
For an organization to prevent cyberattacks, it first needs complete visibility into all the events that occur within its network. With this visibility, the organization can analyze risky behavior by users and entities, and take the necessary steps to proactively secure itself.
However, if an attack were to still happen, the organization again needs complete visibility to identify how and from where the attacker entered the network. Even when performing log forensics, organizations need complete network visibility. Without it, the organization won’t be able to go back in time, identify the root cause, and tie it back to the behavior of particular employees or endpoints.
To gain network visibility, organizations need to ingest the logs of all the network devices within a security analytics solution such as SIEM tool. The first step to gaining visibility is discovering all the devices connected to the network. But in the case of a growing organization where new devices may be added to the network continuously, maintaining visibility on all network devices is easier said than done. However, organizations with undiscovered devices are sitting ducks for cyberattacks.
While adding devices manually is an option, it’s not a feasible one, especially in a growing organization. In such cases, it’s better to opt for a SIEM solution that can automatically discover devices in your network. Whether the device is a Windows device, a firewall, a router, or another device, a good SIEM solution can automatically discover it, as long as the security analyst inputs the IP range in which they want devices to be discovered.
Once these devices are discovered, the SIEM solution can analyze the logs from these devices seamlessly and provide detailed reports. The SIEM solution will use its built-in threat intelligence platform (TIP), correlation engine, and anomaly detection module to analyze logs.
A TIP provides threat feeds that give crucial information such as indicators of compromise, malicious IP addresses, and details of known attackers’ capabilities. The correlation engine helps connect the dots between seemingly unrelated events and identify them as a part of a larger incident. And anomaly detection, or UEBA, helps detect anomalous events caused by malicious insiders and external threats. UEBA also enables risk scoring and alert prioritization, making the lives of analysts much easier.
ManageEngine Log360 is a unified SIEM solution with integrated DLP and CASB capabilities that offers real-time security monitoring, complete cloud visibility, integrated compliance management, and so much more.
To automatically discover devices using Log360, select the Settings tab in the Log360 dashboard and click Devices as shown in the figure below.
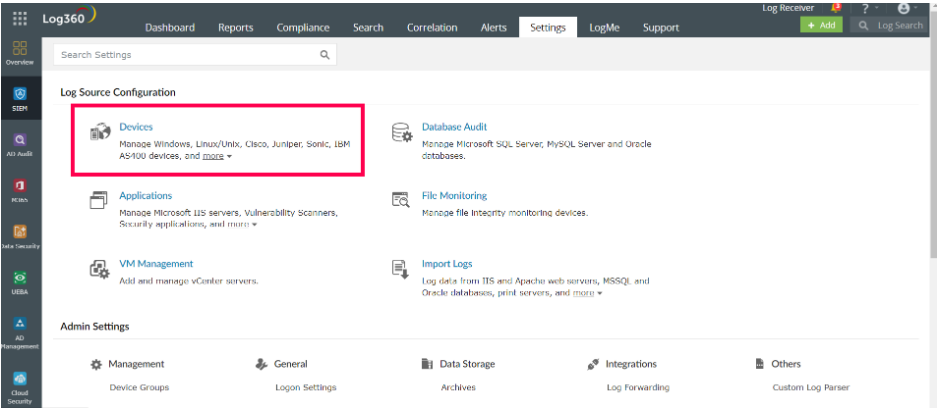
Figure 1: Log360 console showing options for log source configuration
Now if you want to add a device of a specific format, say a syslog device, then click Syslog Devices and select Add Device(s), as shown in Figure 2, to add your required device.
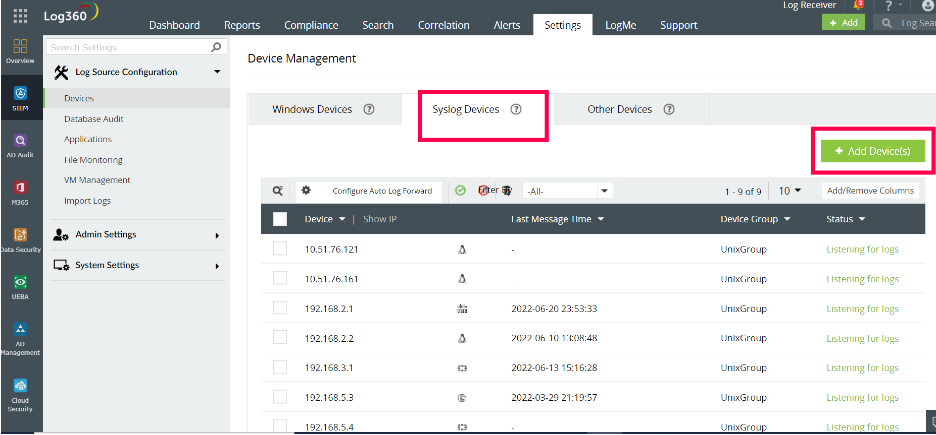
Figure 2: Log360 console displaying options for device discovery
If you already know the host details, input them directly. Otherwise you can select the Discover & Add option as shown below.
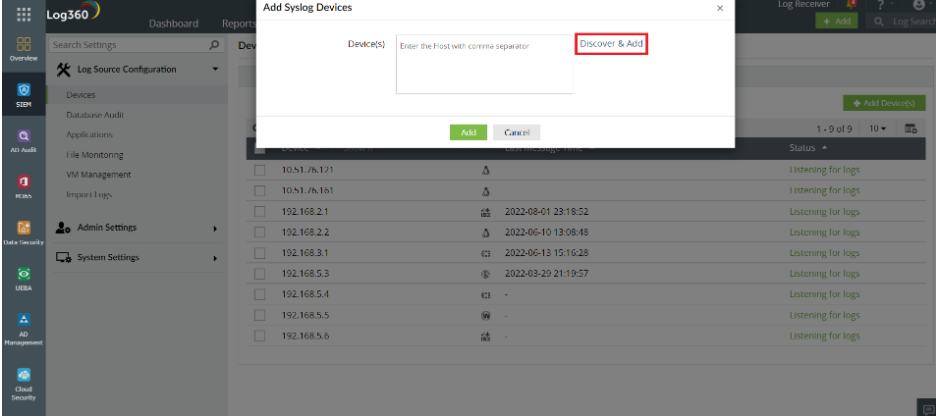
Figure 3: Adding syslog devices using Log360
You can now discover devices based on IP range or CIDR as shown in Figure 4.
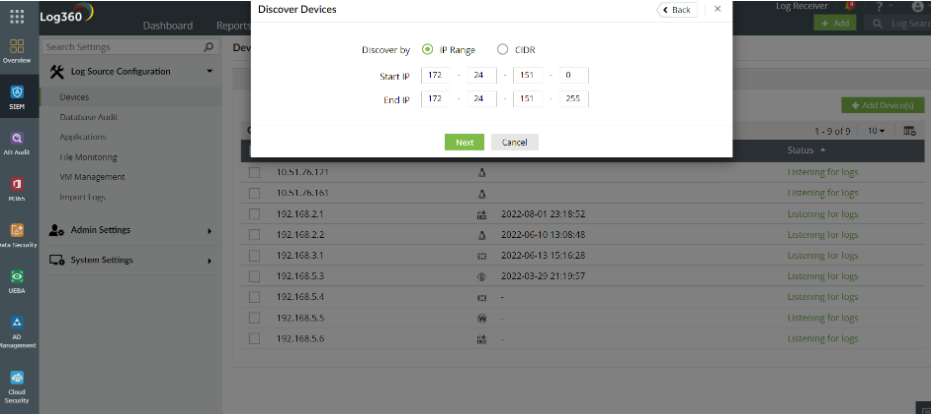
Figure 4: Automatically discovering devices using ManageEngine Log360.
Apart from discovering devices automatically, Log360 helps you:
-
Collect logs from more than 700 types of network devices for real-time monitoring.
-
Correlate different events into larger incidents that are easier to manage.
-
Monitor access to servers and databases, and track suspicious activities on your file servers.
-
Receive alerts based on increasing risk scores.
-
Automate your incident response and stop malicious data exfiltration.
To learn more about how Log360 can help your organization defend against cyberattacks, sign up for a personalized demo and talk to our solution experts. Thanks for reading, folks!

