The recently discovered Windows zero-day vulnerability continues to make news as threat actors across the globe are relentless in their efforts to exploit it. The vulnerability, dubbed Follina, can be exploited when the Microsoft Support Diagnostic Tool (MSDT) is called by a Microsoft Office application using the URL protocol.
What is its impact?
Tracked as CVE-2022-30190, exploiting this vulnerability enables the attacker to execute arbitrary code when a Word document is opened or simply previewed on a target computer. Once this is done, the attacker can execute PowerShell commands to install programs, view, change, or delete data, or even create new accounts.
With a rating of 7.8, Follina falls under the “high” severity category. What makes it more serious is that the MSDT tool which collects and sends diagnostic data to Microsoft Support for analysis is found on all Windows and Windows Server OS versions. This means that without a mitigation strategy, all Windows machines are potential targets for bad actors attempting to exploit this vulnerability.
While Microsoft has acknowledged the vulnerability and suggested workarounds to mitigate its impact, it has not issued an official patch to address the flaw (as of June 13 2022).
How to detect Follina exploitations
Monitoring the parent-child processes running in your environment is one way to detect possible exploitation of this vulnerability. If you have a solution that audits Windows processes, you can configure it to:
-
Look for systems spawning msdt.exe as a child process of WINWORD.EXE, EXCEL.EXE, OUTLOOK.EXE, or POWERPNT.EXE.
-
Look for IT_BrowseForFile, IT_LaunchMethod, and IT_RebrowseForFile if you have command-line auditing enabled, as they are not common parameters.
Are there any workarounds?
As part of its advisory, Microsoft has suggested disabling the MSDT URL protocol as a workaround to mitigate this vulnerability.
To disable MSDT URL protocol:
-
Run the Command Prompt as Administrator.
-
Execute the following command to back up the registry key:
reg export HKEY_CLASSES_ROOT\ms-msdt <filename>
-
Then, execute the command shown below:
reg delete HKEY_CLASSES_ROOT\ms-msdt /f
To undo the workaround:
-
Run the Command Prompt as Administrator.
-
Execute the following command to restore the registry key:
reg import <filename>
How ManageEngine ADAudit Plus can help you detect Follina exploits
Using ADAudit Plus’ exclusive process tracking reports, you can verify if your environment is exposed to CVE-2022-30190 and trigger real-time alerts whenever an exploitation attempt is detected.
Check for affected computers using Process Tracking reports
ADAudit Plus automatically enables the “Audit process creation” policy that lets you track process creation activity. However, to avoid false positives, you should enable command line process auditing to ensure that the process creation event (Event ID 4688) includes information about the name of the executable file and the arguments passed.
To enable command line process auditing:
-
Log in to the server running ADAudit Plus and open the Group Policy Management Console.
-
From the GPOs linked to the domain, identify ADAuditPlusMSPolicy GPO, right-click on it, and select Edit.
-
In the Group Policy Editor, navigate to Computer Configuration > Policies > Administrative Templates > System > Audit Process Creation.
-
Right-click on the Include command line in process creation events setting and select Edit.
-
In the Include command line in process creation events window, check Enabled and click OK.
Once the above GPO setting is enabled, ADAudit Plus’ Process Tracking reports will display events related to possible Follina exploits.
To check for affected computers:
-
Log in to your ADAudit Plus web console.
-
Navigate to Server Audit > Process Tracking > New Process Created.
-
In the report, click on Advanced Search and add the appropriate rules corresponding to your environment.
- If you have previously enabled command line process auditing in your environment, you can check for affected computers by adding the set of rules shown in the image below:
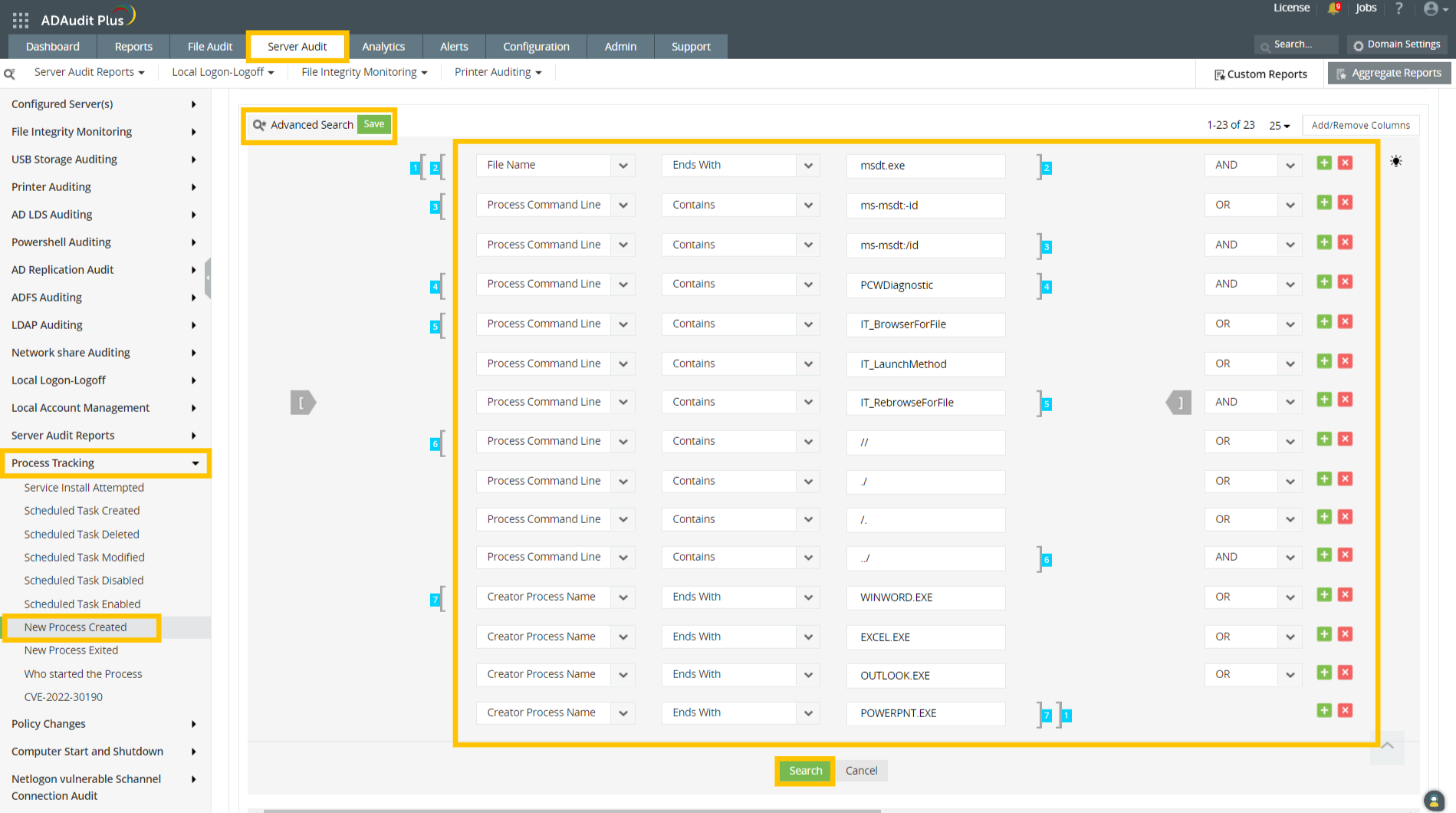
[ [ “File Name” Ends With “msdt.exe” ] AND [ “Process Command Line” Contains “ms-msdt:-id” OR “Process Command Line” Contains “ms-msdt:/id” ] AND [ “Process Command Line” Contains “PCWDiagnostic” ] AND [ “Process Command Line” Contains “IT_BrowserForFile” OR “Process Command Line” Contains “IT_LaunchMethod” OR “Process Command Line” Contains “IT_RebrowseForFile” ] AND [ “Process Command Line” Contains “//” OR “Process Command Line” Contains “./” OR “Process Command Line” Contains “/.” OR “Process Command Line” Contains “../” ] AND [ “Creator Process Name” Ends With “WINWORD.EXE” OR “Creator Process Name” Ends With “EXCEL.EXE” OR “Creator Process Name” Ends With “OUTLOOK.EXE” OR “Creator Process Name” Ends With “POWERPNT.EXE” ] ]
- If you have not enabled command line process auditing in your environment previously, you can check for affected computers by adding the set of rules shown below:
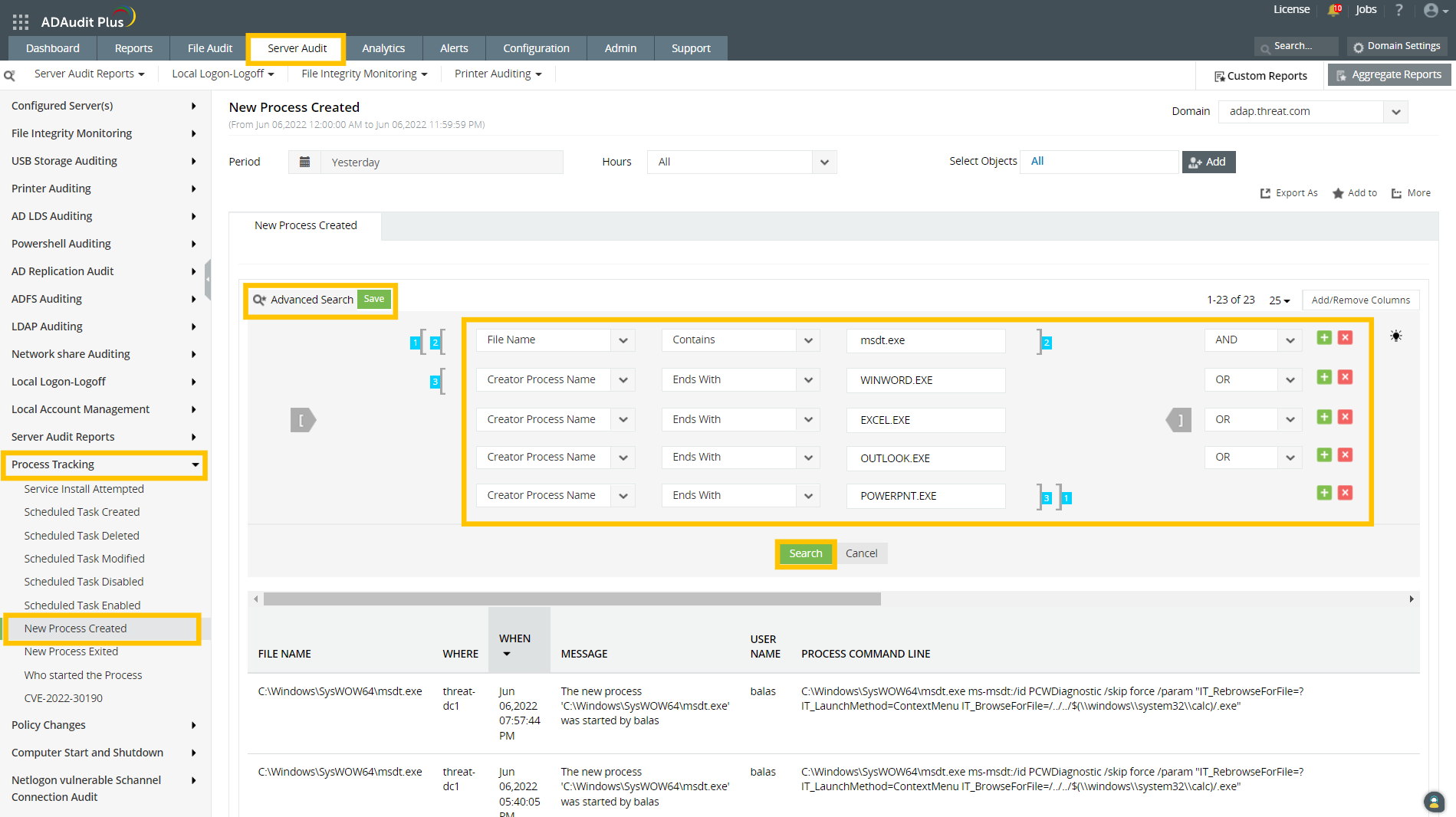
[ [ “File Name” Contains “msdt.exe” ] AND [ “Creator Process Name” Ends With “WINWORD.EXE” OR “Creator Process Name” Ends With “EXCEL.EXE” OR “Creator Process Name” Ends With “OUTLOOK.EXE” OR “Creator Process Name” Ends With “POWERPNT.EXE” ] ]
Note: As information related to the executable file name and the arguments passed will not be available in event ID 4688 when command line process auditing is not enabled, the reports resulting from the set of rules in the above image may indicate false positives.
- If you have previously enabled command line process auditing in your environment, you can check for affected computers by adding the set of rules shown in the image below:
-
Once you have added the rules, click Search and you will find the list of computers affected by this vulnerability.
Set up real-time alerts to detect future Follina exploits with ADAudit Plus
With ADAudit Plus, you can also configure alert profiles to receive real-time alerts when events related to this vulnerability are logged in the future.
To create an alert profile:
-
Log in to your ADAudit Plus web console.
-
Navigate to Configuration > Alert Profiles > Create Alert Profile.
-
Specify a suitable Name and Description for the alert profile and select its Severity.
-
In the Category field, select All and click the “+” symbol on the right.
-
In the pop up screen, select your Domain, select All in the Category drop down, click Search, type “Process Tracking” and press Enter.
-
Check the Process Tacking for the <selected> domain report profile and click OK.
-
Enter a suitable Alert Message.
-
In the Advanced Configuration section, select Filter, click Add Filter, and add the appropriate rules corresponding to your environment.
- If you have previously enabled command line process auditing in your environment, add the set of rules shown in the image below:
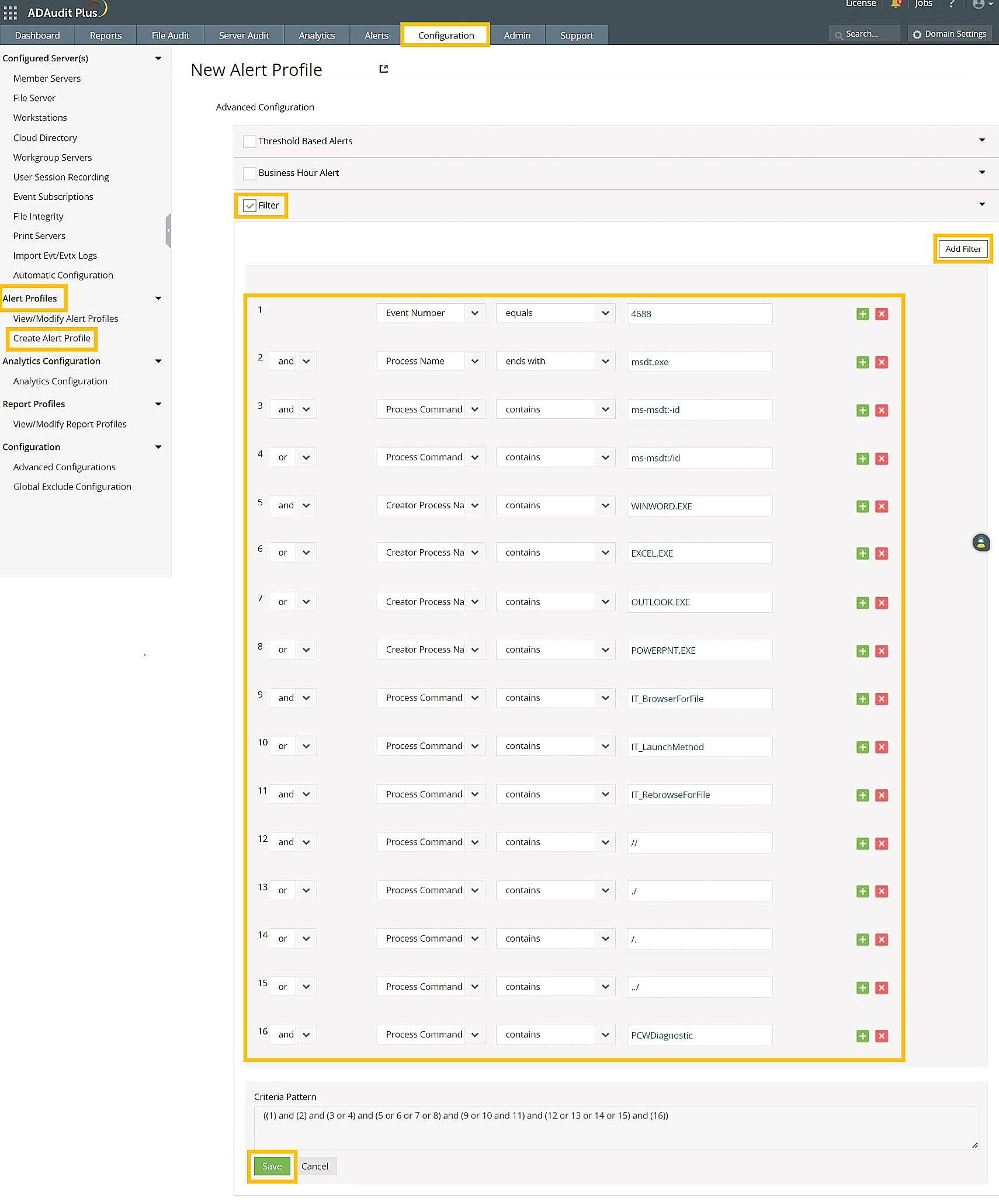
- If you have not enabled command line process auditing in your environment previously, add the set of rules shown in the image below:
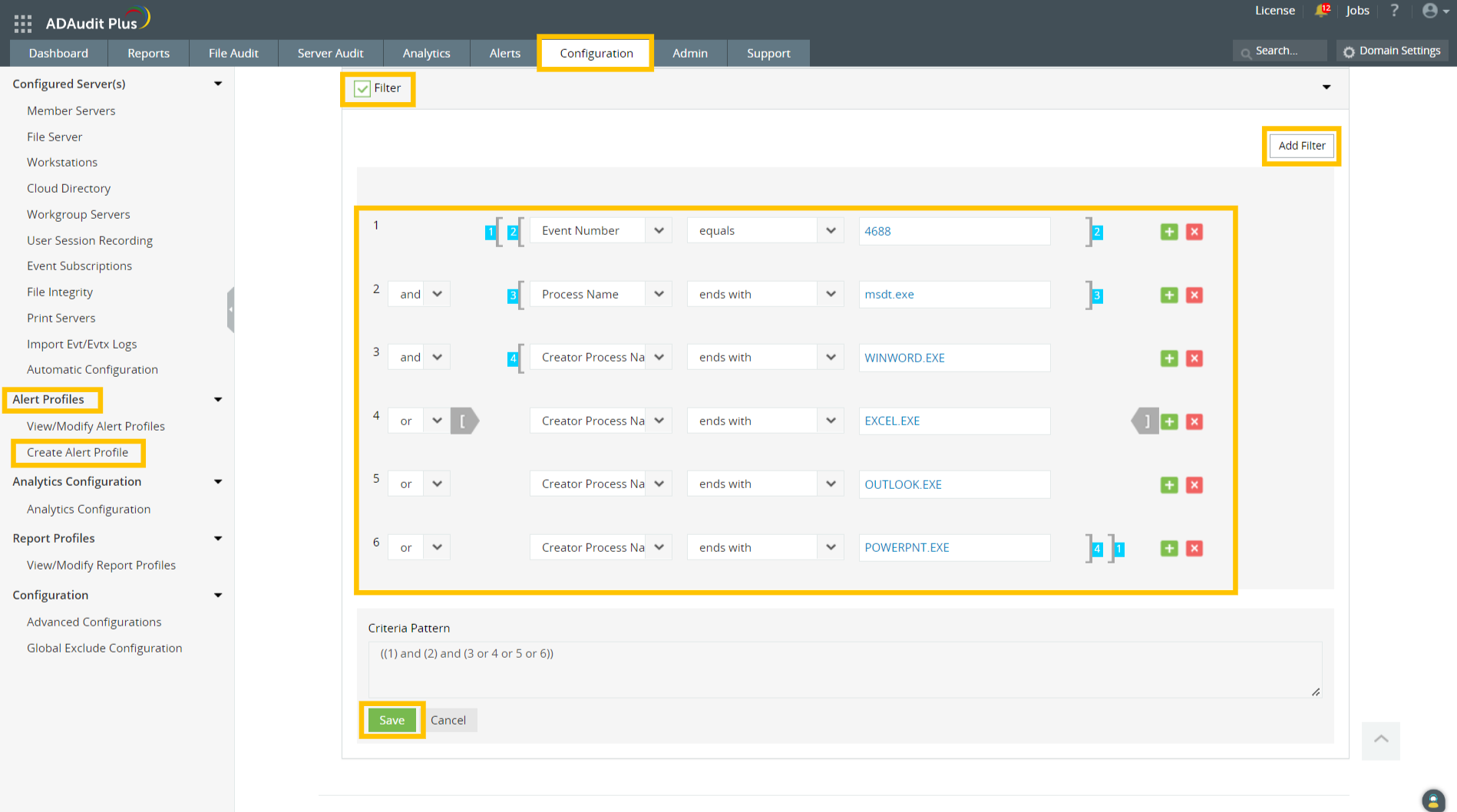
Note: As information related to the executable file name and the arguments passed will not be available in event ID 4688 when command line process auditing is not enabled, the reports resulting from the set of rules in the above image may indicate false positives.
- If you have previously enabled command line process auditing in your environment, add the set of rules shown in the image below:
-
In the Alert Actions section, choose how you would like to receive the alert message (SMS or E-mail notifications) and configure the corresponding settings.
-
Click Save.
Now you have successfully set up alerts to receive instant SMS or email notifications when a potential exploitation attempt is detected.
About ManageEngine ADAudit Plus
ADAudit Plus is a real-time change auditing solution that helps keep your Active Directory, Azure AD, file servers, Windows servers, and workstations both secure and compliant.
