Email-based attacks can take many forms, and are typically deployed by cybercriminals in order to extort ransom or leak sensitive data. Just recently, a banking Trojan named Trickbot targeted Italy, a hotspot for COVID-19 cases, with email spam campaigns. While the email subject line is in line with the daily concerns and talks about spread of the virus, the attachment was actually a malicious script. Meanwhile, from April 6 to April 13, 2020, Google blocked more than 240 million COVID-related email spam messages each day. To top it all off, research states that a new phishing site launches every 20 seconds. That means every minute, three new phishing sites designed to target users pop up on the internet.
Corporate email continues to rule the world of business, but is also a high-level vulnerability. Emails have a lot of moving parts, can be accessed from unmanaged devices, and are are frequently an intruder’s gateway into organizations. Users are increasingly using work email addresses to sign up on third-party websites and for other personal reasons, which leads to the exposure of business email addresses on the internet. Before we get into the specifics of email-based attacks, there is a crucial component of any email attack chain that needs immediate unmasking: the discovery of email addresses.
Most phishing campaigns or business email compromise (BEC) attacks would be unsuccessful if cybercriminals had no access corporate email addresses. Unfortunately, considering the growing rate of employees and the increased use of applications, it’s inevitable that attackers will continue to gain access to these emails.
Let’s take a look at a few email discovery techniques:
- Using native tools built into the operating system:
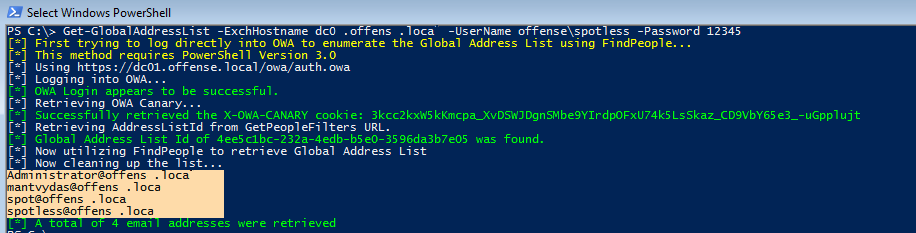
- Your standard users (those with no privileges) can use this free PowerShell script to:
- Discover user account names.
- Perform a password spray attack and compromise a victim with a mailbox.
- Use the victim account credentials to obtain the entire mailing list, or Global Address List (GAL), of an Exchange server.
- Your standard users (those with no privileges) can use this free PowerShell script to:
-
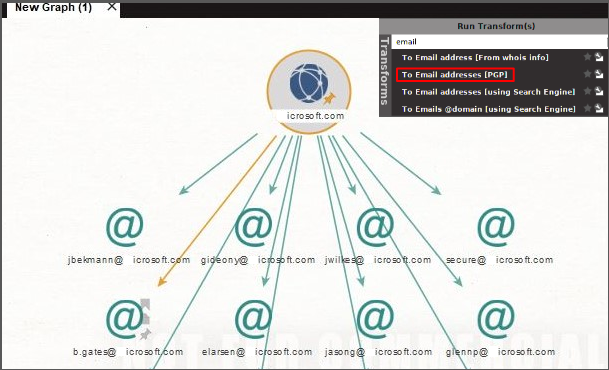
Identifying vulnerable emails with open-source tools:
- There are many open-source intelligence and forensic tools that can help identify email addresses. Just install the program, run an email check on a desired domain, and you’re good to go!
-
Discovering email addresses with online email hunter tools:
-
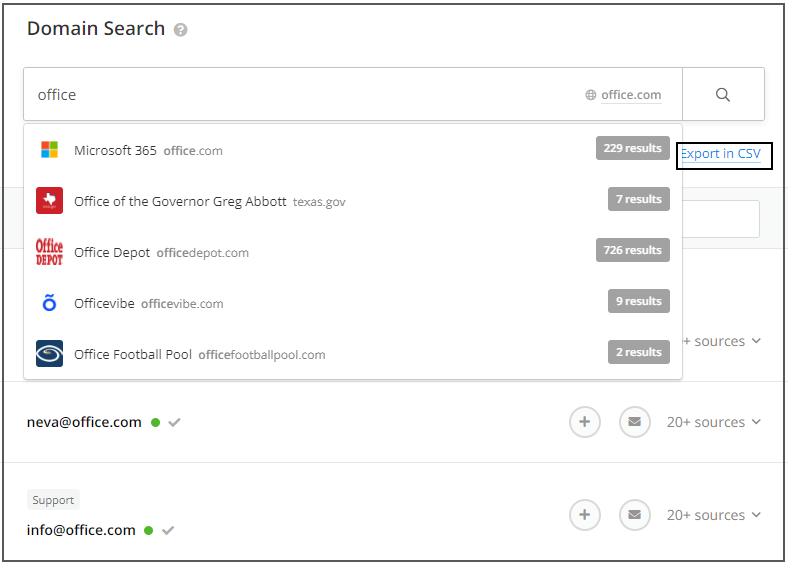
Email discovery may not always involve downloading third-party tools or scripts; the internet is a helpful aid, too!
- This free online tool can help guess domain names, email addresses of individuals along with their industry/field of work, and the list can even be exported!
-
-
Preying on weak naming formats:
-
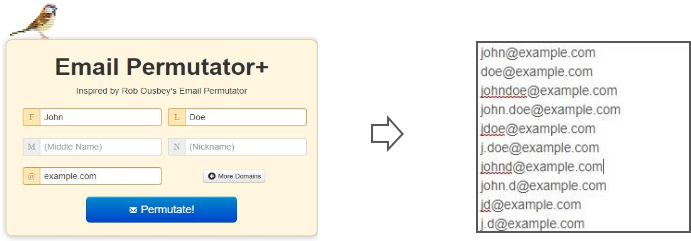
If your name is John Doe, it’s very likely that your email address is something like John.Doe@domain.com.
-
Surprised? Most attackers target email addresses based on common naming formats, like {firstname}.{lastname}.@example.com.
- And of course, there are tools that can permutate this information and obtain various email address combinations.
-
-
Using social engineering tactics to extract emails:
-
Have you ever disclosed your email address due to a call from your bank?
- Perhaps you submitted your email address in response to an official income tax email from the government? Think!
-
Attacking found addresses to access company sensitive data:
Now that the attacker has sufficient ammunition, a full-fledged security attack can be conducted. Here are a few examples:
-
A classic password spray on found email addresses:
-
All you need is a list of emails, a script, and a command line interface!
-
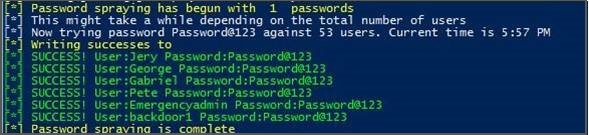
-
Obfuscating emails with spam:
- A high volume of commercialized emails are sent to the victim to obfuscate phishing attempts, or authentication confirmation emails (during a brute-force login attempt).
-
Spear phishing attack:
- Attackers spend a substantial amount of time studying the individual targeted for attack, then send an email impersonating someone well-known to the victim.
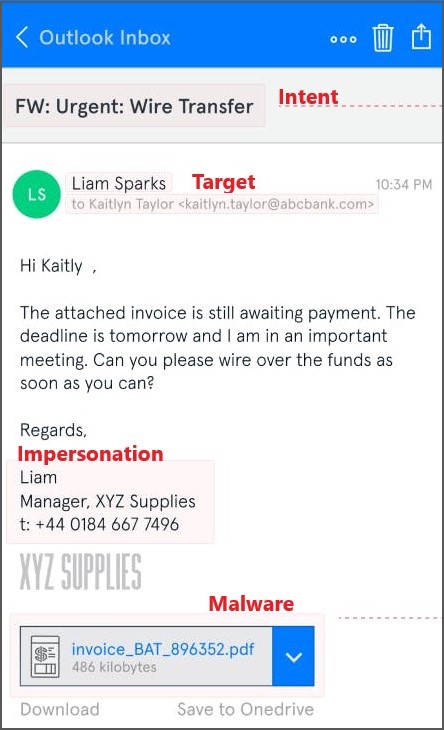
It could also be an email bomb attack, where an attacker subscribes a victim’s email address to multiple lists, causing a denial-of-service (DDOS) on the company mail server.
The risk of email-based attacks is high, especially now with most of the world working remotely over unsecure network connections.
So the next time your users download an attachment, be sure to check the source. Password protect confidential data sent over email. Watch out for users trying to run unknown scripts to discover emails or attempting to download malicious third-party tools.
Check out Log360, a comprehensive monitoring tool that can capture and alert on malicious scripts used for email discovery, and detect third-party tool downloads and malware via email attachments by tracking changes to the registry, files and folders, and new process additions.
With the present situation in mind, we’d like to offer a fully functional edition of our SIEM solution, Log360, at no cost to you until June 30, 2020. Check this link for more information.

