The IT industry has seen an unshakable surge in malware attacks. According to SonicWall’s 2022 Cyber Threat Report, almost 2.8 billion malware attacks were detected in 2022. Approximately 30% of these malware attacks were carried out using emails containing malicious links and attachments. On June 10, 2022, one such malware, Dark Crystal, also known as DCRat, jolted Ukraine. It is a remote access Trojan (RAT) that has been receiving regular upgrades and new modules since 2018. DCRat malware includes its own integrated development environment (IDE), allowing remote access and control of an infected device.
The execution of the attack
DCRat attacks typically employ a variety of devious strategies, including malspam, phishing, spear phishing, using pirated commercial software such as rouge updaters, and using hacked antivirus software such as Microsoft Defender, to eventually fetch and execute DCRat’s .NET payload on the victim’s machine.
The ubiquitous distribution method relies upon spam campaigns, where thousands of scam emails are sent. A malevolent Microsoft 365 document is sent as an attachment to potential victims. This document contains a macro code that will drop and execute a batch script named c:\user\public\new.bat. Once a victim opens the document, the script is executed in PowerShell to download the second phase payload that is responsible for downloading and executing the actual DCRat malware.
The following is the basic process through which DCRat works:
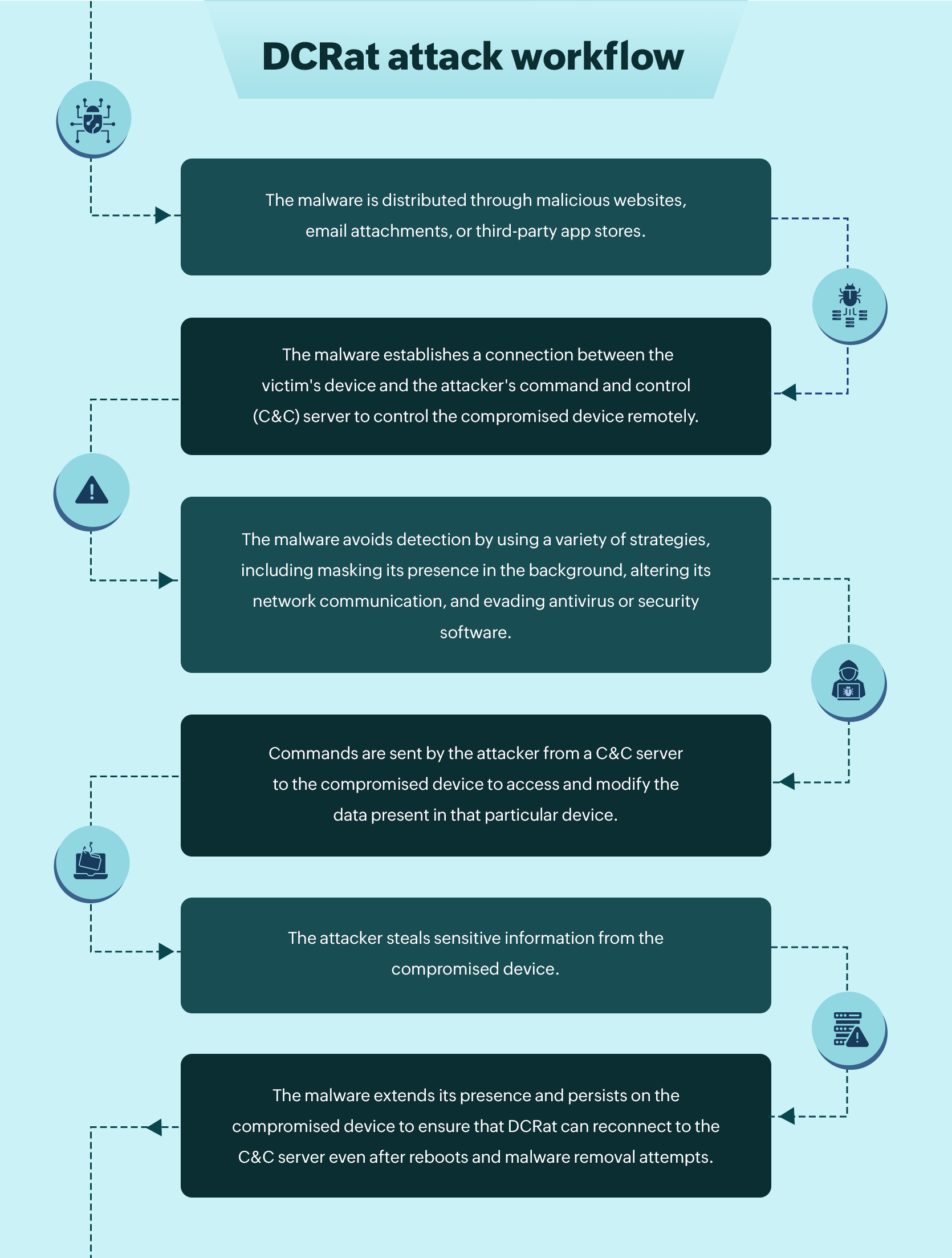
Fig 1: DCRat attack workflow.
The table below lists the various tactic and techniques from the ATT&CK framework relevant to a DCRat malware attack.
|
Tactic |
Technique |
Description |
|
Reconnaissance
|
Gather Victim Host Information (T1592.001) (T1592.002 ) Gather Victim Network Information (T1590.005 ) |
The adversaries gain access to information about the target device. This information might be gathered via various techniques, including phishing and active scanning. Attackers try to gather the victim’s IP address, which can be used during targeting. |
|
Initial access |
Phishing: Spearphishing attachment (T1566.001) |
Attackers try to gain access to the compromised device through spear phishing emails. |
|
Execution |
Command and Scripting Interpreter: PowerShell (T1059.001) Command and Scripting Interpreter: Windows Command Shell (T1059.003 ) |
Attackers now abuse PowerShell commands and scripts for execution. The attackers may also abuse the Windows Command Prompt to control any aspects of the victim’s system with different levels of permissions. |
|
Execution, Persistence, and Privilege execution |
Scheduled Task/Job: Scheduled Task (T1053.005) |
Attackers will abuse the Windows Task Scheduler to execute malicious code. They use the .NET wrapper for task scheduling. |
|
Defense Evasion |
Masquerading (T1036) |
Attackers will manipulate features to appear legitimate to the user. |
|
Defense Evasion |
Obfuscated Files or Information (T1027) |
The attackers try to make the file difficult to analyze by encrypting its content. |
|
Defense Evasion |
System Binary Proxy Execution: Mshta (T1218.005) |
Adversaries may abuse mshta.exe to proxy execute malicious HTA files and JavaScript through a trusted Windows utility. |
|
Discovery |
System Time Discovery (T1124) |
The attacker will try to discover the time zone of the remote system with the help of .NET executables. |
|
Command and Control |
Ingress Tool Transfer (T1105) |
The attackers transfer tools or files from their external system to the compromised system. |
|
Impact |
Data Destruction (T1485 ) |
The attackers try to destroy, modify, create, or overwrite files on specific systems. |
|
Impact |
System Shutdown/Reboot (T1529) |
The attackers may try to reboot or shut down systems to interrupt access. |
Best practices to prevent a RAT attack
-
Update your OSs, programs, and antivirus software frequently. Security fixes that fix flaws that RATs could exploit are frequently included in software updates.
-
Make sure the firewall is activated on each of your devices to prevent unapproved incoming and outgoing connections.
-
Avoid downloading from unidentified or dubious websites because they can house malicious files. Use trustworthy antivirus or antimalware software. Run system scans frequently to find and get rid of any potential RATs or malware.
-
Adopt safe browsing practices and remain cautious during online interactions. Watch out for phishing emails, phishing messages, and suspicious links.
-
Make regular backups of important files and store them in a safe place. In the event of a RAT infection or other security incident, backups allow you to restore your data without paying a ransom or suffering significant losses.
How can a SIEM solution aid in tackling such attacks?
An effective SIEM solution will have capabilities to detect, prioritize, investigate, and respond to security threats. It can detect and help mitigate various malware attacks, including DCRat.
The following actions can be performed with an effective SIEM solution:
-
Audit PowerShell to see what scripts are executed in your system, with the details on who executed the script and when the script was executed.
-
Monitor all file changes, including renaming, creation, modification, and deletions.
-
Receive alerts on any unusual activities, including malware activities.
-
Analyze multiple events across your network to identify threats.
-
Monitor and audit network shares in your organization.
-
Track suspicious activities in your file servers and endpoint devices.
-
Monitor logon and logoff events.
If you want to protect your organization from malware such as DCRat, sign up for a personalized demo of ManageEngine Log360, a unified SIEM solution with data security and cloud security capabilities.