This year’s Cybersecurity Awareness Month has come to an end and, with every passing year, cyberthreats are increasing in number and complexity. Reactive solutions are no longer enough to confront cyberattacks. Organizations must implement proactive strategies to secure their IT assets.
During the pandemic, many organizations adopted remote work to ensure business continuity. Hybrid workforce models enable a lot of employee flexibility perks, but from a cybersecurity perspective include significant security challenges, such as securing remote and BYOD devices against new and endpoint-targeted attacks. According to the 2020 Ponemon Institute report, 68% of organizations experienced one or more endpoint attacks in a span of 12 months that successfully compromised data and their IT infrastructure. This number reinforces that endpoints, especially remote ones, are often the entry points to an organization’s network and introduces three important questions:
1. What are the types of attacks that target endpoints?
2. What are the attack surfaces at the endpoint level that need to be secured?
3. What type and how many endpoint security solutions are required to secure your IT assets against major attacks?
Let us try addressing these questions one by one.
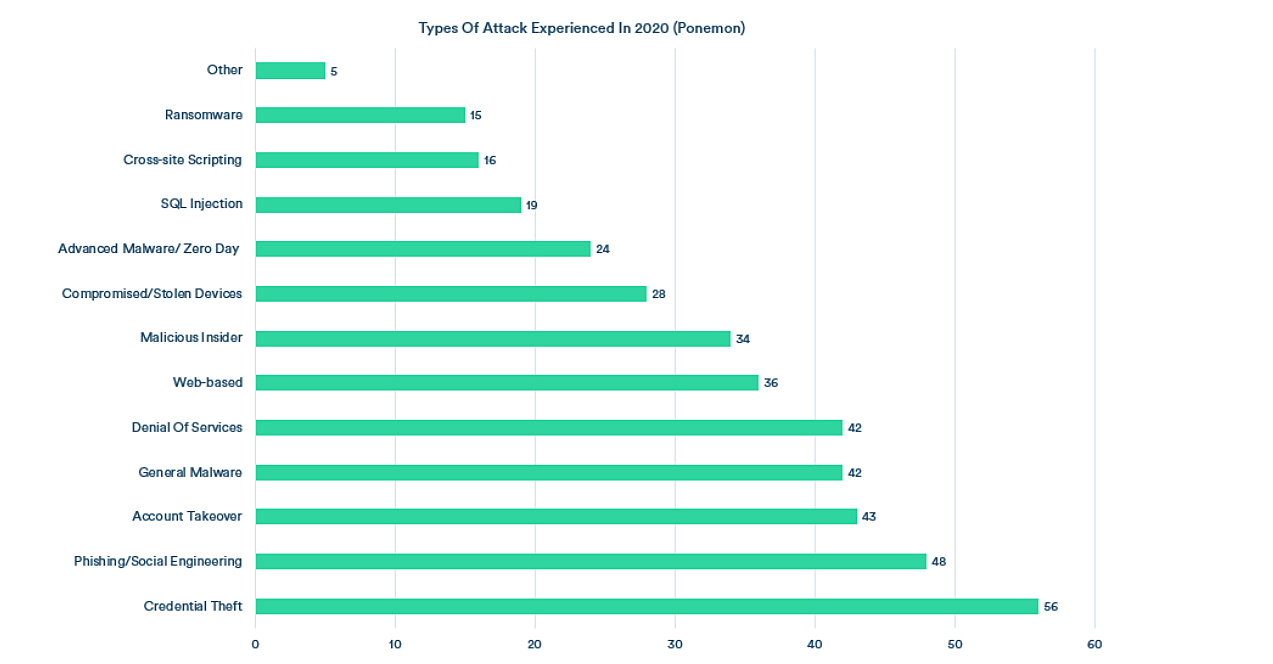
Types of attacks that target endpoints: According to a survey by Ponemon, 56% of organizations faced credential theft and 28% of organizations faced attacks involving stolen devices and compromised devices. Some of the other types of attacks that target endpoints are ransomware, malware, zero-day, web- and browser-based, malicious insider, unauthorized devices, social engineering targeting malicious applications, and data theft from stolen devices.
Attack surfaces at the endpoint level that need to be secured:
-
Unauthorized plug-ins
-
Unpatched applications/end of life applications/legacy software
-
Malicious add-ons/browser extensions
-
Unfiltered web URLs
-
Malicious applications
-
Absence of role-based privilege management
-
Un-encrypted hard drive that poses a risk of data breach in case of hardware theft
Features of an ideal endpoint security solution:
Broadly, most of the attacks mentioned in the graphic can be solved through seven specific solutions that we’ll address in more detail below. It’s vital to understand, however, that it’s not ideal or financially feasible for organizations to invest in seven, or even multiple, software solutions to address endpoint security issues.
Endpoint security needs to be unified. Users must be able to secure various endpoint attack surfaces from a single centralized console and deploy a single solution to ensure the issues are mitigated and resolved in a timely and efficient manner.
This unified endpoint security solution must ideally possess the following features:
Vulnerability management:
-
Monitor and manage actively exploited and publicly disclosed vulnerabilities in your network.
-
Secure zero-day vulnerabilities with alternate fixes until the patches are available.
-
Detect and resolve security misconfigurations like weak passwords, default configurations, disabled firewall, unused users and groups, and open shares.
-
Identify and uninstall high risk software, such as end-of-life, peer-to-peer, and desktop sharing software.
Patch management:
-
Completely automate the patch deployment process.
-
Patch OS and third-party applications across heterogeneous platforms.
-
Adopt flexible deployment policies that let users patch according to their requirements.
-
Decline patches to groups of computers running business critical applications you don’t want updated.
-
Automatically test patches and approve them for deployment.
Browser security:
-
Track the browsers and their add-ons used in your network.
-
Monitor and control browser extensions, plug-ins, and add-ons present in your network.
-
Filter URLs to ensure that only trusted and authorized websites are accessed.
-
Restrict downloads from unauthorized websites.
-
Harden browsers by configuring the necessary browser security settings.
Device control:
-
Allow, restrict, or remove devices based on the organization’s requirements.
-
Establish a list of trusted devices and allow them to access endpoints.
-
Grant temporary access to restricted devices with ease.
-
Enable file shadowing and file tracing.
-
Set role-based access to files and limit file transfer rates.
Application control:
-
Automate discovery of all running applications.
-
Build rule-based application lists and associate them with user groups.
-
Whitelist trusted applications and blacklist malicious applications, down to the executable level.
-
Regulate and manage greylisted applications with ease.
BitLocker management:
-
Scan managed systems for BitLocker encryption status and drive details.
-
Enable Trusted Platform Module (TPM) management from a single console.
-
Create drive encryption policies and associate them with target groups.
-
Enforce multi-factor authentication for computers without TPM.
-
Utilize safe recovery key retrieval options.
Endpoint detection and response:
-
Initiate incident data search and investigation.
-
Prioritize alerts about suspicious activities to determine whether the response should be escalated.
-
Deploy suspicious activity detection.
-
Utilize threat hunting and data exploration.
-
Detect and stop malicious activity in the network.
Desktop Central has crossed a milestone to bring unified security with its Endpoint Security add-on. It provides vulnerability management, browser security, device control, application control, and BitLocker management integrated into a single add-on. Evaluate the comprehensive feature list. With the Endpoint Security add-on, you benefit from five additional security solutions within the same, single console. To investigate all the features, download Desktop Central’s 30-day free trial. Navigate to Admin > Endpoint Security add-on and enable it. Experience hands-on ManageEngine’s across-the-board unified endpoint management and security solution today.

