
Active Directory (AD) objects are rarely managed as standalone entities. In Part 3 of this series, we covered practical exercises for creating and managing two of the most critical AD objects, namely users and computers, after setting up a laboratory AD environment on virtual machines.
To manage AD effectively, knowledge and practical experience with AD groups and organization units (OUs) is imperative. In this fourth part of our series, we’ll elaborate on this.
Introduction to AD groups and organizational units
AD groups: Groups are containers that hold other AD objects such as users, computers, or even other groups. Groups help with the effective organization and management of individual AD objects.
Individual AD users are often grouped together to form AD groups for better management. Grouping users based on a specific purpose ensures that appropriate permissions and access rights are enabled for better organization and control of each user identity.
AD administrators usually focus on AD groups comprised of AD users rather than of computers or of other objects, because of the dynamic nature and complexity of user objects. For example, the groups that the users objects may be a part of, the telephone number of a user, or the user’s access to different network resources may constantly change. These changes have to be made in AD. User groups are dynamic AD objects requiring constant updates and attention.
AD groups come in two variations:
-
Security groups: These are AD groups concerned with assigning user permissions and rights for ensuring effective control on the access to shared network resources.
-
Distribution groups: These are used in conjunction with email services and help with creating and managing email distribution lists.
OUs: OUs are logical containers used to organize AD domains better.
As covered in Part 1 of this series, one of the main benefits of AD is that administrators can centrally manage and administer effective resource allocation in the AD environment.
Group Policy settings are applied to a logical group of AD objects to manage them more effectively. OUs are these logical groups, which contain users, computers and other groups. They help in administering permissions and applying Group Policy settings.
The permission to access certain applications and file systems, controlling user and computer settings and maintaining control on the availability and updating of software for every AD user are some of the settings that can be configured through Group Policy Objects in AD. Through them, the maintenance and management of the AD environment becomes seamless.
How do AD groups and OUs differ from each other?
Both AD groups and OUs can contain other AD objects; both of them help to manage the AD objects better but why do we till use both?
The answer lies in understanding the two categories of AD objects in finer detail. Let us compare and contrast the two below:
Similarities:
-
Both OUs and AD groups help with managing the domain structure. Since domains are fairly inflexible upon creation, how well AD services can be utilized within a domain is dependent on how the OUs are structured and how groups are managed upon their creation.
-
OUs and groups can be created based on any of the following criteria:
➤ Business needs, i.e., department-wise categorization of OUs or an AD group solely for sales executives of a particular product.
➤ Geographical locations, i.e., an OU created specifically for a particular region or an AD group for marketing executives in a particular branch office.
➤ Object types, i.e., individual OUs for user and computer accounts.
➤ As-needed basis, i.e. separate OUs for servers for easier Group Policy application.
Differences:
|
OUs |
AD groups |
| OUs help to assign administrative privileges. |
Groups are used to define access permissions and user rights to the objects contained within them. |
Some common privileges include:
|
These permissions include read, write, and share permissions to manage access and modify shared network resources such as printers or common files in a shared folder |
|
It is worth noting here that such Group Policy settings can be applied only to OUs rather than to individual AD groups. |
Users are usually grouped together into global groups, which are in turn added to domain local groups (mostly in the case of multi-domain organizations) and ultimately added to access control lists to enable the setting of such permissions. |
On careful analysis, it’s important to realize that in order to set up a successful AD environment, both groups and OUs have to be configured cohesively.
Although AD groups and OUs differ, they have to be managed together, taking into consideration both broad and granular management needs.
Now, to begin working hands-on with these two AD objects, let us divide the scope of this blog in two parts.
Part 1: Working with AD groups
Similar to the procedure followed in Part 3 of this series, we will use Active Directory Administrative Center (ADAC) and Active Directory Users and Computers (ADUC) as the two primary tools to carry out the sample exercises.
Creation of AD user groups
To create a group with ADAC:
-
Choose the default Users container.
-
From the right pane within the users container, you can create a new group.
-
Assign a group name, which will automatically fill in the sAMAccountName.
-
The group type can be selected here along with the group scope; the group type can be set as universal (if you have a multi-domain organization), domain local, or global.
It is good practice to provide a short description of the group at the time of its creation.
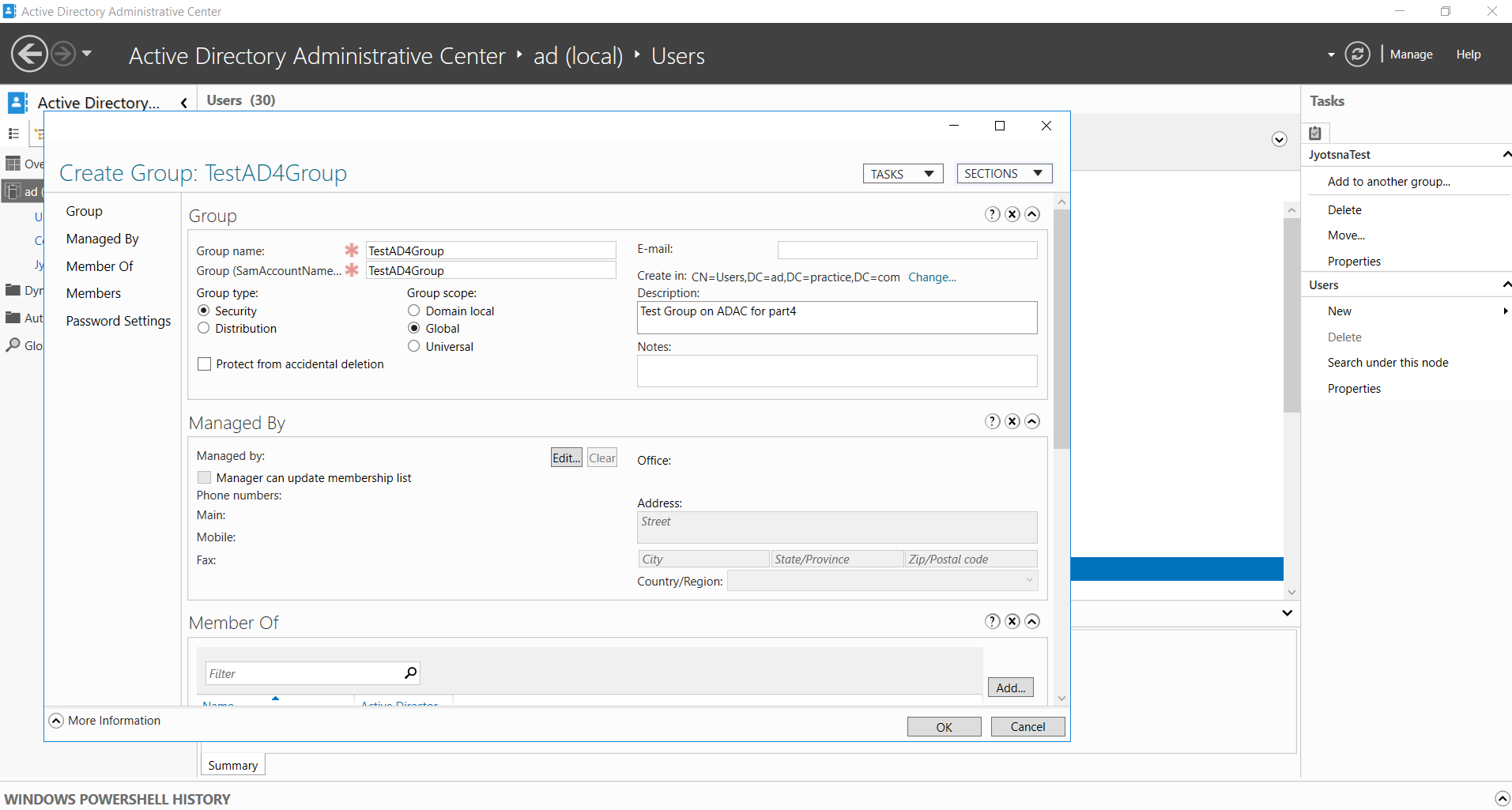 Figure 1. A global security group called TestAD4Group is being created using ADAC
Figure 1. A global security group called TestAD4Group is being created using ADAC
To create a group with ADUC:
- Right-click the Users container to see the option to create a new group.
- The rest of the details to be provided and the subsequent steps are similar to those in ADAC.
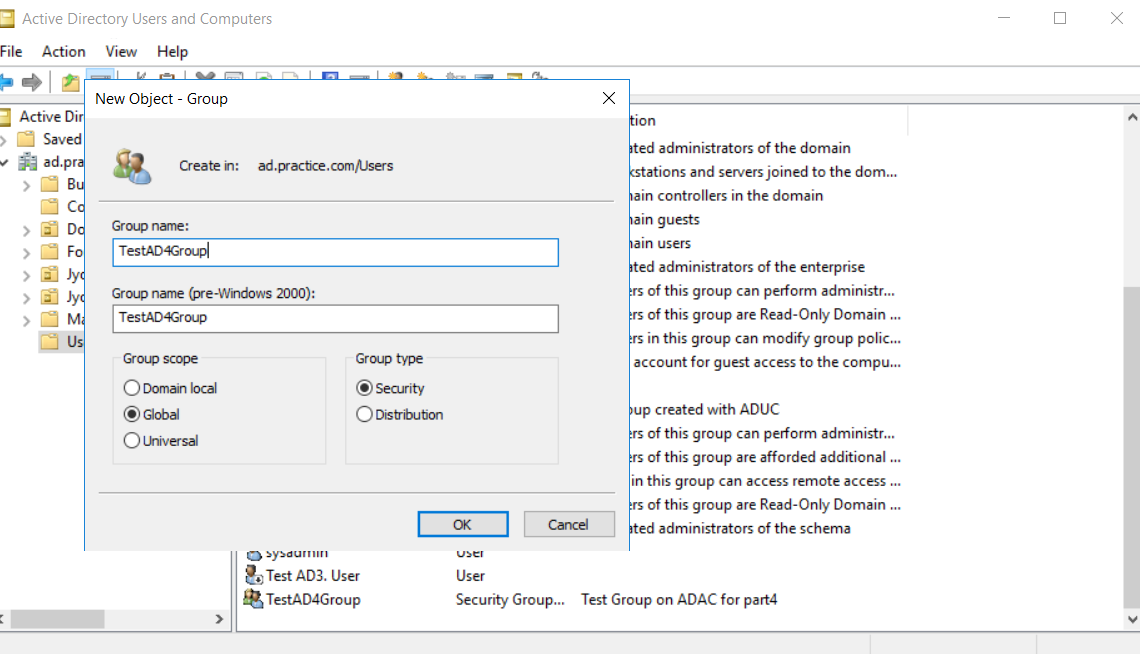
Figure 2. A global security group called TestAD4Group is being created using ADUC
AD group membership
The group properties provide information on group membership.
To add new members through either ADAC or ADUC, user names have to be searched for and then added.
Let us try this out. In our previous blog, a sample user called Test AD3.User was created.
To add this user to the group TestAD4Group, you can use either ADAC or ADUC.
A screenshot of the window that opens up during this operation is shown below.
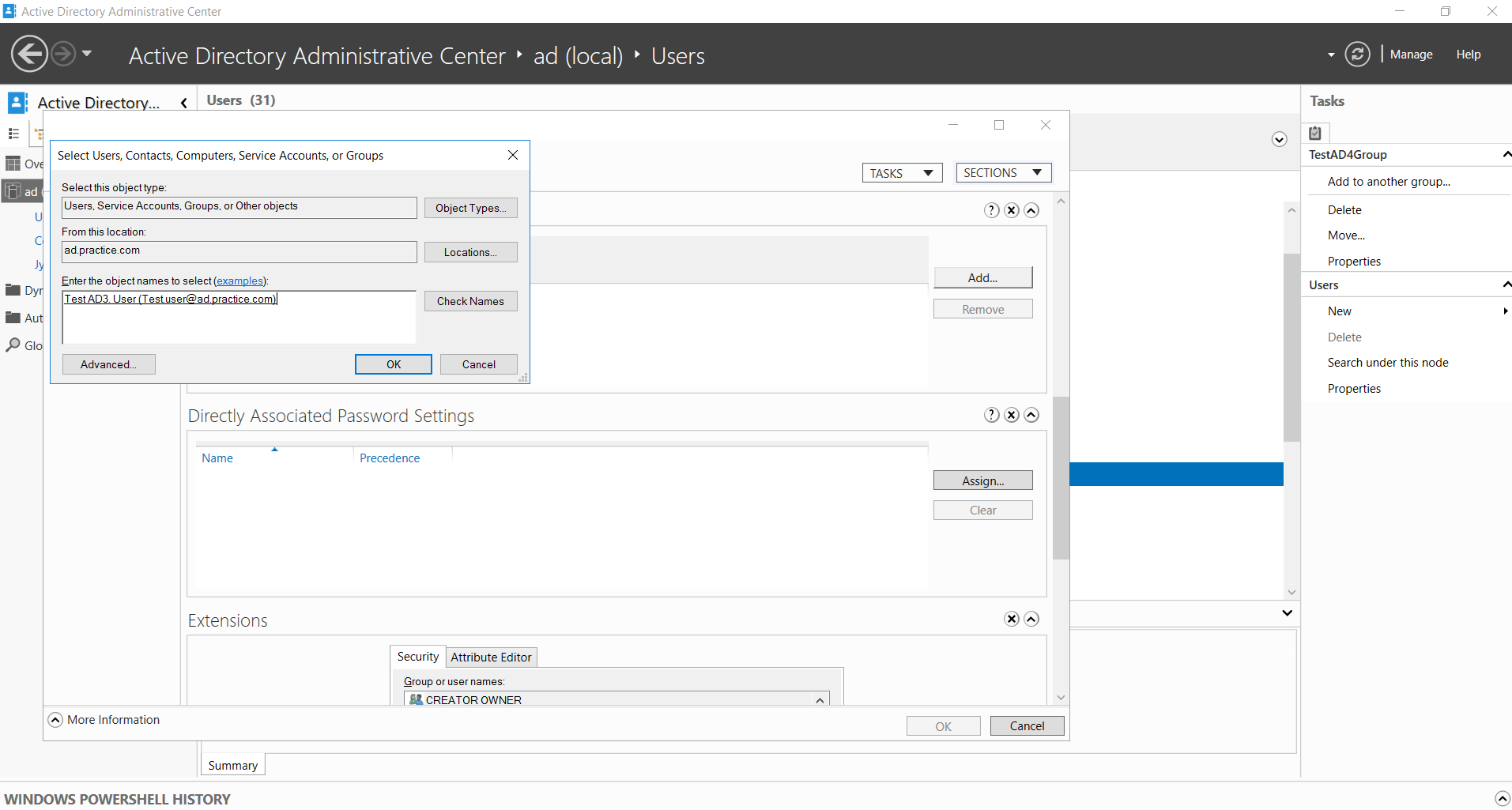
Figure 3. Adding a test user to a test group created using ADAC
You can also delete group members through ADAC and ADUC using the remove option.
Creation of AD computer groups
Computer groups can be created in the Computer containers on both ADAC and ADUC. Computers created can be added to these computer groups in a similar manner to that followed for users.
Deletion of AD groups
To delete AD groups that no longer serve their intended purpose, right-click the AD group and choose the delete option available on the menu that pops up.
Management of AD groups
Any problems concerning AD groups usually involve members being part of incorrect groups. Group properties can be reviewed and members can be added or removed as per the procedure explained above to ensure that the appropriate AD groups are configured for the right set of AD users.
Part 2: Working with OUs
OUs differ from default containers in their ability to have Group Policy applied to them and the possibility to have other OUs contained within them. Either of these is not possible with containers.
To have a hands-on experience with working with OUs, either ADAC or ADUC can be used. Let us look at a few simple AD exercises on OUs.
Creation of OUs
Before the how behind the procedure of OU creation is discussed, a good understanding of the why is crucial. Once the purpose of the new OU is clear from an organizational and administrative perspective, the following procedure can be followed for creation.
To create an OU with ADAC:
-
Either a sub-domain or a parent domain can be selected to create the new OU within it. On selection, the New option from the tasks pane on the right lets you create a new OU.
-
Note that the OU name to be provided has to be unique if the OU is being created in the root domain.
-
The information to be provided for OU creation is fairly simple as seen in the sample TestADACOU created below.
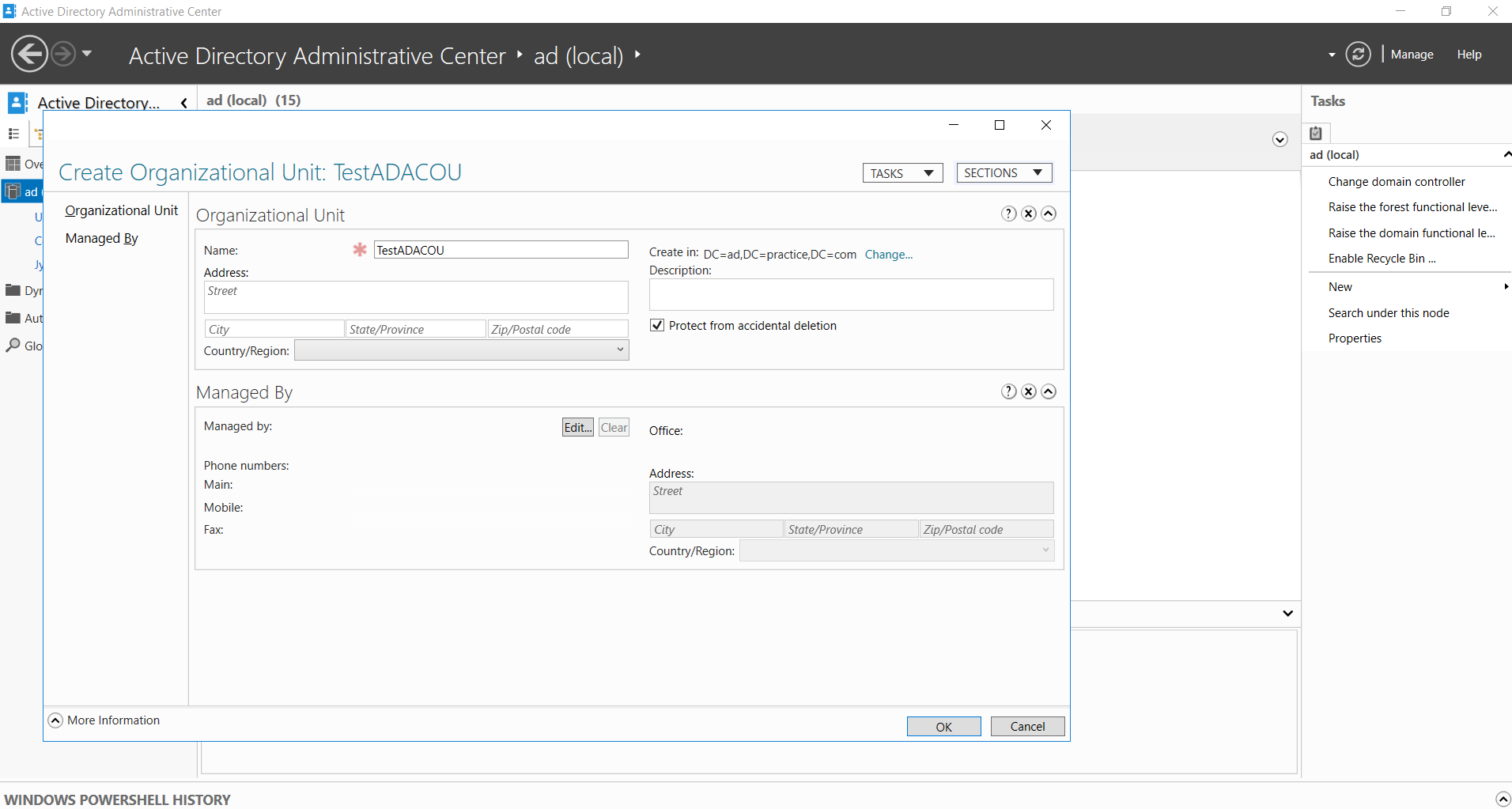
Figure 4. Test OU created using ADAC
The procedure is similar in ADUC; right-click on the required domain to create a new OU.
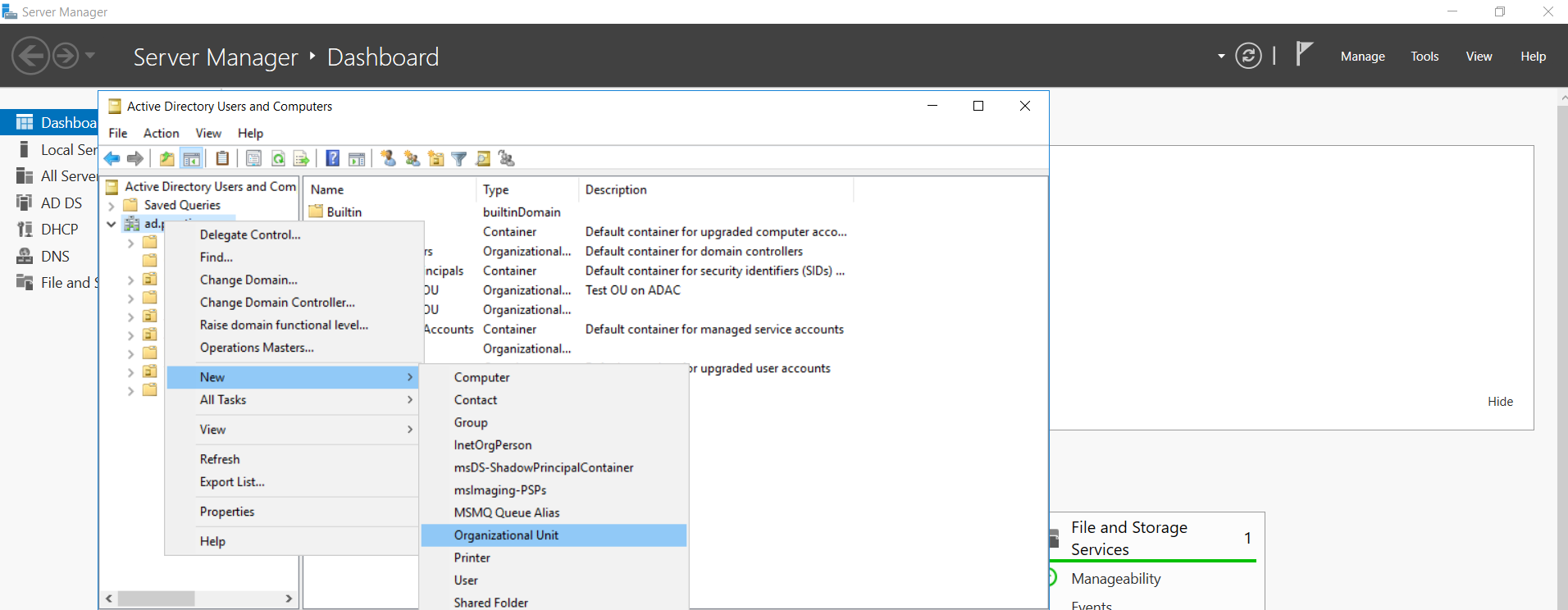
Figure 5. Procedure to create a test OU using ADUC
Since OUs contain innumerable other important AD objects that form the basis of how resources in the organization are centrally managed, administrators have the option to protect them from accidental deletion. This will help prevent the unnecessary, malicious, or wrongful deletion of OUs at the hands of others.
Modification of OUs
-
The management of OUs includes renaming by right-clicking that lists the rename option for any individual OU.
-
Adding a description for all OUs is always a good practice. This option can be found under the Properties tab of every individual OU.
-
One or more users can be added under the Managed By tab of each OU to designate specific users to oversee the management of OUs. This option is available to these added users if they are provided with the appropriate permissions.
-
Deleting OUs can also be performed by right-clicking the OU and selecting Delete.
Consider a scenario where certain employees in the organization are transferred to a new department at a new location. In these cases, moving objects between OUs becomes a critical task to ensure that this change reflects in the AD database too. All the necessary changes in the employee’s Group Policy settings have to be configured.
Although user PowerShell commands to move objects between OUs is easier, faster, and requires less manual intervention, you can use either ADAC and ADUC to move objects if you aren’t familiar with writing PowerShell scripts yet.
After learning about some of the most important practical tasks associated with AD groups and OUs, you can now rest assured that your foundation on AD is sound. The ultimate aim of this series is to help you build on your knowledge of Active Directory Domain Services to understand a wide variety of AD management aspects.
AD is a complex world in itself used for a variety of purposes. This blog series is a step towards establishing a strong working foundation to tackle AD, starting with the fundamentals.

