
ManageEngine Log360 was featured in the GigaOm Radar report on Automated Security Operations Management (ASOM), published in October 2022 and written by Logan Andrew Green. The research firm’s report includes an in-depth study of the solutions offered by some of the major vendors in the market and highlights Log360 as a Challenger in the ASOM sector.
Log360 is a unified SIEM solution from ManageEngine with integrated DLP and CASB capabilities. It helps detect, prioritize, investigate, and respond to security threats. It combines threat intelligence, machine learning-based anomaly detection, and rule-based attack detection techniques, and offers an incident management console for remediating detected threats effectively.
ASOM: A new integrated category
GigaOm believes that in today’s rapidly changing threat landscape, it is important to integrate security information and event management (SIEM) solutions along with security orchestration, automation, and response (SOAR) tools in order to help analysts manage threats more efficiently. This new integrated category has been defined by GigaOm as automated security operations management (ASOM).
The report assesses the featured vendors based on:
-
The findings of two previous GigaOm reports: “Key criteria for evaluating security and information events management” and “Key criteria for evaluating security orchestration and automation response.”
-
The solution’s functionality.
-
The extent of the solution’s SIEM and SOAR integration.
After assessment, vendors are placed in a visual radar graphic. The placement shows whether the vendor is a platform-play or a feature-play, and whether it is a mature organization or an innovative one. The above parameters combine to provide a picture of a vendors’ execution prowess, future roadmap, ability to innovate, approach, strength within the ecosystem, etc. These measures in turn help define the four corners of the radar graphic: maturity and innovation; feature play and platform play.
ManageEngine’s SIEM solution, Log360 is placed on the radar as a Challenger and Fast Mover; it is also advancing towards the leader-focused center. Further, it is placed on the Platform Play side of the chart, indicating that it provides an integrated SIEM/SOAR product. Along the vertical axis, which compares maturity vis-à-vis innovation, ManageEngine’s modular solution is placed towards the Innovation side.
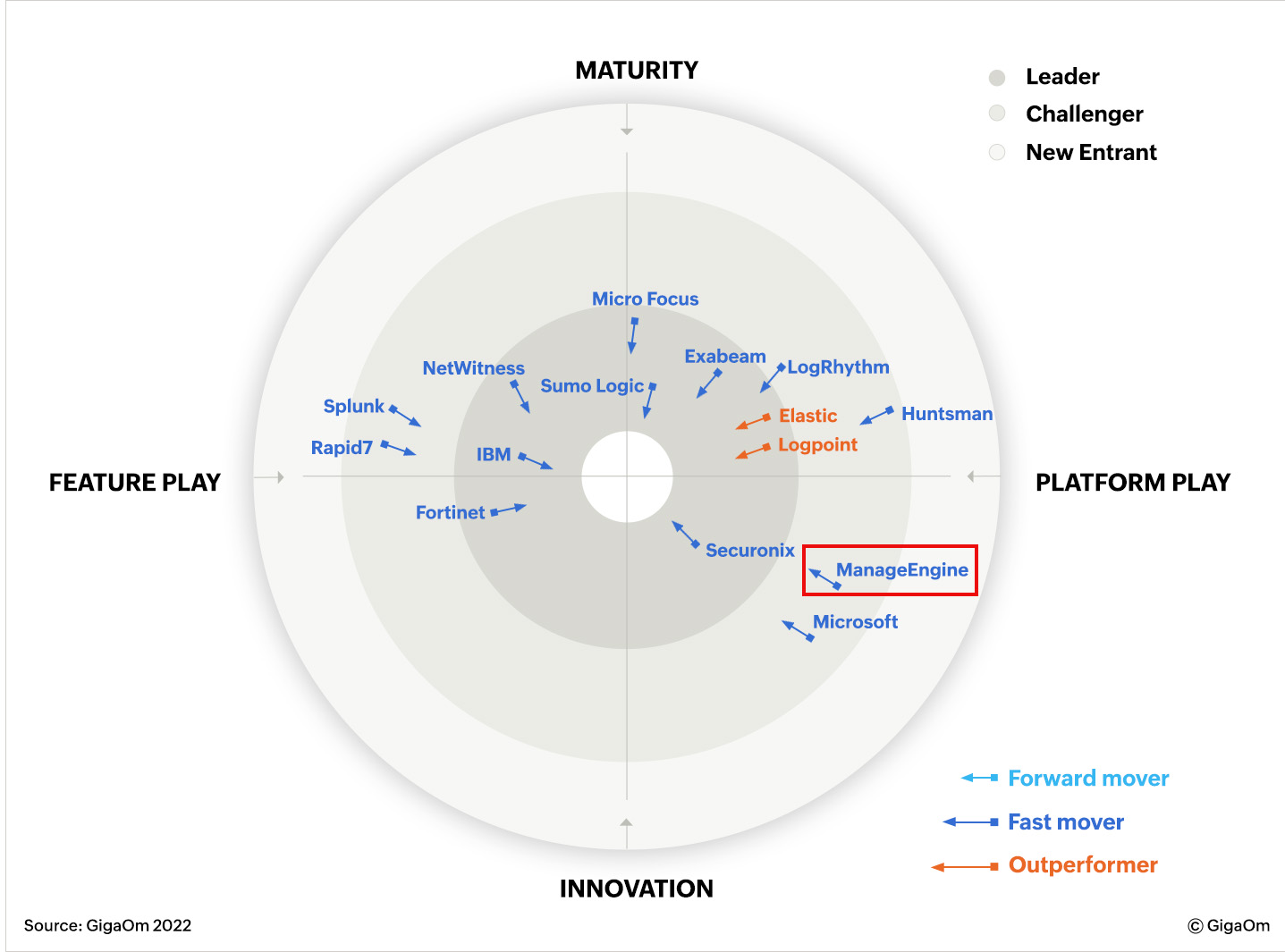
Referring to ManageEngine’s suite of products as the Swiss Army Knife of SIEM solutions, the report highlights the following strengths of Log360:
-
Market segmentation
-
SIEM features of log and compliance management
-
SIEM-SOAR integration
-
ML-related developments
Market segmentation
Log360 has extended its wings into different market categories, such as small and midsize businesses (SMBs), large enterprises, regulated industries, managed security service providers (MSSPs), and network service providers. Log360 has a concentrated market in the US, is gaining a foothold in European countries, and is further extending its market into Middle Eastern countries and India. ManageEngine’s prestigious clientele includes eBay, IBM, Toshiba, L&T Infotech, and Cisco, among many others, spanning across different industries.
SIEM features: Log and compliance management
ManageEngine Log360 has some of the best SIEM features in the market. It can collect data from more than 750 sources, including servers, applications, workstations, vulnerability scanners, virtual environments, databases, threat solutions, and cloud infrastructures, and then analyze them to detect security threats. With this, security analysts can triage the threats, analyze and mark them as incidents, and quickly remediate them with automatic workflow capabilities. Log360 features rule-based, signature-based, and machine-learning-based threat detection capabilities with its real-time correlation engine, MITRE ATT&CK threat modelling framework adoption, and UEBA module, respectively.
The correlation engine of Log360 comes with pre-built rules to detect known threats and attacks such as brute force, various strains of ransomware, and more. This engine is integrated with the response module for automatic workflow execution for containing attacks. The correlation engine also provides users with a detailed incident time line to help in post-breach impact analysis. Further, the solution adopts the threat modelling framework MITRE ATT&CK to detect various tactics and techniques used by adversaries. The techniques can be correlated to trace the complete attack pattern at various stages, and granular workflow actions can be setup to stop the spread of the attack. Log360 is also capable of generating IT audit reports as per the requirements of the various auditing standards such as SOX, HIPAA, GLBA, FISMA, and PCI DSS and generating custom reports for other compliance requirements.
SIEM-SOAR integration
SIEM-SOAR integration is among the most sought after combination by enterprises today. Integrated SIEM-SOAR solutions enable a user to manage all the SIEM activities, generate required reports, and also orchestrate defensive response actions over threats. Further, it enables the automation of any preventive actions to be taken against such threats. Security operations center (SOC) analysts can manage incidents by using the integration with ticketing systems and can assign them to the right admins as soon as the alert is triggered. Log360 provides a comprehensive incident management dashboard that helps analysts to measure the performance of their SOCs and optimize them. The incident dashboard gives key metrics such as the mean time to detect (MTTD), mean time to resolve (MTTR), and overdue and unattended incidents. Log360 can be integrated with help desk software like ManageEngine ServiceDesk Plus, Jira Service Desk, Zendesk, ServiceNow, and more.
ML-related developments
Machine learning (ML) and artificial intelligence (AI) are becoming the fuel for any tech-related solution, making ML and AI-based security solutions the need of the hour. ManageEngine’s Log360 is successfully incorporating ML and AI into its capabilities. With threat feeds from various threat analytics vendors, Log360 is able to detect threats quickly. ML innovations in SIEM solutions have led to advanced UEBA or anomaly detection: The process of detecting any anomalous activity performed by a user or entity within the network. The data from log sources are collected, and the ML algorithm models study the data to develop a baseline for a particular user or entity. For example, a login or logoff at an unusual hour would trigger an anomaly, alerting the analyst. Similarly, any anomalous file deletion can be detected and raise an alert. UEBA can be further enhanced with seasonality and peer group analysis to make threat detection more accurate. Get an in-depth understanding about seasonality by reading more here.
Analyst’s view
The GigaOm report highlights that ASOM solutions are the current industry demand, as they provide an off-the-shelf comprehensive tool for analysts to manage most security activities. However, it also suggests that ASOM solutions are highly complex, and many enterprises are looking out for affordable SIEM solutions with SOAR and UEBA capabilities. While SIEM-as-a-service or managed SIEM offerings do come in handy, they may lack the technical knowledge and cultural understanding about the customer.
AI-driven automation and solutions provide a more sustainable solution. AI-based solutions have the ability to detect threats on their own. GigaOm describes ManageEngine Log360 as a robust platform that can support a range of features and capabilities, and also provide affordable security solutions with AI and ML intervention to small and large-scale enterprises of all industries.
