A recap of the events that led to the fall of the organization:
 The breach became public knowledge only on Aug 29, 2011 when a rogue certificate generated for google.com was presented to a number of internet users in Iran. Users were presented with fake certificates, but the browsers assumed them as ‘secure, trusted connection’- just as they would treat the genuine certificates signed by the CAs.
The breach became public knowledge only on Aug 29, 2011 when a rogue certificate generated for google.com was presented to a number of internet users in Iran. Users were presented with fake certificates, but the browsers assumed them as ‘secure, trusted connection’- just as they would treat the genuine certificates signed by the CAs.- The successful hack implies that the current network setup and / or procedures at DigiNotar are not sufficiently secure to prevent this kind of attack.
- The most critical servers contain malicious software that can normally be detected by anti-virus software. The separation of critical components was not functioning or was not in place. We have strong indications that the CA-servers, although physically very securely placed in a tempest proof environment, were accessible over the network from the management LAN.
- The network has been severely breached. All CA servers were members of one Windows domain, which made it possible to access them all using one obtained user/password combination. The password was not very strong and could easily be brute-forced.
- The software installed on the public web servers was outdated and not patched.
- No antivirus protection was present on the investigated servers.
- An intrusion prevention system is operational. It is not clear at the moment why it didn’t block some of the outside web server attacks. No secure central network logging is in place.
In this case, an effective vulnerability scanner could have easily detected vulnerabilities; enforcement of standard password management practices could have helped automatically randomize passwords and combat the compromise of the password of the domain in which the CA servers where present; an efficient patch management software could have helped keep the software on web servers up-to-date; real-time monitoring of security events and analysis of system logs could have helped identify security breaches.
The growing list of cyber-criminal activities across the globe have assumed such grave proportions that all enterprises – big and small, are exposed to security breaches and identity thefts of various kinds. Though in reality, it is not possible to prevent all types of security incidents, the ones that happen due to lack of mandatory security measures are indeed preventable.
Combating the sophisticated cyber threats mandates a multi-pronged strategy – deploying security devices, enforcing security policies, controlling access to resources, monitoring events, analyzing logs, detecting vulnerabilities, managing patches, tracking changes, ensuring compliance, monitoring traffic and a host of other activities.
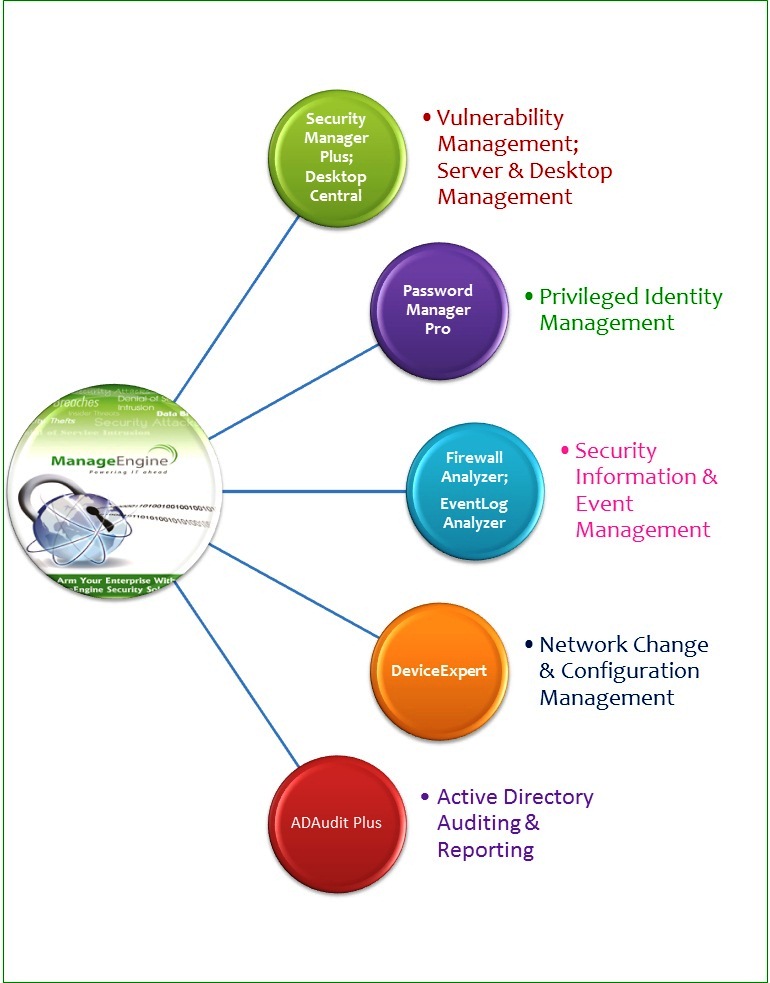
ManageEngine has a range of affordable Enterprise Security Management Software Solutions that help you build a secure fortress enabling you stay secure, ensure business continuity and enhance productivity.
ManageEngine Security Solutions aid in:
- Network Security Management
- Network Security Audits
- User Account & Rights Management
- Privileged Identity and Access Management
- Regulatory Compliance
- Internal Controls
With cyber threats looming large, taking preventive action is the need of the hour. Use ManageEngine and Stay Secure!
Bala
ManageEngine Password Manager Pro
Quick Video | Free Trial Download | White Papers | Success Stories