Over the past 14 years, I have been around the world helping admins, auditors, and security professionals understand how the domain password policy works in Active Directory. The default behavior has not changed in those 14 years, so you can imagine how many people I have helped, not to mention how many times I have spoken about it.
So why mention it here? Well, I still find admins and auditors not understanding how the domain password policy works, so let me explain it below.
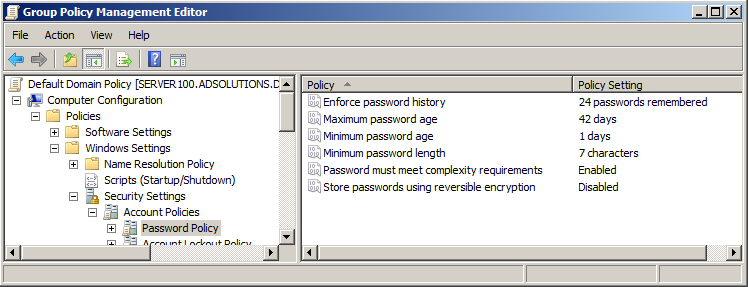
By default in every installation of Active Directory, the Default Domain Policy establishes the domain password policy (for all users configured and stored in Active Directory, that is). Figure 1 illustrates what those configurations look like and where you can find them in the Default Domain Policy.
Figure 1. Default Domain Policy password policy.
The way the password policy works is that this GPO and the settings contained within this GPO configure the domain controllers (DCs) and the Active Directory databases located on them. It is the responsibility of the DCs and databases located on them to filter each and every password that is attempted to be written to the database, to ensure the password meets the password policy settings.
Note: By using Group Policy, there can only be one password policy for the domain users. Linking and configuring a GPO to an OU will not configure the password policy differently for the users in that OU. Password policy settings affect computers (see Figure 1) not user accounts!
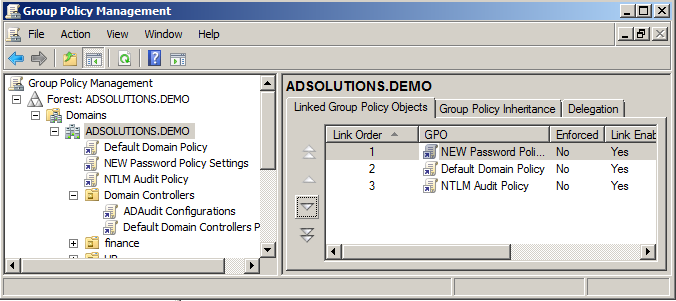
What you can do is create a new GPO, link it to the domain level, and give it higher precedence than the Default Domain Policy. The settings in this new GPO (for example, you set the minimum password length) will override the settings in the Default Domain Policy due to the higher precedence. You set precedence in the Group Policy Management tool, which you can see in Figure 2.
Figure 2. Each GPO linked to the domain has a precedence, compared to the other GPOs.
If you want to have multiple password policies in the same domain, either you need to buy a third- party product or you can use the fine-grained password policies. Fine-grained password policies are a Microsoft technology to control password policies but don’t use Group Policy as the deployment mechanism.
To audit the effective domain password policy, you obviously can not just look at the Default Domain Policy because another GPO linked to the domain might have different password policy settings contained in it that will override the Default Domain Policy. So how do you correctly verify the effective password policy for your domain users stored on domain controllers?
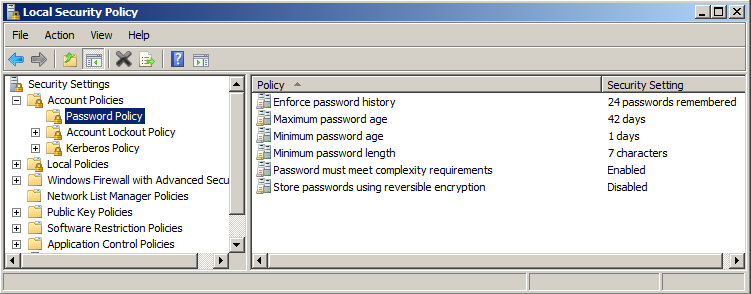
The answer is simple and a built-in tool! The tool is secpol.msc and you can run this on any domain controller from the command prompt or the Start button | Search programs and files box. Figure 3 illustrates what the result would look like.
Figure 3. Secpol.msc displays the actual settings for the computer.
By using the secpol.msc tool, you can verify with 100% confidence what the current password policy settings are for your domain users.




Thank you for your post! It just solved our problem over where I work. I just want you to know that you are appreciated. 🙂 Hope you have a great day!
KPMG are one such auditor. Their report impacted a multi-million dollar business takeover. Sloppy.
…”I still find admins and auditors not understanding how the domain password policy works”
Because it is SOOOOOOO uselessly complicated.