Within the confines of the Windows Server environment lies the Group Policy settings, which are the security configuration powerhouses controlling every security event. The legacy audit settings and advanced audit settings—subsets of the Group Policy settings—are the lifelines that help administer many events and their permissions. These security settings must be configured with the utmost caution and monitored at all times to ensure the Windows Server fort is strong against malicious intruder and insider attacks. When an attack happens, an alert containing the event history is emailed to the configured email addresses instantly.
Read on to learn why we recommend the Advanced Audit Policy Configuration settings to ensure the best Windows security auditing.
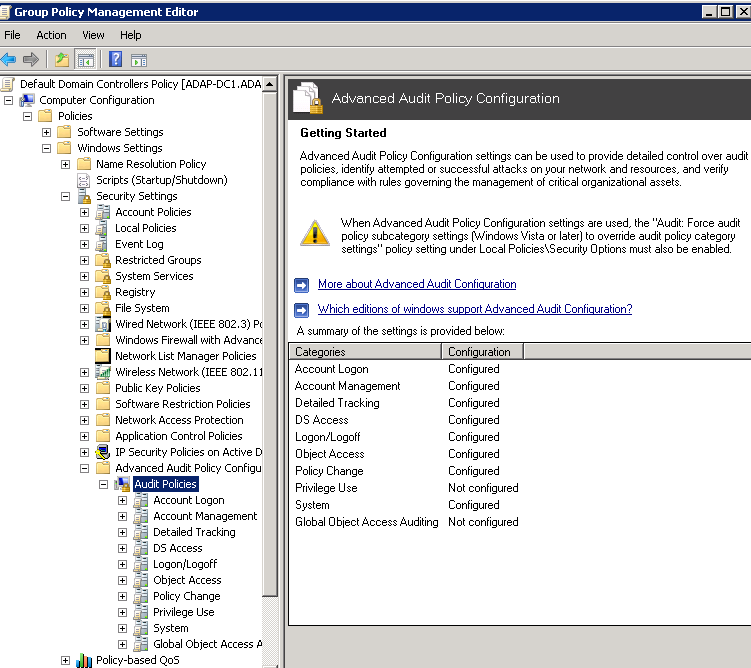
The legacy audit settings and the advanced audit settings are different in their depth of audit event filtering and yet similar in their coverage of events. Legacy audit has nine settings under Windows Settings > Security Settings > Local Policies > Audit Policy, whereas the advanced audit policy has 53 settings under Windows Settings > Security Settings > Advanced Audit Policy Configuration.
| Legacy audit policy settings | Advanced audit policy settings |
| Audit account logon events |
Account Logon
Audit Credential Validation |
| Audit account management |
Account Management
Audit Application Group Management |
| Audit directory service access |
DS Access
Audit Detailed Directory Service Replication |
| Audit logon events |
Logon/Logoff
Audit Account Lockout |
| Audit object access |
Object Access
Audit Application Generated |
| Audit policy change |
Policy Change
Audit Audit Policy Change |
| Audit privilege use |
Privilege Use
Audit Non Sensitive Privilege Use |
| Audit process tracking |
Detailed Tracking
Audit DPAPI Activity |
| Audit system events |
System
Audit IPsec Driver |
Benefits of the advanced audit settings
You might ask if 53 settings are better than nine settings. In most cases, the answer is yes!
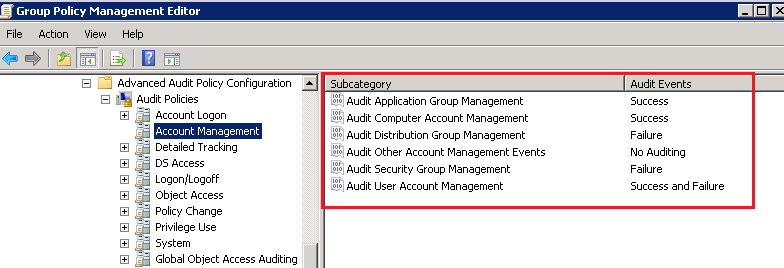
In the advanced audit settings, for instance, the account management setting would provide six audit options, whereas the legacy audit settings provides one. With the Advanced Audit Policy Configuration, administrators can be even more selective in what type of events to audit.
Event log filtering: 6 settings vs. 1 setting
Let’s say you are interested in auditing Account Management. In the advanced audit settings, you would configure the individual audit settings within Account Management and choose which events you want to audit and which events you want to ignore. You can configure success for one event, failure for another, success and failure for yet another, and no auditing at all for a fourth audit setting. This ability to isolate events and record is not possible in the legacy audit settings, where by default all the above events are recorded. In turn, you would be performing a lot of unwanted event monitoring and filling precious disk space with many needless event logs.
Enable subcategory override
While the legacy audit settings can be applied to all Windows versions, the advanced audit settings can be applied only to Windows Vista and above, and Windows 2008 and above.
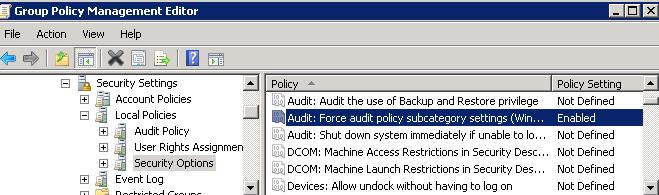
Implementing both the legacy and advanced audit policy settings will cause unexpected outcomes due to conflicts between similar settings in the two groups of policy settings. The below setting will ensure the legacy audit settings are ignored.
Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options. Then enable the override policy, i.e., Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings.
View the documentation below to learn about the required advanced audit policy configurations for a secure Windows Server environment audit setting.
For more information, visit our how-to videos and documentation.
About ManageEngine ADAudit Plus
ADAudit Plus is web-based Windows Active Directory and Windows Server change reporting software. It audits, tracks, and reports on Active Directory, workstation logons and logoffs, file servers, and other types of servers to help meet the most-needed security, audit, and compliance demands. Track authorized or unauthorized access of users, GPOs, groups, and computers, as well as OU changes, with over 150 detailed, event-specific reports and instant email alerts, and export the results to XLS, HTML, PDF, and CSV formats to assist in interpretation and computer forensics.