Nowadays, with growing infrastructure and increased complexity, it’s near impossible to manage configuration changes manually. Let’s look at an example scenario. Imagine you are the network admin of a large enterprise network handling 5,000 devices. You cannot remember the configuration of every device, especially if the network environment also supports multi-vendor devices.
Therefore, if a change is made to any one of the device’s configuration among the 5,000 and it leads to a network disaster, it’s very time-consuming to go through every line of every configuration to find the root cause. There is also a higher probability of missing errors when devices are analyzed manually.
These hectic and time-consuming tasks can be greatly minimized by using a network automation tool containing change management features. But that’s not all; there are certain best practices that need to be followed for the configuration change management process to vastly enhance the efficiency of a network.
Configuration change management is the process of controlling the entire life cycle of changes made in a network, including operational, strategic, or tactical changes. While no change management process provides 100% efficiency, it can help to reduce or minimize the risks of unauthorized or unnecessary changes, which are the leading causes of network disasters like downtime.
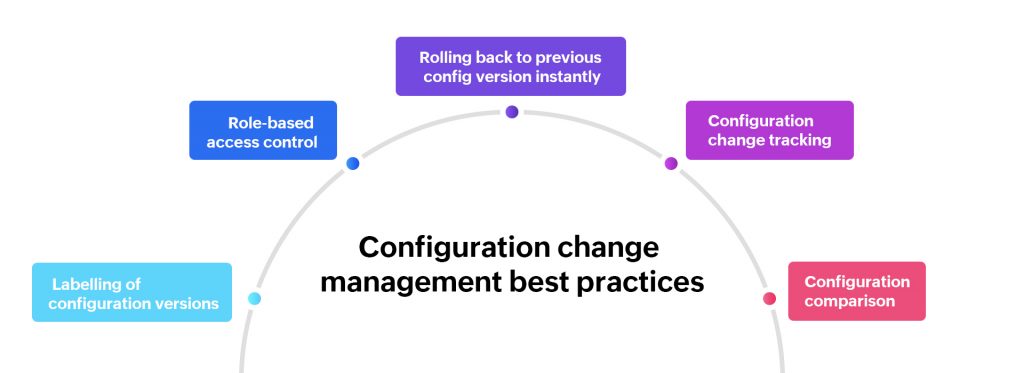
Now, let’s look at the top five best practices that should be followed for a better configuration change management process:
-
Configuration change tracking
-
Role-based access control
-
Configuration comparison
-
Labelling of configuration versions
5. Rolling back to a previous configuration version immediately
1. Configuration change tracking
All configuration changes must be monitored constantly in real time so they are managed efficiently without any human errors, which can lead to unimaginable losses to businesses. Also, manually tracking every device is near impossible in a large network environment.
With a real-time change notification feature, admins can know instantly the what, when, and who of configuration changes in real time. This helps admins be aware of what is happening in and around their networks, and instantly apply a solution depending on the changes made.
2. Role-based access control
Admins need to play the authority in a large enterprise network to keep everything under control. If the same authority is provided to everyone in a network, it will lead to disasters like unauthorized or unnecessary configuration changes.
With a dedicated role-based access control feature, admins can choose to accept or reject changes made by operators, and they can also provide specific devices for operators to handle, minimizing the risk of unnecessary changes. Unauthorized changes can be minimized by providing specific roles, such as operator or admin. Since all changes go through an approval process first, this is a vital best practice that needs to be followed to eradicate changes made unnecessarily.
3. Configuration comparison
Whenever there is a network mishap due to the addition or modification of a configuration file, admins have to search every line of each configuration to find the exact root cause. This means management overhead for admins is exorbitant.
With a side-by-side configuration comparison, admins can compare configurations or versions of devices to know exactly which lines have been changed or added in a device’s configuration. Admins can also compare the unstable network configuration with the stable configuration after downtime and find the issue immediately.
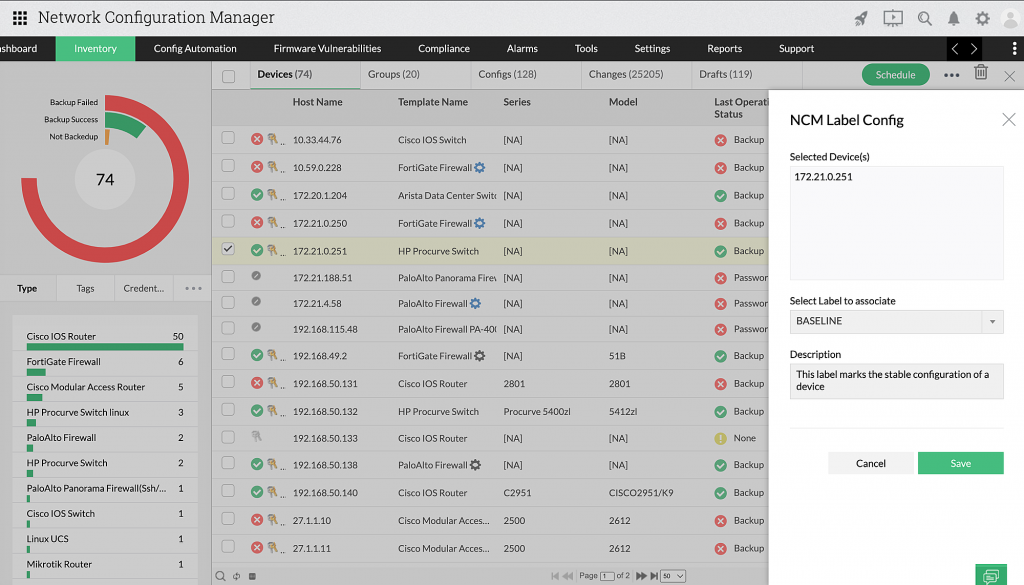
4. Labelling of configuration versions
Labelling versions is an important best practice because it makes it straightforward for admins to identify which is the latest configuration version and which is the baseline configuration version.
Labelling is mainly useful in large enterprise networks where there are a lot of changes made to a configuration file at a quick rate. For example, say a device’s configuration was changed or modified 46 times. The admins cannot remember manually which is the 46th version and which is the 32nd version. Instead, they can label them as versions one through 46; now, if the admin requires version 45 immediately during downtime, they can retrieve the version easily and use it.
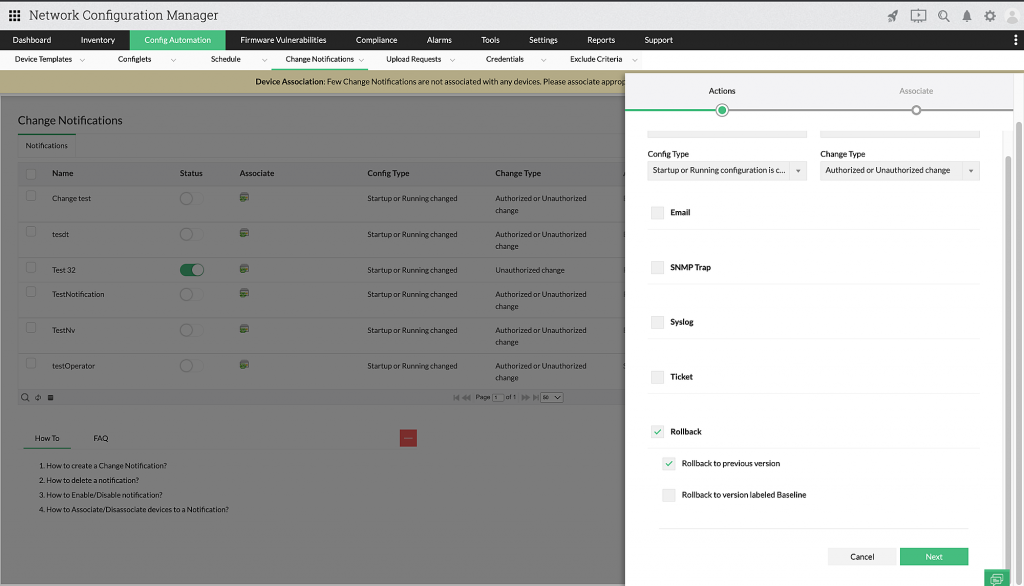
5. Rolling back to a previous configuration version immediately
Network efficiency, like every minute of network uptime, is critical or even vital for certain large-scale enterprise networks. During downtime, enterprises experience huge losses in terms of costs and revenue, and their reputations can also be hit hard.
How can this be avoided? Admins can use a rollback feature to roll back to the previous stable or baseline version (selected by the user) as soon as an unnecessary or unauthorized change is made, eventually saving precious minutes and the reputation of the enterprise.
ManageEngine Network Configuration Manager: The all-in-one configuration change management solution
ManageEngine Network Configuration Manager is a network configuration and change management, multi-vendor-supporting network automation solution. This solution is specially crafted to ease the workload of admins in a network environment.
Some of the features of Network Configuration Manager include the following:
1. Automated configuration backups
2. Configuration change management
3. Automation with Configlets (script templates)
4. Compliance management
5. Firmware vulnerability management
Now, let‘s look at configuration change management in Network Configuration Manager, and how it provides all the best practices with built-in features.
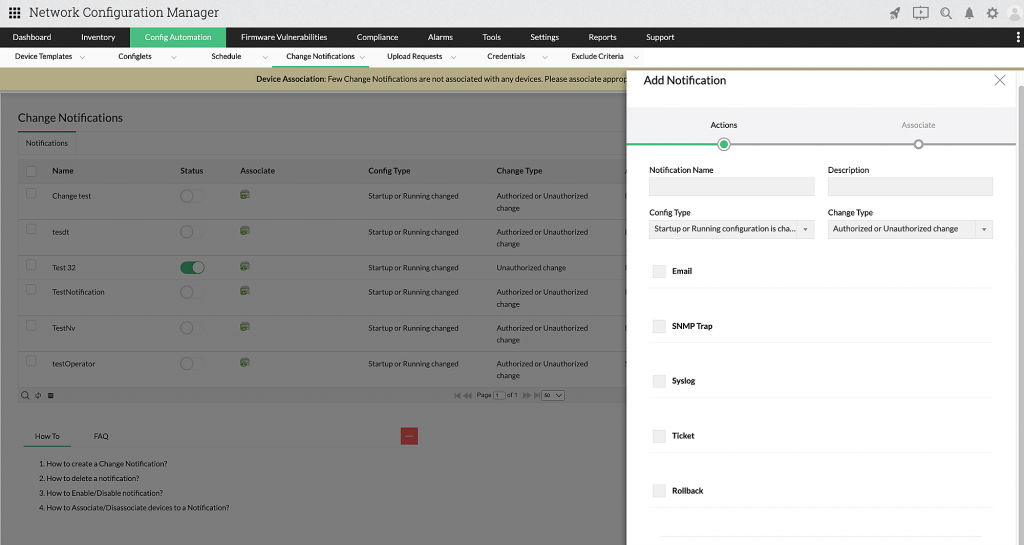
1. Configuration change tracking
Network Configuration Manager provides real-time change notifications, which support notifications either via email, SNMP traps, syslogs, or tickets. The user can choose any one of the options and immediately be notified whenever a change is made in the network. With this feature, admins can keep track of the who, what, and when of configuration changes.
2. Role-based access control
Network Configuration Manager provides the option of role-based access control, where admins can create or add new users and assign them specific scopes and devices. Only the devices assigned will be accessible by the newly added users. If the scope is selected as “Operator,” then only operator privileges are given. If this operator makes any minute change to the configuration of the devices assigned to them, the corresponding admins will immediately receive a notification. The admin can then choose to accept or reject the change.
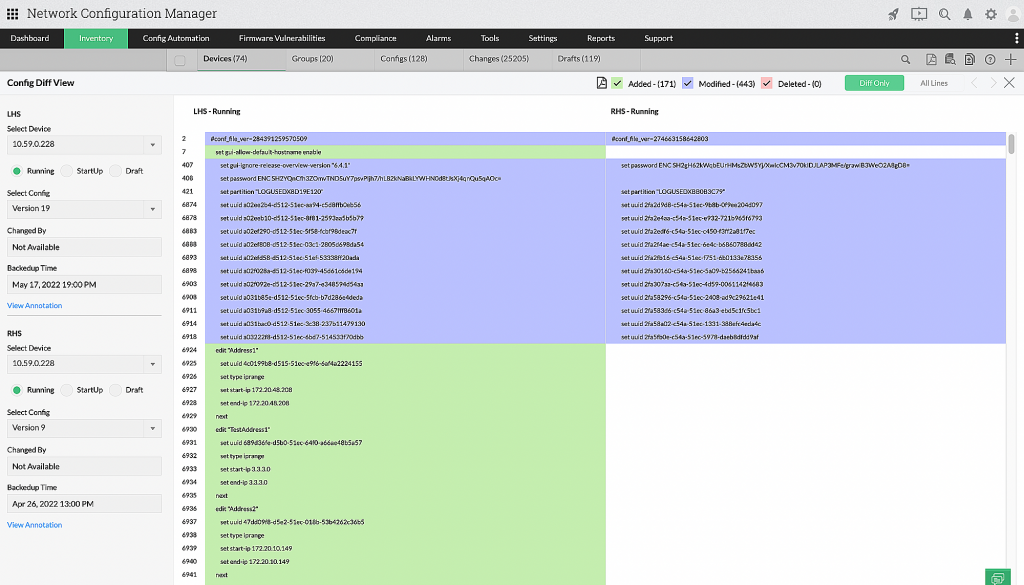
3. Configuration comparison
Network Configuration Manager has a unique comparison feature called Diff View. With Diff View, admins can compare two configurations of the same device or two configurations of two different devices side by side. The differences are color-coded depending on the changes made for better readability; for example, newly added lines are shown in green, modified lines are in purple, and deleted lines are in pink.
4. Labelling of configuration versions
With Network Configuration Manager, admins can assign labels to configurations according to their needs, and upload those configurations easily as well. With this, admins can quickly upload stable or baseline versions during sudden downtime.
5. Rolling back to a previous configuration version immediately
With Network Configuration Manager’s rollback feature, admins can immediately roll back to the previous version or baseline version (whichever is chosen) whenever an unnecessary change is detected. Network Configuration Manager nullifies the change and rolls back to the selected previous version.
Download Network Configuration Manager now, and efficiently manage changes to your network environment.
If you are interested in the product and want to learn more, you can apply for a free online demo conducted by our experts.
Confused about the right price for your enterprise? Get a personalized price quote.

