view of all changes that occurred in the domain.Before lunch: Discovering security changes on the domain is time-consuming and, on a good day, the entire process might take up to three hours. It's even more time-consuming now as organizations are starting to adopt public cloud services (like Azure AD) alongside traditional on-premises infrastructures.
To maximize available time and resources, IT admins should prioritize and manage the next most crucial tasks of the day by tending to requests and tickets.
Here are examples of some requests that IT admins typically receive, and their internal thought process:
Discovering security changes on the domain is time-consuming and, on a good day, the entire process might take up to three hours. It's even more time-consuming now as organizations are starting to adopt public cloud services (like Azure AD) alongside traditional on-premises infrastructures.
To maximize available time and resources, IT admins should prioritize and manage the next most crucial tasks of the day by tending to requests and tickets.
Here are examples of some requests that IT admins typically receive, and their internal thought process:
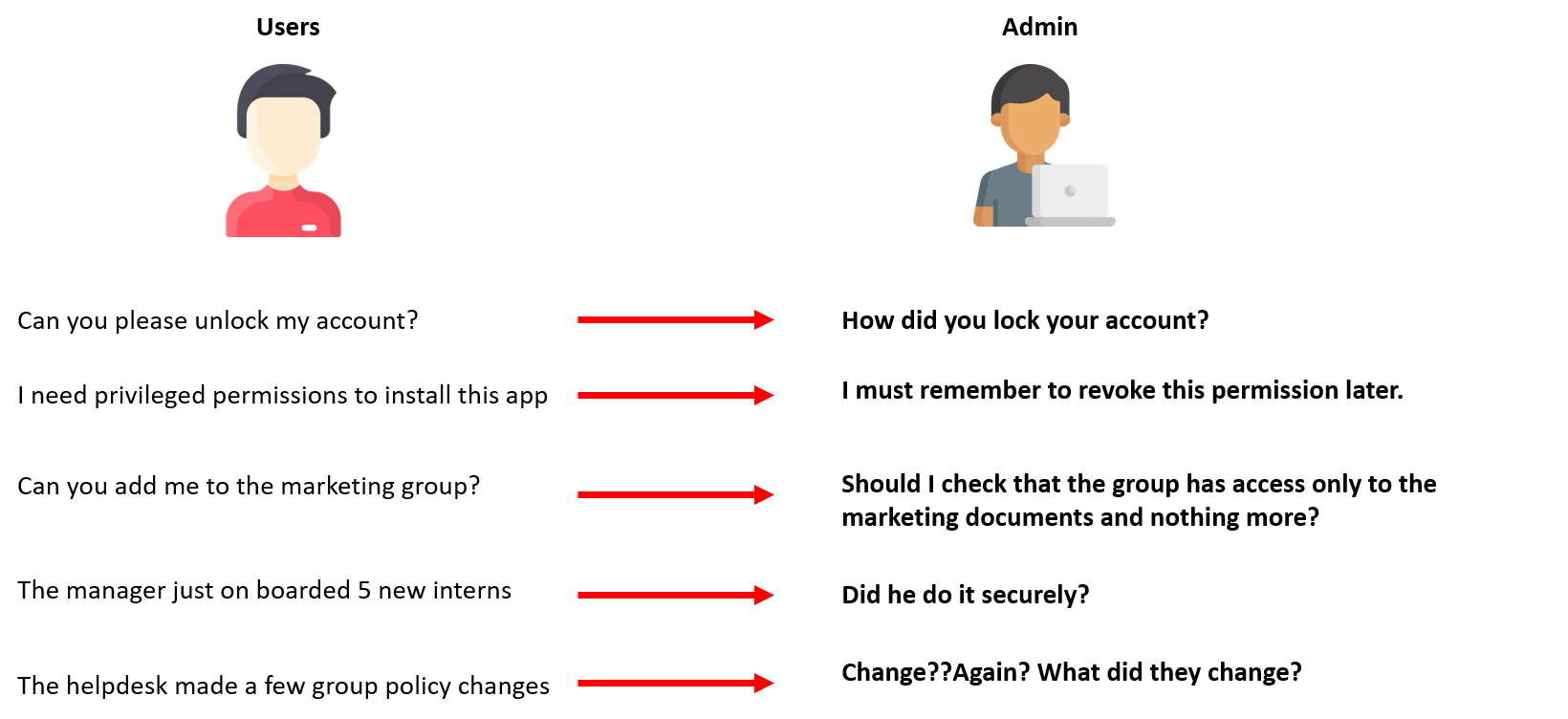 As you can see, although an IT admin tends to the requests and tickets, the skepticism and fear of something unsuitable happening secretly haunts them. Unfortunately, time is not a friend, end users have their job responsibilities and typically can't wait long for a resolution. After a stressful morning of discovering security changes, handling requests and tickets, it's finally time for the best part of the day, lunch! (This is probably the only "me time'" IT admins enjoy.)Afternoon to Evening:
As you can see, although an IT admin tends to the requests and tickets, the skepticism and fear of something unsuitable happening secretly haunts them. Unfortunately, time is not a friend, end users have their job responsibilities and typically can't wait long for a resolution. After a stressful morning of discovering security changes, handling requests and tickets, it's finally time for the best part of the day, lunch! (This is probably the only "me time'" IT admins enjoy.)Afternoon to Evening:  Post-lunch is for confirming if every event that occurred in the network is authorized or not. This is often the most difficult part of the work day as an IT admin needs to survey various components of an IT infrastructure. For example:
Post-lunch is for confirming if every event that occurred in the network is authorized or not. This is often the most difficult part of the work day as an IT admin needs to survey various components of an IT infrastructure. For example:- What are the actions performed by privileged users? Was an end user granted an IT admin role?
- Did help desk reset a users password? Alternatively, did a user self-reset their own password?
- Was data inside a file modified? Was a user given access to read or modify a sensitive file or folder?
- Was the manager of a group changed? Did an end user assume ownership of a folder?
- Modifying Windows firewall inbound and outbound rules
- Trying to brute-force a victim's VPN logon
- Running scripts to obtain domain-rich information, and discover vulnerabilities and possible opportunities for a privileged escalation
- Creating a scheduled task to install malware in the registry keys in the systems
- Introducing malicious executables in core configuration folders (like the SYSVOL folder of group policies) to propagate malware across endpoints
- Granting illicit consent to an application configured in Azure, to maintain backdoor access, and more