Fileless threats are on the rise. These threats occur when cybercriminals use pre-existing software in victims’ systems to carry out attacks, instead of using a malicious attachment or file. More often than not, a criminal’s favorite tool for a fileless attack is PowerShell.
PowerShell is a hacker-favorite
PowerShell is a pre-existing command line interface (CLI) used by system administrators to automate routine tasks and manage system configuration. It is mostly used for script execution-based, post-exploitation attacks.
Hackers use PowerShell because it’s,
-
Effortless to gain privileged access: Gaining access to a tool like PowerShell means gaining access to every single system in the network, since administrators use it to monitor and execute commands in all of them, including Active Directory.
-
A whitelisted tool: PowerShell displays a trusted digital signature as a whitelisted tool. This means it is easy to surpass firewalls or other anti-malware software.
-
Easy to execute: There are numerous free PowerShell scripts hackers can easily access online for free to execute an attack. PowerShell is also an open source software (since 2016) which means it can be used to carry out every part of an attack kill chain.
-
Compatible with different operating systems: PowerShell is supported by Linux and macOS systems along with Windows.
Hackers use frameworks to execute PowerShell attacks
Over time, pen testers have identified frameworks and tools used by criminals to execute PowerShell attacks. Some of them include:
- Empire
-
Nishang
-
Cobalt Strike
-
PowerSpolit
We’ll take a deeper look at Empire to understand how criminals can use a framework to execute an attack. Empire can be executed using three main components:
➤ a listener is a system that listens for an RDP connection
➤ a stager is a piece of code that can be used to execute malicious scripts in the victim’s system, using an agent
➤ an agent is a program that maintains the connection between the victim system and the listener
The attack is carried out using the following steps:
- The attacker downloads the Empire post-exploitation tool onto their system.
-
They set up a listener using the tool.
-
A launcher is created. A shell launcher helps replace the existing Windows 10 script with a custom shell script. This file is renamed to misguide the victim.
-
The victim downloads the malicious file from let’s say, a phishing website. They download it thinking it is a jpeg file but it is actually the launcher that connects the victim’s system with the listener.
-
Once the connection is established, the attacker looks for agents that can be used to execute malicious scripts.
-
If the agent found does not have higher privileges, the attacker proceeds to escalate them.
-
Once elevated privileges are obtained, the attacker can use these to execute various attacks. They could obtain password credentials using other post-exploitation tools like Mimikatz, for example.
Similar attacks can be executed using the other pen-testing tools and frameworks listed above. Cobalt Strike is a legitimate penetration testing tool whose cracked version has been used often to execute attacks.
Cybersecurity best practices to detect PowerShell attacks
Here are some security best practices you can implement in your organization to detect and curb PowerShell attacks:
- Code Signing: This means adding a digital certificate to an executable or script to track and avoid any tampering.
-
Just Enough Administration (JEA): In PowerShell, JEA helps limit the kind of administrative controls each user has, including privileged users.
-
Constrained language mode: Enabling this mode in PowerShell helps avoid certain scripts that can increase the vulnerability of systems to attacks.
-
Enable transcription, module, and script-block logging: Enabling logging will help track each PowerShell session, monitor executions of script and code, and record all information to aid analysis, including timestamps and metadata for each command.
Investing in a SIEM solution
Enabling logging is not enough. Continuous monitoring of logs is required to spot malicious scripts and detect possible PowerShell attacks. Investing in a SIEM solution and sending it the transcription, module and script block logs can help you track specific commands and executions that can indicate these attacks.
Here are some of the reports a security analyst can study to track possible indicators of PowerShell attacks with ManageEngine Log360, a MITRE ATT&CK-powered SIEM solution:
– Remote PowerShell session creation
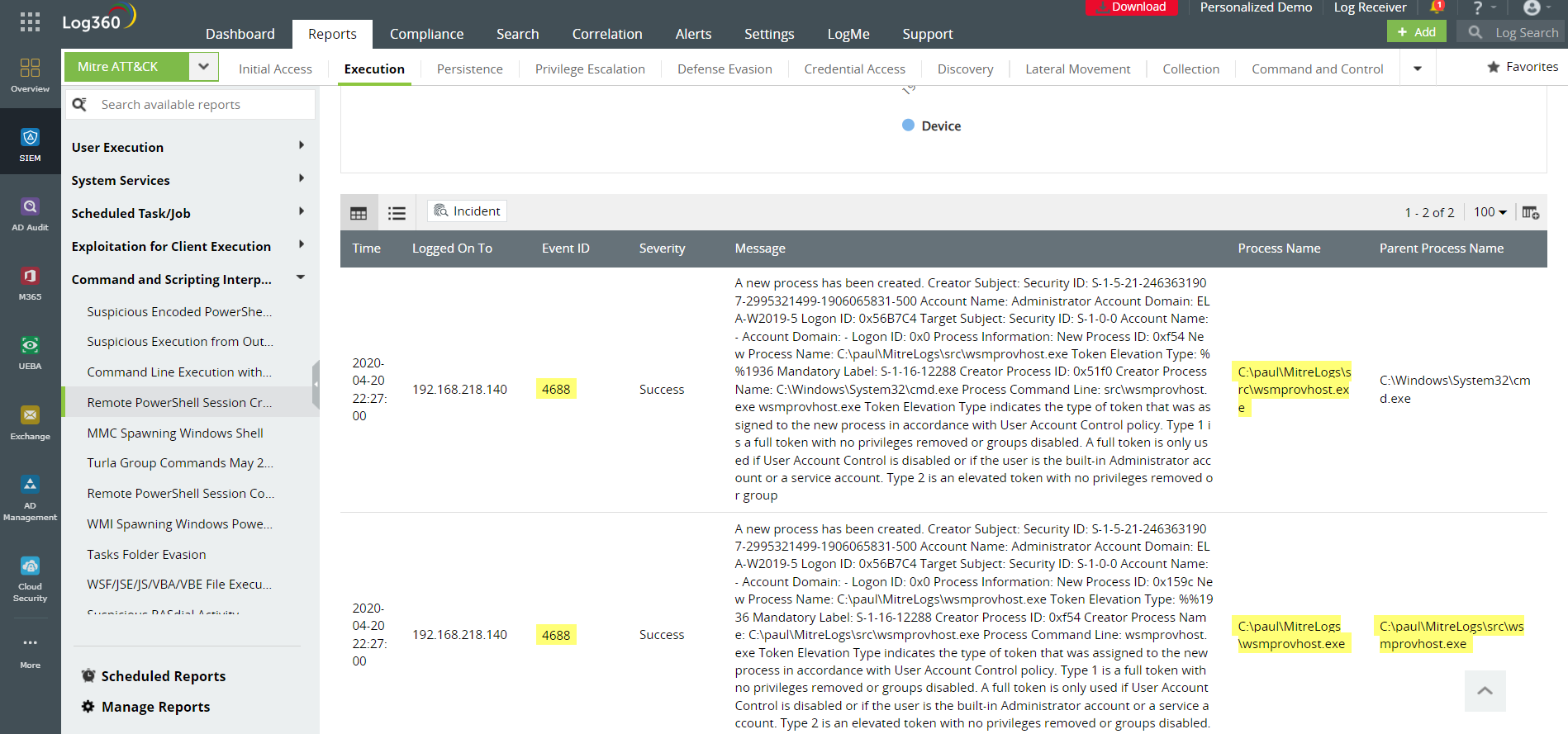
Figure 1: Whenever a suspicious remote PowerShell session is created (Windows Event ID 4688), Log360 records it as part of its MITRE ATT&CK-based reports.
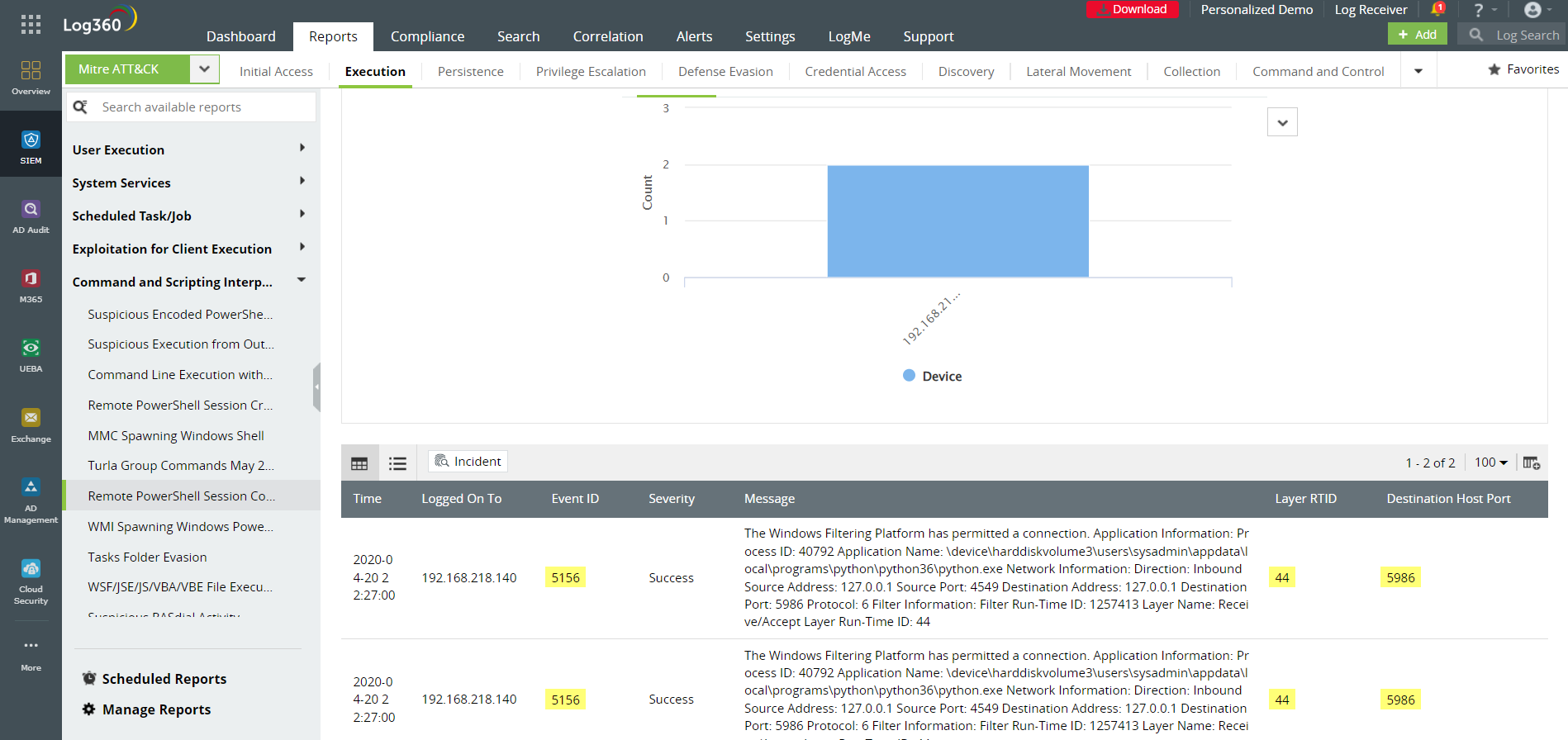
Figure 2: Log360 records any suspicious remote session connection allowed through WFP with Event ID 5156.
-WMI spawning Windows PowerShell
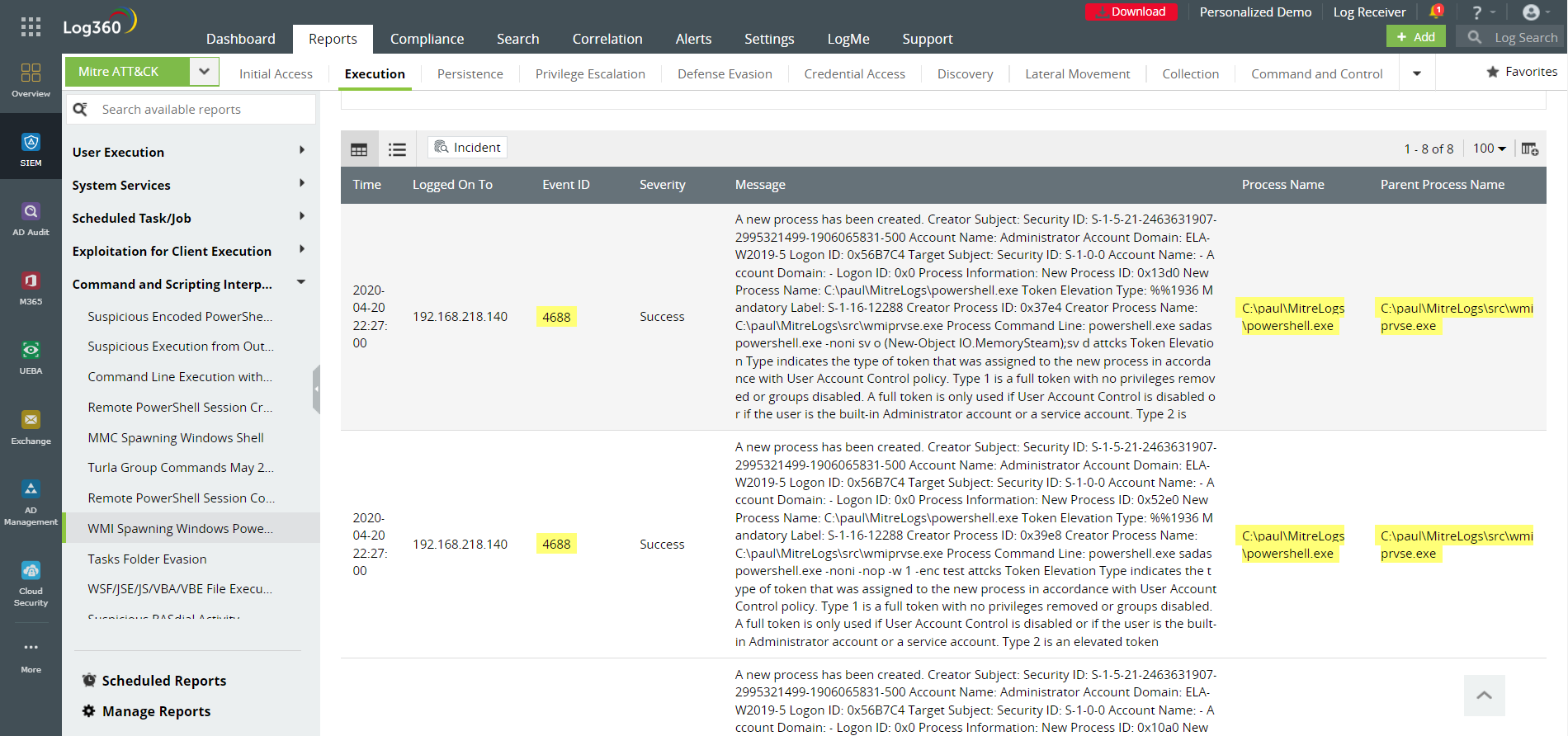
Figure 3: Attackers often use WMI to execute malicious PowerShell scripts. Log360 records such executions.
– PowerShell download file
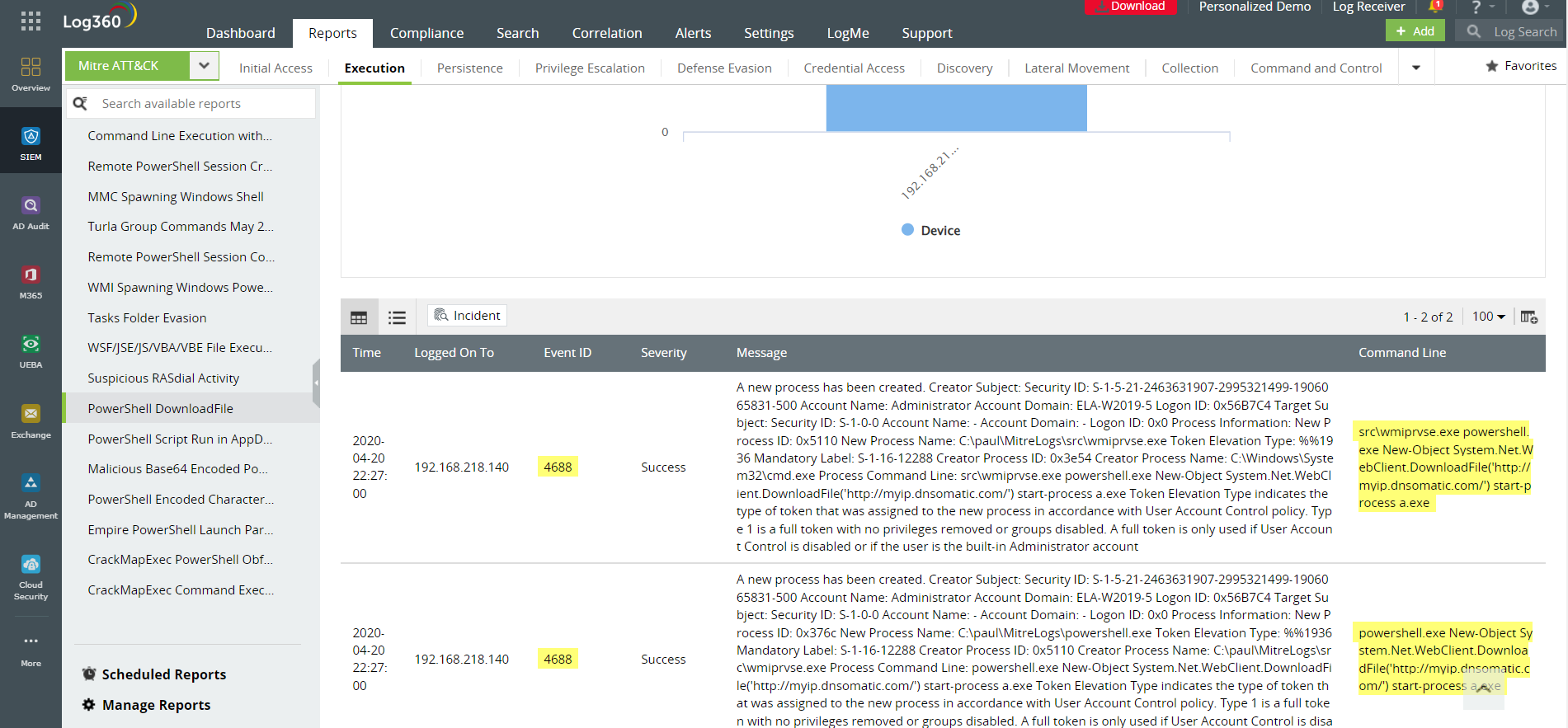
Figure 4: Log360 records executables or processes indicating possible malicious downloads.
– PowerShell script run in-app data
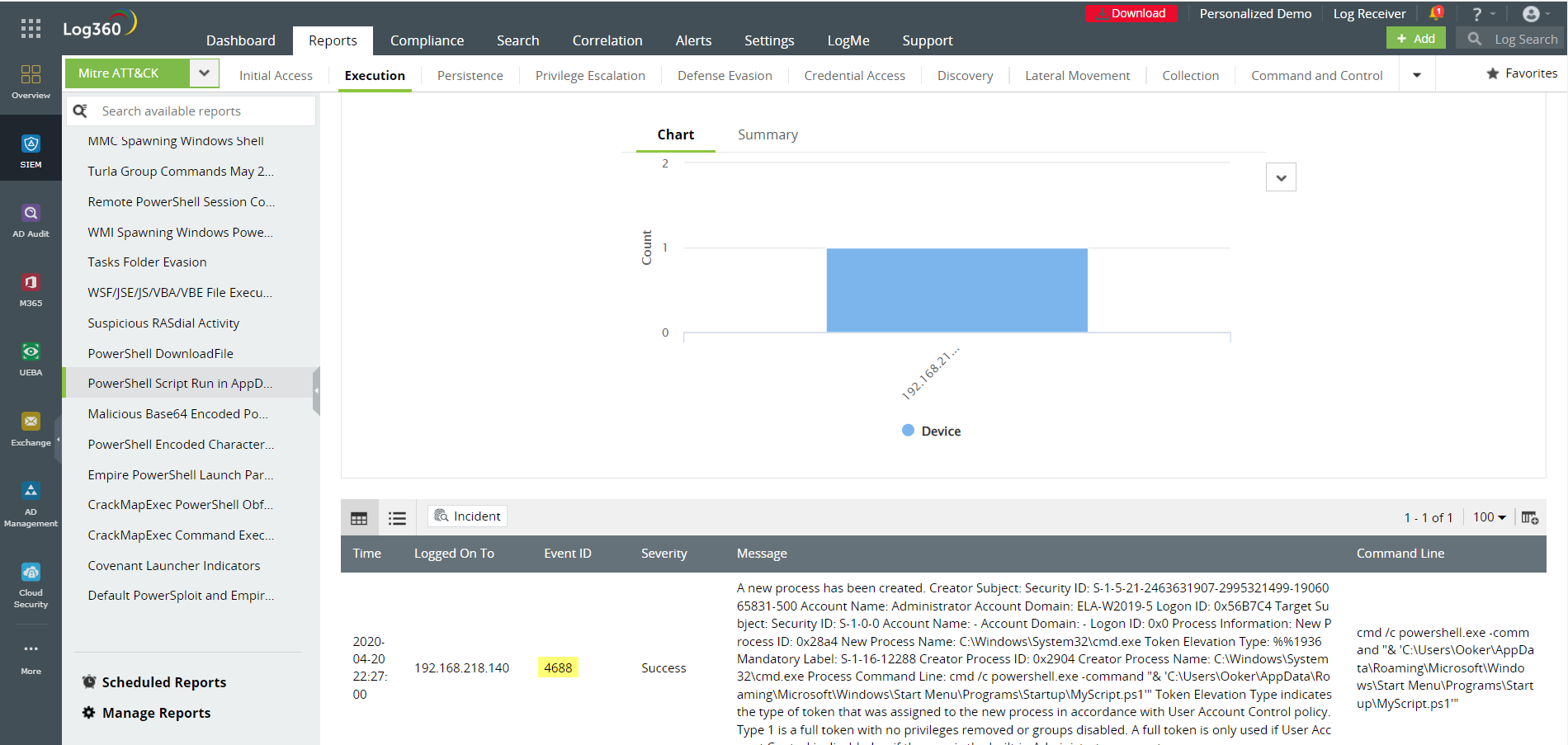
Figure 5: Malicious PowerShell script run in the hidden AppData directory could lead to changes in system applications. Log360 records possible suspicious commands that could indicate this in its reports.
– PowerShell encoded character syntax
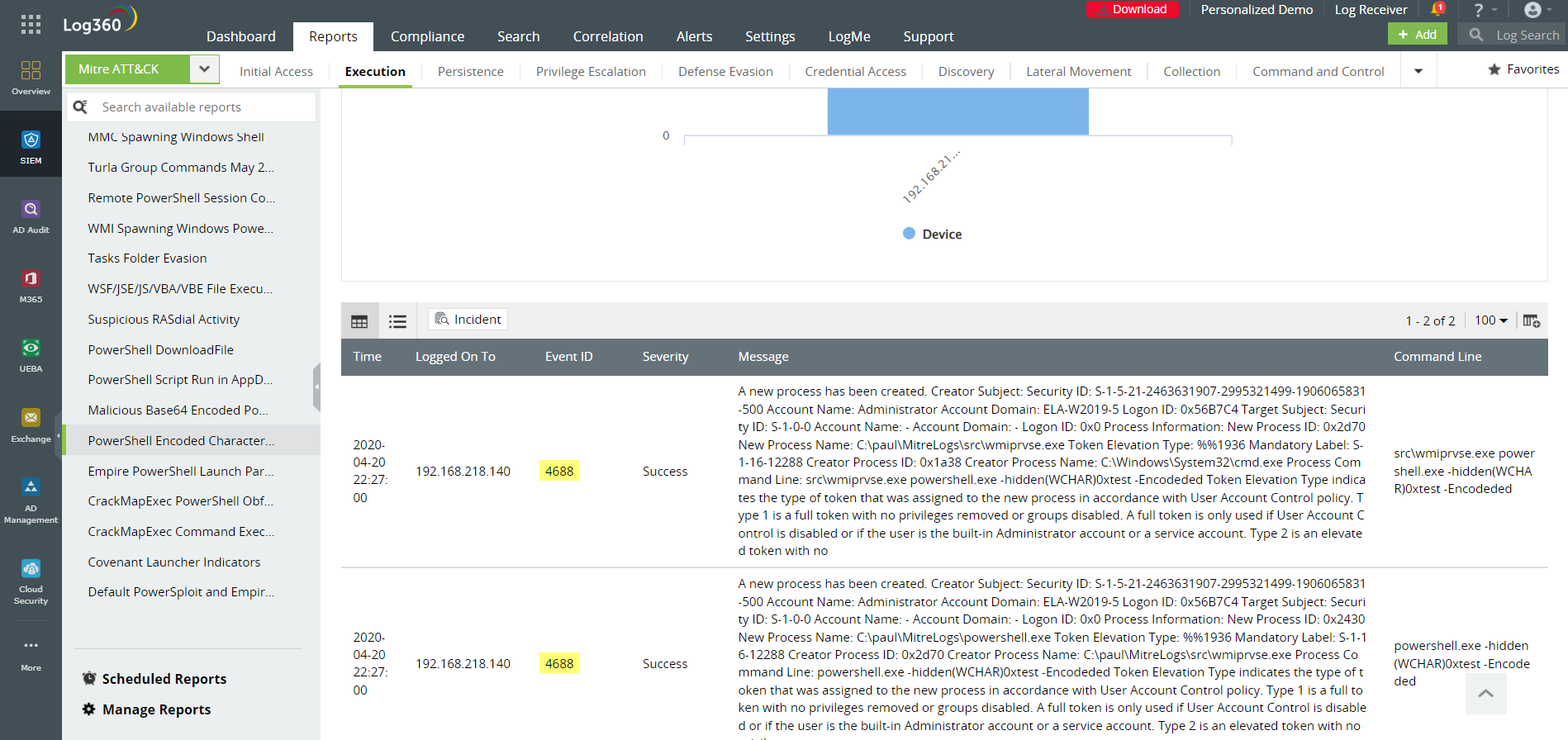
Figure 6: Attacks often use encoded PowerShell code to start processes that can enable the download of malicious files, Log360 tracks these commands in this report.
– Malicious Base64 encoded PowerShell keywords in command lines
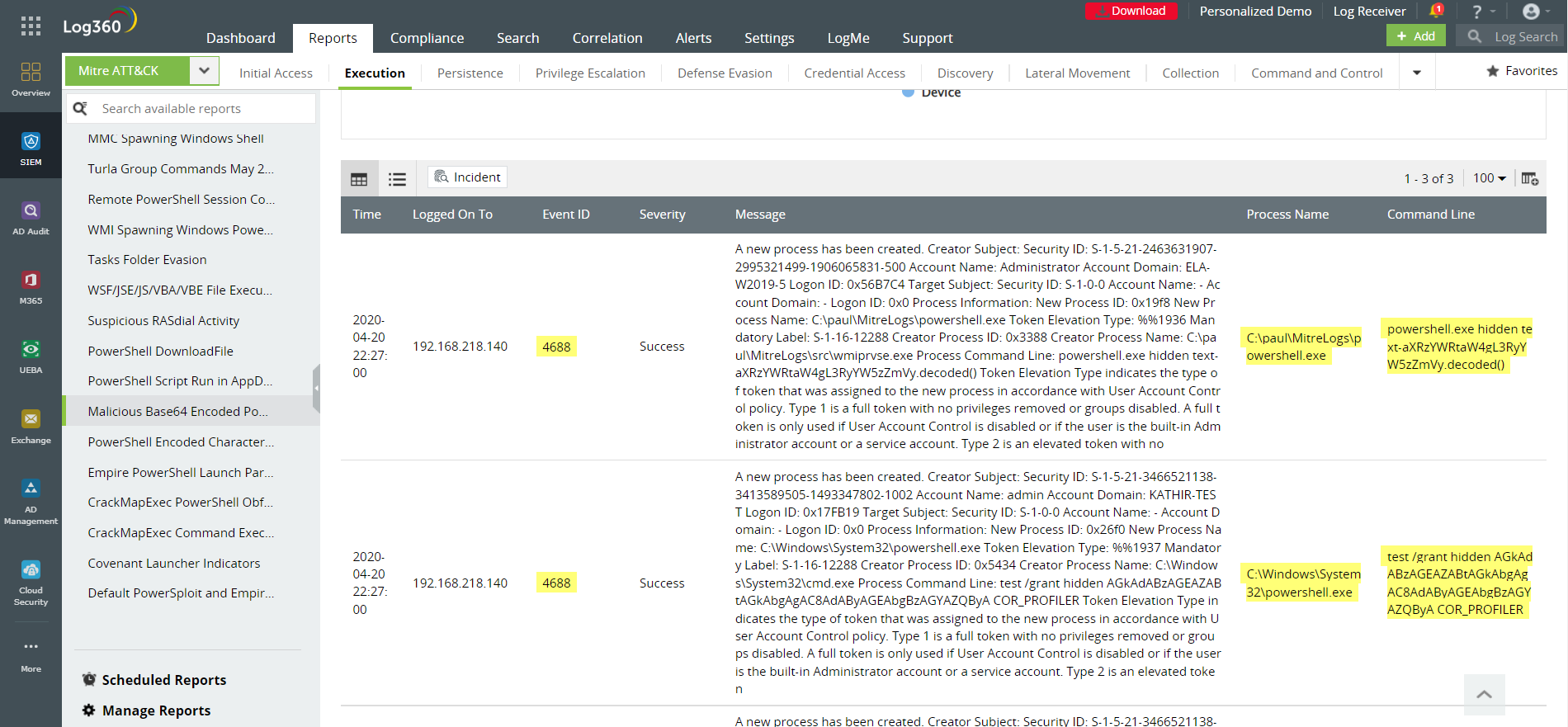
Figure 7: Base64 encoded PowerShell script is often used to execute malicious commands in systems that are designed to transmit data in ASCII format. Any executable that signals this is logged by Log360.
– Empire PowerShell launch parameters
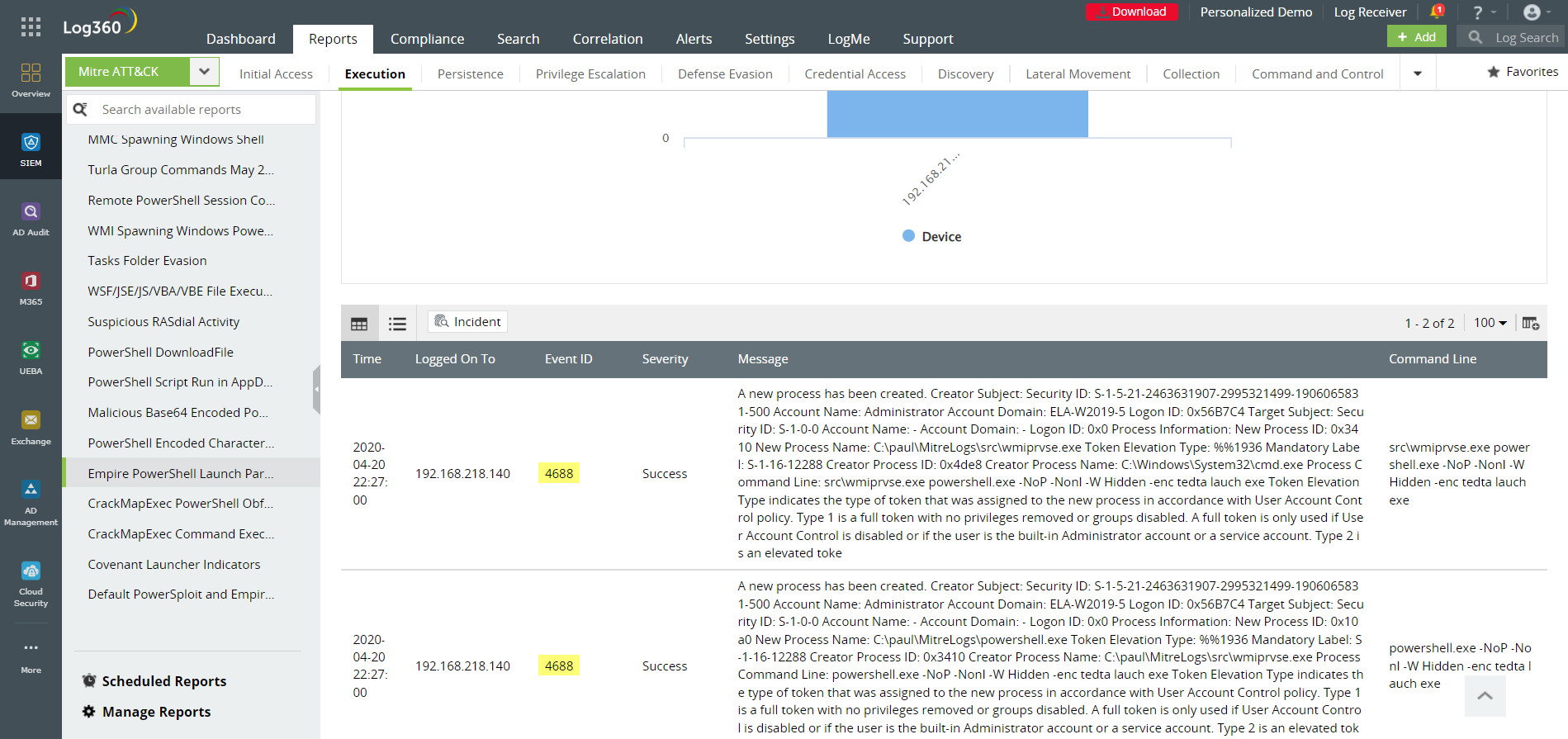
Figure 8: Commands or executables that could signal attackers trying to launch the Empire framework are logged in this report.
To learn more about how Log360 reports can help you detect and prevent PowerShell-based attacks, download our free 45-day trial and sign up for a personalized demo with our product experts. Experience better cybersecurity today with Log360, a unified SIEM solution.