Microsoft has two solutions for deploying the requirements for Active Directory domain users passwords. The requirements, referred to as the password policy, can be deployed through Group Policy Objects (GPOs) or through Active Directory objects called fine grained password policies (FGPPs). Both solutions have the same list of constraints, such as minimum password length and maximum password age, but the details around the implementation are radically different.
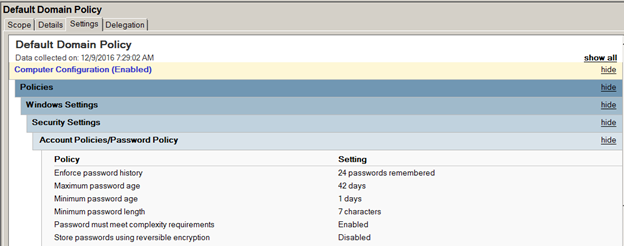
Deploying a password policy using a GPO is the seasoned solution, since it was introduced when Active Directory was released in 2000. By default, the password policy is configured in the Default Domain Policy, which is linked to the domain node. Figure 1 illustrates what the password policy has been for the past ten or more years.
Figure 1. Password policy configurations in the Default Domain Policy.
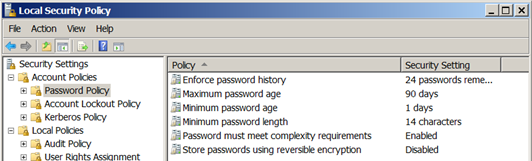
Although the password policy can be configured in any GPO and linked to any node within Active Directory, the only password policy settings that will be applied to domain users will be in GPOs linked to the domain, containing password policy settings, and with the highest priority. Therefore, there can be only one password policy for all of the domain users in a single domain. To see the resulting password policy, you can run secpol.msc from the command line of any of the domain controllers in your domain. The result can be seen in Figure 2.
Figure 2. Resulting password policy deployed using a GPO as shown by the secpol.msc command.
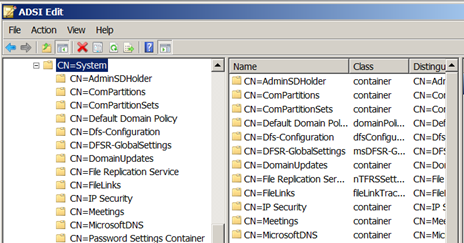
FGPPs, on the other hand, are not deployed by using a GPO in any way. Instead, FGPPs are defined inside of Active Directory by creating a Password Settings Container. This can be accomplished by using ADSIEdit.msc from a domain controller in the domain. You can see the Password Settings Container in Figure 3.
Figure 3. Password Settings Container allows the creation of FGPPs.
Right-clicking on the Password Settings Container allows you to create a new object, which then walks you through a wizard that helps you define the settings. The settings for FGPPs are the same as for the password policy deployed through a GPO (see Figure 2 for those settings), but instead of directly modifying each setting, the wizard prompts you for each setting.
There can be more than one FGPP, allowing for more than one password policy for domain users in the same domain. To target which users receive the appropriate FGPP, the msDS-PSOAppliesTo attribute of the newly created FGPP object needs to be configured with the appropriate group(s). More than one group can receive a single FGPP. If there is a user that does not receive a FGPP through group membership, the password policy deployed through the GPO linked to the domain will be applied to that user. Each FGPP has a priority configuration, so if a user is part of more than one group listed as the msDS-PSOAppliesTo attribute on the FGPPs, the user will receive only the password settings contained in the highest priority FGPP for which a group they have membership in is listed.
A few clarifying notes:
- There can be only one password policy if you use the password policy settings in a GPO.
- A GPO linked to an organizational unit (OU) will not affect domain users located in that OU.
- No additional settings can be configured for the password policy, except those listed in Figure 2.
- A new password policy filter can be created and implemented for the domain, but this requires significant development and configuration.
- FGPPs do not provide any additional password policy controls other than those listed in Figure 2.
As you can see, both Microsoft solutions are a little confusing, but effective. If you want more than the basic password policy configurations, you will need to look at other solutions. In our next blog post, we will compare these two Microsoft solutions to ADSelfService Plus, which offers more granular controls and deployment through OUs. To get your sneak peak at ADSelf Service Plus now, download it here.


Password “max age” is a thing of the past. Please stop making your users change them. All they do is add 1 or ! to the end of the current password…and the bad guys know this. As of 2019, this is no longer considered standard for general users:
https://www.isaca.org/resources/isaca-journal/issues/2019/volume-1/nists-new-password-rule-book-updated-guidelines-offer-benefits-and-risk
(Look at the 4th bullet-point)
Some one hack mee again and change my domain
Hi,
Is there any way to check whether FGPP’s applied successfully or not on particular group.
Hi Shankar. This can be checked the following ways:
1) msDS-PSOApplied attribute of the group holds the DN of the applied PSO.
2) msDS-PSOAppliesTo attribute of the PSO (multi-valued) contains the DN of the group and users that it applies to.
Reference:
1) https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc770848(v=ws.10)
2) https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-ada2/336e2078-6d91-4adf-9e70-a23e746b840b
3) https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-ada2/a182b5e8-8141-43e4-9c17-67fade1984a7
The same can be queried using the Active Directory PowerShell module.
Get-ADGroup -Identity groupSamName -properties * | Select-Object msDS-PSOApplied
Reference: https://docs.microsoft.com/en-us/powershell/module/activedirectory/get-adgroup?view=windowsserver2019-ps
Hello,
Is there a maximum number of FGPP’s a domain can have? If I define 10 user groups with no users in common, can each group have a separate and different PSO?
thanks
Hi Peter. No, there’s no fixed limit; it’s just an object. If you define 10 users groups with no users in common then each group will have a separate PSO.
I want to check Passoword policy of an end point using a command line such that i can implement it in a program . Is there a way to check those, especially “Password Complexity” value? Net Account command is not giving this particular key value.
Hi Shiv.
1) The password policy settings of the default domain policy can be obtained using the following PowerShell command:
Get-ADDefaultDomainPasswordPolicy
Please note that the password policy settings of a domain-level GPO will be applied for the entire domain.
Reference: https://docs.microsoft.com/en-us/powershell/module/addsadministration/get-addefaultdomainpasswordpolicy?view=win10-ps
2) For FineGrained Password Policies (FGPP) / PSO, refer to the following PowerShell commands:
Get-ADFineGrainedPasswordPolicy
Get-ADUserResultantPasswordPolicy
References:
https://docs.microsoft.com/en-us/powershell/module/addsadministration/get-adfinegrainedpasswordpolicy?view=win10-ps
https://docs.microsoft.com/en-us/powershell/module/addsadministration/get-aduserresultantpasswordpolicy?view=win10-ps
3) In terms of the password policy settings for machine accounts, machine accounts are exempted from password policy settings. Read more at https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/machine-account-password-process/ba-p/396027.
Hope that helps!
One should look at ActivePasswords too. Very flexible password settings for both groups and OU’s.
If you’re running Server 2012 or newer, you can run Active Directory Administrative Centre (ADAC) and edit the fine grained password policies there, instead of using ADSI Edit. Plus you can select a user in ADAC, click on “View resultant password settings” and get accurate details. Some other ways of doing this like net accounts, GP Results Wizard etc don’t appear to be aware of fine grained policies, so you may get inaccurate results.
Yes, that is true about the ADAC.
As for net accounts, GP Results, or any other GP related reporting, they have no clue about FGPP and never will.
At this point, the biggest issue with FGPP is they don’t provide any additional controls over using Group Policy, which has proven to provide weak passwords that are easy to crack.
I think you got images 1 and 3 mixed up. Good article though!
Thanks, Diego! The images have been updated.
Can you have GPO and FGPPs running in the same domain at the same time. Meaning who ever does not get FGPR applied gets GPO?
If there is a user that does not receive a FGPP through group membership, the password policy deployed through the GPO linked to the domain will be applied to that user.
Derek, you’ve got the figures mixed up 😉