Most of the enterprises have their LAN network connected to a firewall, and from there to an edge router which connects to the WAN cloud. In this topology, network administrators also employ NAT for traffic redirection and other purposes.
Though the primary design of NAT was as a mechanism to conserve IP V4 Addresses, it also has evolved as a security mechanism for the network. NAT gives network administrators greater control to filter traffic to the network and and restrict access to various resources within the network.
Some of the advantages in using NAT in IP networks are:
1. It helps to extenuate the depletion of IP V4 address space
2. Networks can use private address space internally and still connect to Internet using a single public IP address
3. Increased security by hiding internal network topology
In this blog we will discuss briefly about NAT and which type of NAT is best suitable to allow NetFlow packets to reach the NetFlow Analyzer server. There are various ways for configuring NAT. Some of them are:
Static NAT:
Static NAT provides one-to-one mapping between an unregistered IP address and a registered IP Address. This is particularly useful in cases when a host or device needs to be accessible from the outside public Internet.
Dynamic NAT:
Dynamic NAT is used when a pool of public IP Address provided the ISP is shared by an entire private IP subnet. Here, the internal private IP addresses is translated to a public addresses from the range of public addresses, when the private host initiates the connection.
Overloading or Port Address translation:
This is the most frequently used type of NAT in IP networks. A variation of Dynamic NAT, also known as Network Address Port Translation (NAPT), multiple private IP addresses are mapped to a single registered IP address with the connections differentiated based on TCP/UDP port numbers.
Overlapping:
In Overlapping, the IP addresses used on the internal network are registered IP addresses utilized on another network. To avoid conflicts, a NAT table is built to translate the internal addresses to a unique IP address and vice versa.
For NetFlow packets to reach NetFlow Analyzer:
Among the various NAT mechanisms, overloading (PAT) and static NAT are the best suitable for methods to forward NetFlow packets from the outside to a server within the network.
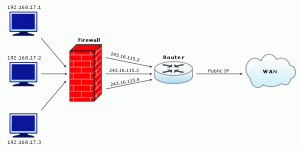
Static NAT forwards packets received on a public IP Address to its mapped inside address. Or simply put, you can have devices from external sites sending traffic to the mapped public IP Address of the NetFlow Analyzer server. Static NAT is not widely preferred due to the cost factors and etc involved with having a dedicated public IP address mapped to the NetFlow Analyzer server’s private IP Address.
As in the image, the private IP Address 192.168.17.1 is always translated to the public IP Address 243.16.115.2, and so hosts from outside will be able to access the internal host using the IP Address 243.16.115.2. For this, the configuration for this can be done as below:
Firewall(config)# interface ethernet 0
Firewall(config-if )# ip address 192.168.17.1 255.255.255.0
Firewall(config-if )# ip nat inside
Firewall(config)# interface serial 0
Firewall(config-if )# ip address 100.100.100.1 255.255.255.252
Firewall(config-if )# ip nat outside
Firewall(config)# ip nat inside source static 192.168.17.1 243.16.115.2
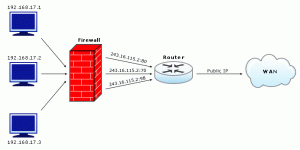
With NAT Overloading or PAT, inbound traffic to a public IP address is redirected to the internal addresses based on the port number. For the following image, all traffic to 243.16.115.2 on port 80 is translated to the private IP Address 192.168.17.1
The configuration for PAT for the example can be done as below:
Firewall(config)# interface ethernet 0
Firewall(config-if )# ip address 192.168.17.1 255.255.255.0
Firewall(config-if )# ip nat inside
Firewall(config)# interface serial 0
Firewall(config-if )# ip address 243.16.115.2 255.255.255.0
Firewall(config-if )# ip nat outside
Firewall(config)# ip nat pool overloadpool 243.16.115.2 243.16.115.2 prefix-length 24
Firewall(config)# ip nat inside source list 1 pool overloadpool overload
Firewall(config)# access-list 1 permit 192.168.17.0 0.0.0.255
Port Redirection:
Port Redirection is a feature available in many devices to allow outside users to connect to a particular IP address/port and have the device redirect the traffic to the appropriate inside server/port. This is suitable when you need to sent traffic from external devices to specific internal IP Address on a particular port.
As an example, say you need traffic from external sites reaching the public IP 243.16.115.2 on UDP port 9996 to be forwarded to the internal host having the IP Address 192.168.17.2. The configuration can be done as below:
Firewall(config)# interface ethernet 0
Firewall(config-if )# ip address 192.168.17.2 255.255.255.0
Firewall(config-if )# ip nat inside
Firewall(config)# interface serial 0
Firewall(config-if )# ip address 243.16.115.2 255.255.255.252
Firewall(config-if )# ip nat outside
Firewall(config)# ip nat inside source static udp 192.168.17.2 9996 243.16.115.2 9996
Hope these suggestions will make the configuration of your network to receive NetFlow packets a more easier job. Please do let us know if you have any suggestions on the configurations or any queries regarding NetFlow and NetFlow Analyzer.
Regards,
Don Thomas Jacob

[…] » NAT configuration for NetFlow :: NetFlow Analyzer Blogs … […]