In HBO’s hit seriesô Game of Thrones,ô theô Sevenô Kingdomsô had the Wall to keep outô Whiteô Walkers, and for many generations, it did exactly that.ô But even the strongest fortifications can fall flat if improperly managed; like the Wall along theô border of the Seven Kingdoms,ô the true strength comes from those defending it.
Similarly,ô yourô firewall is theô first line of defense againstô cyberô attacks. With a stable set ofô rulesô or policies in place,ô you can keepô your companyô safeô from hackers.ô But keeping track ofô firewall security policies is a great challengeô in itself.ô Evenô small organizationsô canô have hundreds of rules to manage, whileô larger onesô mayô have thousands.ô Many of these rulesô date back more thanô five to ten years, and often there is a lack of continuity in definingô new rules as mostô rules are inherited fromô their predecessors. This mismanagement of rules severely affectsô firewall performance, leaving your network vulnerable to security breaches.
Cyberô attacks areô imminent.ô Are your firewall rules optimized to defendô against them?
The targeted attack sectorô continues to expand,ô including a 600 percent increase in IoT attacks during 2017.ô This same year,ô cryptojacking exploded by 8,500 percent.ô Meanwhile,ô ransomwareô hasô shiftedô its focusô fromô attempting to elicit a fewô higher ransoms from largerô companies toô instead collecting many smaller ransom amounts from a huge number of small companies.ô Gartner predicts that 99 percent ofô exploitedô vulnerabilities will continue to be ones known by security and IT professionals for at least one year.ô Gartner concludes that the best and cheapest way to mitigate cyber attacks caused by known vulnerabilities is by removing them altogether through regular patching.
Given these troubling network security trends, your firewall rules and policies need to be spot on. Policies should also be periodically updated if you want to stay ahead of today’s cyber criminals. To help you detect and fix the vulnerabilities in your firewall policies, here are a few firewall rule best practices you should apply in your IT department.
Removeô unused rules: As years go by and new policies are defined by different security admins, the number of rules tend toô pile up.ô Cleaning up unused rulesô on a regular basisô helps avoid clogging upô your firewall’s processor.
Removeô rule anomalies: As new rules are defined without analyzing the old ones, there is a good chanceô rulesô will become redundant or contradict each other. These anomaliesô can negatively affectô your firewall’s performance,ô soô it’s important toô periodically analyze and remove these anomalies.
Optimizeô policies:ô Placing theô most used rules on top andô moving the lesser-used rules to the bottom helps improve the processing capacity ofô your firewall. This is anô activityô that should be performed periodically,ô as different types of rules are used at different times.
Restrictô lax rules: Permissive rulesô give users more freedom,ô which can translate into giving usersô accessô toô moreô resources than required to perform business-related functions. This leads to two types of problems:
-
Under or overutilizedô network bandwidth.
-
Moreô exposure toô potentially malicious sites.
ô Avoid these issues byô restricting over permissive rules.
Setô ruleô alerts: Setting alerts when certain rules are triggered is a good way to identify the reason and cause ofô aô security attack.ô This not only helps youô identify suspicious IPs, but also helps identify the internal userô trying to access the IP.
These best practices helpô improve the performance ofô your firewall, butô you know what makes optimizing your firewall policies even easier? Introducing Firewall Analyzer, our toolô that can crunchô theô numbers and churn out suggestions for efficient performance ofô your firewall.
Firewall Analyzer uses secure protocols such a Telnet, SSH, and SCP to retrieveô rule information from your security devices and provide an array of reports and insights on yourô firewall policies.
With theô Firewall Analyzerô Ruleô Management module you can now get a complete drill down on:
1. Firewall rules
Get a detailed report onô all denied, allowed, inbound, outbound, and inactive rules.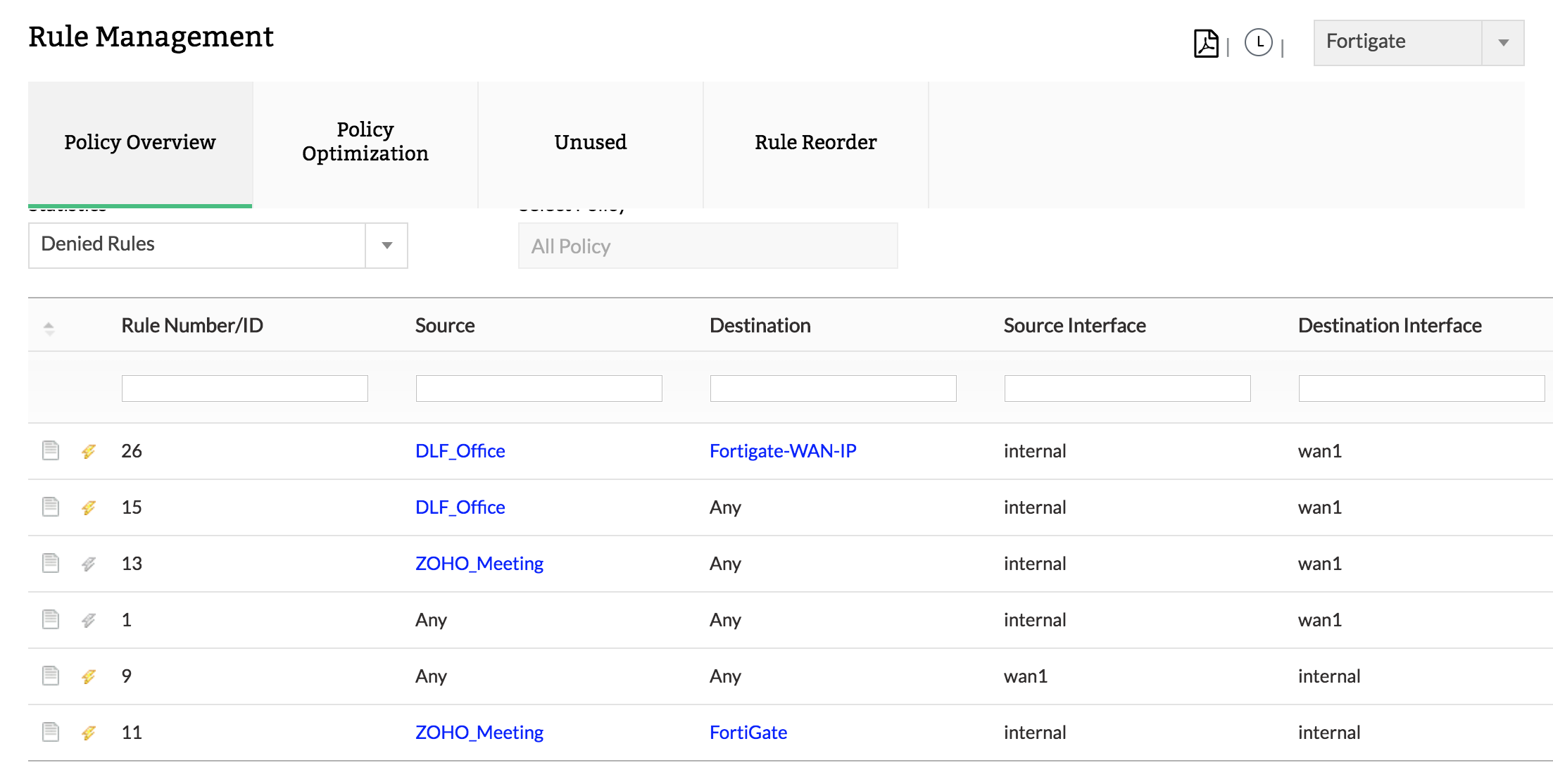
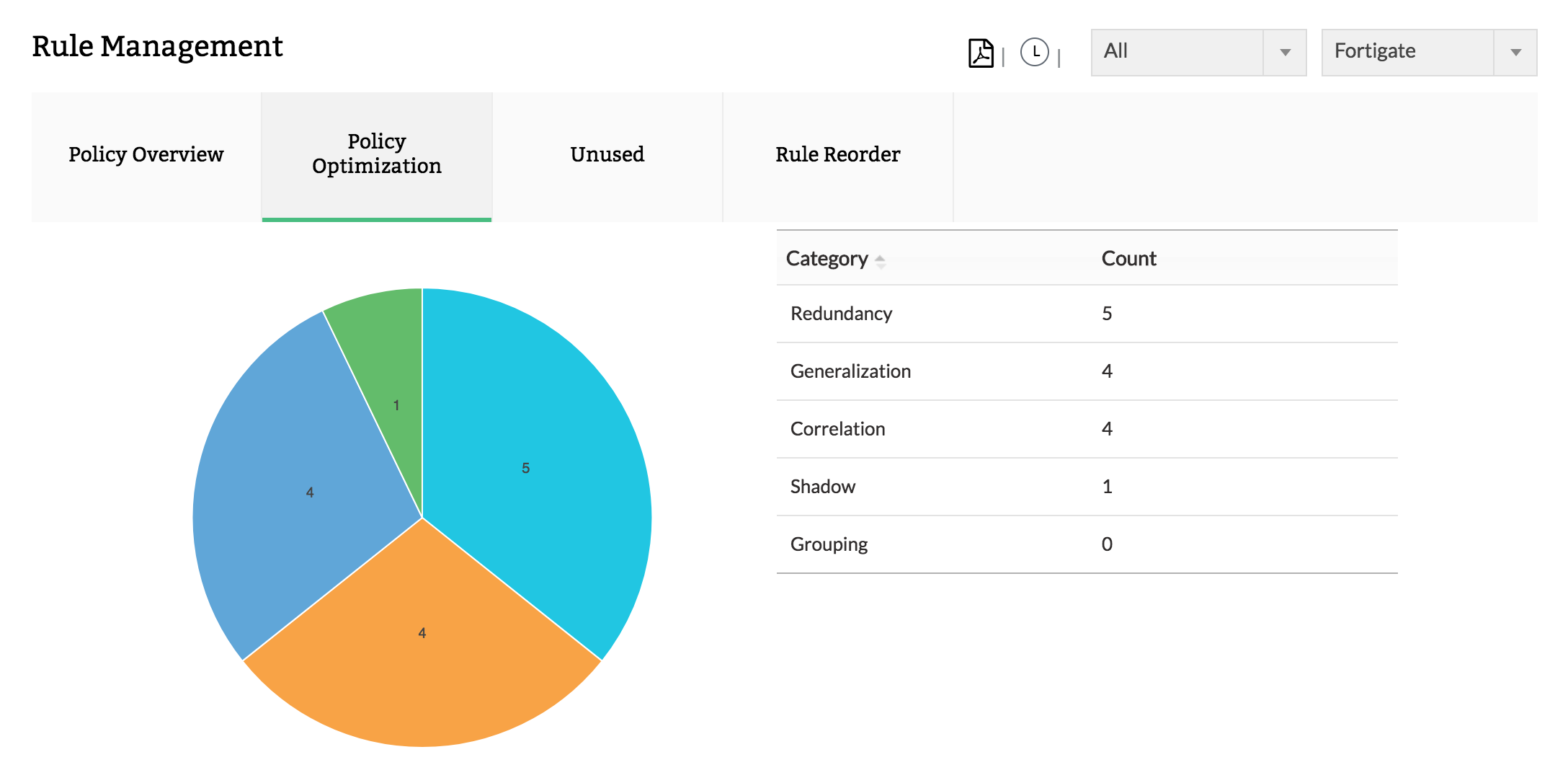
2.ô Rule anomalies
Detect and record redundancy, generalization, correlation, shadow, and grouping anomalies in your firewall.
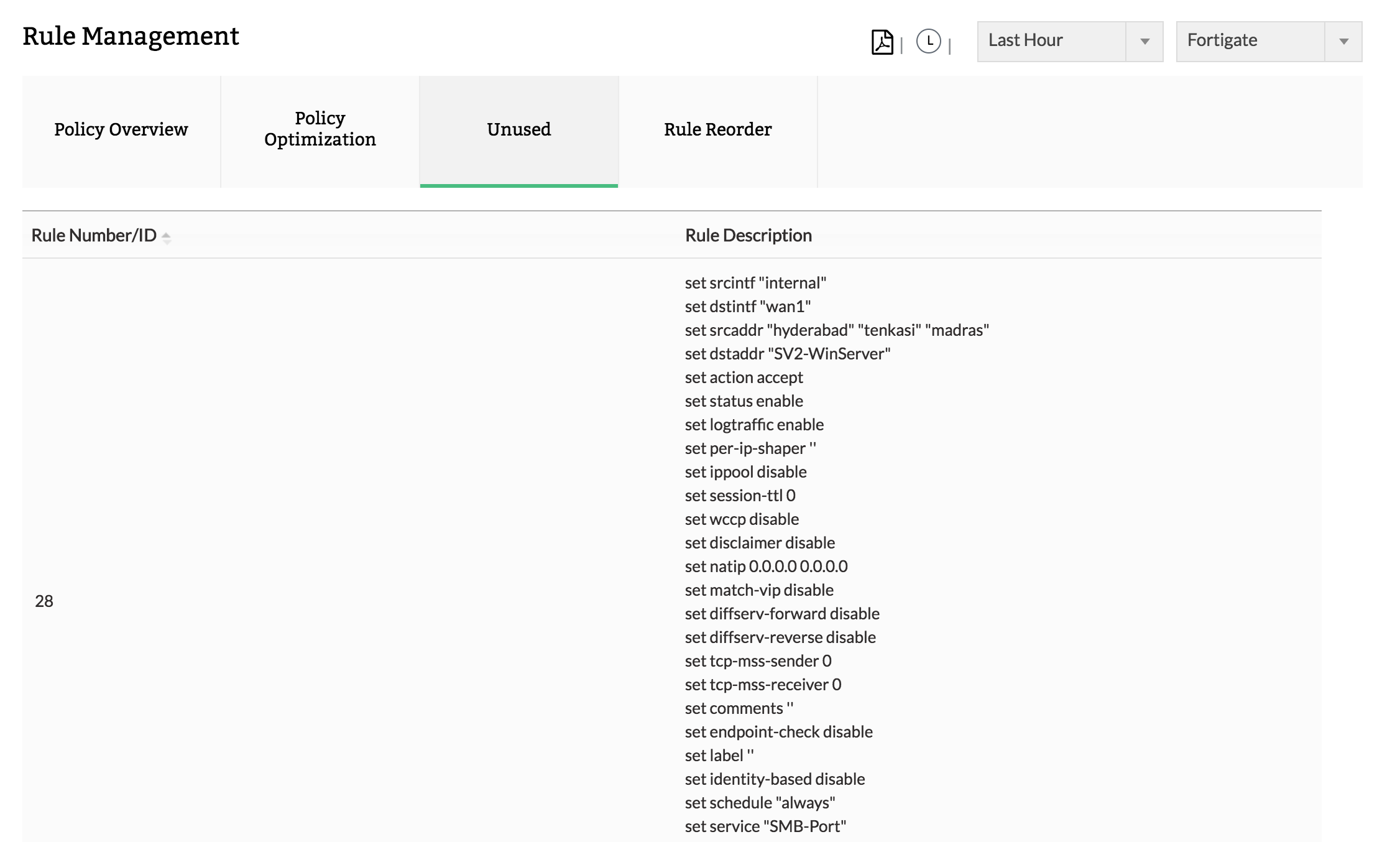
3. Unusedô rules
Get a complete list ofô all unused rules.
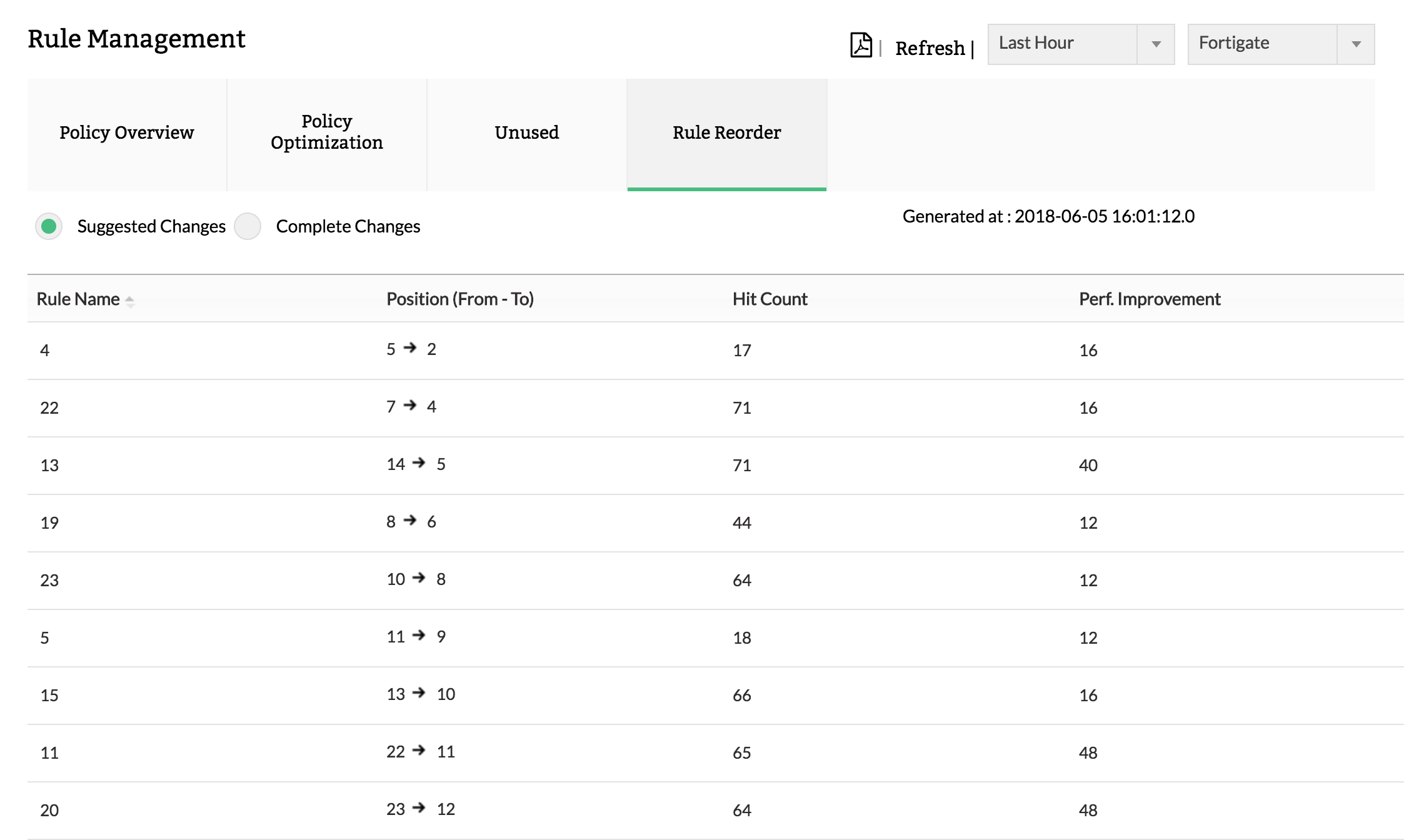
4. Policyô optimization
Gain insight on how to improve performance by changing the rule order.
Attacks are coming. Make sure you’re ready for them. Try outô aô free, 30-day trialô ofô Firewall Analyzer now, andô get on top of yourô firewall’s performance.