On March 9, 2021, Verkada, a software company that specializes in making security cameras for monitoring physical access control, was subject to a security hack.
Hackers gained access to the video feed of at least 15 thousand cameras deployed across various locations and exposed the inner workings of hospitals, clinics, and mental health institutions; banks; police departments; prisons; schools; and companies like Tesla and Cloudflare.
The hackers’ tweets relating to the Verkada hack contain the #OperationPanopticon hashtag. The panopticon is a type of institutional building and a system of control. It’s concept is to allow all prisoners of an institution to be observed by a single security guard without the inmates being able to tell whether they are being watched. Pretty apt concept, right?
Organizations were being watched. What can they do about it?
This incident is a testament to just how broadly we’re being surveilled and tracked, and how often little care is put into securing the platforms used to do so. But before we head into the specifics, how did the attack on Verkada happen?
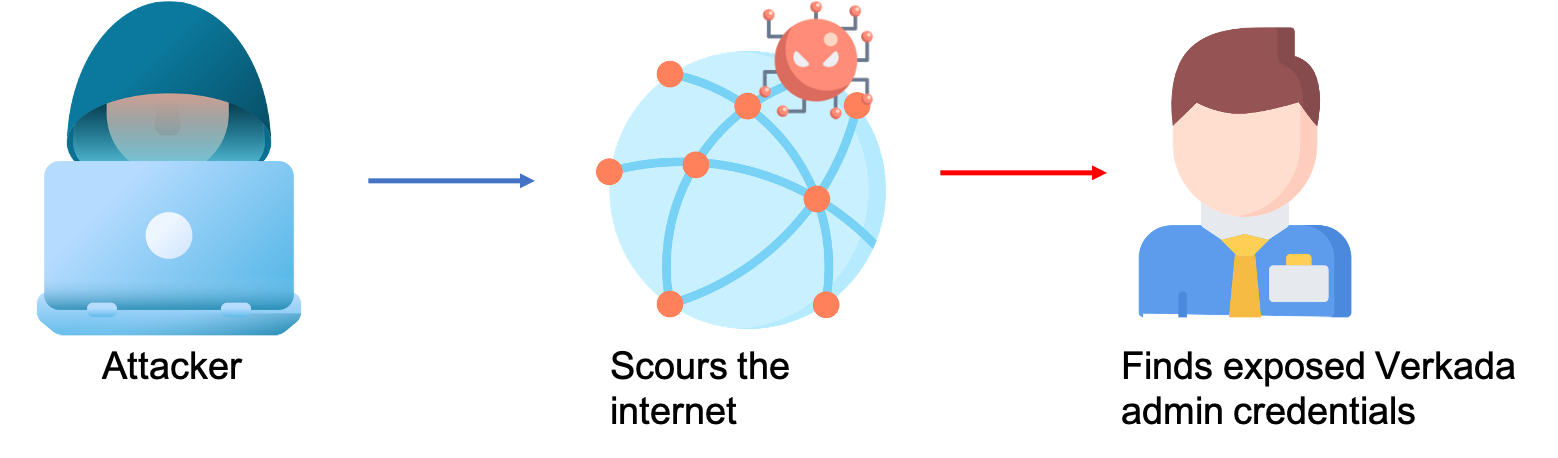
The attackers claimed that they were able to get an administrator’s account credentials, which were publicly available online, with Super Admin rights, giving them access to any camera belonging to any of the company’s clients.
Not only did Super Admin rights provide access to video feeds, they also provided access to the root shell inside the cameras running inside each customer’s facility.
No Zero Trust principle: History repeats itself
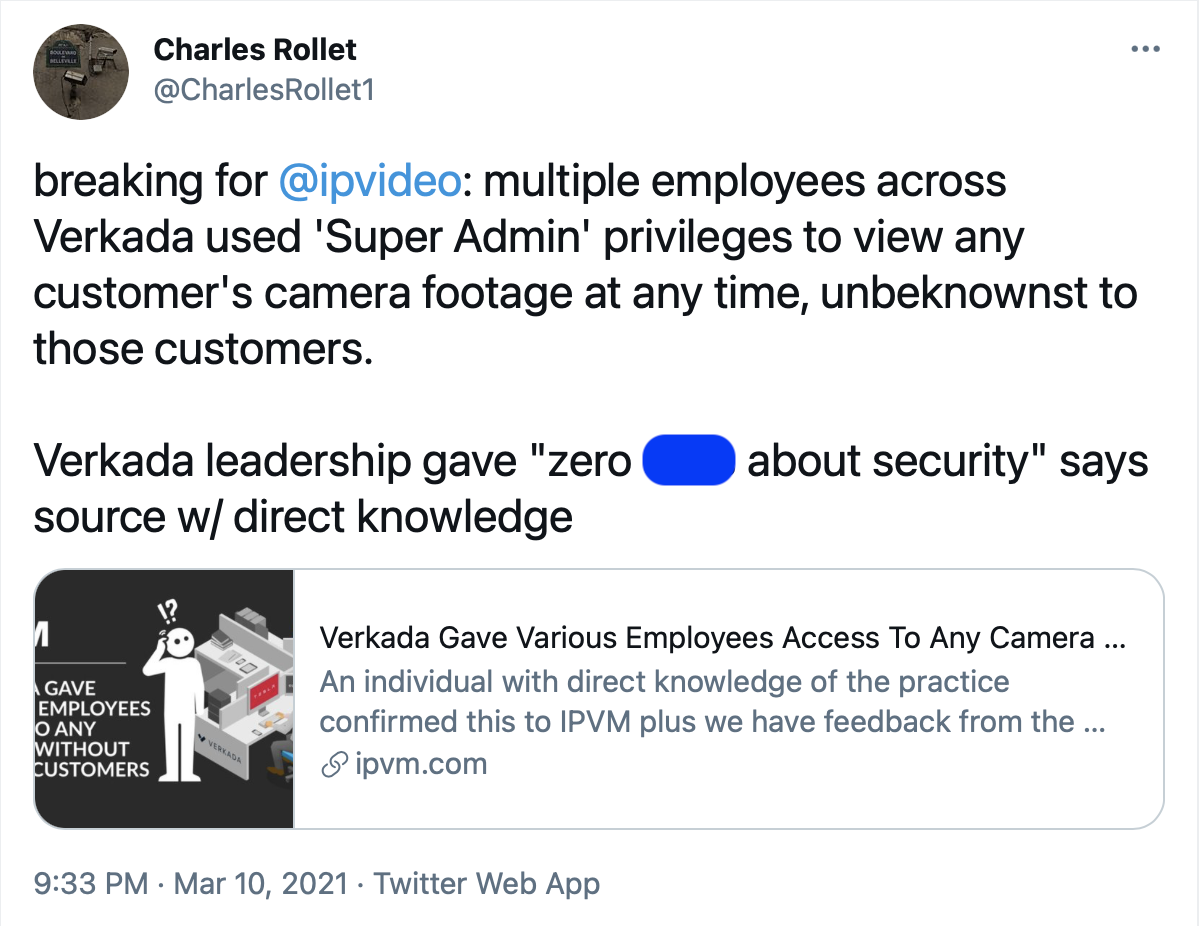
Some organizations essentially give users free access instead of giving users only the access they require. After the Verkada breach, it was discovered that basically every team member had Super Admin privileges.
So there you have it. That’s the first problem.
Access to the server was not monitored
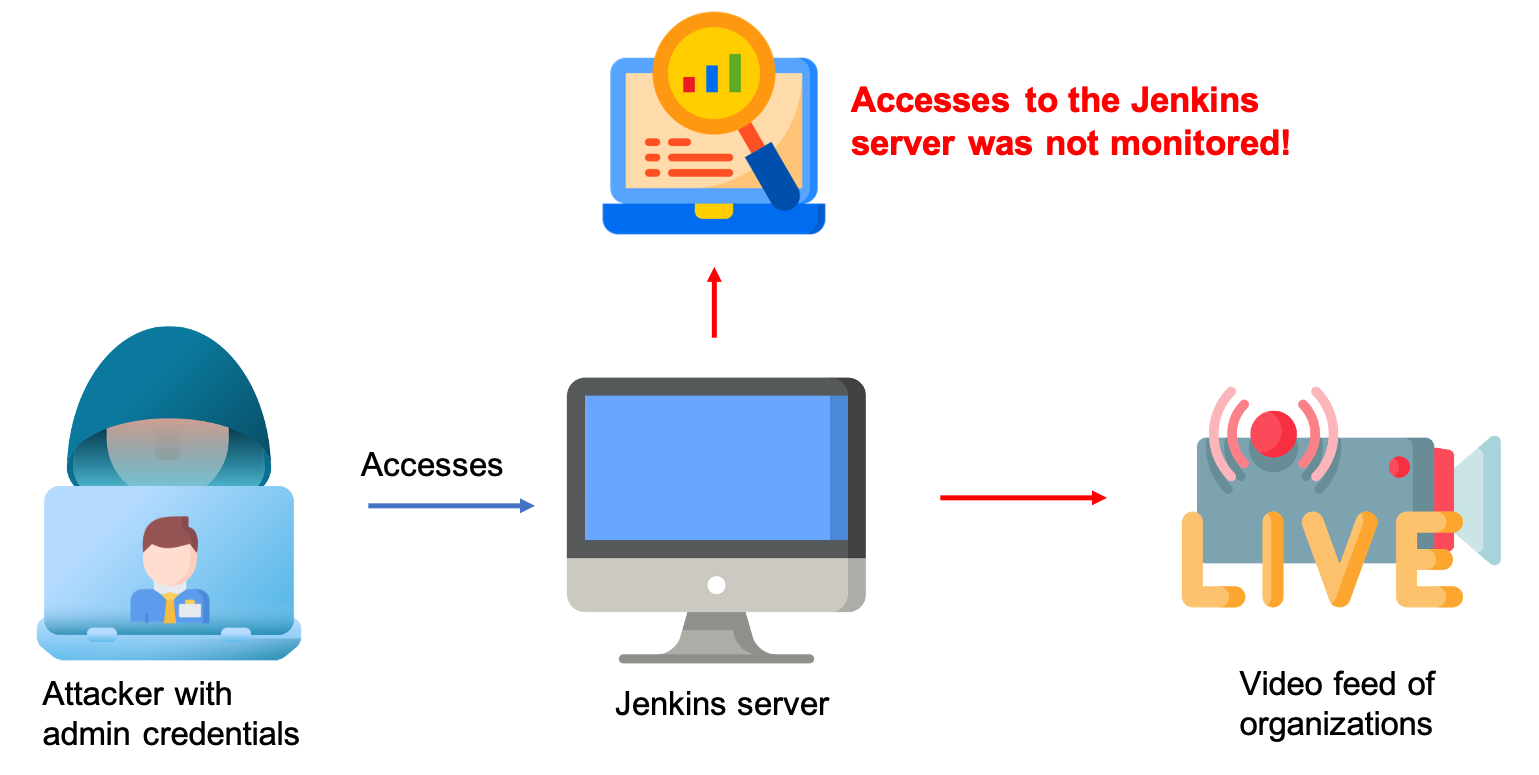
According to the company, attackers gained access via a Jenkins server used by the support team to perform bulk maintenance operations on customer cameras.
If the Jenkins server was monitored by Verkada for unauthorized access from unknown hosts, the attack could have been stopped in its tracks.
“Monitor all servers, users, and endpoints connected to your network.” This is yet another principle of Zero Trust that was not enforced.
Features and tools native to the system were not monitored
The hackers said that they were able to obtain root access on the cameras, meaning they could use the cameras to execute their own code. Obtaining this level of access did not require additional hacking, but attackers were able to leverage a built-in or pre-installed feature of the cameras.
It is a growing cyberattack trend, where attackers are leveraging command line shells and other components of the OS to help move their attacks forward and blend malicious actions with genuine, authorized processes.
Monitoring parts of your OS (like registry key changes, command line activities, and policy changes) that originally could not be modified by anyone except admins is crucial to detect the presence of threat actors in your network.
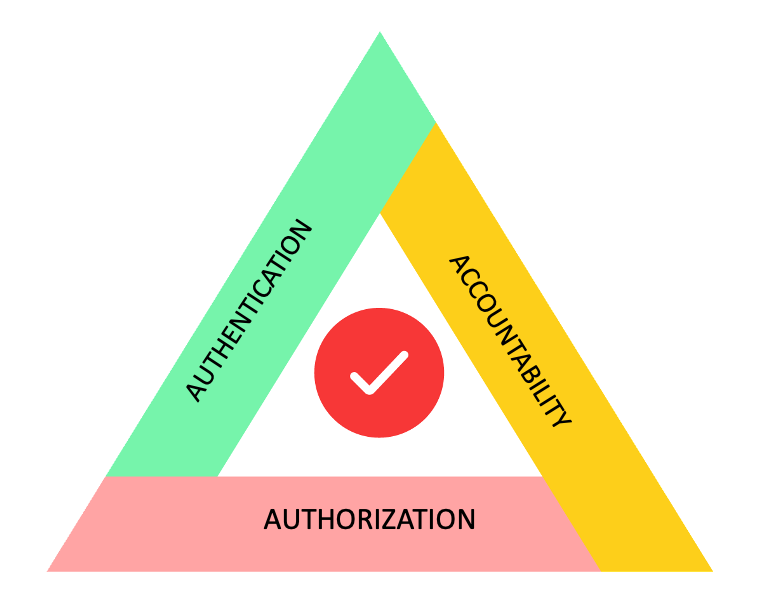
To summarize, Verkada failed to address the three important principles for secure identity and access management (IAM).
-
It failed to secure authentication, because super administrator credentials were publicly exposed on the internet.
-
Unrestricted, authorized access to all critical resources was a dream come true, not only for employees, but for the attackers as well, because admin privileges were granted to employees haphazardly.
-
Lastly, Verkada couldn’t hold anyone accountable for malicious actions through the Jenkins server nor could it track commands executed after root access was obtained. It also failed to monitor attempts to access the archived video recordings from cameras in client organizations.
Verkada fell short on these IAM requirements because it did not have an end-to-end security incident monitoring, alerting, and response strategy for its network.
Check out our integrated IAM solution, ManageEngine AD360, built to meet the IAM and cybersecurity requirements of today’s IT world. Upgrade your IAM game before it’s too late!
If you have any questions, leave a comment below and we will get back to you!

