
From the outset, Apple has been keen to protect user privacy and security, and deprecating kernel extensions is one of the company’s latest moves towards modernizing its platform. As part of Apple’s sustained effort to make macOS a more reliable and secure platform, the tech giant announced at WWDC 2019 that kernel extensions are going to be replaced in macOS Catalina with Apple’s new technology, system extensions. But, why should you care? Let’s explore now.
What are kernel extensions?
The kernel is the core of the operating system; it facilitates the interaction between macOS and software components, performing low-level tasks such as disk management, task management, and memory management. A kernel extension, aka a KEXT, is an application bundle used to extend the native functionality of macOS by allowing software to load directly in the macOS kernel. Antivirus software, firewalls, VPN clients, and USB drivers all take advantage of KEXTs.
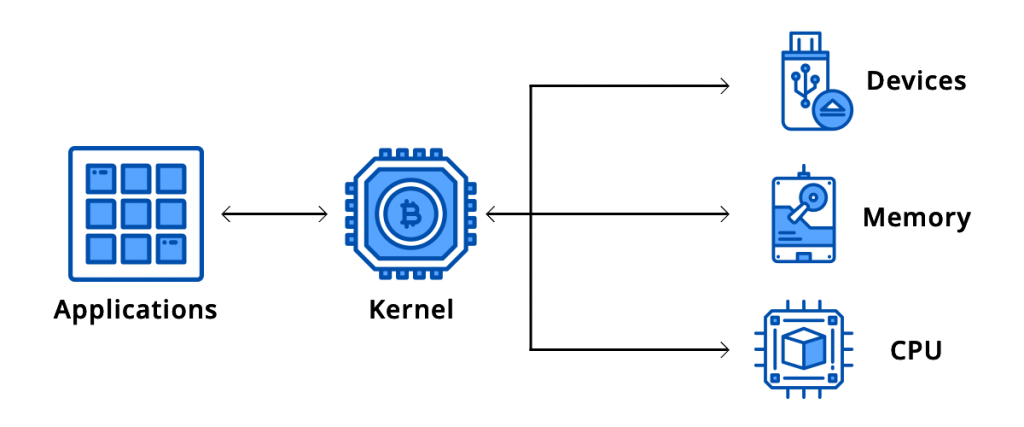
The pitfalls of KEXTs
Since KEXTs are programmed to load in the protected kernel space, if a KEXT crashes or malfunctions it can cause a kernel panic and take down the whole system. System extensions work similar to KEXTs, but they run in the user space outside the kernel like other applications. This makes system extensions more reliable and secure, as well as easier to develop.
Three kinds of system extensions can be built in Catalina: network extensions, driver extensions, and endpoint security extensions. With network extensions, you can customize the networking features of OS X, such as creating and managing VPN configurations using the built-in VPN protocol, personal VPN, or a custom VPN protocol. Driver extensions control hardware devices such as USB, serial, network interface, and human interface devices. Extensions built with Apple’s Endpoint Security framework monitor system events like process executions and raising signals for potentially malicious activity.
The kernel defines and enforces the rules of the system’s security policy. When a KEXT loads, it becomes part of the kernel and gets access to everything on the machine. Since a KEXT is part of the kernel, which makes security rules, it is above the rules. There are no security rules that can restrict it. If a KEXT is compromised, it can take over the entire machine, introducing critical security and reliability problems.
Unlike KEXTs, system extensions run in user space outside the kernel, so they have to follow the rules of the system security policy. System extensions are granted special privileges like having direct access to their associated hardware devices, or using special APIs to communicate directly with kernel systems. Ergo, if a system extension crashes, the rest of the system and apps are unaffected and keep running.
What does it mean for you?
-
As KEXTs are phased out, you may start receiving warning messages from Apple when software on your Mac loads legacy KEXTs. This is to give you advance notice that the loaded extension will be incompatible with a future version of macOS.
-
Installing third-party KEXTs on macOS Catalina now requires that you restart your Mac before they’re permitted to load.
-
As system extensions serving the same purpose as existing KEXTs are added, KEXTs will be gradually replaced in macOS Catalina.
-
Like KEXTs, system extensions need to be granted permission to access or modify operating system components; that permission can be granted either manually by an admin user or by an MDM provider.
Using an MDM solution like Mobile Device Manager Plus, you can whitelist only requisite system extensions, avoiding any potential security threats. With features like automated bulk enrollment, remote management, automated OS update management, and theft detection, you can put your feet up and let your MDM tool take care of your IT assets. Start your free trial now, to see for yourself!

